Actions overview
The WebADM installation consists of:
- Download the packages;
- Install the packages;
- Choosing your WebADM PKI setup;
- Choosing your main LDAP identity source;
- Choosing your SQL DBMS;
- Setup your DBMS;
- Run the WebADM setup script as primary node;
- Start the WebADM services and log in to the WebADM Administrator portal.
- Finishing the setup graphically;
The previously listed actions will provide a standalone installation of the WebADM server. If you want to set up WebADM in cluster mode, follow the WebADM Cluster and Failover Setup Guide, which is a continuation of this documentation.
Architecture overview
Below are the DNS names and IP addresses to be used in the standalone and HA guides:
| Details | Hostnames | IP Addresses |
|---|---|---|
| WebADM Server 1 | webadm1.rcdevsdocs.com | 192.168.4.160/24 |
| WebADM Server 2 | webadm2.rcdevsdocs.com | 192.168.4.161/24 |
| SQL Server 1 | webadm1.rcdevsdocs.com | 192.168.4.160/24 |
| SQL Server 2 | webadm2.rcdevsdocs.com | 192.168.4.161/24 |
| Session Server 1 | webadm1.rcdevsdocs.com | 192.168.4.160/24 |
| Session Server 2 | webadm2.rcdevsdocs.com | 192.168.4.161/24 |
| PKI Server 1 | webadm1.rcdevsdocs.com | 192.168.4.160/24 |
| PKI Server 2 | webadm2.rcdevsdocs.com | 192.168.4.161/24 |
| Active Directory DC 1 | ad1.rcdevsdocs.com | 192.168.4.163/24 |
| Active Directory DC 2 | ad2.rcdevsdocs.com | 192.168.4.164/24 |
| WAProxy Server 1 | waproxy1.rcdevsdocs.com | 172.16.0.10/24 |
| WAProxy Server 2 | waproxy2.rcdevsdocs.com | 172.16.0.11/24 |
| Proxy Server 1 | proxy1.rcdevsdocs.com | 172.16.0.12/24 |
| Proxy Server 2 | proxy2.rcdevsdocs.com | 172.16.0.13/24 |
| SMTP Cluster | mail.rcdevs.com | 146.59.204.189 |
Downloading packages
The self-installer package can be downloaded from the RCDevs website in the Download section. Download the webadm_all_in_one package.
If you are using an RPM/Debian repository, the download will be done using the apt install or dnf install command, depending on your distribution.
Packages Installation
Through Repositories
After repository configuration you can execute the following command install WebADM and its dependencies.
RPM repository
[root@webadm1 ~]# dnf install webadm_all_in_one -y
Debian repository
[root@webadm1 ~]# apt install webadm-all-in-one -y
Output:
RCDevs Enterprise Linux Repository 16 kB/s | 171 kB 00:10
Dependencies resolved.
===========================================================================================================================================================================
Package Architecture Version Repository Size
===========================================================================================================================================================================
Installing:
webadm_all_in_one noarch 1.0.1-0 rcdevs 2.0 k
Installing dependencies:
openid noarch 1.6.4-2 rcdevs 11 M
openotp noarch 2.2.17-1 rcdevs 14 M
pwreset noarch 1.3.4-2 rcdevs 1.3 M
selfdesk noarch 1.4.4-3 rcdevs 2.5 M
selfreg noarch 1.4.2-3 rcdevs 4.2 M
smshub noarch 1.3.1-1 rcdevs 1.5 M
spankey noarch 2.1.4-2 rcdevs 13 M
webadm x86_64 2.3.17-3 rcdevs 156 M
Transaction Summary
===========================================================================================================================================================================
Install 9 Packages
Total download size: 203 M
Installed size: 382 M
Downloading Packages:
(1/9): pwreset-1.3.4-2.noarch.rpm 244 kB/s | 1.3 MB 00:05
(2/9): openid-1.6.4-2.noarch.rpm 1.9 MB/s | 11 MB 00:05
(3/9): selfdesk-1.4.4-3.noarch.rpm 10 MB/s | 2.5 MB 00:00
(4/9): selfreg-1.4.2-3.noarch.rpm 29 MB/s | 4.2 MB 00:00
(5/9): smshub-1.3.1-1.noarch.rpm 8.2 MB/s | 1.5 MB 00:00
(6/9): openotp-2.2.17-1.noarch.rpm 2.2 MB/s | 14 MB 00:06
(7/9): webadm_all_in_one-1.0.1-0.noarch.rpm 20 kB/s | 2.0 kB 00:00
(8/9): spankey-2.1.4-2.noarch.rpm 14 MB/s | 13 MB 00:00
(9/9): webadm-2.3.17-3.x86_64.rpm 28 MB/s | 156 MB 00:05
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 18 MB/s | 203 MB 00:11
Running transaction check
Transaction check succeeded.
Running transaction test
Transaction test succeeded.
Running transaction
Preparing : 1/1
Running scriptlet: webadm-2.3.17-3.x86_64 1/9
Installing : webadm-2.3.17-3.x86_64 1/9
Running scriptlet: webadm-2.3.17-3.x86_64 1/9
Please run /opt/webadm/bin/setup.
Running scriptlet: openid-1.6.4-2.noarch 2/9
Installing : openid-1.6.4-2.noarch 2/9
Running scriptlet: openid-1.6.4-2.noarch 2/9
Running scriptlet: openotp-2.2.17-1.noarch 3/9
Installing : openotp-2.2.17-1.noarch 3/9
Running scriptlet: openotp-2.2.17-1.noarch 3/9
Running scriptlet: pwreset-1.3.4-2.noarch 4/9
Installing : pwreset-1.3.4-2.noarch 4/9
Running scriptlet: pwreset-1.3.4-2.noarch 4/9
Running scriptlet: selfdesk-1.4.4-3.noarch 5/9
Installing : selfdesk-1.4.4-3.noarch 5/9
Running scriptlet: selfdesk-1.4.4-3.noarch 5/9
Running scriptlet: selfreg-1.4.2-3.noarch 6/9
Installing : selfreg-1.4.2-3.noarch 6/9
Running scriptlet: selfreg-1.4.2-3.noarch 6/9
Running scriptlet: smshub-1.3.1-1.noarch 7/9
Installing : smshub-1.3.1-1.noarch 7/9
Running scriptlet: smshub-1.3.1-1.noarch 7/9
Running scriptlet: spankey-2.1.4-2.noarch 8/9
Installing : spankey-2.1.4-2.noarch 8/9
Running scriptlet: spankey-2.1.4-2.noarch 8/9
Installing : webadm_all_in_one-1.0.1-0.noarch 9/9
Verifying : openid-1.6.4-2.noarch 1/9
Verifying : openotp-2.2.17-1.noarch 2/9
Verifying : pwreset-1.3.4-2.noarch 3/9
Verifying : selfdesk-1.4.4-3.noarch 4/9
Verifying : selfreg-1.4.2-3.noarch 5/9
Verifying : smshub-1.3.1-1.noarch 6/9
Verifying : spankey-2.1.4-2.noarch 7/9
Verifying : webadm-2.3.17-3.x86_64 8/9
Verifying : webadm_all_in_one-1.0.1-0.noarch 9/9
Installed:
openid-1.6.4-2.noarch openotp-2.2.17-1.noarch pwreset-1.3.4-2.noarch selfdesk-1.4.4-3.noarch selfreg-1.4.2-3.noarch smshub-1.3.1-1.noarch
spankey-2.1.4-2.noarch webadm-2.3.17-3.x86_64 webadm_all_in_one-1.0.1-0.noarch
Complete!
All the listed packages above have been installed successfully. You can continue with the WebADM setup script.
Using the Self-Installer
You first need to download and install the WebADM all-in-one software package. You can download the latest package on the RCDevs Website. Download and copy the WebADM-all-in-one self-installer package to your server.
You can copy the downloaded package to the server with WinSCP or SCP.
Then connect via SSH to your server, uncompress and run the self-installer package with:
[root@webadm1 tmp]# gunzip webadm-all-in-one-2.3.x.sh.gz
[root@webadm1 tmp]# sh webadm_all_in_one-2.3.x-x64.sh
WebADM v2.3.x (x64 bit) Self Installer
Copyright (c) 2010-2024 RCDevs Security SA All rights reserved.
Install WebADM in '/opt/webadm' (y/n)? y
Extracting files, please wait... Ok
Removing temporary files... Ok
Run WebADM setup script now (y/n)? n
Packages are now installed.
Choosing your PKI setup
When deploying WebADM, you are also deploying a PKI, which is mandatory for WebADM to run. The PKI component of WebADM is called Rsignd. Rsignd is configured during the execution of the WebADM setup script. It can be configured as a Standalone Certificate Authority (CA) or as a Subordinate CA. The default and simplest setup is to configure WebADM/Rsignd as a standalone PKI.
Standalone Certificate Authority
If you do not have any Enterprise Certificate Authority in your infrastructure or if you don't want to configure WebADM as a Subordinate Certificate Authority, then configure WebADM as a Standalone CA.
Subordinate Certificate Authority
If you already have a Root/Enterprise Certificate Authority, you can generate a Subordinate Certificate Authority (certificate/key) from your existing enterprise CA that will be used by WebADM/Rsignd to generate certificates for various purposes.
If you want to configure WebADM as a Subordinate Certificate Authority, copy the certificate and the related key in PEM format to /opt/webadm/pki/ca/ as ca.crt and ca.key, respectively.
If not done beforehand, the setup script will stop.
Once you have this information, you can continue with the next section.
Choosing your LDAP identity source
Before running the WebADM setup script, you need to identify your main company identity source, such as Active Directory, OpenLDAP, Novell, etc.
