Overview
In this documentation, we will guide you through the process of reprogramming your YubiKey using the YubiKey Personalization Tool, generating an inventory file with the Yubico tool to import the YubiKey into the WebADM inventory, and assigning and using your YubiKey with OpenOTP. For this process, you will need to have WebADM and OpenOTP installed and configured. Please refer to the WebADM Installation Guide and the WebADM Administrator Guide for detailed instructions.
In this guide, we will utilize the YubiKey Personalization Tool for configuring the YubiKeys and the YubiKey Manager to manage the PIV (Personal Identity Verification) functionality of the YubiKeys.
YubicoOTP
Validation with OpenOTP
Programmation
Once Yubico Personalization Tool is installed, open it.
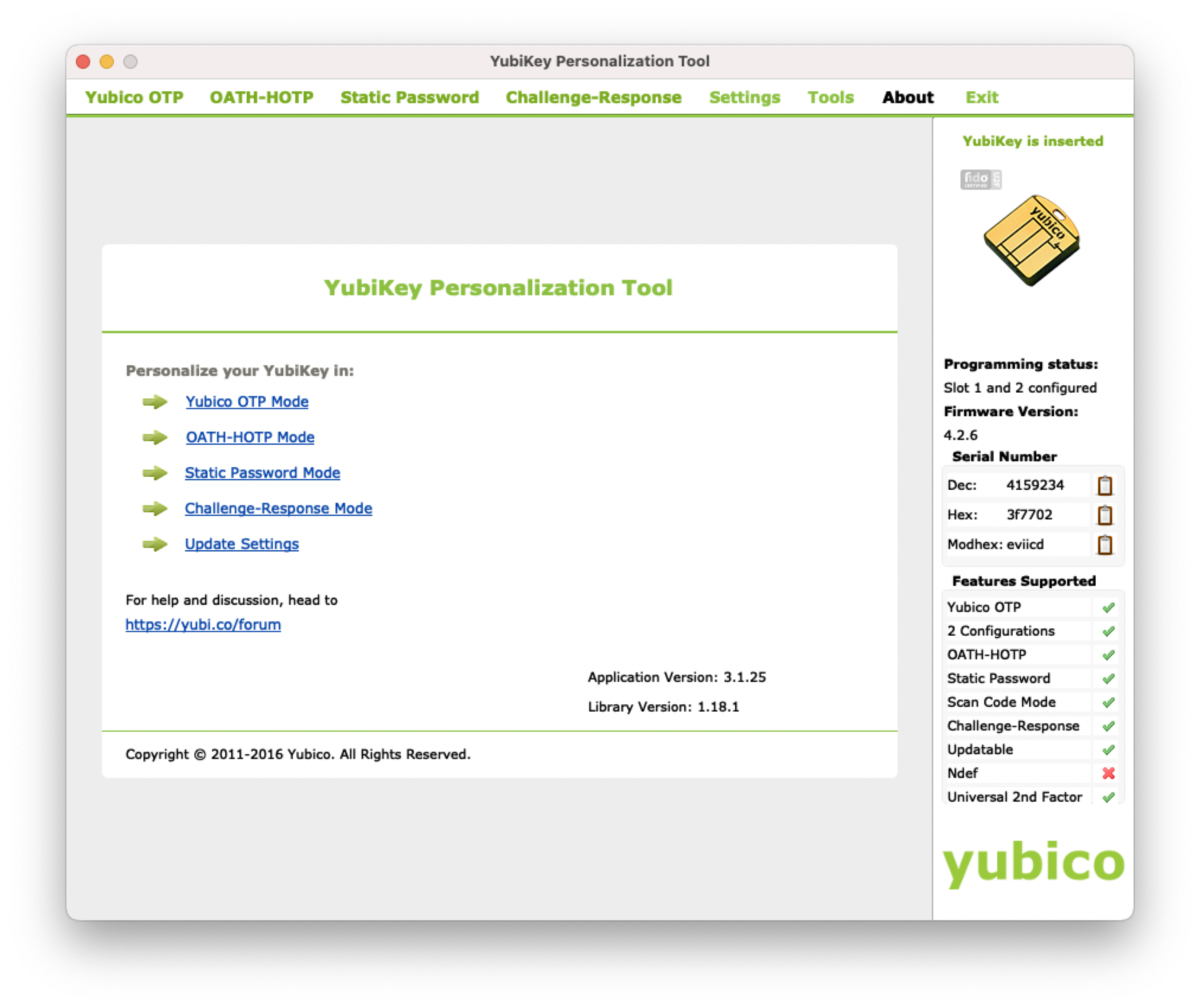
To ensure you have the correct settings from the start, click on Restore Defaults under Settings in the Yubico Personalization Tool before proceeding.
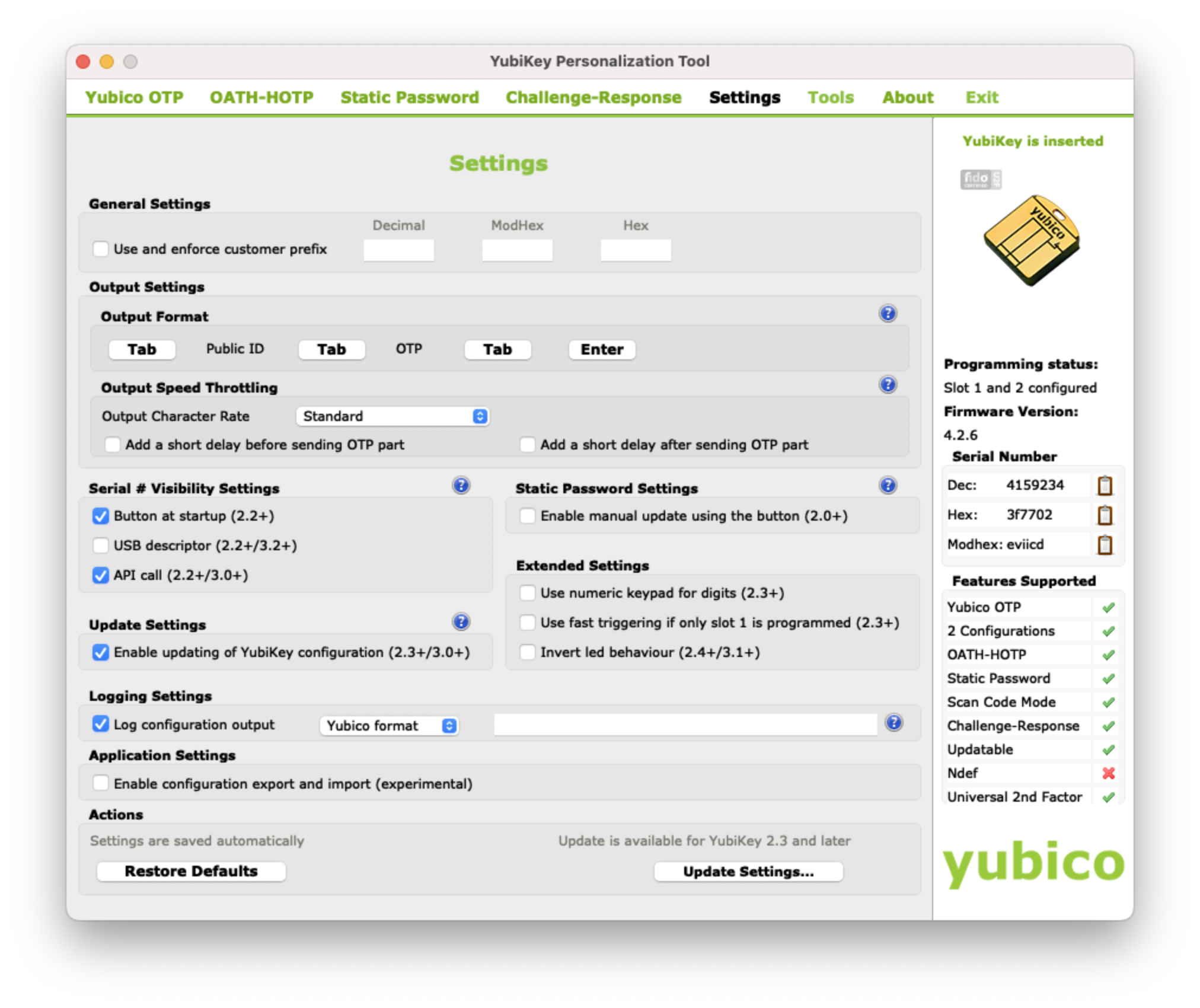
Once you're in the application, navigate to the Settings page and configure the Log configuration output setting to Yubico format.
Inventory generation
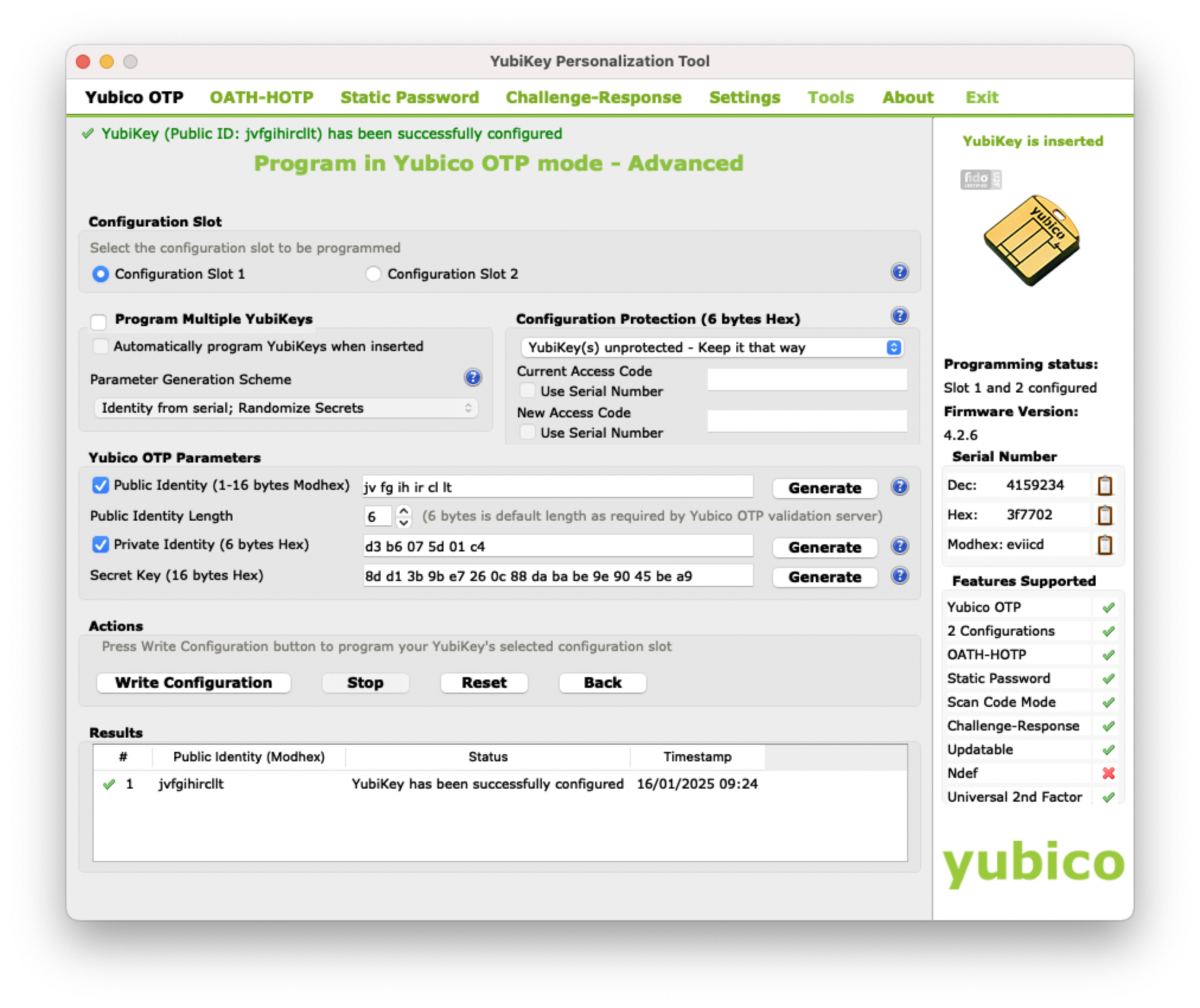
Once you have configured this setting, plug in your YubiKey. Then, switch to the Yubico OTP tab and click on Advanced. Select Configuration Slot 1.
Click the three Generate buttons to create a new Public/Private Identity and a new Secret Key.
Next, click on the Write Configuration button. You will be prompted to save the inventory file.
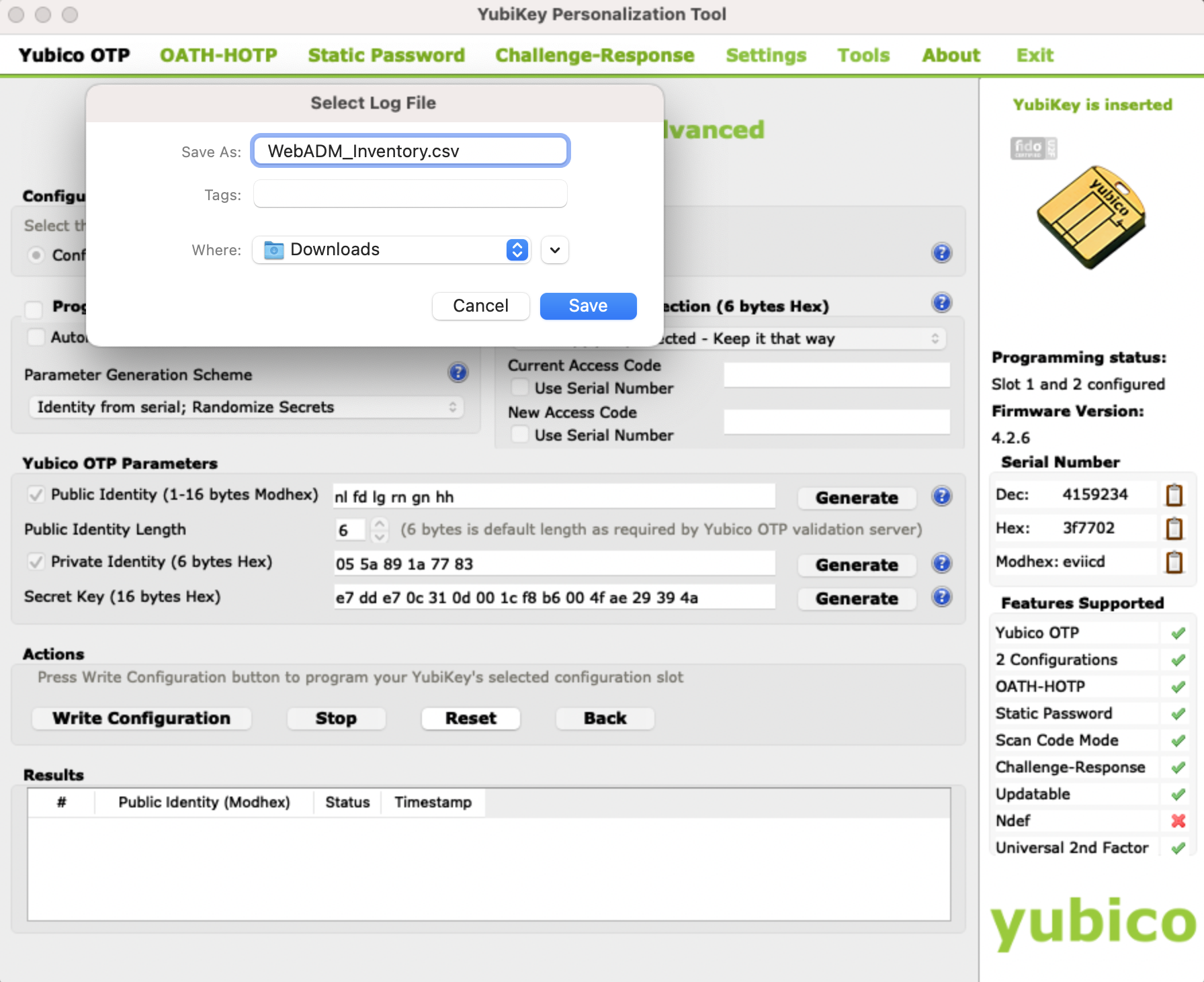
Save this file, as it will be imported into the WebADM inventory in the next step.
