Overview
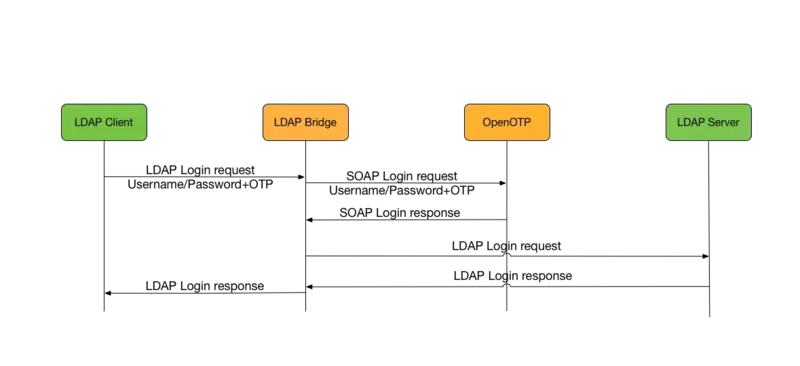
The main use-case of OpenOTP LDAP Bridge is enabling enterprise applications that use LDAP as an external authentication mechanism to work with OpenOTP. LDAP Bridge allows authentication to be delegated to an OpenOTP server transparently, without changing the LDAP back-end. From the client applications perspective, the main change is that it will use the LDAP Bridge as an LDAP server, instead of the backend-end LDAP server.
LDAP Bridge works by relaying LDAP messages to a back-end LDAP server. It intercepts user bind (LDAP authentication) operations and makes an OpenOTP call to authenticate the request with OpenOTP. It then sets the result of the bind request to the authentication result of the OpenOTP call.
One drawback of LDAP protocol is that LDAP bind does not support challenge-response or interactive user dialogue, which means that all authentication factors must be passed concatenated in one unique login request. Like RCDevs’ OpenOTP RADIUS Bridge, LDAP Bridge is not designed to be exposed to the internet, but rather to sit beside WebADM, or in a DMZ.
System Requirements
LDAP Bridge runs on Linux 64bit operating systems with GLIBC ≥ 2.5. The installation package contains all the required dependencies allowing LDAP Bridge to run on any Linux system without any other requirement.
LDAP Bridge requires a working OpenOTP+WebADM installation (version ≥ 1.4) connected to an LDAP backend.
The LDAP Bridge can be run on the same server as OpenOTP and WebADM. A standalone LDAP Bridge should meet the following requirements:
- Running a Linux distribution with Glibc ≥ 2.5 installed (RedHat, CentOS, SUSE, Debian, Ubuntu).
- At least a 1 GHz x86-64 processor (two cores or vCPUs recommended).
- 512 MB of RAM.
- At the very least 20 MB of free disk space.
Installation
Installation with dnf Repository
On a RedHat, CentOS or Fedora system, you can use our repository, which simplifies installation and updates.
dnf clean all
dnf install ldproxy
Installation with Debian Repository
On a Debian system, you can use our repository, which simplifies installation and updates.
Clean the cache and install WebADM with all WebApps & Services:
apt update
apt install ldproxy
Installation using the Self-Installer
You first need to download and install the LDAP Bridge software package. You can download OpenOTP LDAP Bridge on the RCDevs Website and copy it to your server. You can copy the package file to the server with WinSCP or scp. Then connect via SSH to your server, uncompress and run the self-installer package with:
gunzip ldproxy-1.2.*.sh.gz
bash ldproxy-1.2.*.sh
The installation process will automatically run the console-based setup script in bin/setup.
Configuration
Once the package is installed, you can run the setup script:
[root@ldproxy ~]# /opt/ldproxy/bin/setup
Checking system architecture...Ok