You will need the following information/objects creation from your LDAP:
- LDAP directory IP/DNS name to use with WebADM, along with port and encryption settings;
- Tree-base of your LDAP directory for Active Directory setup (e.g: dc=domain,dc=com);
- Service account distinguished name (proxy_user in RCDevs terminology);
- Service account password;
- Group(s) allowed to log in to the WebADM Administrator Portal and administer the solutions;
Once you have this information, you can continue with the next section.
Choosing your SQL DBMS
WebADM is deployed with an SQL database that stores various information such as logs, inventoried hardware tokens, certificates, API keys, and more.
WebADM supports various DBMS solutions. Here is the list:
- MySQL: 8.0, 8.4 and 9.0;
- MariaDB: 10.5, 10.6, 10.11, 11.2, 11.4, 11.5;
- PostgreSQL: 12 to 16;
- CockroachDB: 23.2 to 24.2
- MSSQL;
- SQLite
In the WebADM standalone and cluster guides, we will demonstrate the setup with MariaDB server.
Setup your SQL DBMS
The setup of the SQL DBMS consist of:
- Installing the MariaDB server;
- Running the mariadb-secure-installation script for MySQL/MariaDB;
- Creating a database for WebADM;
- Creating a user and its password for WebADM to connect to the SQL database;
- Granting privileges to the SQL user on the newly created database;
The WebADM Setup Wizard, described later in this documentation, will create the SQL tables.
Installation of MariaDB server
Install with Debian repository:
root@webadm:~# apt install mariadb-server
Install with yum repository:
root@webadm:~# dnf install mariadb-server
Enable and start the MariaDB service
Then enable, start mariadb service, and execute built-in script to secure installation:
root@webadm:~# systemctl enable mariadb
root@webadm:~# systemctl start mariadb
Running the mariadb-secure-installation script
root@webadm:~# mariadb-secure-installation
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MariaDB to secure it, we'll need the current
password for the root user. If you've just installed MariaDB, and
you haven't set the root password yet, the password will be blank,
so you should just press enter here.
Enter current password for root (enter for none):
OK, successfully used password, moving on...
Setting the root password ensures that nobody can log into the MariaDB
root user without the proper authorisation.
You already have a root password set, so you can safely answer 'n'.
Change the root password? [Y/n] Y
New password:
Re-enter new password:
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MariaDB installation has an anonymous user, allowing anyone
to log into MariaDB without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] Y
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] Y
... Success!
By default, MariaDB comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] Y
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] Y
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MariaDB
installation should now be secure.
Thanks for using MariaDB!
Create the WebADM database, user and grant permissions
[root@webadm1 ~]# mysql -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 3
Server version: 10.5.22-MariaDB MariaDB Server
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> CREATE DATABASE webadm;
Query OK, 1 row affected (0.00 sec)
MariaDB [(none)]> CREATE USER 'webadm'@'localhost' identified by 'password';
Query OK, 0 rows affected (0.00 sec)
MariaDB [(none)]> GRANT ALL PRIVILEGES ON webadm.* to 'webadm'@'localhost';
Query OK, 0 rows affected (0.00 sec)
Your database is configured.
WebADM Setup script
Ensure you have all the required information listed in previous sections ready before starting the setup process.
Run the WebADM setup script with the following command:
[root@webadm1 tmp]# /opt/webadm/bin/setup
You are then prompted for the WebADM license agreement that you have to accept by entering Yes:
RCDEVS WEBADM LICENSE AGREEMENT
RCDevs WebADM Server ("WebADM")
Copyright (c) 2010-2024 RCDevs Security SA, All rights reserved.
IMPORTANT: READ CAREFULLY: By using, copying or distributing the Software
Product you accept all the following terms and conditions of the present
WebADM License Agreement ("Agreement").
If you do not agree, do not install and use the Software Product.
WebADM includes additional software products provided by RCDevs SA under
freeware and commercial licenses. These additional software are installed
under the "/opt/webadm/webapps" and "/opt/webadm/websrvs" directories.
This Agreement is subject to all the terms and conditions of any such
additional software license.
1. DEFINITIONS. "Software Product" means RCDevs Server with which the
Agreement is provided which may include third party computer information
or software, including apache2, php, libmcrypt, libcurl, libgmp, redis,
libxml2, libpng, libqrencode, openldap, openssl, apcu, unixodbc, geoip,
expat, hiredis, nghttp2, hiredis, libmaxmind, openscn libcouchbase
unmodified software and libraries and related explanatory written
materials ("Documentation"). "You" means you or any recipient that
obtained a copy of the Software Product pursuant to the terms and
conditions of the Agreement.
2. LICENSE. Subject to your compliance with the terms and conditions of
the Agreement, including, in particular, the provisions in Sections 3, 5
and 6 below, RCDevs hereby grants You a non-exclusive and royalty-free
license to use and distribute the Software Product solely for
non-commercial purposes in worldwide. You may:
a. download and install the Software Product on any computer in your
possession;
b. use the Software Product and any copy solely for a non-commercial
purposes;
c. make any original copies of the Software Product; and
d. distribute any copy of the Software Product only in the form
originally furnished by RCDevs with no modifications or additions
whatsoever. If You have the slightest doubt that your copy of the
Software Product is not original, You must contact RCDevs for an
original copy.
3. OBLIGATIONS AND RESTRICTIONS ON LICENSE. The license granted in
Section 2 is subject to the following obligations and restrictions:
a. The Software Product and copies are to be used only for non-commercial
purposes. Prohibited commercial purposes include, but are not limited to:
(i) Selling, licensing or renting the Software Product to third
parties for a fee (by payment of money or otherwise, whether direct or
indirect);
(ii) Using the Software Product to provide services or products to
others for which you are compensated in any manner (by payment of
money or otherwise, whether direct or indirect), including, without
limitation,providing support or maintenance for the Software Product;
(iii) Using the Software Product to develop a similar application on
any platform for commercial distribution.
You shall use your best efforts to promptly notify RCDevs upon learning
of any violation of the above commercial restrictions.
b. RCDevs, in its sole and absolute discretion, may have included a
portion of the source code or online documentation of the Software.
Except for any such portions, YOU SHALL NOT MODIFY, REVERSE ENGINEER,
DECOMPILE, DISASSEMBLE, OR OTHERWISE ATTEMPT TO DISCOVER THE SOURCE CODE
OF THE SOFTWARE PRODUCT, except to the extent this restriction is
prohibited by applicable law. Further, You may not create derivate works
of or based on the Software Product.
c. Any copy of the Software Product that you make must conspicuously and
appropriately reproduce and contain RCDevs's copyright and other
proprietary notices that appear on or in the Software Product (see
Software Product for examples of such notices) and disclaimer of
warranty; keep intact the Agreement and all notices that refer to the
Agreement and any absence of warranty; and give any other recipients of
the Software Product a copy of the Agreement.
d. As used in this Agreement, the term "distribute" includes making the
Software Product available (either intentionally or unintentionally) to
third parties for copying or using. Each time You distribute the Software
Product or any original copy of the Software Product, You are responsible
for the recipient expressly agree to comply with the terms and conditions
of the Agreement. The recipient automatically receives the license to
use, copy or distribute the Software Product subject to these terms and
conditions. You may not impose any further restrictions on the
recipients' exercise of the rights granted herein.
e. RCDevs shall have no obligation to provide any maintenance, support,
upgrades or new releases of the Software Product.
4. INTELLECTUAL PROPERTY OWNERSHIP, RESERVATION OF RIGHTS. Title,
copyright, ownership rights, and any other intellectual property rights
in and to the Software Product, including its Documentation, and each
copy thereof are and shall remain the only and absolute property of
RCDevs. Except as expressly stated herein, the Agreement does not grant
You any intellectual property rights in the Software Product and all
rights not expressly granted are reserved by RCDevs.
5. WARRANTY DISCLAIMER.
THE SOFTWARE PRODUCT IS LICENSED FREE OF CHARGE, AND THERE IS NO WARRANTY
OF ANY KIND FOR THE SOFTWARE PRODUCT.
RCDevs PROVIDE THE SOFTWARE PRODUCT "AS IS" WITH ALL FAULTS AND ANY
EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED
WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE,
TITLE, CUSTOM, ACCURACY OF INFORMATIONAL CONTENT, SYSTEM INTEGRATION OR
NON-INFRINGEMENT ARE DISCLAIMED.
THE ENTIRE RISK AS TO THE RESULTS, QUALITY AND PERFORMANCE OF THE
SOFTWARE PRODUCT IS WITH YOU. SHOULD THE SOFTWARE PROVE DEFECTIVE, YOU
(AND NOT RCDevs) ASSUME THE COST OF ALL NECESSARY SERVICING, REPAIR OR
CORRECTION.
6. LIMITATION OF LIABILITY.
YOU EXPRESSLY ACKNOWLEDGE AND AGREE THAT IN NO EVENT WILL RCDevs BE
LIABLE FOR ANY DAMAGES, CLAIMS OR COSTS WHATSOEVER INCLUDING ANY DIRECT,
INDIRECT, INCIDENTAL, SPECIAL, PUNITIVE, CONSEQUENTIAL OR EXEMPLARY
DAMAGES,INCLUDING BUT NOT LIMITED TO,DAMAGES FOR LOSS OF USE, DATA, OR
OTHER INTANGIBLE LOSSES, ARISING OUT OF, OR RELATED TO THE AGREEMENT OR
TO YOUR USE OR THE INABILITY TO USE THE SOFTWARE PRODUCT OR
DOCUMENTATION, EVEN IF RCDevs HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH
LOSS, DAMAGES OR CLAIMS.
7. TERMINATION. The license granted hereunder is effective until
terminated by RCDevs, in its sole discretion, after notification.
You may terminate the Agreement at any time by uninstalling and
destroying all copies of the Software Product in your possession
or control.
This license will terminate automatically if you fail to comply with the
terms and conditions of the Agreement above. Upon such termination, you
must destroy all copies of the Software Product.
The provisions of Section 5 and 6 shall survive the termination of the
Agreement.