Inventory Import in WebADM
We have now reprogrammed our YubiKey and generated an inventory file for it. The next step is to import this inventory file into WebADM to enable the use of the YubiKey with OpenOTP, Spankey, and other services.
Now, go to the WebADM Admin GUI and click on the Import tab.
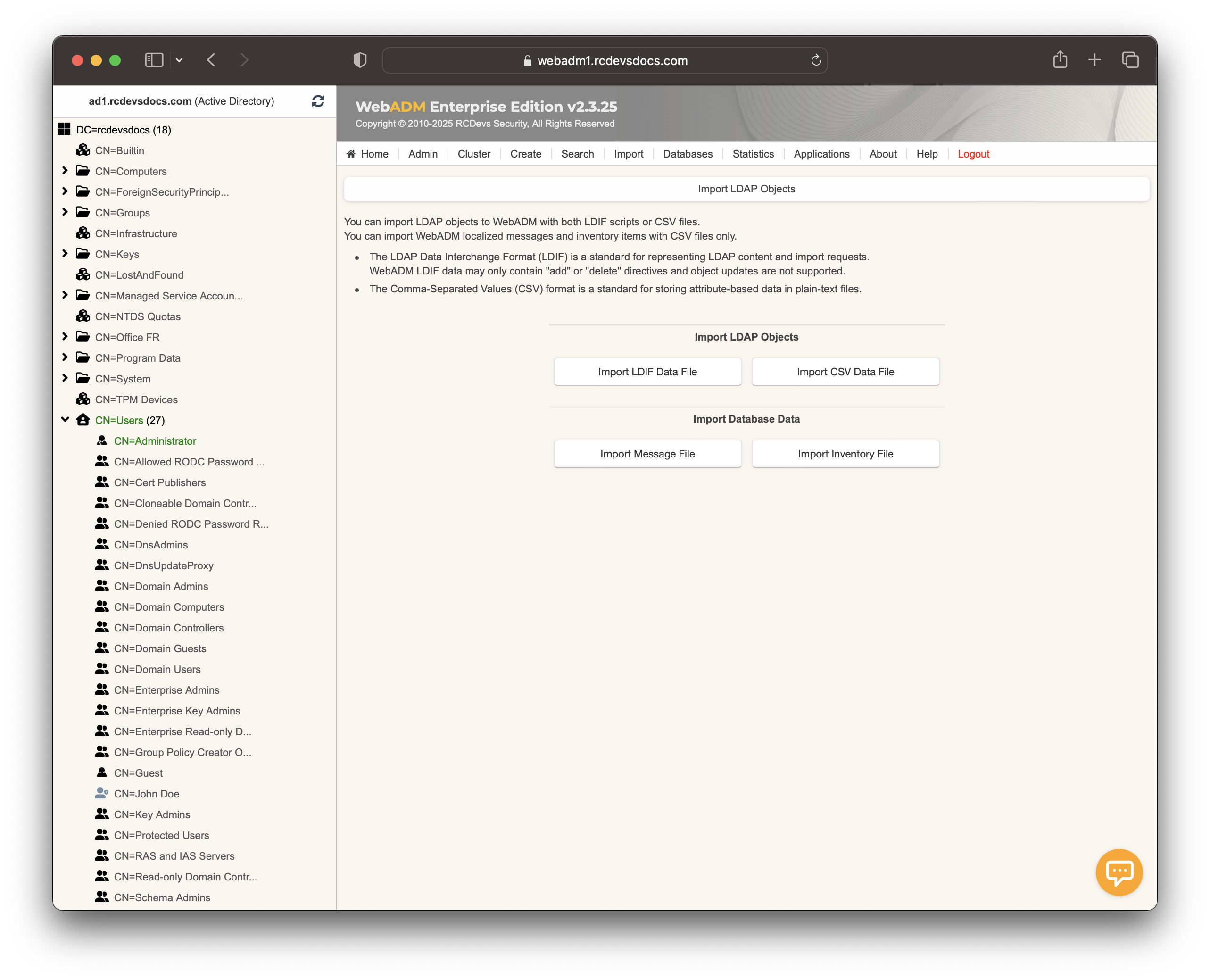
On that page, click the Import Inventory File button.
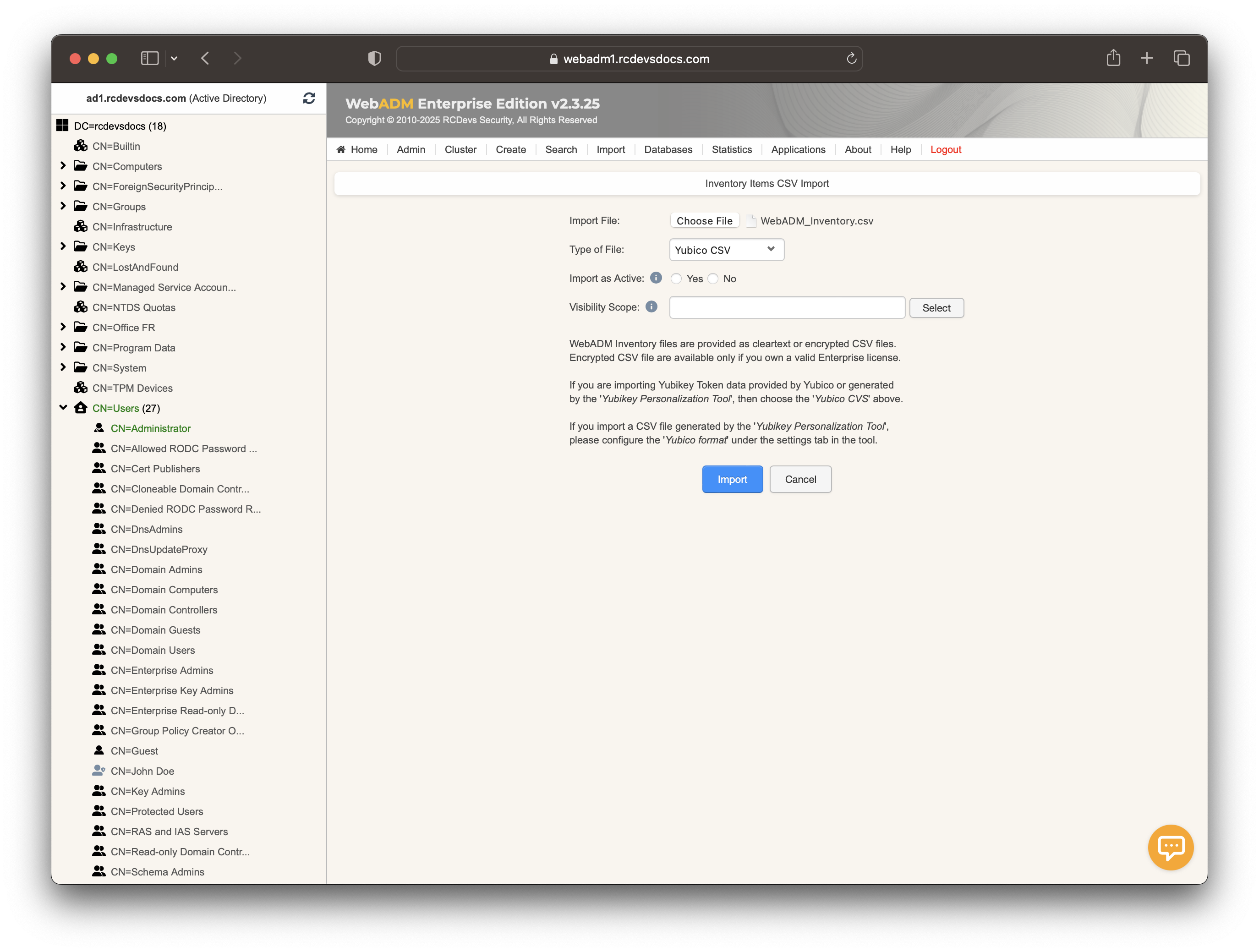
In the Type of File dropdown, select Yubico CSV and browse to the inventory file you previously created using the YubiKey Personalization Tool.
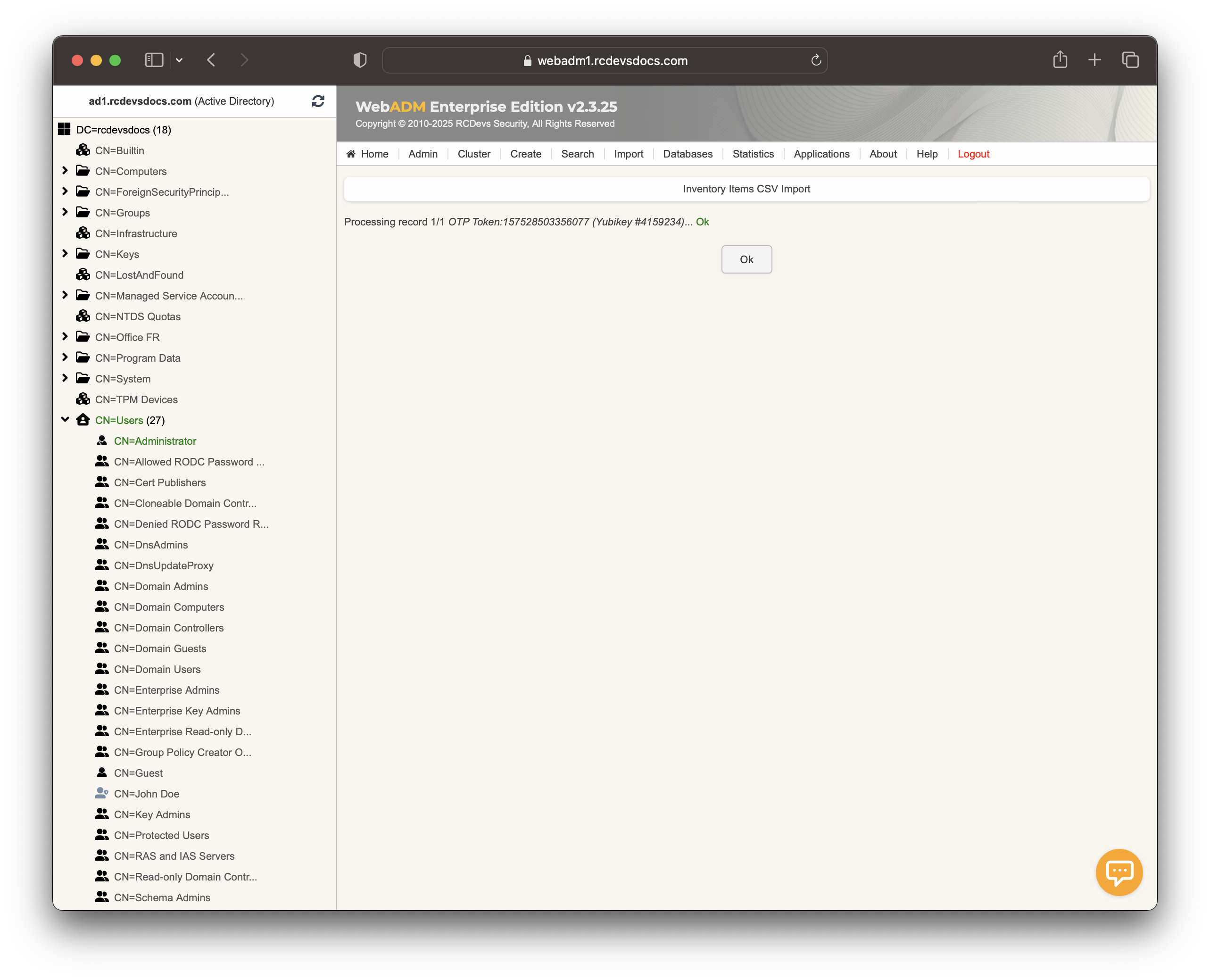
Click the Import button, and the YubiKey should be successfully imported.
You can check the inventory table to verify the new entry. Click on the Databases tab and then select Inventoried OTP Tokens. You should see the new entry listed there.