8. APPLICABLE LAW AND GENERAL PROVISIONS. The Agreement will be governed
by and construed in accordance with the Luxembourg law and submitted to
the Luxembourg competent courts.
The URL-link of any open-source files and libraries relating to the
Software Product is located in the file docs/licenses.txt.
If you have any questions, notices or information relating to the
Agreement, please use the address and contact information included with
the Software Product or via the web at http://www.rcdevs.com/.
I agree with RCDevs WebADM terms and conditions (Yes/No): Yes
Select "Master setup" for the first deployed server by typing m.
Setup WebADM as master server or slave (secondary server in a cluster) ([m]/s)? m
Choose your PKI setup:
Setup WebADM as a Standalone CA (1) or Subordinate CA (2) ([1]/2)?
To configure WebADM as a Subordinate CA, you need to copy your Sub-CA certificate and key as PEM format in /opt/webadm/pki/ca/ca.crt and /opt/webadm/pki/ca/ca.key
- If option 1 is chosen, CA certificate and CA key are going to be generated at the end of the setup, and you are prompted to provide the following information regarding the creation of your PKI.
Setup WebADM as a Standalone CA (1) or Subordinate CA (2) ([1]/2)? 1
Please, provide the Issuer Name of the root certificate that is going to be created for the new Certificate Authority. If none of asked attribute is provided, a default name like 'WebADM CA# XXXXX' will be configured)
This information matter and will be visible in every certificates issued by WebADM!
Country code (e.g. LU): LU
Organization Name (e.g. RCDevs Security SA): RCDevs Support SA
Organizational Unit Name (e.g. Certificate Autority Services): RCDevs Support Root CA
Common Name (e.g. RCDevs Root CA): Support Certificate Autority
- If option 2 is chosen, the CA certificate and CA key must already be copied as
ca.crtandca.keyin PEM format to the/opt/webadm/pki/ca/folder, as described in the previous sections.
You are then prompted to choose your identity source and schema setup. Read the descriptions of each setup and choose your preferred one.
1) Default configuration (local RCDevs Directory)
2) Other generic LDAP server (Novell eDirectory, Oracle, OpenLDAP)
3) Active Directory with schema extention (preferred with AD)
4) Active Directory without schema extention
5) Active Directory schemas Mixed (Extended and Not Extended schema setup used)
Choose a template number [1]:
-
If you choose the RCDevs directory, the RCDevs-slapd component must already be configured and running.
-
Choose option 2 for Novell eDirectory, Oracle Directory, OpenLDAP, or other LDAP setups not listed in this setup.
-
If you choose AD with Schema extension, a small extension of your AD schema will be required. This extension involves adding a few new objectClasses and attributes to your schema, which will be used by WebADM and its components to store their data. For example, token data will be stored in the webadmData attribute. The advantage of schema extension is to avoid potential conflicts with other applications that may store data in the same attributes used by WebADM.
-
If you choose AD without Schema extension, ensure that the bootableDevice objectClass, bootFile, bootParameter, and serial attributes are not already used by another application. If they are in use, you cannot select this setup and must proceed with Schema extension.
-
This option supports extended schemas for all directory types simultaneously, but not extended schema for Active Directory. It is more designed for Software as a Service (SAAS) providers or configuring WebADM with multiple LDAP tenants where schema extension is not possible on Active Directory. With this setup, WebADM will read the schema of all LDAP tenants configured and store data according to what is available. If Schema extension is detected, WebADM objectClasses and attributes are prioritized. If another tenant (AD schema not extended) is configured, the bootableDevice objectClass, bootFile, bootParameter, and serial attributes will be used. All LDAP Directory except Active Directory must have their schema extended.
Important notes regarding Active Directory and Schema Extension
To perform the Active Directory schema extension using the graphical setup wizard of WebADM (later in the installation process), the domain controller set as the primary LDAP server configured with WebADM must host the schema master FSMO role. Additionally, the first authenticated user on the WebADM Administrator portal must be part of the Schema Administrator group to successfully perform the schema extension operations.
Select your option, and then you are prompted to provide the first LDAP server IP/DNS name, LDAP port and encryption:
Please type the name/ip of the LDAP server: ad1.rcdevsdocs.com
Please type the port for LDAP [389]:
Checking LDAP port 389 on ad1.rcdevsdocs.com... Ok
Please choose the encryption ([TLS]/SSL/NONE)?TLS
As I choose AD setup option in that example, I'm prompted to provide the LDAP tree base of my domain.
Please type domain FQDN (i.e. dc=lab,dc=local) []: dc=rcdevsdocs,dc=com
Here the service account (proxy_user) distinguished name (DN) is asked:
Please type a service account with read/write acces to LDAP:
CN=svc_webadm,cn=Users,dc=rcdevsdocs,dc=com
Enter the password of the account previously provided.
Please type the user password for CN=svc_proxy_user,cn=Users,dc=rcdevsdocs,dc=com:
WebADM test the LDAP access with the provided information and credentials:
Testing user access...Ok
Provide here the super_admin account or group DN. super_admins members are allowed to log in to WebADM Admin portal and manage the products.
Please type an account or group DN with read/write access to LDAP (multiple accounts and groups can be configured later in webadm.conf. Nasted groups are not supported for super_admins):
cn=grp_webadm_admins,cn=Users,dc=rcdevsdocs,dc=com
All graphical configuration performed through WebADM Admin GUI is stored in an LDAP container or an OrganizationalUnit. Provide the DN of the object.
Please type the WebADM container [cn=WebADM,dc=rcdevsdocs,dc=com]:
ou=webadms,dc=rcdevsdocs,dc=com
Provide then the FQDN of this server. This will be used for WebADM SSL certificate/key generation.
Enter the server fully qualified host name (FQDN) [webadm1.rcdevsdocs.com]: webadm1.rcdevsdocs.com
Setup is finishing. In case you chosen standalone CA at the begining of this setup, the CA certificate and key are going to be generated. Certificate use by this WebADM node is also going to be generated and signed by the Rsignd service (CA).
Adding CA certificate to the local trust list... Ok
Generating SSL private key... Ok
Creating SSL certificate request... Ok
Signing SSL certificate with CA... Ok
Creating webadm system user... Ok
Setting file permissions... Ok
Adding systemd service... Ok
Adding logrotate scripts... Ok
Generating secret key string... Ok
WebADM has successfully been setup.
Internal/External services configuration (servers.xml)
External services such as LDAP, SQL, Session Server, SMTP, etc., are all declared in the /opt/webadm/conf/servers.xml configuration file. You can edit this file if any changes are needed regarding the configured connectors. You must at least add your previously configured SQL settings.
<?xml version="1.0" encoding="UTF-8" ?>
<Servers>
<!--
******************************************
*** WebADM Remote Server Connections ***
******************************************
You can configure multiple instances for each of the following servers.
At login, WebADM will try to connect the configured servers in the same
order they appear in this file and uses the first one it successfully
establishes the connection to. If the server connection goes down, it
will automatically fail over to the next configured server.
Any special characters must be encoded in XML compliant format.
At least one LDAP server and one SQL server is required to run WebADM.
Supported servers: OpenLDAP, Active Directory, Novell eDirectory, 389.
Allowed LDAP parameters are:
- name: server friendly name
- host: server hostname or IP address
- port: LDAP port number
default and TLS: 389
default SSL: 636
- encryption: connection type
allowed type are NONE, SSL and TLS
default: 'NONE'
- ca_file: Trusted CA for SSL and TLS
- cert_file: client certificate file
- key_file: client certificate key
-->
<LdapServer name="AD 1"
host="ad1.rcdevsdocs.com"
port="389"
encryption="TLS"
ca_file="" />
<!--
SQL servers are used for logs; message localizations and inventories.
Supported servers: MySQL5, MySQL8, PostgreSQL, MSSQL, Sybase, Oracle, SQLite.
Allowed SQL parameters are:
- type: MySQL5, MySQL8, MariaDB, PostgreSQL, MSSQL, SQLite.
- name: server friendly name
- host: server hostname or IP address
- port: SQL port number (depends on server type)
- user: database user
- password: database password
- database: database name
- charset: character set (use latin1 if you get unicode issues)
- encryption: connection type allowed type are NONE, SSL and TLS
- ca_file Trusted CA for SSL and TLS
- cert_file: client certificate file
- key_file: client certificate key
With SQLite, only the 'database' must be set and other parameters are
ignored. The database is the full path to an SQLite DB file where WebADM
has full write access.
With Oracle, you can optionally use TNS names. If the 'tnsname' is set
then the 'host' and 'port' parameters are ignored and a tnsnames.ora
file must exist under the conf/ directory.
-->
<SqlServer name="SQL Server 1"
type="MariaDB"
host="localhost"
user="webadm"
password="webadm"
database="webadm"
encryption="NONE" />
<!--
A session server is required for storing/sharing persistent memory data
on your WebADM server(s). You must specify two servers with clustering.
The session server is based on Redis6 which is included in WebADM.
With WebADM >= 2.1.5, TLS encryption is used by default on port 4000!
-->
<SessionServer name="Session Server 1"
host="localhost"
port="4000"
secret="my_secret" />
<!--
A PKI server (or CA) is required for signing user certificates.
The RSign PKI server is included in WebADM. So you can keep the
default settings here.
-->
<PkiServer name="PKI Server 1"
host="localhost"
port="5000"
secret="my_secret" />
<!--
HTTP proxy servers can be used by WebADM for connecting
remote Web services and version checking.
-->
<ProxyServer name="HTTP Proxy 1"
host="proxy1.rcdevsdocs.com"
port="8080"
user=""
password=""
ca_file="" />
<!--
SMTP mail servers can be used by WebADM for sending emails.
If no server is specified, WebADM will use the local mailer
in /usb/sbin/sendmail to send emails.