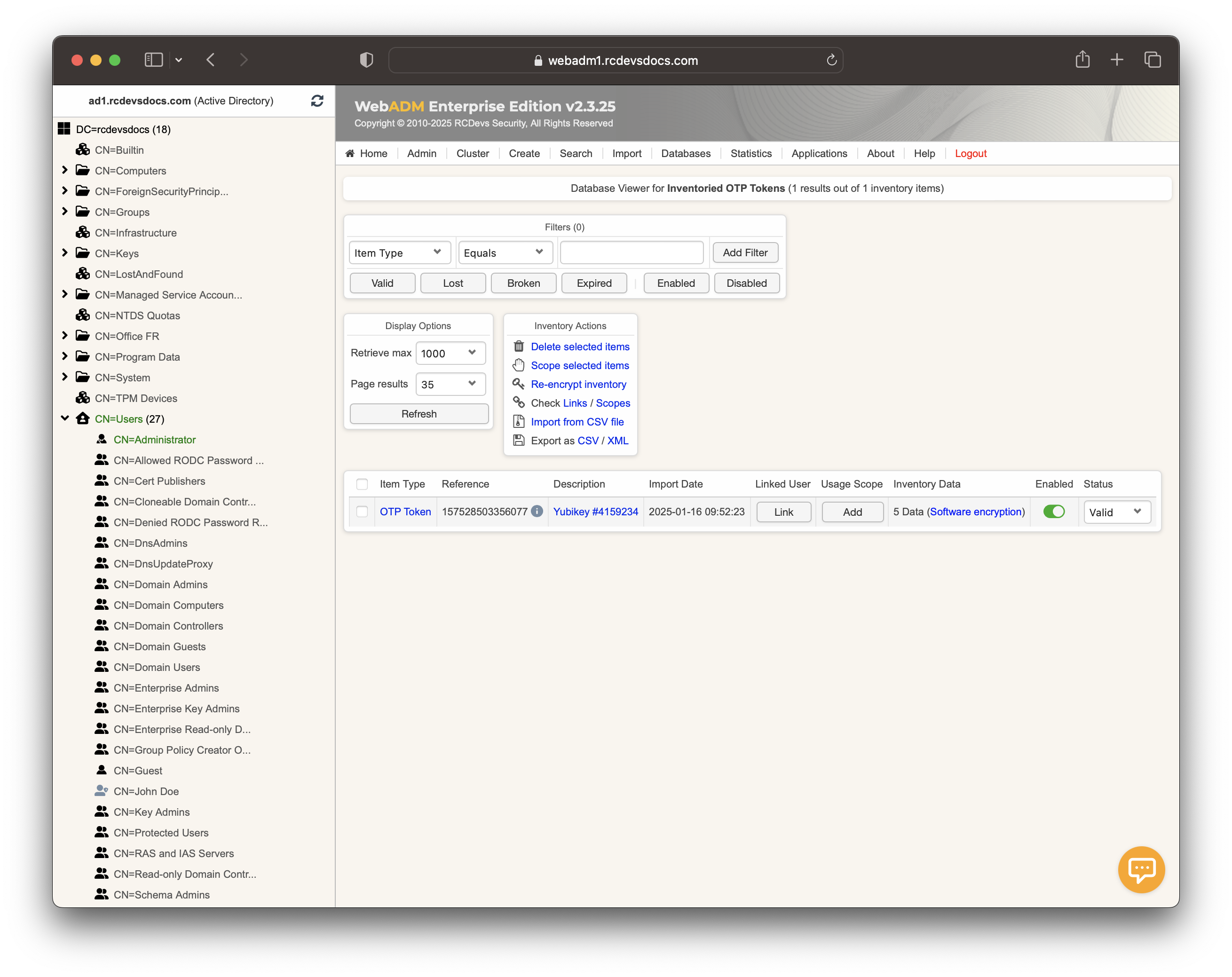
I am now able to assign this YubiKey to a user account. This step will be covered in the next section.
User Registration
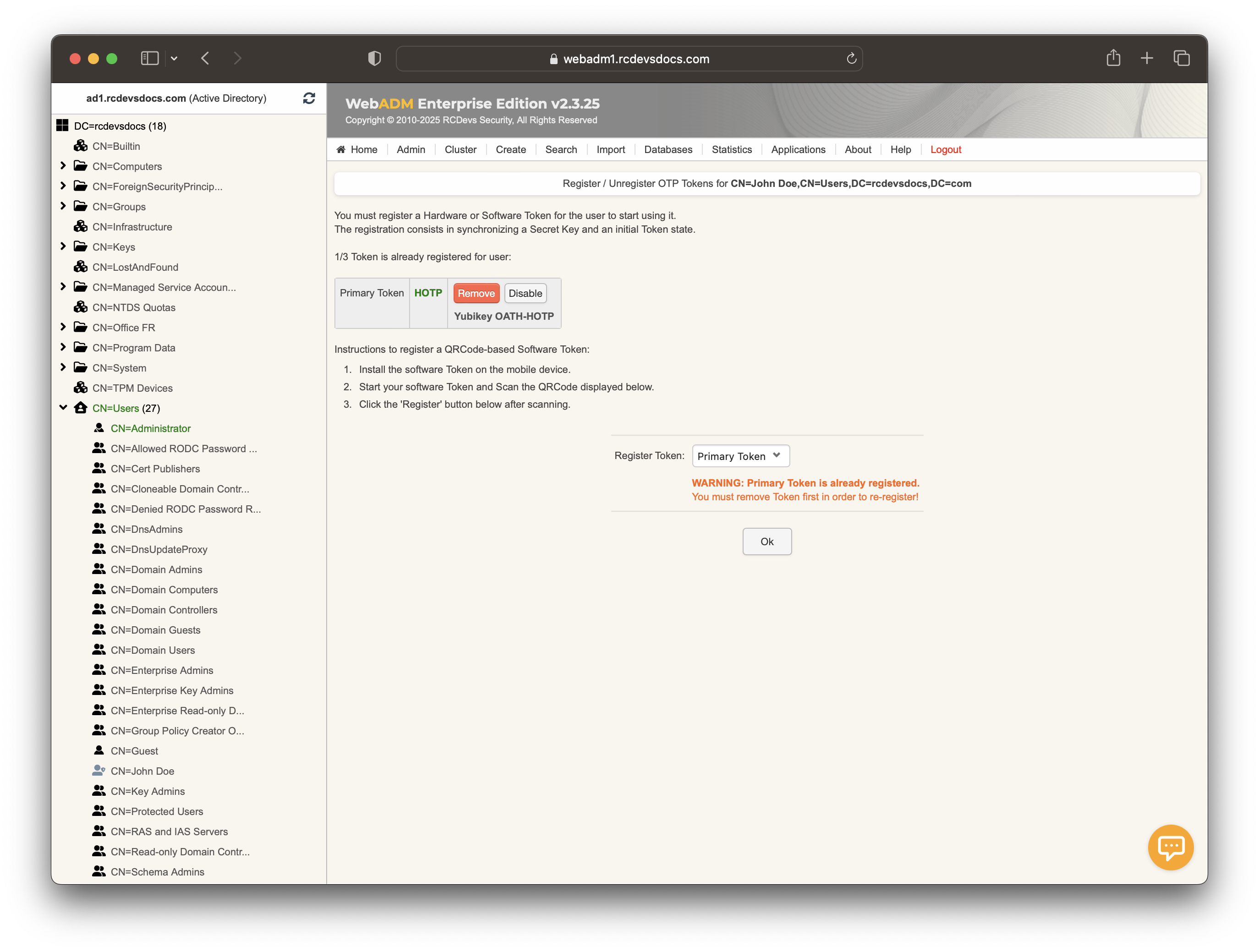
The YubiKey can be assigned to a user through the WebADM Admin GUI, or via the User Self-Service Desk (SelfDesk), User Self-Registration (SelfReg), or Administration Helpdesk (Helpdesk) applications. In this section, we will assign the YubiKey to the user using the Admin GUI. Click on an activated user account in the left-hand tree.
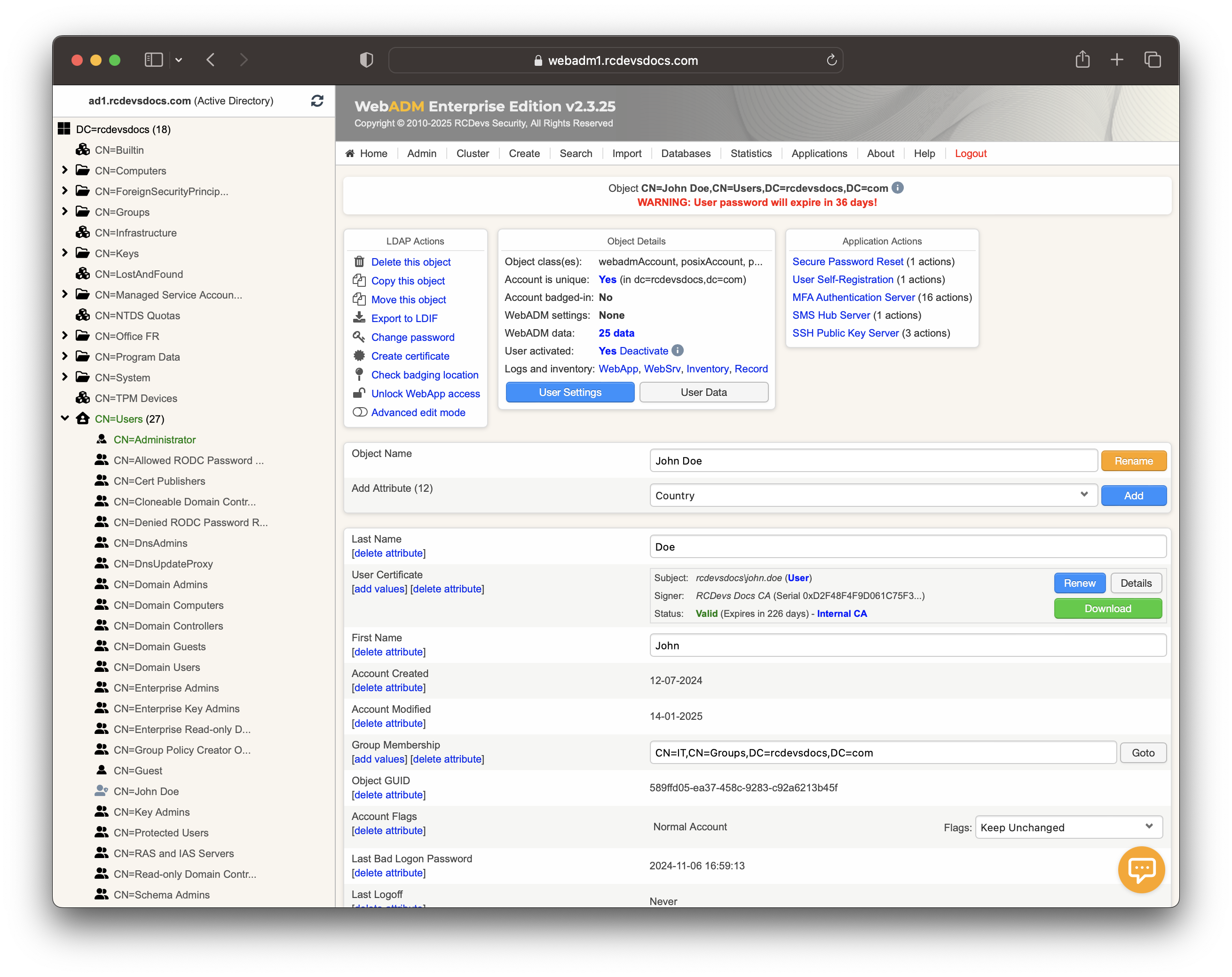
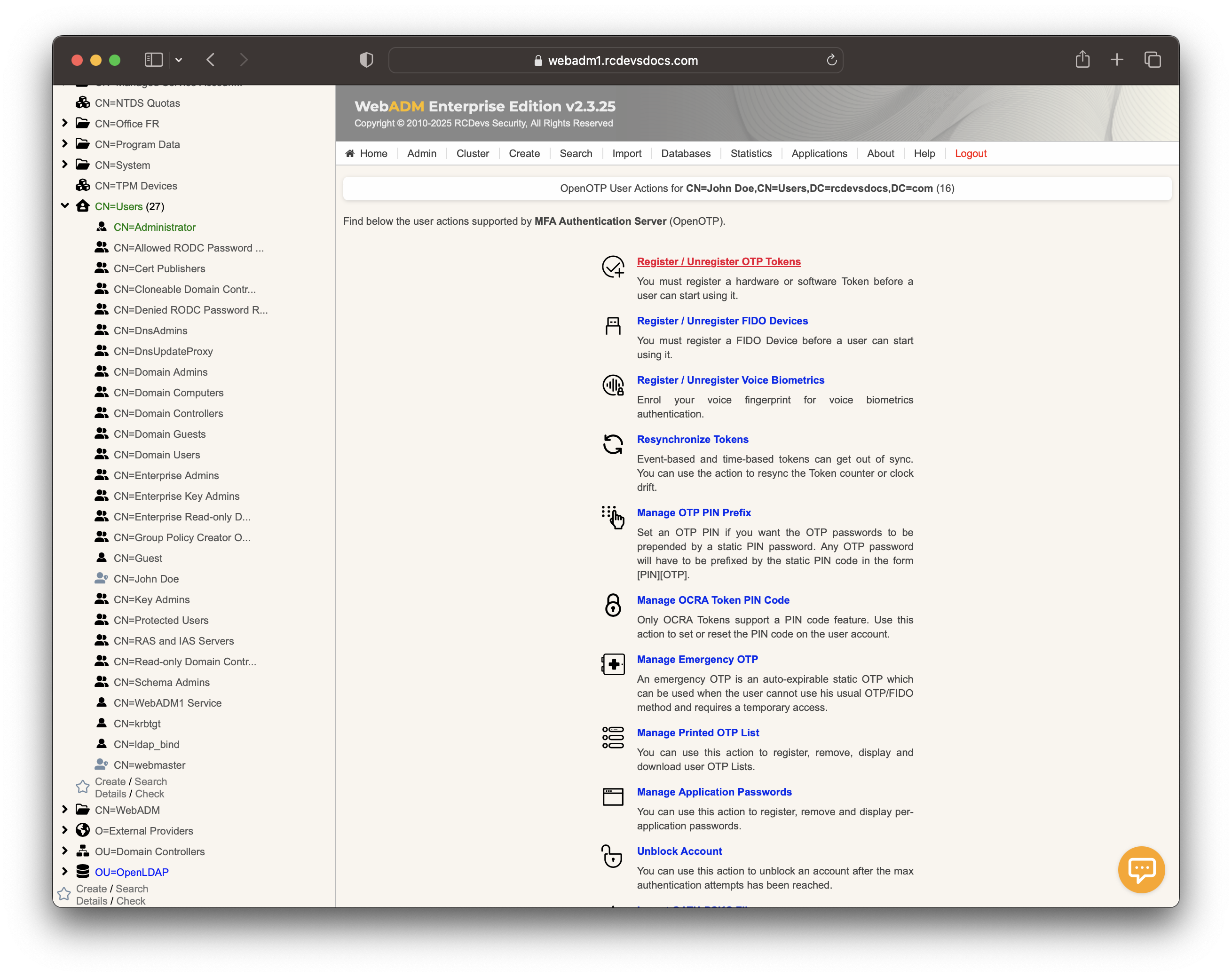
Click on MFA Authentication Server under the Application Actions box, then select Register/Unregister OTP Tokens.
Register your token, select Primary Token, and check the box I use a Yubikey Token.
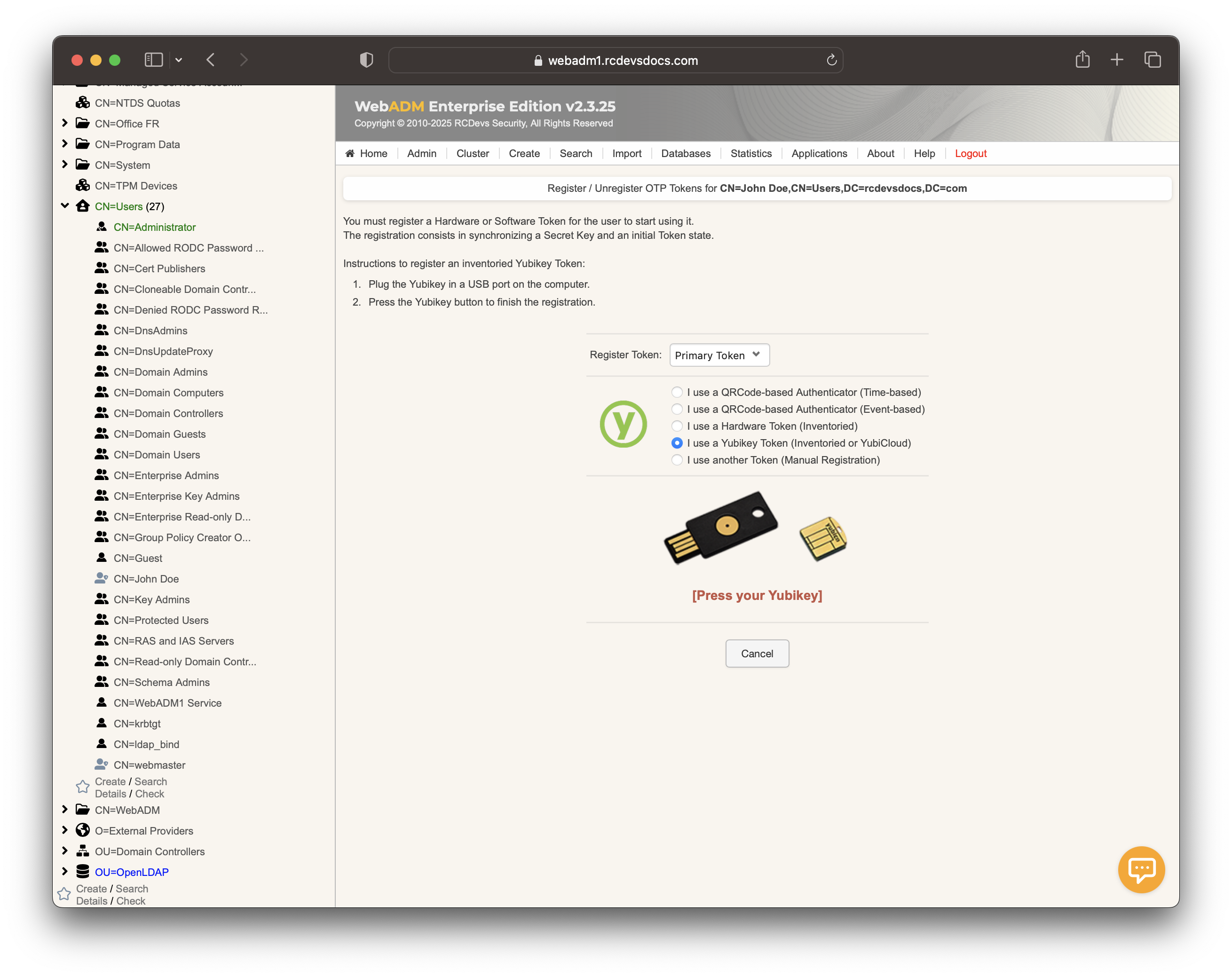
At this step, simply perform a short touch on your YubiKey to select Slot 1 and enroll it to the user account.
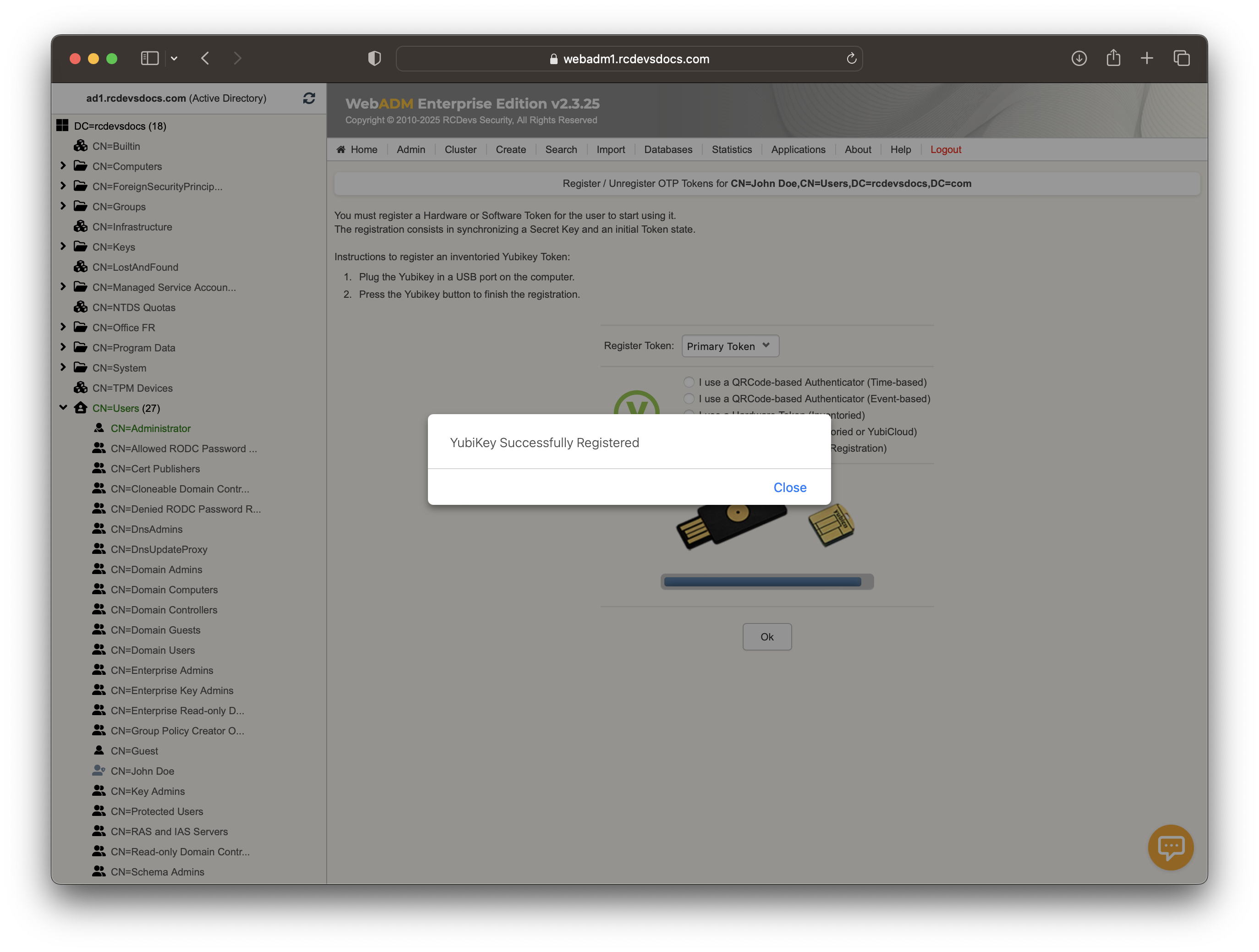
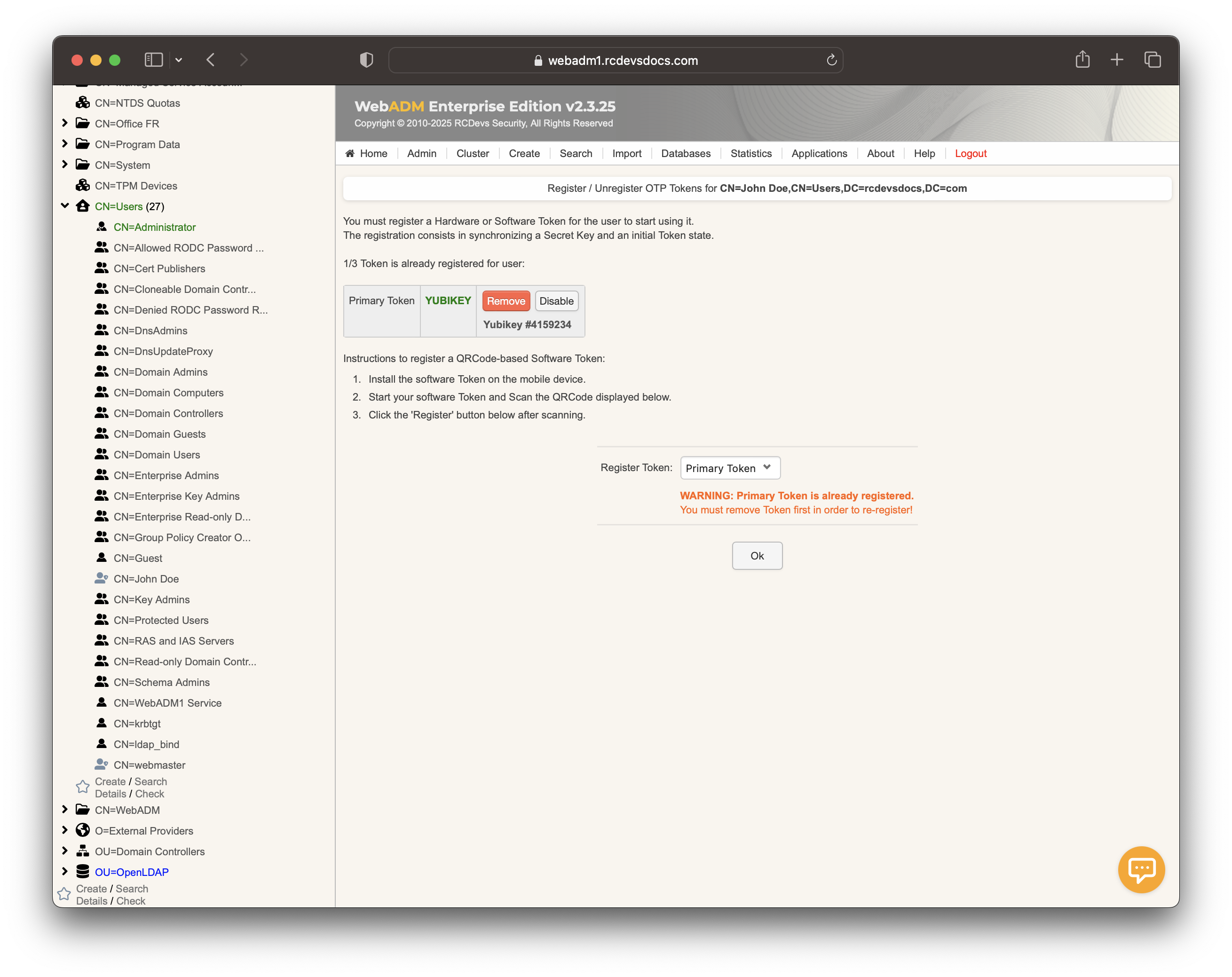
The YubiKey is now correctly assigned to the user account. If you return to the Databases tab and select Inventoried OTP Tokens, you will see a link between the YubiKey database entry and the LDAP user.
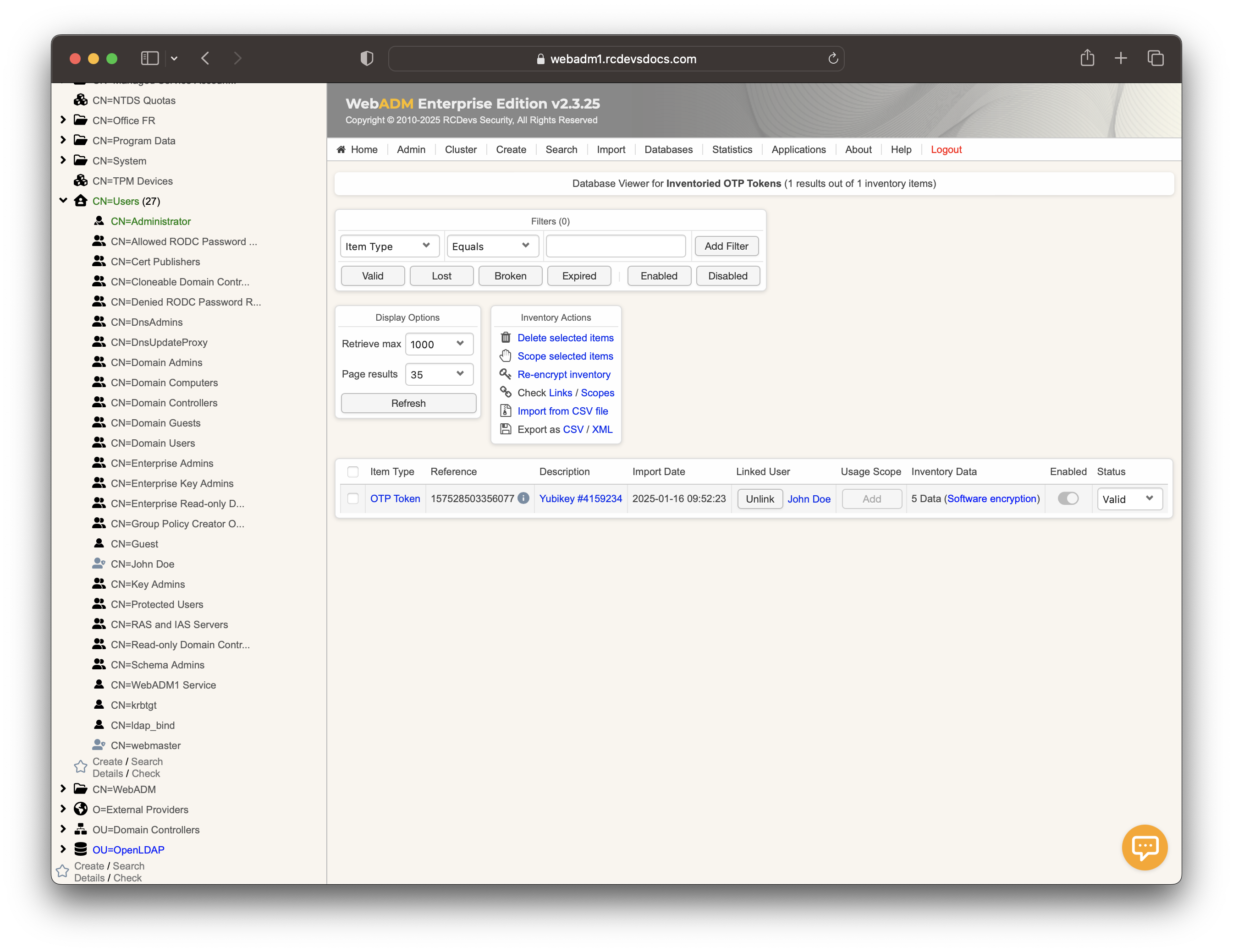
A YubiKey can be assigned to multiple users, but to do so, you must first remove the User DN link in the database from the YubiKey entry. Removing the link between the YubiKey and the user does not remove the YubiKey from the user account. The first user who enrolled the YubiKey will always be able to use it to log in.