-->
<MailServer name="SMTP Server 1"
host="mail1.rcdevsdocs.com"
port="25"
user=""
password=""
encryption="NONE"
ca_file="" />
</Servers>
WebADM configuration file (webadm.conf)
The configuration file we are focusing now is /opt/webadm/conf/webadm.conf. After the master setup, mandatory parameters has been already configured in that file in order to start WebADM services but everything is not setup. That configuration file contain the main configuration of WebADM regarding LDAP attributs, super_admins, services account, encryption key, HSM configuration and more.... All settings that can be changed are well documented in the configuration file.
LDAP Attributes, LDAP objectClasses should not be changed. They have been configured according to the LDAP setup you choose during the setup script.
Found below, an example of webadm.conf file:
#
# WebADM Server Configuration
#
# Administrator Portal's authentication method.
# - PKI: Requires client certificate and login password.
# - UID: Requires domain name, login name and password.
# - DN: Requires login DN and password.
# - OTP: Like UID with an OTP challenge.
# - U2F: Like UID with a FIDO-U2F challenge.
# - MFA: Like UID with both OTP and FIDO-U2F challenge.
# Using certificates is the most secure login method. To use certificate login,
# you must log in WebADM and create a login certificate for your administrators.
# The UID mode requires a WebADM domain to exist and have its User Search Base
# set to the subtree where are located the administrator users. When using UID
# and if there is no domain existing in WebADM, the login mode is automatically
# forced to DN. You will also need to log in with the full user DN and set up
# a WebADM domain to be able to use the UID login mode.admin_auth UID
admin_auth UID
# Show the registered domain list when admin_auth is set to UID, OTP or U2F.
# And set a default admin login domain when auth_mode is set to these methods.
list_domains Yes
#default_domain "Default"
# Manager API's authentication method. Only UID, PKI and DN are supported here.
# If you set the admin_auth with multi-factor (PKI, OTP or U2F), then you must
# either use manager_auth PKI or UID with a list of allowed client IPs.
#manager_auth UID
#manager_clients "192.168.0.10","192.168.0.11"
# User level changes the level of feature and configuration for all applications.
# WebADM proposes three levels: Beginner, Intermediate and Expert. The default
# level (Expert) is recommended as it provides access to all the RCDevs features.
#user_level Expert
# If your LDAP directory is setup with a base DN (ex. dc=mydomain,dc=com on AD),
# you can optionally set the base_treebase suffix and omit the suffix in other
# LDAP configurations like proxy_user, super_admins and containers.
ldap_treebase "dc=rcdevsdocs,dc=com"
# The proxy user is used by WebADM for accessing LDAP objects over which the
# admin user does not have read permissions or out of an admin session.
# The proxy user should have read permissions on the whole LDAP tree,
# and write permissions on the users/groups used by the WebApps and WebSrvs.
# The use of a proxy user is required for WebApps and WebSrvs.
# With ActiveDirectory, you can use any Domain Administrator DN as a proxy user,
# which should look like cn=Administrator,cn=Users,dc=mydomain,dc=com.
proxy_user "CN=svc_webadm,cn=Users"
proxy_password "my_password"
# Super administrators have extended WebADM privileges such as setup permissions,
# additional operations and unlimited access to any LDAP encrypted data. Access
# restriction configured in the WebADM OptionSets do not apply to super admins.
# You can set a list of individual LDAP users or LDAP groups here.
# With ActiveDirectory, your administrator account should be is something like
# cn=Administrator,cn=Users,dc=mydomain,dc=com. And you can replace the sample
# super_admins group on the second line with an existing security group.
super_admins "cn=grp_webadm_admins,cn=Users"
# LDAP objectclasses
container_oclasses "container", "organizationalUnit", "organization", "domain", "locality", "country", \
"openldaprootdse", "treeroot"
# user_oclasses is used to build the LDAP search filter with 'Domain' auth_mode.
# If your super admin user user does not have one of the following objectclasses,
# add one of its objectclasses to the list.
user_oclasses "user", "account", "person", "inetOrgPerson", "posixAccount"
group_oclasses "group", "groupOfNames", "groupOfUniqueNames", "dynamicGroup", "posixGroup"
# With ActiveDirectory 2003 only, you need to add the 'user' objectclass to the
# webadm_account_oclasses and the 'group' objectclass to the webadm_group_oclasses.
webadm_account_oclasses "webadmAccount"
webadm_group_oclasses "webadmGroup"
webadm_config_oclasses "webadmConfig"
# LDAP attributes
certificate_attrs "userCertificate"
password_attrs "userPassword", "unicodePwd", "sambaNTPassword"
uid_attrs "uid", "samAccountName", "userPrincipalName"
member_attrs "member", "uniqueMember"
memberof_attrs "memberOf", "groupMembership"
memberuid_attrs "memberUid"
language_attrs "preferredLanguage"
mobile_attrs "mobile"
mail_attrs "mail"
webadm_data_attrs "webadmData"
webadm_settings_attrs "webadmSettings"
webadm_type_attrs "webadmType"
webadm_voice_attrs "webadmVoice"
# Set the LDAP container required by WebADM to store its configuration objects.
config_container "ou=webadms"
# You can alternatively configure each configuration container independently.
#domains_container "cn=Domains,cn=WebADM"
#clients_container "cn=Clients,cn=WebADM"
#devices_container "cn=Devices,cn=WebADM"
#webapps_container "cn=WebApps,cn=WebADM"
#websrvs_container "cn=WebSrvs,cn=WebADM"
#adminroles_container "cn=AdminRoles,cn=WebADM"
#optionsets_container "cn=OptionSets,cn=WebADM"
#mountpoints_container "cn=MountPoints,cn=WebADM"
# You can set here the timeout (in seconds) of a WebADM session.
# Web sessions will be closed after this period of inactivity.
# The Manager Interface cookie-based sessions are disabled by default.
# admin_session and manager_session can be set in the form 'shared:900'
# in order to force sessions to be stored in the Session Servers instead of SHM.
admin_session 3600
manager_session 0
webapps_session 600
# You can set here the WebADM internal cache timeout. A normal value is one hour.
cache_timeout 3600
# Application languages
languages "EN","FR","DE","HU","ES","IT","FI","JP"
# WebADM encrypts LDAP user data, sensitive configurations and user sessions with
# AES-256. The encryption key(s) must be 256bit base64-encoded random binary data.
# Use the command 'openssl rand -base64 32' to generate a new encryption key.
# Warning: If you change the encryption key, any encrypted data will become invalid!
# You can set several encryption keys for key rollout. All the defined keys are used
# for decrypting data. And the first defined key is used to (re-)encrypt data.
# Two encryption modes are supported:
# Standard: AES-256-CBC (default)
# Advanced: AES-256-CBC with per-object encryption (stronger)
encrypt_data yes
encrypt_mode Standard
encrypt_hsm No
encrypt_key "cq19TEHgHLQuO09DXzjOw30rrQDLsPkT3NiL6l3BH2w="
# Hardware Cryptographic Module
#hsm_driver "/usr/local/lib/libsofthsm2.so"
#hsm_slot 274906134
#hsm_key "TestKey"
#hsm_pin 12345678
# The data store defines which back-end is used for storing user data and settings.
# By default WebADM stores any user and group metadata in the LDAP objects. By setting
# the data_store to SQL, these metadata are stored in a dedicated SQL table.
# LDAP remains the preferred option because it maximizes the system consistency.
# SQL should be used only if you need read-only LDAP access for the proxy_user.
data_store LDAP
# The record store defines which back-end is used to store SpanKey records.
# Choose SQL to store records in the database and NAS to store on a shared NAS folder.
# With NAS, the store_path must be configured and accessible from all cluster nodes.
record_store SQL
#record_path "/mnt/records"
# The group mode defines how WebADM will handle LDAP groups.
# - Direct mode: WebADM finds user groups using the memberof_attrs defined above.
# In this case, the group membership is defined in the LDAP user objects.
# - Indirect mode: WebADM finds user groups by searching group objects which contain
# the user DN as part of the member_attrs.
# - Auto: Both direct and indirect groups are used.
# - Disabled: All LDAP group features are disabled in WebADM.
# By default (when group_mode is not specified) WebADM handles both group modes.
group_mode Auto
# LDAP cache increases a lot of performances under high server loads. The cache limits
# the number of LDAP requests by storing resolved user DN and group settings. When
# enabled, results are cached for 300 secs.
ldap_cache Yes
# LDAP routing enables LDAP request load-balancing when multiple LDAP servers are
# configured in servers.xml. You should enable this feature only if the LDAP server
# load becomes a bottleneck due to a big amount of users (ex. more than 10000 users).
#ldap_routing No
# You can optionally disable some features if you run multiple WebADM servers with
# different purposes. For example, if you don't want to provide admin portal on an
# Internet-exposed WebApps and WebSrvs server.
# By default, all the functionalities are enabled.
enable_admin Yes
enable_manager Yes
enable_webapps Yes
enable_websrvs Yes
# Enable syslog reporting (disabled by default). When enable, system logs are sent
# to both the WebADM log files and syslog.
#log_debug No
#log_mixsql No
#log_syslog No
#syslog_facility LOG_USER
#syslog_format CEF
# Alerts are always recorded to the SQL Alert log. Additionally, when alert_email
# or alert_mobile is defined, the alerts are also sent by email/SMS.
alert_email "alert@rcdevsdocs.com"
alert_mobile "+33 12345678"
# Protect WebADM against bruteforce attacks on the WebApps by blacklisting source IPs
# for 20 seconds after 5 failed login attempts.
ip_blacklist Yes
# You can publish WebADM applications and OpenOTP mobile endpoint over Internet using
# a reverse proxy (WAF) or RCDevs WebADM Publishing Server (WAProxy).
# Set the IP address(es) of your reverse-proxy or WAProxy server(s). WebADM expects
# the HTTP_X_FORWARDED_FOR and HTTP_X_FORWARDED_HOST headers from reverse proxies!
# Use 'waproxy_proxies' ONLY if you are using RCDevs WAProxy as reverse-proxy!
#reverse_proxies "192.168.0.100", "192.168.0.101"
waproxy_proxies "172.16.0.10", "172.16.0.11"
# The 'public_hostname' is mandatory to let WebADM know your public endpoints' URLs.
# Use the public DNS name of your reverse proxy or WAProxy server without a scheme.
# The setting used to be named 'waproxy_pubaddr' in WebADM versions before v2.3.12.
public_hostname "otp.rcdevsdocs.com"
# Check for new product versions and license updates on RCDevs' website.
# These features require outbound Internet access from the server.
cloud_services yes
# WebApps theme (default or flat)
# Comment the following line to disable the default theme.
webapps_theme "default"
# End-user message templates
# The following variables are available: %USERNAME%, %USERDN%, %USERID%, %DOMAIN%, %APPNAME%
# Additional variables are available depending on the context: %APPNAME%, %APPID%, %TIMEOUT%, %EXPIRES%
app_unlock_subject "Unlocked access to %APPNAME%"
app_unlock_message "Hello %USERNAME%,\r\n\r\nYou have a one-time access to the %APPNAME%.\r\nYour access will automatically expire %EXPIRES%."