Validation with Yubicloud
Yubicloud validation server config in OpenOTP
First, if you need to reprogram your YubiKey, you will need to register it on a YubiCloud server. You can do this on their public server using the following URL: https://upload.yubico.com/. Use the CSV file generated in the previous Inventory generation section of this documentation. Note that by default, the keys are already programmed with the YubiCloud validation servers.
Next, you will need to obtain a YubiCloud Client ID and a YubiCloud Secret Key from this URL: https://upgrade.yubico.com/getapikey/.
Once you have this information, log in to your WebADM GUI, go to the Applications tab, and click on Configure for the MFA Authentication Server (OpenOTP). In the YubiKey Tokens section, enable YubiCloud and enter the values for the Client ID and the Secret Key.
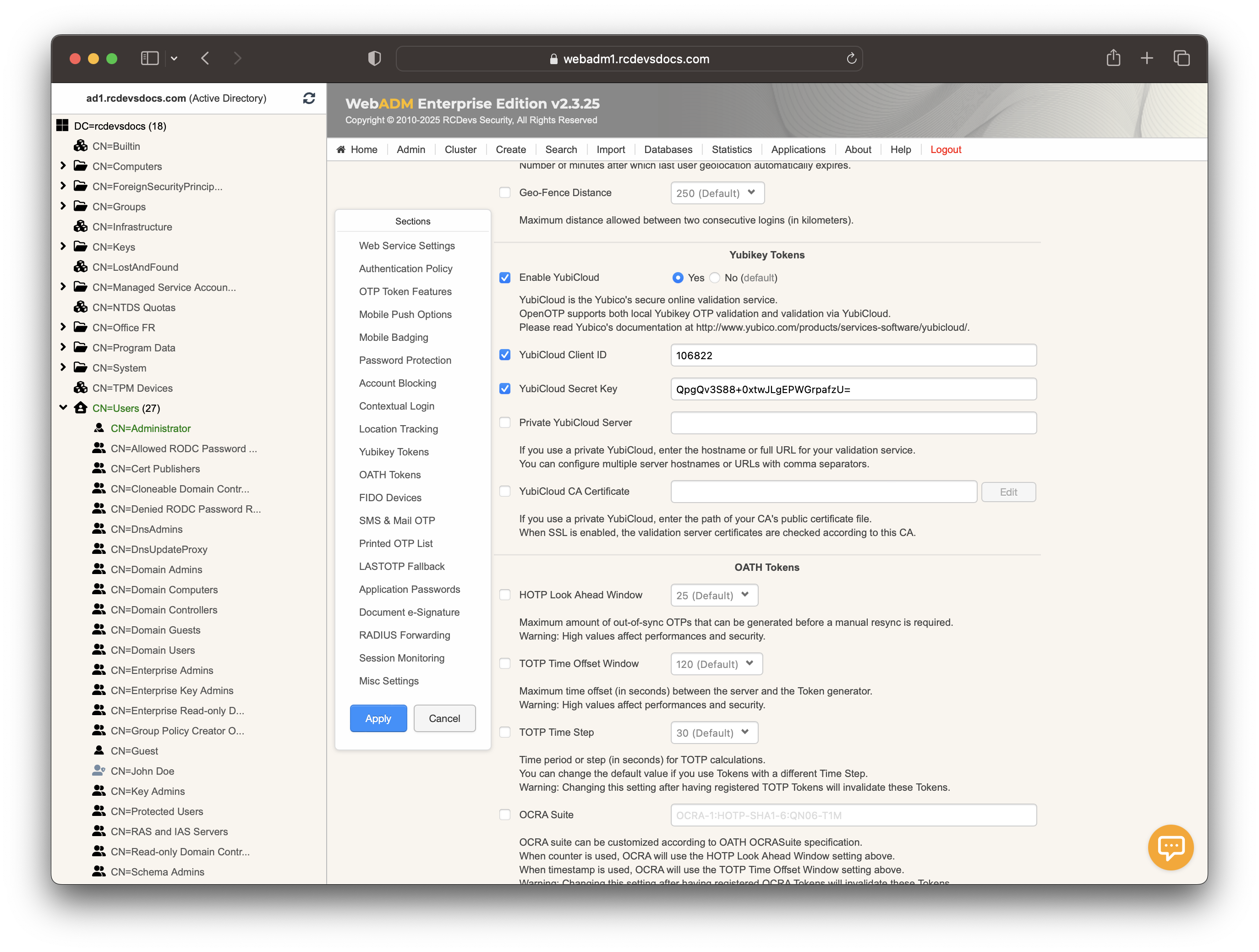
You can apply these settings.
User Registration
Once the previous configuration is complete, go to the user for whom you want to register the YubiKey. Click on MFA Authentication Server in the Application Actions box for the user, then select Register/Unregister OTP Tokens. Choose an available token slot before selecting the YubiKey token.

Press your Yubikey as asked and it will be enrolled on this user.
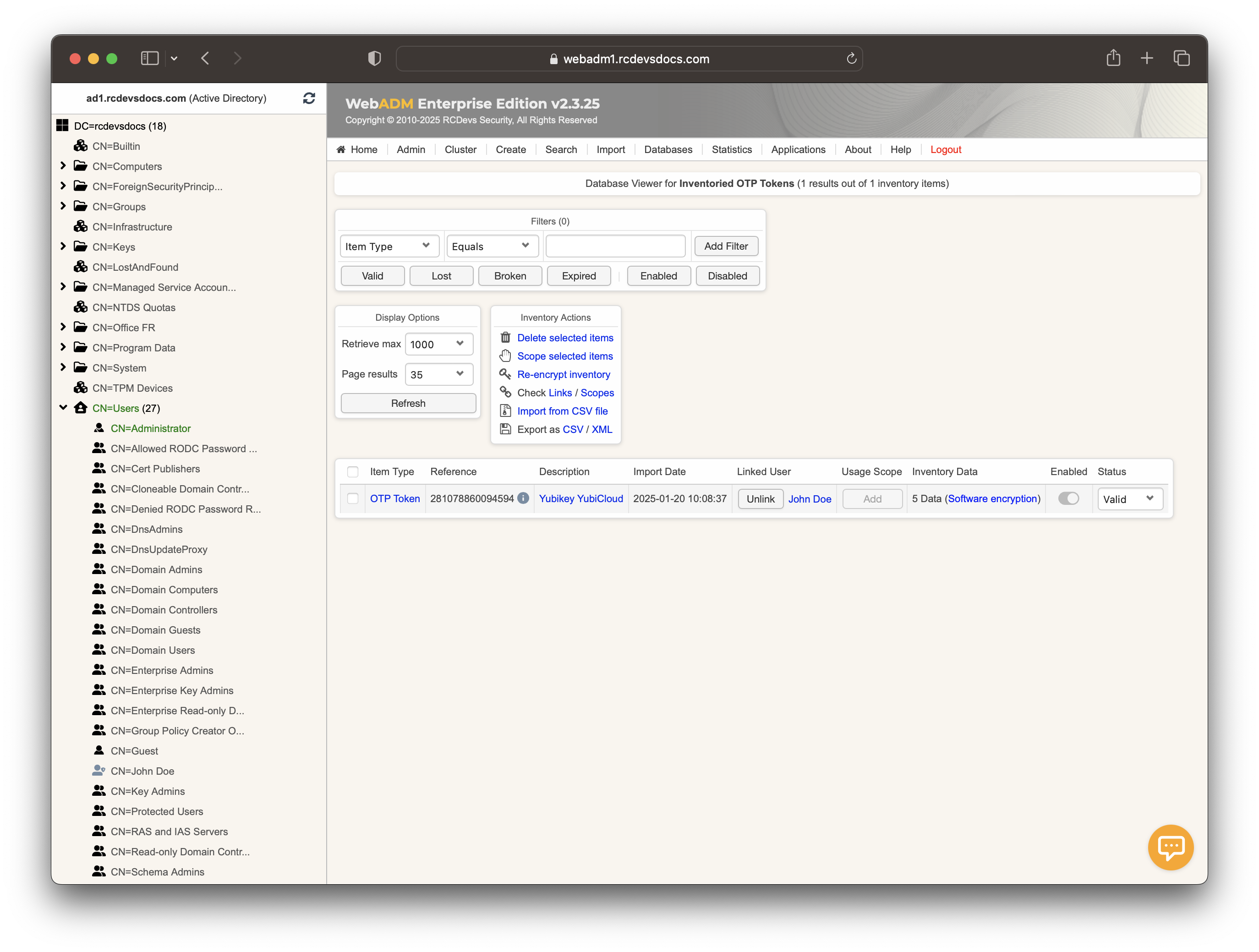
You can check in the Databases tab, Inventoried OTP Tokens section, that this key is enrolled as a YubiKey Yubicloud.
User Authentication
Logs when validated by Yubicloud
We can now test user authentication with YubiCloud by returning to the MFA Authentication Server in the Application Actions box for the user and clicking on Test OTP & FIDO Authentication.
Enter the LDAP password in the corresponding field before clicking the Start button if LDAP authentication is required, or select a policy you would like to test with the YubiKeys.
Then, place the cursor in the OTP password field and perform a short touch on your YubiKey to activate Slot 1.
Then, go to the Databases tab and navigate to the WebADM Server Log File section to view the logs corresponding to the authentication we just performed.
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] New openotpNormalLogin SOAP request
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > Username: john.doe
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > Domain: rcdevsdocs
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > LDAP Password: xxxxxxxxxxxx
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > Client ID: OpenOTP
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > Source IP: 192.168.3.217
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] > Context: bc7a98e8114eb99d2cde9823883ecc17
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Registered openotpNormalLogin request
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com (cached)
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Resolved LDAP groups: IT,Enterprise Admins (cached)
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Started transaction lock for user
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found user language: EN
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found 1 user mobiles: +33612345678
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found 1 user emails: john.doe@rcdevsdocs.com
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found 52 user settings: LoginMode=LDAPOTP,OTPType=TOKEN,PushLogin=Yes,ChallengeMode=Yes,ChallengeTimeout=90,OTPLength=6,OfflineExpire=30,MobileTimeout=30,EnableLogin=Yes,HOTPLookAheadWindow=25,TOTPTimeStep=30,TOTPTimeOffsetWindow=120,OCRASuite=OCRA-1:HOTP-SHA1-6:QN06-T1M,U2FPINMode=Discouraged,SMSType=Normal,SMSMode=Ondemand,MailMode=Ondemand,PrefetchExpire=10,LastOTPTime=300,ListChallengeMode=ShowID
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found 13 user data: ListInit,ListState,AppKeyInit,LastOTP,Device1Type,Device1Name,Device1Data,Device1State,TokenType,TokenKey,TokenState,TokenID,TokenSerial
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Last OTP present (valid until 2025-01-24 09:55:34)
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] OTP List present (0/50 passwords used)
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Found 1 registered OTP token (YUBIKEY)
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Requested login factors: LDAP & OTP
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] LDAP password Ok
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Authentication challenge required
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Started OTP authentication session of ID gFLykyAF2CSqMn1X valid for 90 seconds
[2025-01-24 09:51:15] [127.0.0.1:57976] [OpenOTP:PMO13QIW] Sent login challenge response
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] New openotpChallenge SOAP request
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] > Username: john.doe
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] > Domain: rcdevsdocs
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] > Session: gFLykyAF2CSqMn1X
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] > OTP Password: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Found authentication session started 2025-01-24 09:51:15
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Started transaction lock for user
[2025-01-24 09:51:21] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Sending YubiCloud validation request to 5 servers
[2025-01-24 09:51:22] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Received accept response from YubiCloud server api.yubico.com
[2025-01-24 09:51:26] [127.0.0.1:57980] [OpenOTP:PMO13QIW] YUBIKEY password Ok (token #1)
[2025-01-24 09:51:26] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Updated user data
[2025-01-24 09:51:26] [127.0.0.1:57980] [OpenOTP:PMO13QIW] Sent login success response
Logs when locally validated by OpenOTP
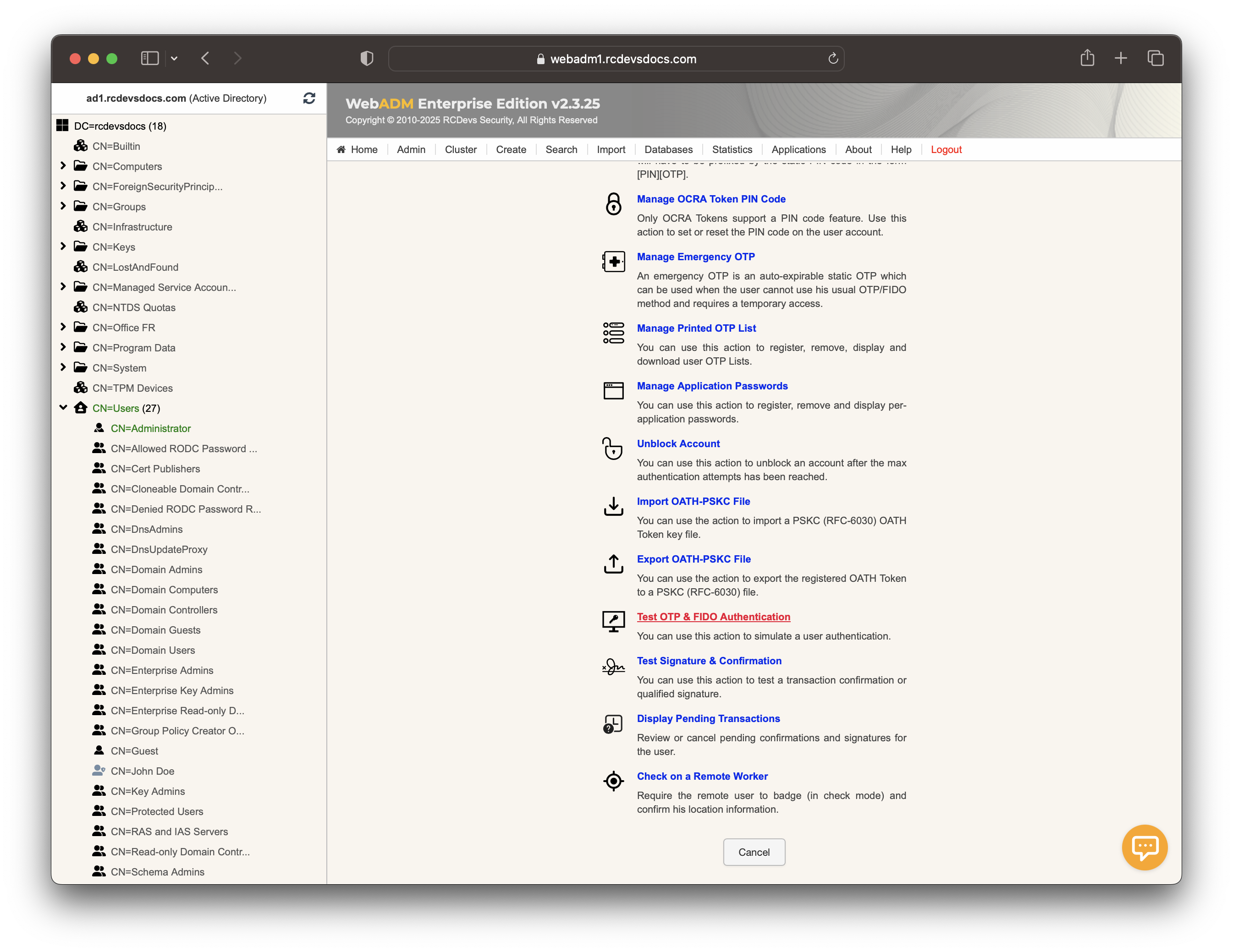
Let's test user authentication with OpenOTP. Return to the MFA Authentication Server in the Application Actions box for the user and click the Test OTP & FIDO Authentication action.

Enter the LDAP password in the corresponding field before clicking the Start button if LDAP authentication is required, or select a policy you would like to test with the YubiKeys.

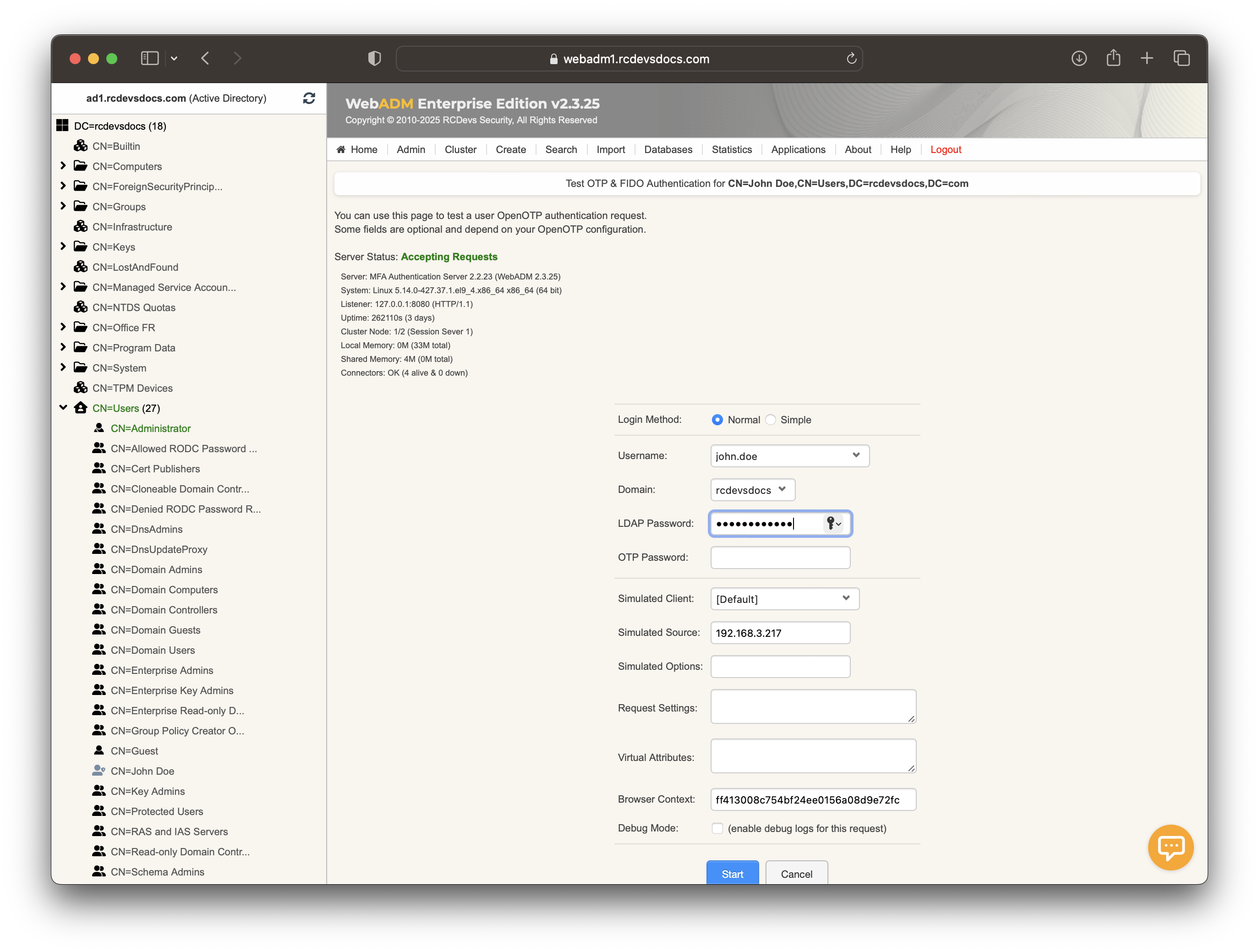
Then put the cursor in the OTP password field and short touch your Yubikey for activating Slot 1.


Then, go to the Databases tab and navigate to the WebADM Server Log File section to view the logs corresponding to the authentication we just performed.
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] New openotpNormalLogin SOAP request
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > Username: john.doe
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > Domain: rcdevsdocs
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > LDAP Password: xxxxxxxxxxxx
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > Client ID: OpenOTP
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > Source IP: 192.168.3.217
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] > Context: e4b8befbff2104f67155f1bd962c7f94
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Registered openotpNormalLogin request
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Resolved LDAP groups: IT,Enterprise Admins
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Started transaction lock for user
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found user language: EN
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found 1 user mobiles: +33612345678
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found 1 user emails: john.doe@rcdevsdocs.com
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found 52 user settings: LoginMode=LDAPOTP,OTPType=TOKEN,PushLogin=Yes,ChallengeMode=Yes,ChallengeTimeout=90,OTPLength=6,OfflineExpire=30,MobileTimeout=30,EnableLogin=Yes,HOTPLookAheadWindow=25,TOTPTimeStep=30,TOTPTimeOffsetWindow=120,OCRASuite=OCRA-1:HOTP-SHA1-6:QN06-T1M,U2FPINMode=Discouraged,SMSType=Normal,SMSMode=Ondemand,MailMode=Ondemand,PrefetchExpire=10,LastOTPTime=300,ListChallengeMode=ShowID
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found 13 user data: ListInit,ListState,AppKeyInit,LastOTP,Device1Type,Device1Name,Device1Data,Device1State,TokenType,TokenKey,TokenState,TokenID,TokenSerial
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Last OTP expired 2025-01-16 11:10:42
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] OTP List present (0/50 passwords used)
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Found 1 registered OTP token (YUBIKEY)
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Requested login factors: LDAP & OTP
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] LDAP password Ok
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Authentication challenge required
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Updated user data
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Started OTP authentication session of ID J2QBq3NqV82h6jL7 valid for 90 seconds
[2025-01-16 11:12:39] [127.0.0.1:43706] [OpenOTP:8B7HX5AJ] Sent login challenge response
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] New openotpChallenge SOAP request
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] > Username: john.doe
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] > Domain: rcdevsdocs
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] > Session: J2QBq3NqV82h6jL7
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] > OTP Password: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] Found authentication session started 2025-01-16 11:12:39
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] Started transaction lock for user
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] YUBIKEY password Ok (token #1)
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] Updated user data
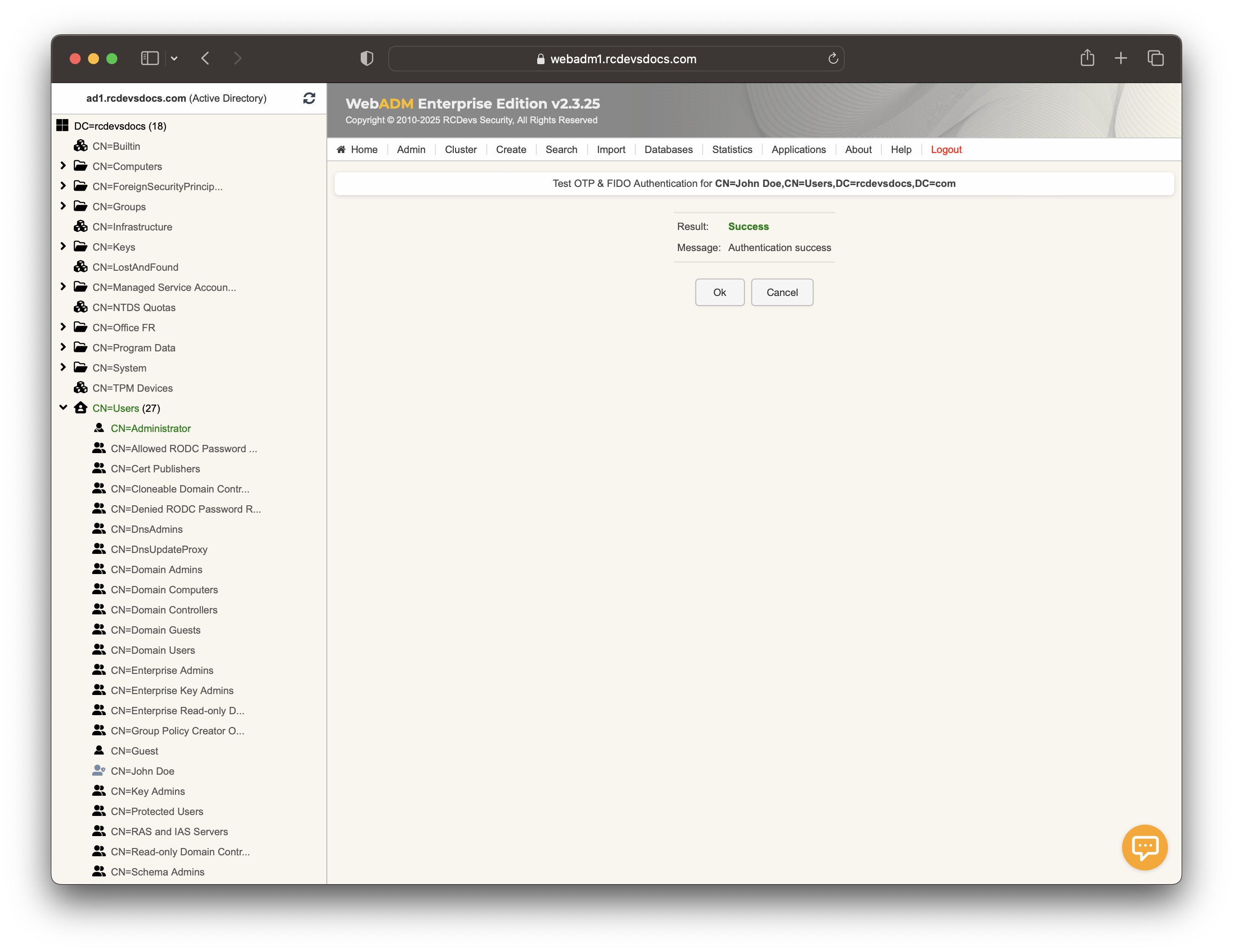
[2025-01-16 11:12:59] [127.0.0.1:59728] [OpenOTP:8B7HX5AJ] Sent login success response
Yubico OATH-HOTP
Program the key
Instead of generating a 44-character key when you press the YubiKey, you can configure it to generate a 6 or 8-digit OTP code.
First, you need to edit some settings in the YubiKey Personalization Tool. Go to the Settings tab and select Log configuration output: Yubico format as shown below:

Now, we will reprogram the YubiKey. Switch to the OATH-HOTP tab and select Advanced configuration. Choose Configuration Slot 2, and disable the option OATH Token Identifier (6 bytes) as shown below:
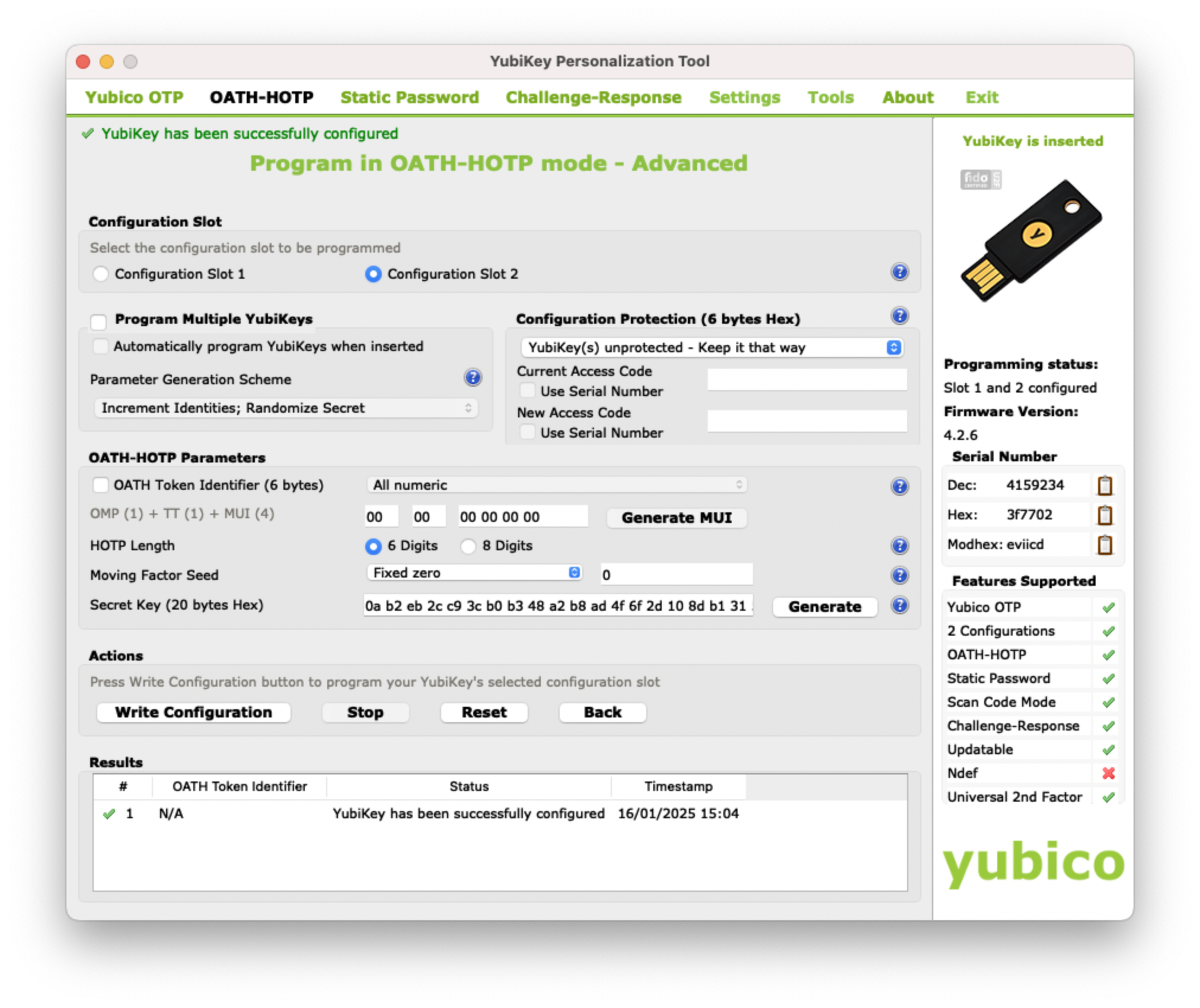
Plug in your YubiKey and click on the Generate buttons. Then, click on the Write Configuration button, and you should be prompted to save the inventory file. At this step, your YubiKey should generate a 6 or 8-digit OTP code when you perform a long touch. If this does not happen, there is no point in proceeding with the next steps.