ldap_expire_subject "Login password near expiration"
ldap_expire_message "Hello %USERNAME%,\r\n\r\nYour login password will expire %EXPIRES%.\r\nPlease reset your password before expiration!\r\n\r\nRegards"
cert_expire_subject "Login certificate near expiration"
cert_expire_message "Hello %USERNAME%,\r\n\r\nYour login certificate will expire %EXPIRES%.\r\nPlease renew your certificate before expiration!\r\n\r\nRegards"
access_sign_subject "Agreement signature required for %CLIENT%"
access_sign_message "Hello %USERNAME%,\r\n\r\nPlease sign the agreement in order to access %CLIENT%.\r\nThe signature request expire %EXPIRES%."
no_badgeout_subject "Forgot badge-out %EXPIRES%"
no_badgeout_message "Hello %USERNAME%,\r\n\r\nYou did not badge-out since %EXPIRES%.\r\nPlease do not forget to badge out today!\r\n\r\nRegards"
no_badgein_subject "Badging required for %CLIENT%"
no_badgein_message "Hello %USERNAME%,\r\n\r\nYou tried to login to %CLIENT% without badging.\r\nPlease badge-in and retry!\r\n\r\nRegards"
# Personalization options
# You can customize your organization name, logo file and website URL.
# The logo file must be PNG image with size 100x50 pixels.
org_name "RCDevs Security"
org_logo "rcdevs.png"
org_site "https://www.rcdevs.com/"
org_from "noreply@rcdevsdocs.com"
# Misc options
#treeview_width 300
#treeview_items 3000
#default_portal Admin
#ldap_uidcase No
ntp_server "ntp.rcdevsdocs.com"
Once you configured all settings you need, it is time to start WebADM services.
Rsignd configuration file (rsignd.conf)
Rsignd is the PKI service running with WebADM. The configuration of Rsignd is located in /opt/webadm/conf/rsignd.conf on all nodes.
The rsignd.conf file must be configured in all WebADM servers in a Master/Master installation, and the secret must match what is configured in servers.xml in PKI section.
# Log file
logfile /opt/webadm/logs/rsignd.log
pidfile /opt/webadm/temp/rsignd.pid
# Default validity period for new certificates (in days)
# The CSR signing requests may set the validity period.
user_cert_validity 365
client_cert_validity 1825
server_cert_validity 3650
# Unless sepcified here smartcard certificates' expiration uses
# the user_cert_validity by default.
smartcard_cert_validity 1825
# Required by CiscoISE not supporting WebADM custom attributes.
#no_custom_extensions 0
# Certificate and key used for the SSL listener
rsignd_cert /opt/webadm/pki/webadm.crt
rsignd_key /opt/webadm/pki/webadm.key
# Path CA certificate files and serial
ca_cert /opt/webadm/pki/ca/ca.crt
ca_key /opt/webadm/pki/ca/ca.key
ca_serial /opt/webadm/pki/ca/serial
# Serial number format (hex or dec)
serial_format hex
# Set to yes if the CA or rsignd private keys requires a decryption password.
# PEM passwords will be prompted at WebADM startup.
ca_password no
rsignd_password no
# HSM certificate authority (CA)
# The HSM model and PIN code are configured in webadm.conf.
hsm_ca no
hsm_keyid 0
#
# Directory or file containing trusted CA certificates (in PEM format)
# After adding a new certificate, type a "make" in the "trusted_ca_path"
# to rebuild certificate's hash.
# This is needed for rsignd to read the trusted CA certificates.
# Comment "trusted_path" to disable rsignd certificate's trust restrictions.
trusted_path /opt/webadm/pki/trusted
#
# Client sections
#
# Declare here the Rsign clients with IP addresses or hostnames.
# In cluster mode, the client WebADM server(s) must be defined here!
client {
hostname localhost
secret my_secret
}
The PKI client on the primary node is declared by default during the WebADM setup script. Note that if the localhost value is used here, it must also be used in the PKI section of servers.xml.
Alternatively, the CA Key can be stored on an HSM and used for each certificate signing request. First, configure your HSM with WebADM in webadm.conf, then program the HSM with your CA key (located in the /opt/webadm/pki/ca/ folder) and provide the hsm_keyid value in rsignd.conf. Set the hsm_ca setting to yes. WebADM supports MirKey HSM, SmartCard HSM, and PKCS11 standard HSMs.
Start WebADM services and Run the Graphical Setup
Start WebADM services with the following command:
[root@webadm1 ~]# /opt/webadm/bin/webadm start
Checking libudev dependency... Ok
Checking system architecture... Ok
Checking server configurations... Ok
Found Trial license (RCDEVSSUPPORT)
Licensed by RCDevs Security SA to RCDevs Support
Licensed product(s): OpenOTP,SpanKey
Starting WebADM PKI service... Ok
Starting WebADM Session service... Ok
Starting WebADM Watchd service... Ok
Starting WebADM HTTP service... Ok
Checking server connections...
Connected LDAP server: LDAP Server (ad1.rcdevsdocs.com)
Connected SQL server: SQL Server (localhost)
Connected PKI server: PKI Server (localhost)
Connected Session server: Session Server (localhost)
Connected HTTP Proxy: Proxy Server (proxy1.rcdevsdocs.com)
Connected SMTP Proxy: SMTP Server (mail1.rcdevsdocs.com)
Checking LDAP proxy user access... Ok
Checking SQL database access... Ok
Checking PKI service access... Ok
Checking Mail service access... Ok
Checking HTTP Proxy access... Ok
Checking Cloud service access... Ok
Enter WebADM with your super_admin account and run the graphical setup. The login URL is https://<your-server-address>. Only super_admins and other_admins configured in webadm.conf or through graphical configuration can access this interface.
Important notes:
Until the graphical setup is complete and at least the first WebADM Domain is created, you must log in with the LDAP DistinguishedName (DN) of your super_admins account and not the username.
Once the graphical setup is completed you will be able to log in with a username and password (UID login mode) as configured in the /opt/webadm/conf/webadm.conf file.
If you use RCDevs Directory Server, the admin DN is cn=admin,o=root. The default password is password.
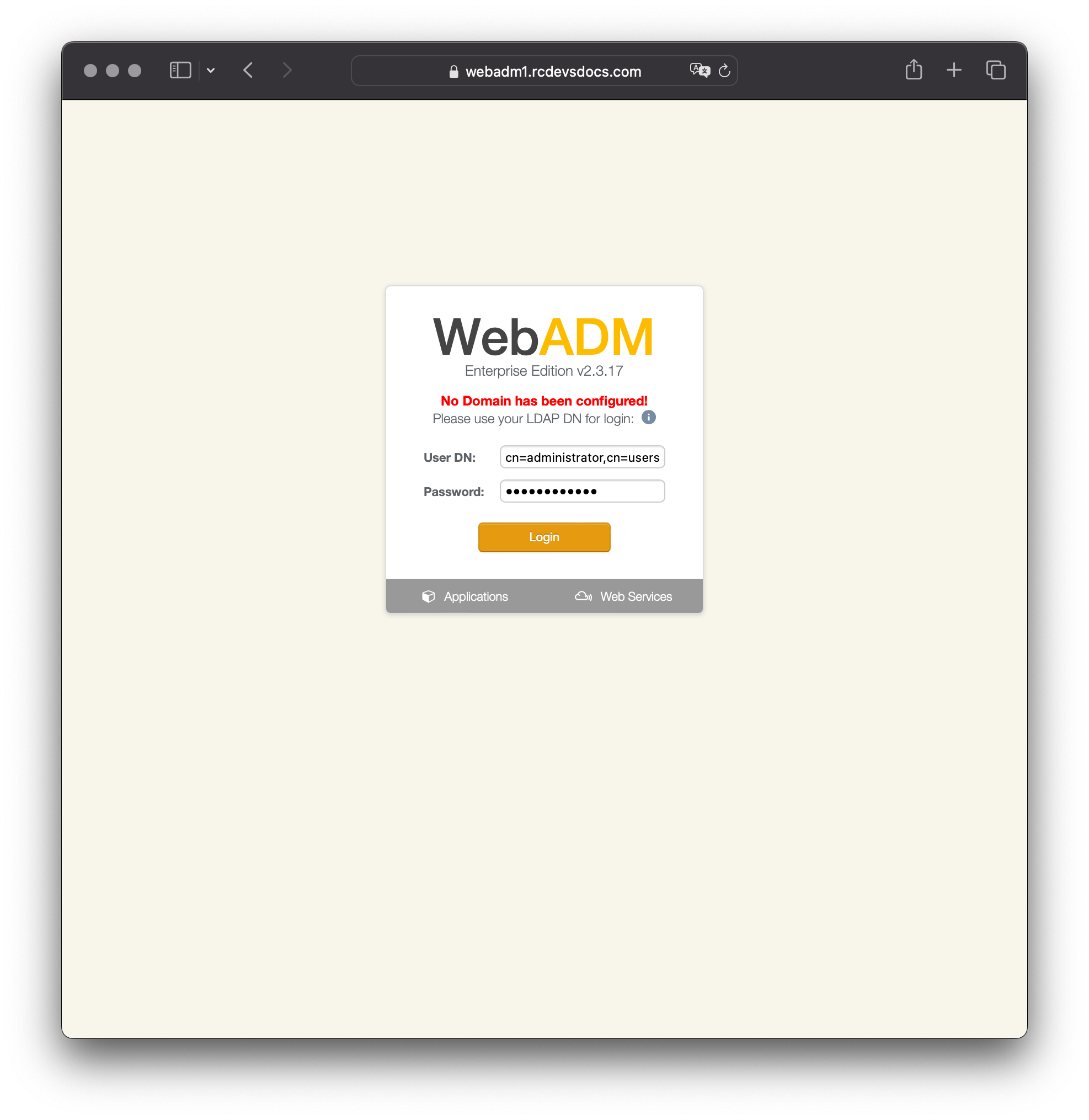
At the first login, the WebADM setup wizard will appear on the home page once you have successfully authenticated on the Administrator portal.