Import it in WebADM
We have now reprogrammed our YubiKey and generated an inventory for it. Next, we will import the inventory file into WebADM to enable the use of this YubiKey within the WebADM/OpenOTP ecosystem.
Now, go to the WebADM Admin GUI and click on the Import tab.

On that page, click the Import Inventory File button.

In the Type of File dropdown, select Yubico CSV and browse for the inventory file you previously created using the YubiKey Personalization Tool.
Click the Import button, and the YubiKey should be successfully imported.

You can check the inventory table to see the new entry. Click on the Databases tab and then select Inventoried OTP Tokens. You should see the new entry listed below.
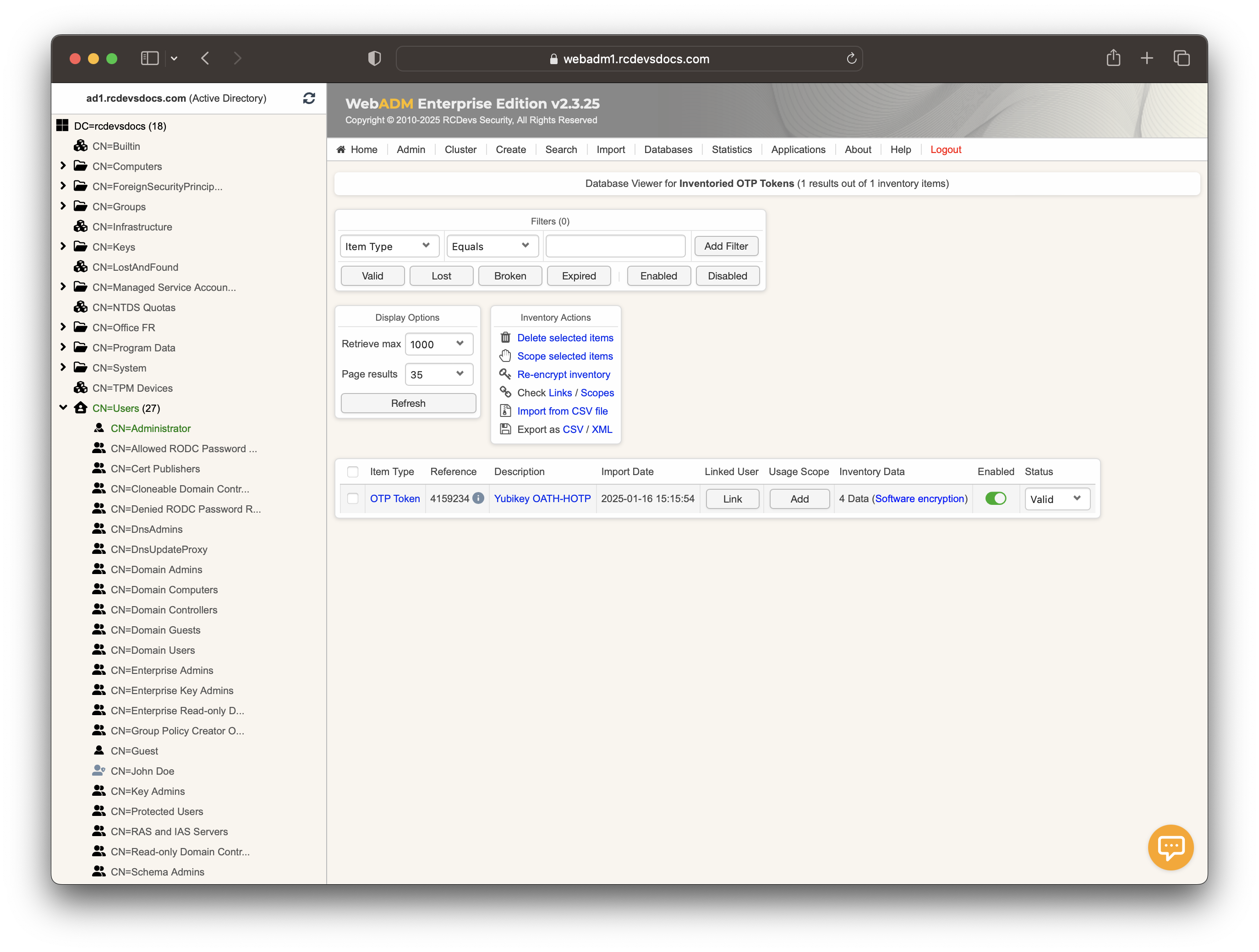
I am now able to assign this YubiKey to a user account. This step will be covered in the next section.
User Registration
We will now assign this HOTP YubiKey to a user account through the WebADM Admin GUI. To assign the YubiKey, you will need its Reference, which is registered under the Databases tab in Inventoried OTP Tokens.

On my side, the reference is 4159234.
Now, click on a user account in the left tree, go to MFA Authentication Server, and select Register/Unregister OTP Tokens. Choose the option I use a Hardware Token (Inventoried). In the Token Serial field, enter the reference you previously copied.
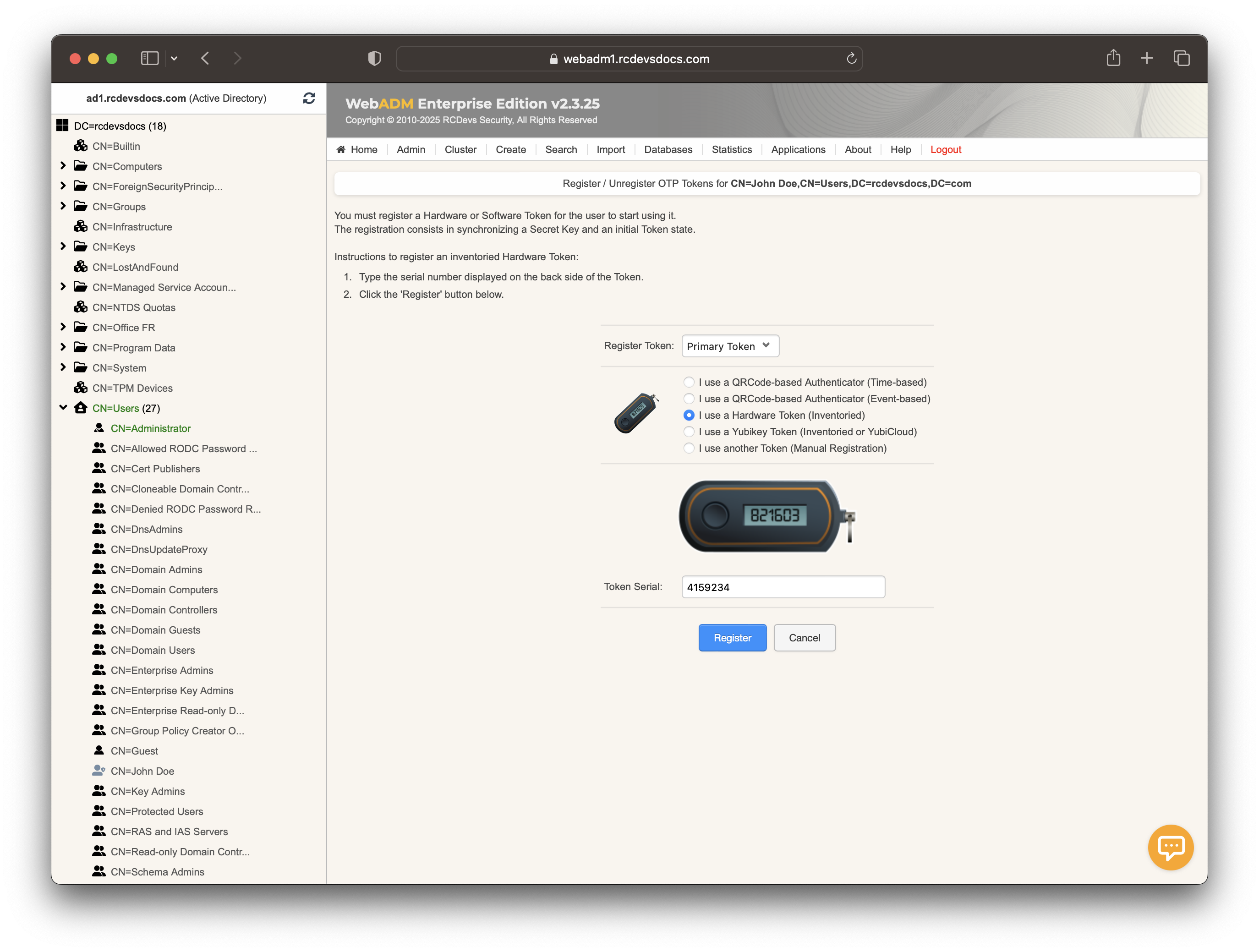
Click on Register, and the YubiKey will now be enrolled on your account.
If you are using an 8-digit OTP length, the OTP length in OpenOTP must be reconfigured.
-
It can be reconfigured at the OpenOTP default configuration level. Be cautious, as this will invalidate any 6-digit OTPs that have already been registered across all accounts.
-
Alternatively, the OTP length can be configured at the user level, which will not impact other users' tokens that are registered in 6-digit mode. However, if any 6-digit tokens have already been registered on the user's account where the setting is changed, they will be invalidated.
Test Authentication
Let's test the user authentication with this new token. Return to the MFA Authentication Server in the Application Actions box for the user and click the Test User Authentication action.

Enter the LDAP password in the corresponding field before clicking the Start button if LDAP authentication is required, or select a policy you would like to test with the YubiKeys.

Then place the cursor in the OTP password field and perform a long touch on your YubiKey to activate Slot 2.


Then you can go to Databases tab and to the WebADM Server Log File section so that you can see the logs corresponding to the authentication we just did.
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] New openotpNormalLogin SOAP request
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > Username: john.doe
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > Domain: rcdevsdocs
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > LDAP Password: xxxxxxxxxxxx
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > Client ID: OpenOTP
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > Source IP: 192.168.3.217
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] > Context: 14260a3ce73b4a7b46949983c70612d4
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Registered openotpNormalLogin request
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com (cached)
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Resolved LDAP groups: IT,Enterprise Admins (cached)
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Started transaction lock for user
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found user language: EN
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found 1 user mobiles: +33612345678
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found 1 user emails: john.doe@rcdevsdocs.com
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found 52 user settings: LoginMode=LDAPOTP,OTPType=TOKEN,PushLogin=Yes,ChallengeMode=Yes,ChallengeTimeout=90,OTPLength=6,OfflineExpire=30,MobileTimeout=30,EnableLogin=Yes,HOTPLookAheadWindow=25,TOTPTimeStep=30,TOTPTimeOffsetWindow=120,OCRASuite=OCRA-1:HOTP-SHA1-6:QN06-T1M,U2FPINMode=Discouraged,SMSType=Normal,SMSMode=Ondemand,MailMode=Ondemand,PrefetchExpire=10,LastOTPTime=300,ListChallengeMode=ShowID
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found 11 user data: ListInit,ListState,AppKeyInit,Device1Type,Device1Name,Device1Data,Device1State,TokenType,TokenKey,TokenState,TokenSerial
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] OTP List present (0/50 passwords used)
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Found 1 registered OTP token (HOTP)
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Requested login factors: LDAP & OTP
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] LDAP password Ok
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Authentication challenge required
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Started OTP authentication session of ID LZJ0SLEjPLjRNcxh valid for 90 seconds
[2025-01-16 15:20:58] [127.0.0.1:53992] [OpenOTP:WR600CKY] Sent login challenge response
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] New openotpChallenge SOAP request
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] > Username: john.doe
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] > Domain: rcdevsdocs
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] > Session: LZJ0SLEjPLjRNcxh
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] > OTP Password: xxxxxx
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] Found authentication session started 2025-01-16 15:20:58
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] Started transaction lock for user
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] HOTP password Ok (token #1)
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] Updated user data
[2025-01-16 15:21:04] [127.0.0.1:54004] [OpenOTP:WR600CKY] Sent login success response
FIDO
It is also possible to register the YubiKey as a FIDO device through WebADM. You can follow our documentation to know how to enroll it and then use it through authentications. It will just be required to tap it when asked.
Please refer to our FIDO documentation
PIV/Smartcard
For this step, we’ll need to use a different tool than the one previously mentioned in this documentation. Specifically, you’ll need to install the YubiKey Manager software, which will allow us to complete the procedure.
Generate a P12 certificate bundle through the WebADM Administrator portal Helpdesk portal or the Self-Service portal.
Download the P12 file and copy its associated password—you’ll need it later to import the certificate onto the smartcard.
Refer to the following documentations for instructions on issuing your certificate from the different interfaces and make sure to check the Microsoft Smartcard Login box before issuing the certificate.
From WebADM Admin GUI:
From Helpdesk Portal:
From User Self-Service Desk Portal:
Once you have your PKCS12 bundle, you can import it using the YubiKey Manager software by navigating to the Applications tab and opening the PIV page.