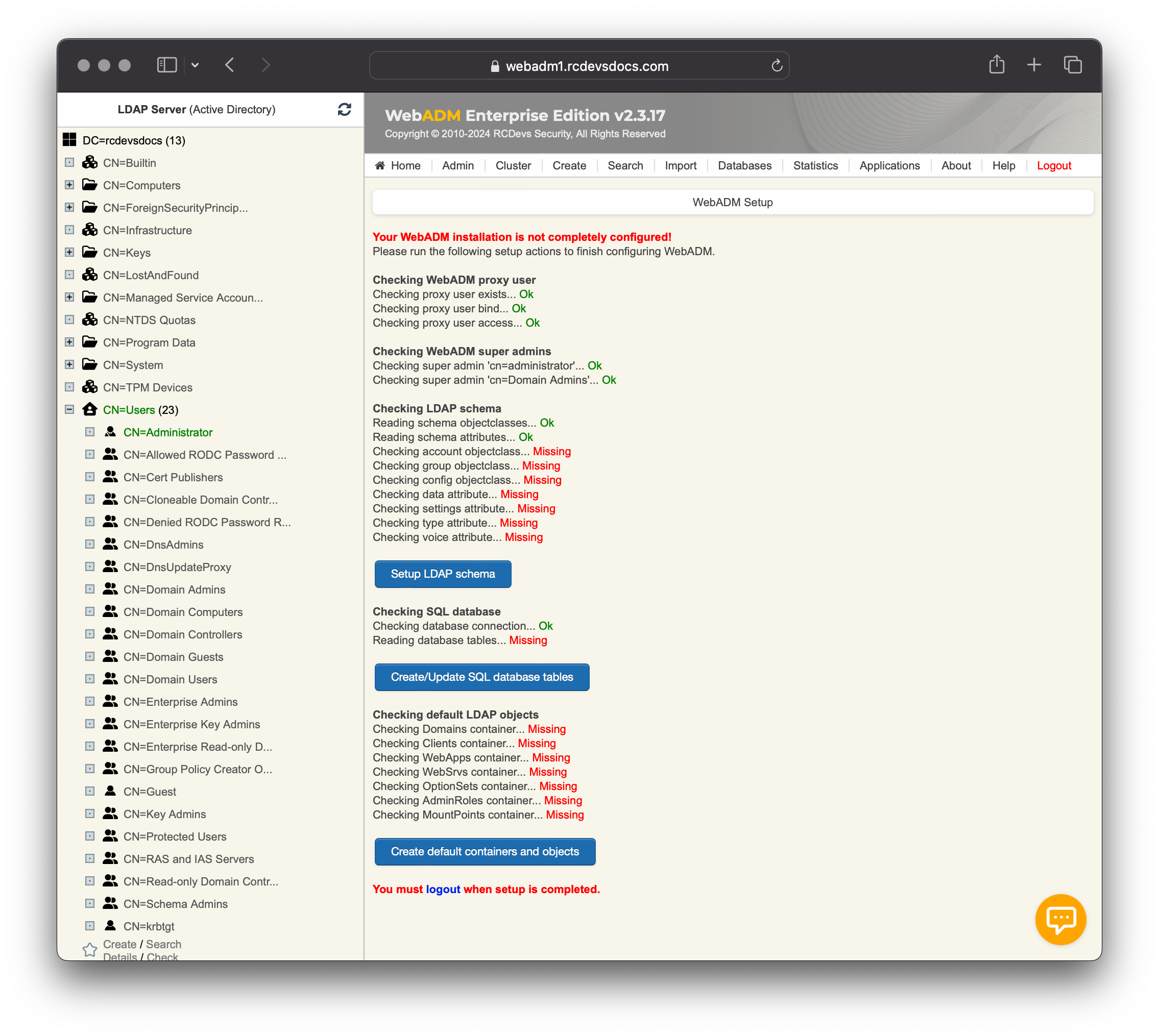
WebADM will not be functional until the graphical setup has been completed. The graphical setup process will:
- Create the required SQL tables. The SQL database must exist!
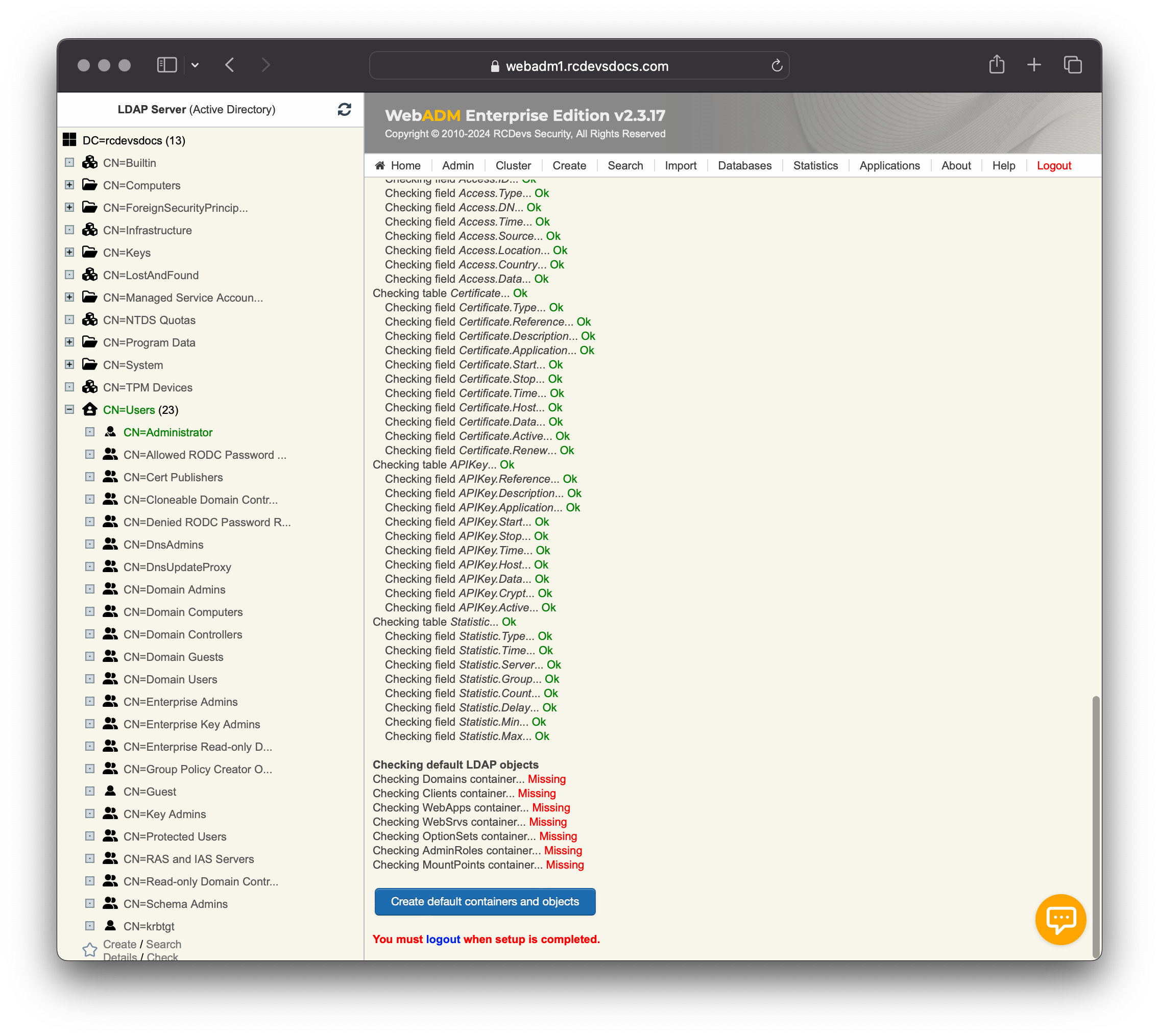
- Register the required LDAP schema object classes and attributes with Novell eDirectory and Microsoft Active Directory if schema extension has been chosen and is not currently available in the schema definition.
- Create the
proxy_user(if not already existing) with LDAP permissions of the authenticated user on the admin portal. - Set up the
proxy_userpermissions (on Novell eDirectory only). - Create the WebADM LDAP/config containers (as defined in the
/opt/webadm/conf/webadm.conffile).
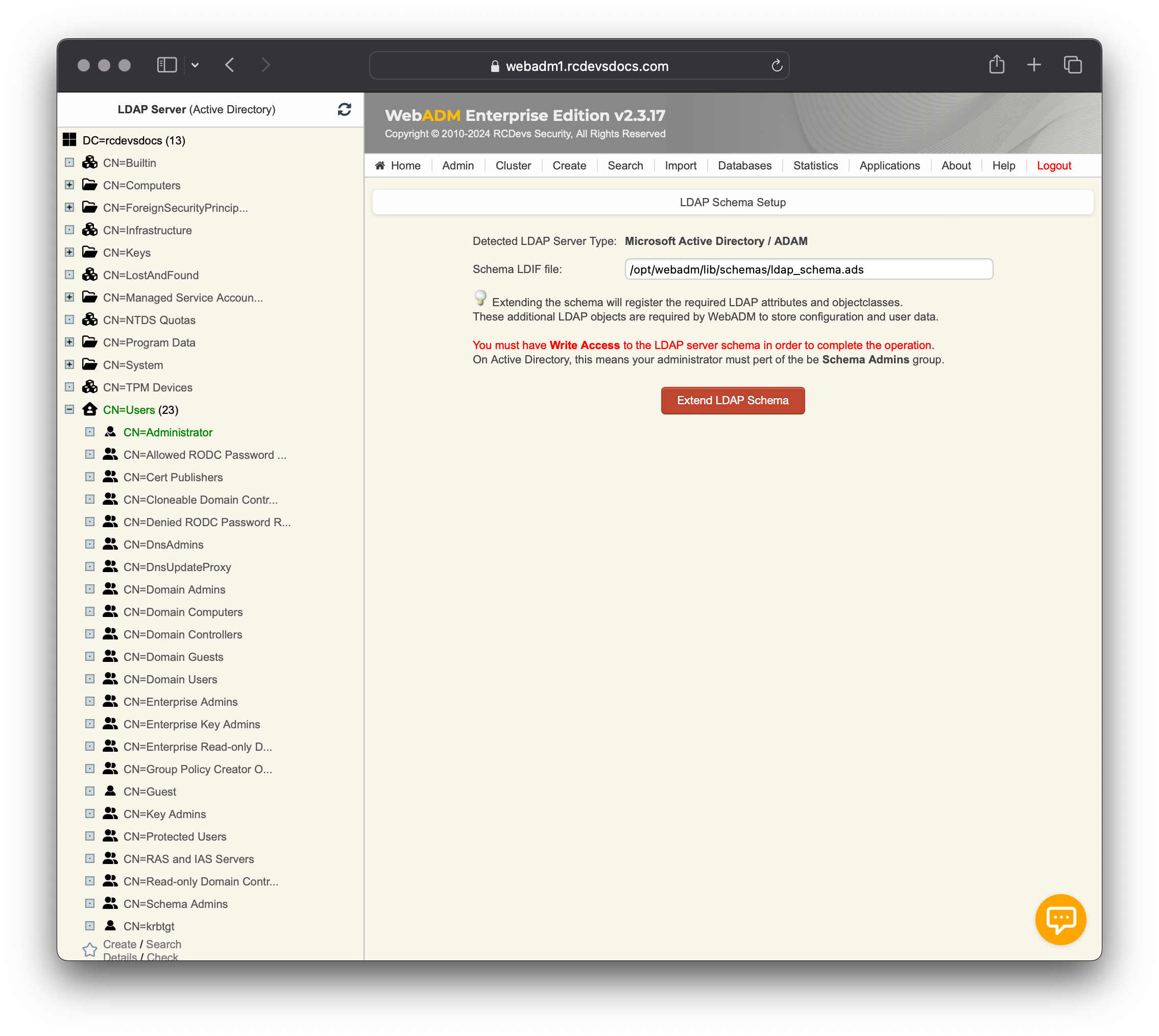
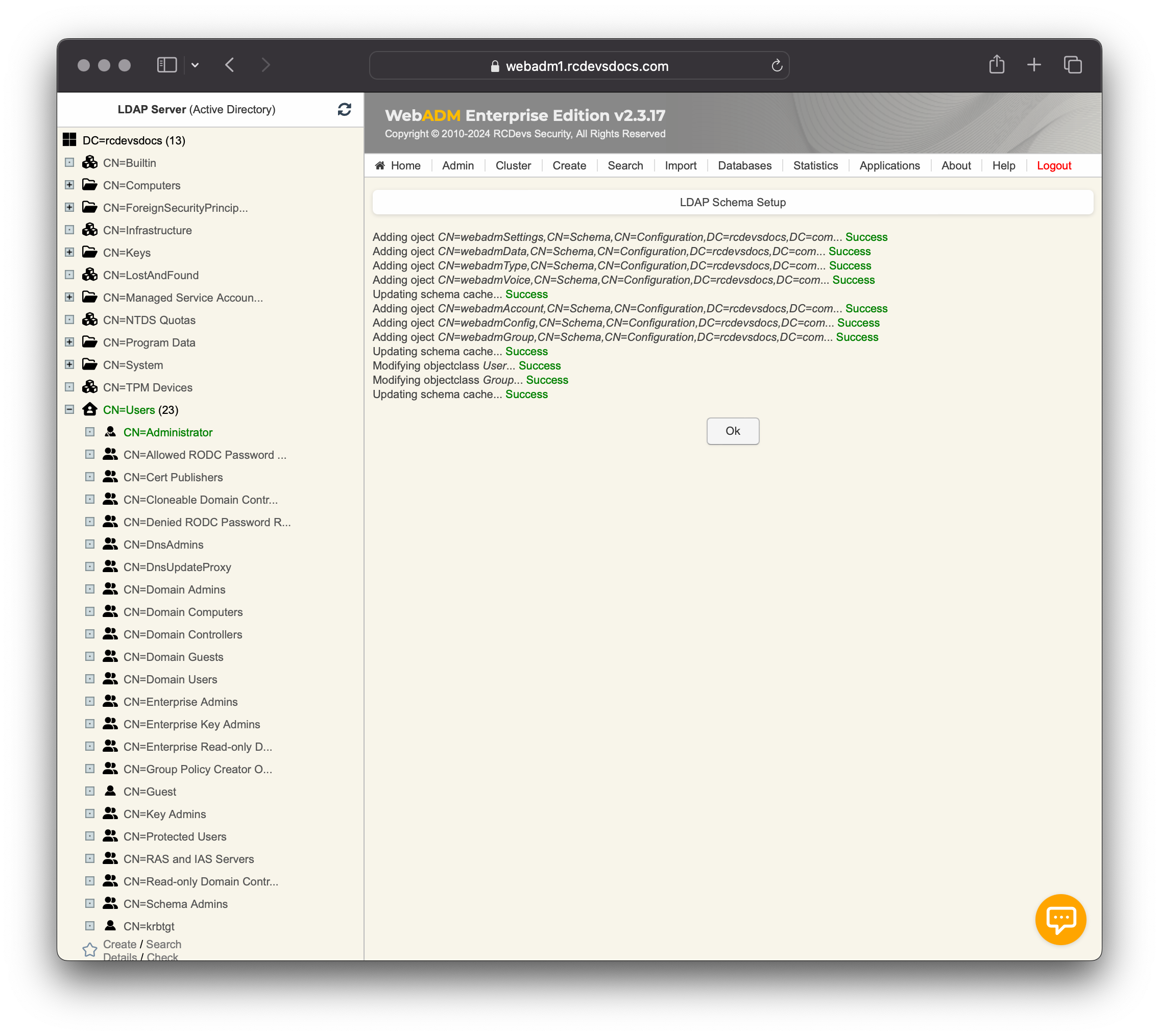
If WebADM fails to automatically create the objectClasses and attributes in an Active Directory environment, it is likely because the connected user on the WebADM admin portal is not part of the schema admin group and does not have the permissions to perform these operations, or the first domain controller configured in /opt/webadm/conf/servers.xml does not have the FSMO schema master role.