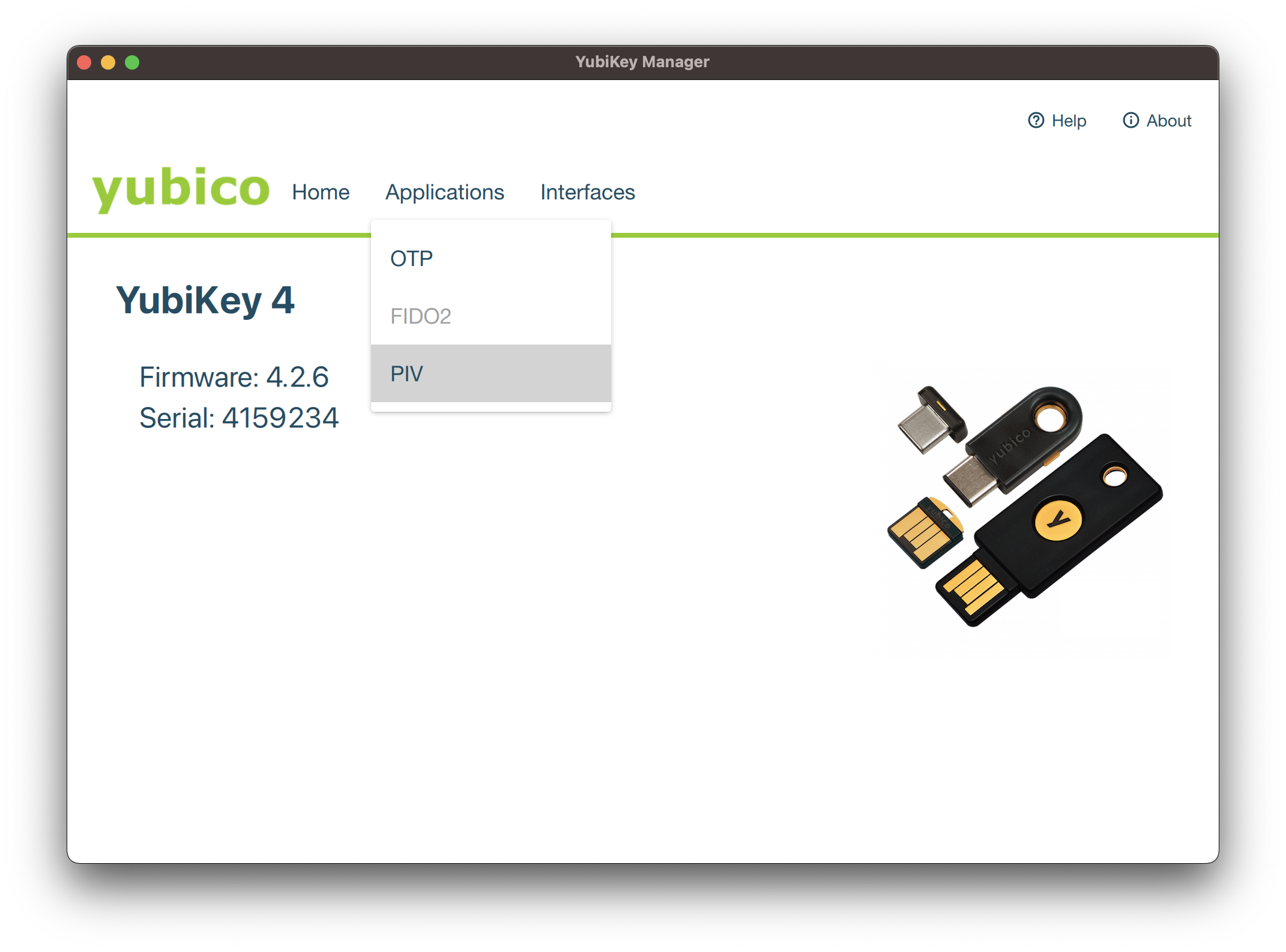
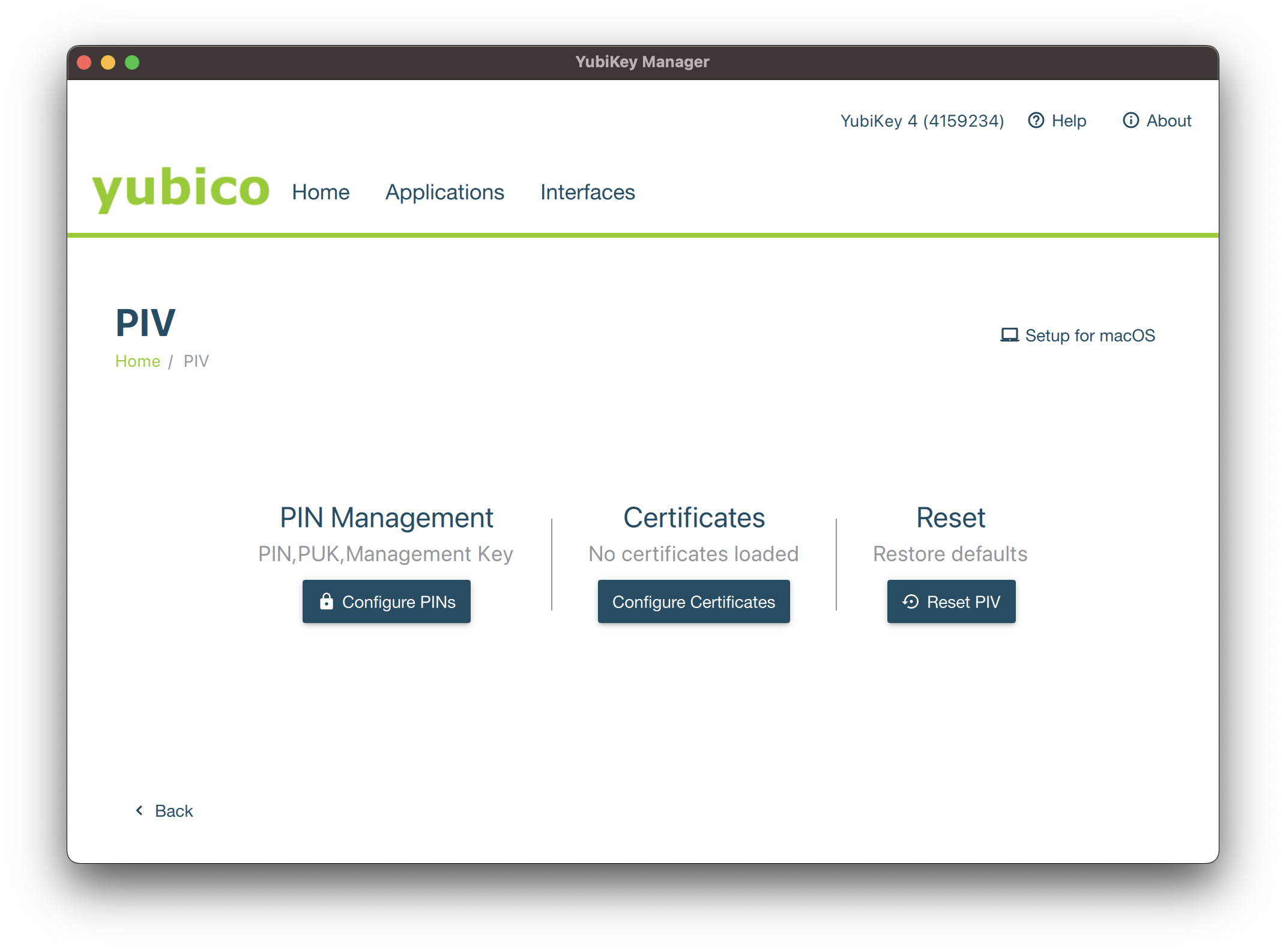
Click on Configure Certificates and then on Import.
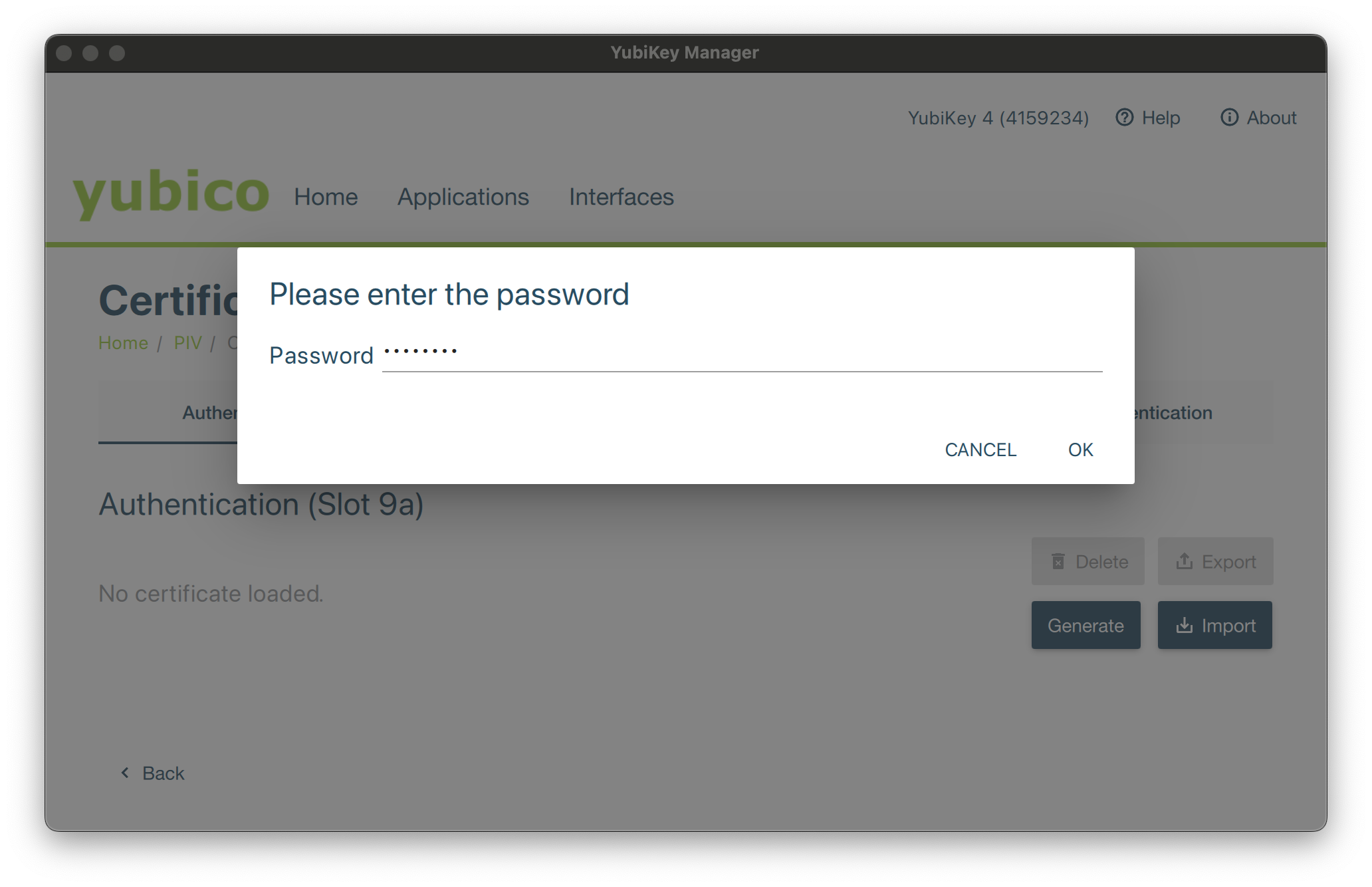
Browse to your P12 bundle in your file system. You will be prompted to enter the password protecting the P12, followed by the Smartcard PIN.
The P12 should now be successfully imported.
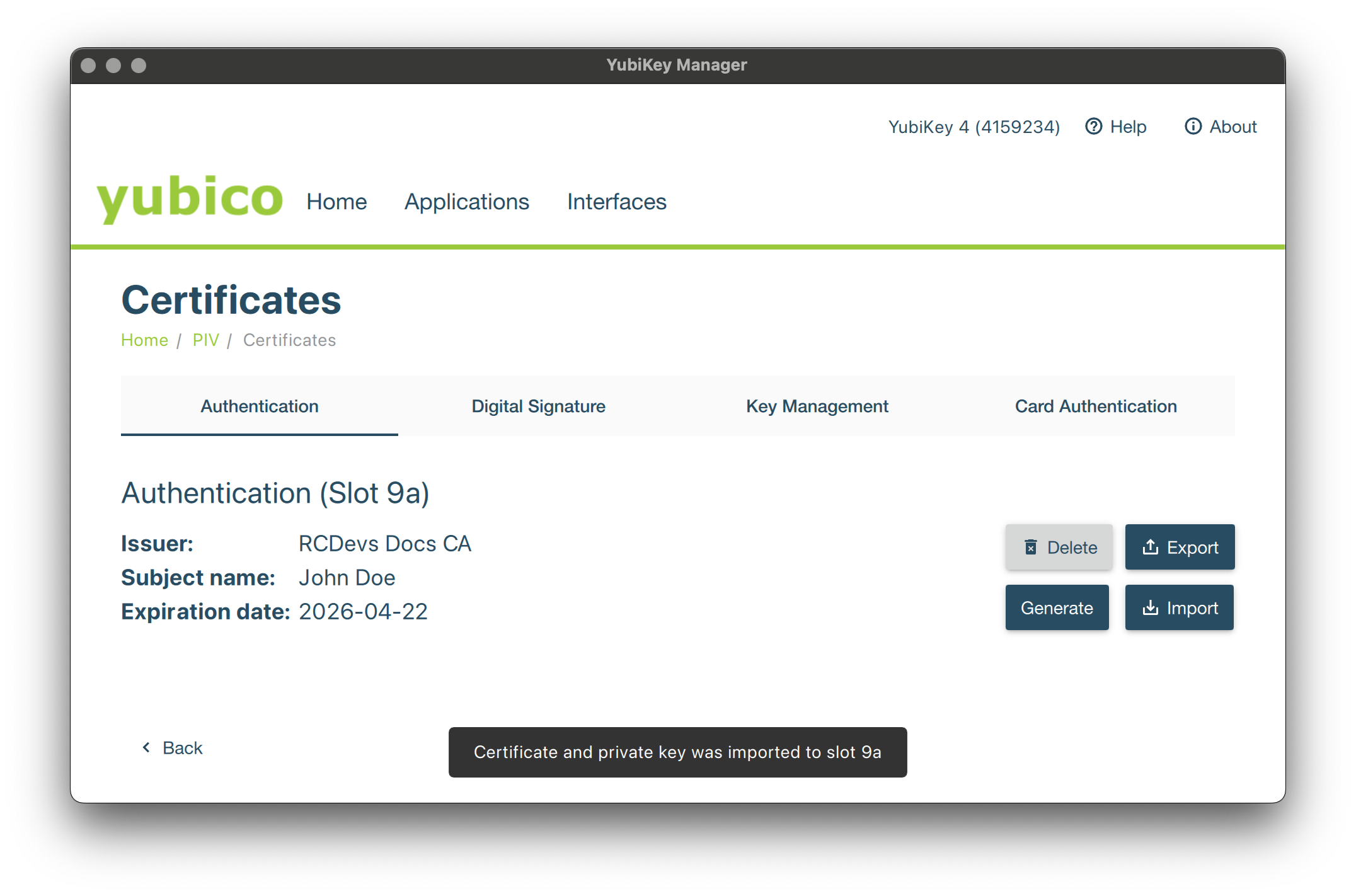
The smartcard can now be used with OpenOTP and supported integrations, such as Windows login through the OpenOTP Smartcard Provider.
Refer to Smartcard Provider for Windows documentation for more information.