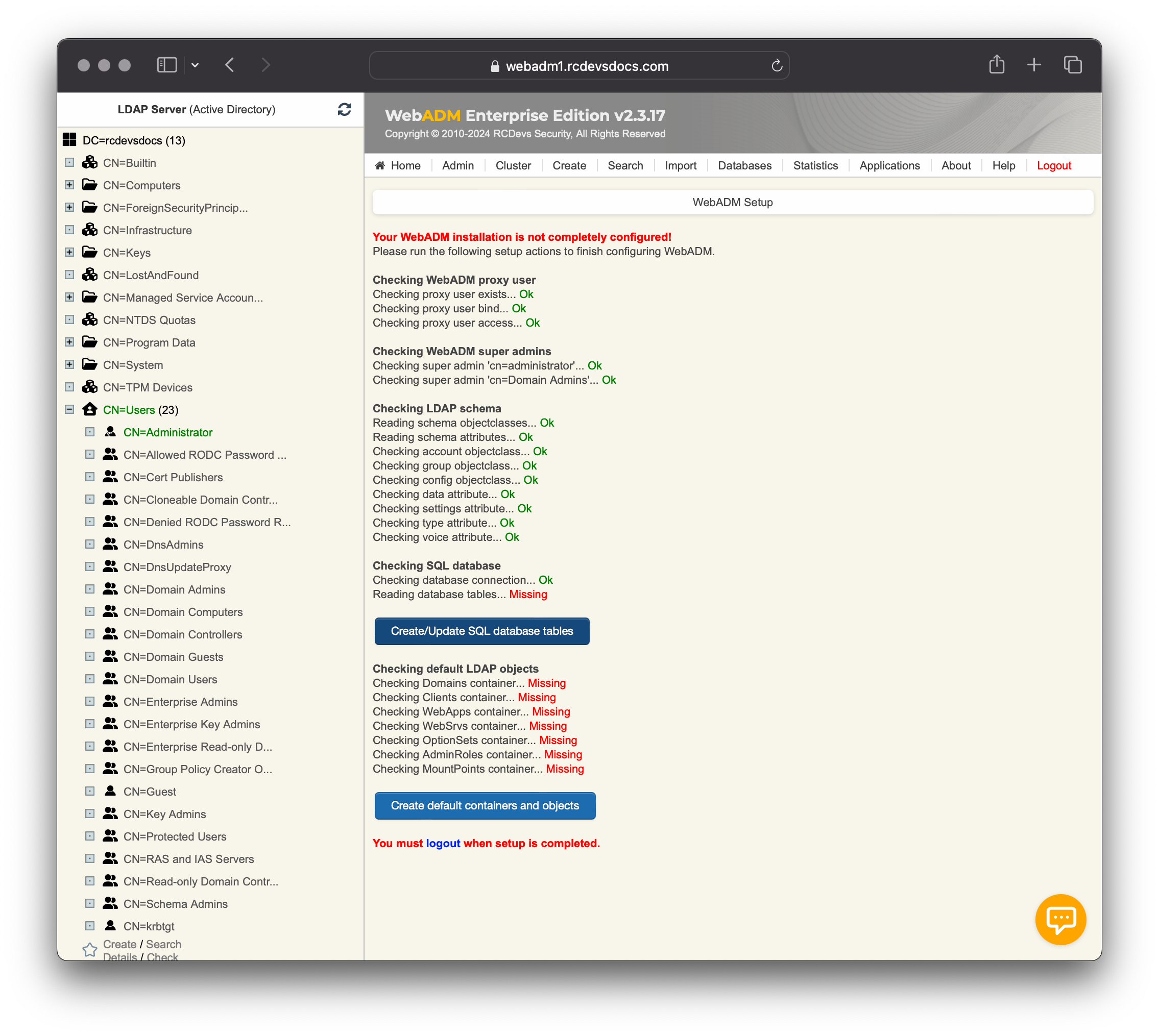
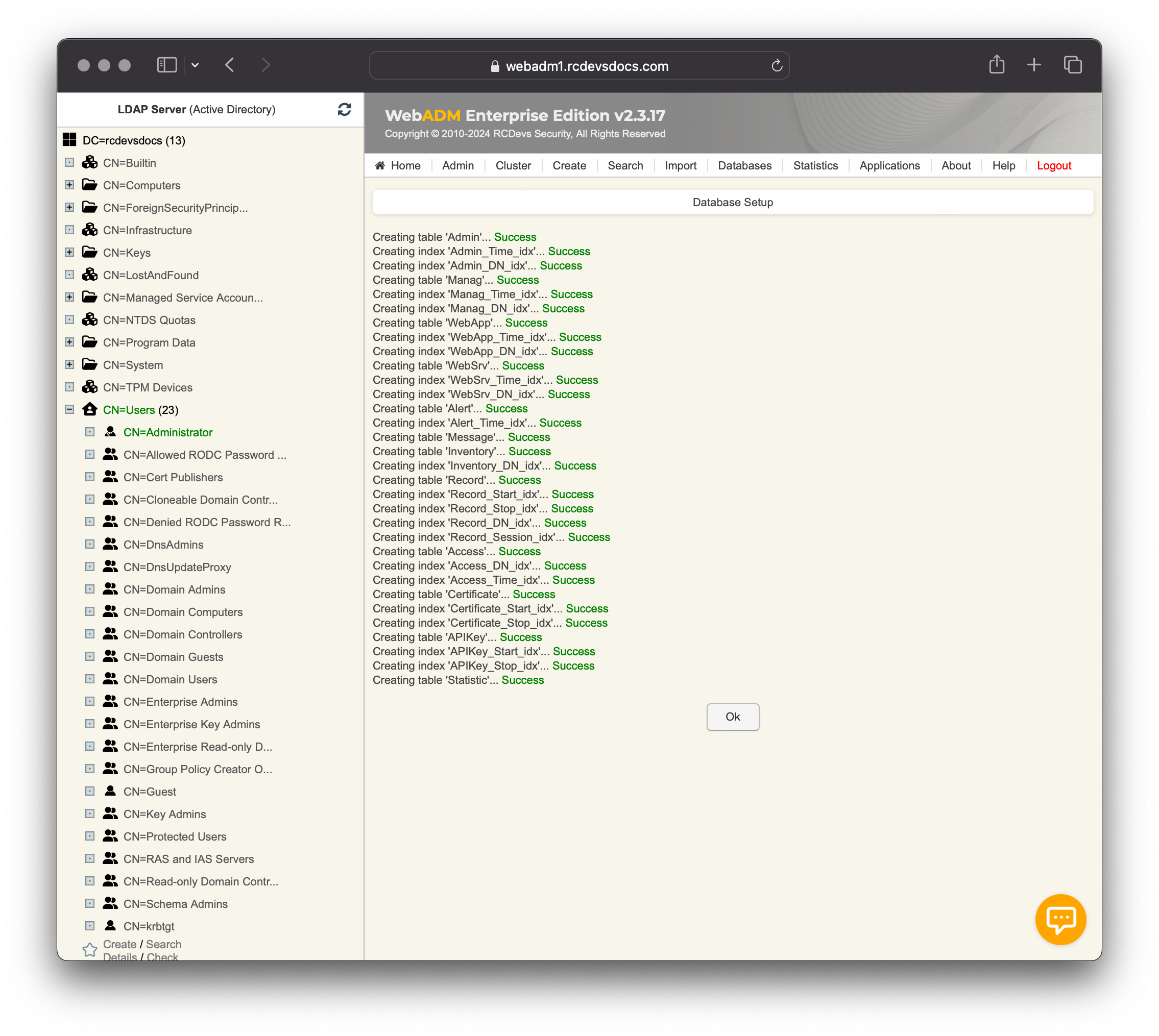
If it fails to create the SQL tables, it is likely because the SQL user does not have the necessary permissions on the database.
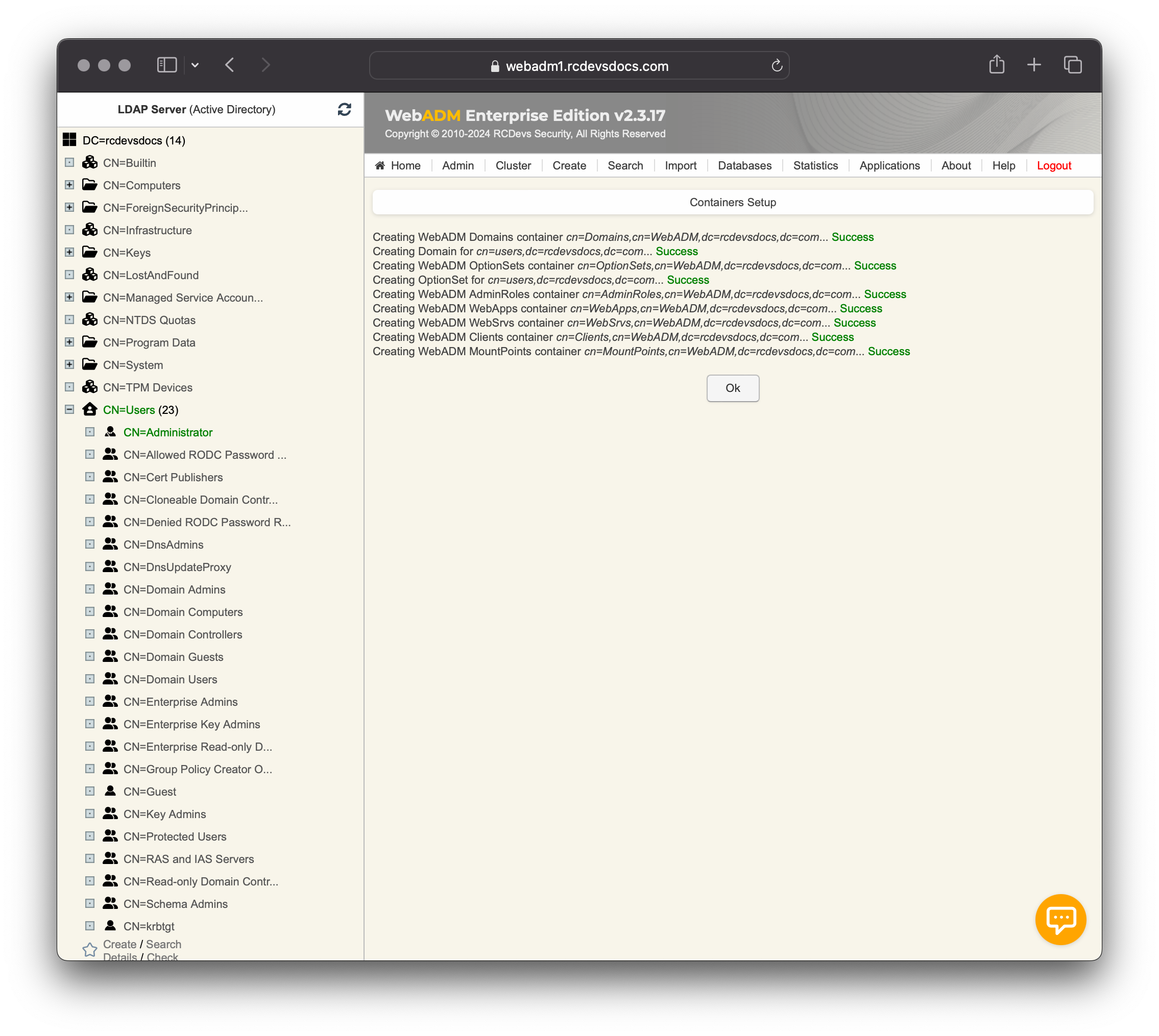
The installation of your standalone WebADM server is complete. You can continue with the WebADM Cluster/Failover guide if you intend to configure a WebADM cluster or start configuration of services and applications from Applications tab.
If you're not planning to set up a WebADM cluster, you can continue using the service account (proxy_user) and super administrator (super_admins) permissions on your directory.