You insert the hostname of the LDAP Bridge server for the certificate generation:
Enter the server fully qualified hostname (FQDN): ldproxy.rcdevsdocs.com
Enter LDAP server IP or hostname [localhost]: ad1.rcdevsdocs.com
Enter LDAP server port [389]:
389
Enter LDAP protocol (ldap/ldaps) [ldap]:
ldaps
If the login mode defined in openotp is OTP, then you need to configure a bind account in ldproxy, if it's only LDAPOTP, you can keep it empty because ldproxy is able to forward the LDAP request with the correct password to the LDAP backend:
Enter a bindable LDAP account from the back-end with no specific permission: CN=ldap_bind,CN=Users,DC=rcdevsdocs,DC=com
Enter the LDAP account password:
You enter the IP of the WebADM server:
Enter WebADM server IP or hostname [localhost]: webadm1.rcdevsdocs.com
Found two server URLs:
> URL1: https://webadm1.rcdevsdocs.com:8443/openotp/
> URL2: https://webadm2.rcdevsdocs.com:8443/openotp/
Retrieving WebADM CA certificate... Ok
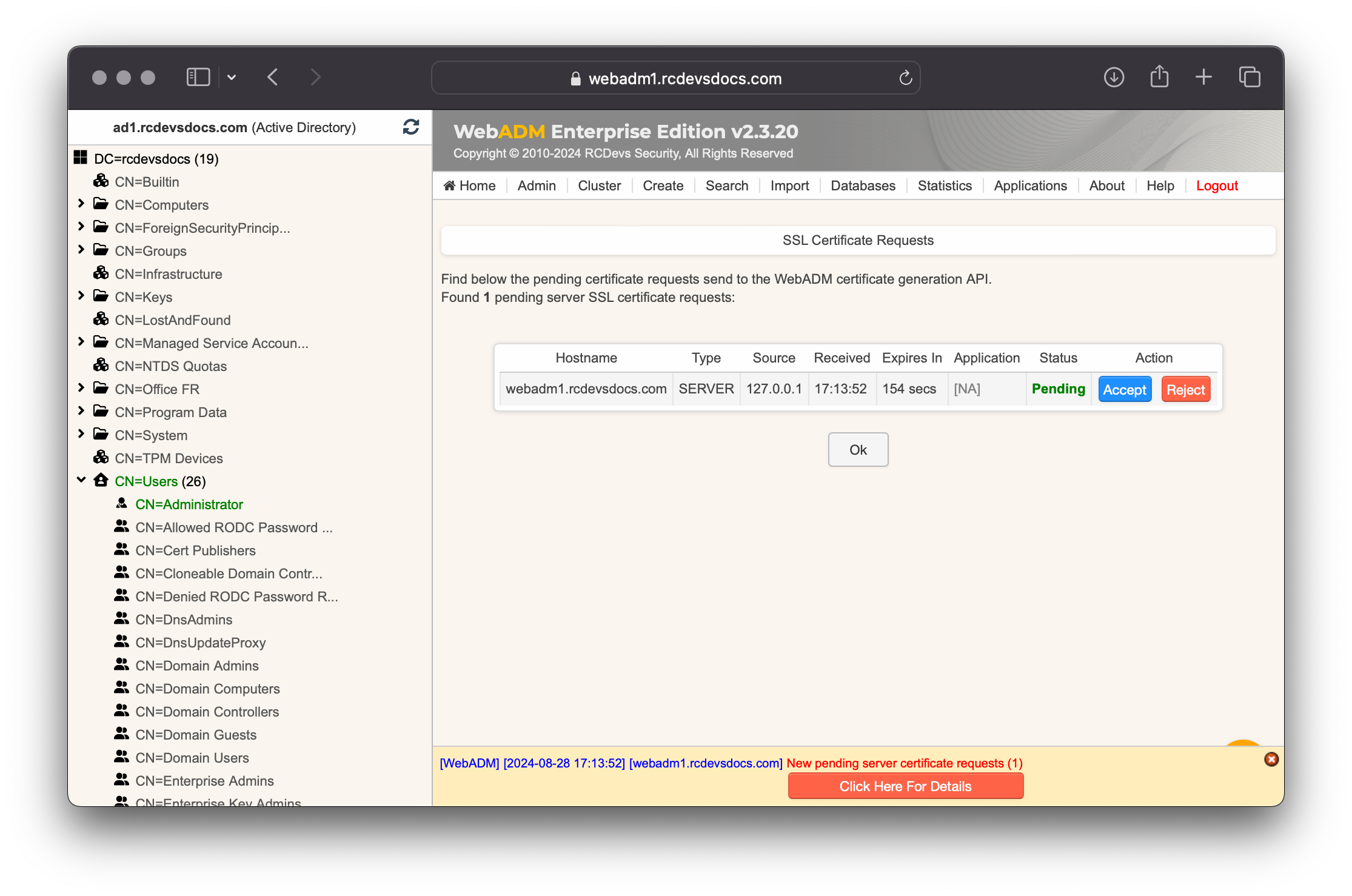
The setup needs now to request a signed SSL server certificate.
This request should show up as pending in your WebADM interface and an administrator must accept it!
Waiting 5 minutes for approbation... Ok
You connect to the WebADM Administrator Portal and approve the certificate request:
Updating OpenOTP configuration file... Ok
Setting file permissions... Ok.
Starting OpenOTP LDAP Bridge... Ok
Do you want OpenOTP LDAP Bridge to be automatically started at boot (y/n)[y]?
y
Adding systemd service... Ok
Do you want to register OpenOTP LDAP Bridge logrotate script (y/n)[y]?
y
Adding logrotate script... Ok
OpenOTP LDAP Bridge has successfully been setup.
You can use ldapsearch for testing. If it's not already available, you can install it with openldap-clients package. In this example, the user administrator is reading information about john. For this test, the authentication policy is set to LDAP on OpenOTP side.
[root@webadm1 lib]# /opt/slapd/libexec/ldapsearch -v -xLLL -H ldap://webadm1.rcdevsdocs.com:10389 -D "CN=Administrator,CN=Users,DC=rcdevsdocs,DC=com" -W -b "DC=rcdevsdocs,DC=com" 'sn=Doe'
ldap_initialize( ldap://webadm1.rcdevsdocs.com:10389/??base )
Enter LDAP Password: ***********
filter: sn=Doe
requesting: All userApplication attributes
dn: cn=John Doe,cn=Users,dc=rcdevsdocs,dc=com
objectClass: top
objectClass: webadmAccount
objectClass: posixAccount
objectClass: person
objectClass: organizationalPerson
objectClass: USER
cn: John Doe
sn: Doe
l: Luxembourg
title: Engineering
userCertificate:: MIIHGjCCBQKgAwIBAgIRANbeaPtj9+hbsuR9m3qdKWYwDQYJKoZIhvcNAQEL
BQAwUjEXMBUGA1UEAwwOUkNEZXZzIERvY3MgQ0ExCzAJBgNVBAsMAkNBMR0wGwYDVQQKDBRSQ0Rld
nMgRG9jdW1lbnRhdGlvbjELMAkGA1UEBhMCTFUwHhcNMjQwODIzMTU1NDI0WhcNMjUwODIzMTU1ND
I0WjCB1TEcMBoGA1UEAwwTcmNkZXZzZG9jc1xqb2huLmRvZTEYMBYGCgmSJomT8ixkAQEMCGpvaG4
uZG9lMRowGAYKCZImiZPyLGQBGRYKcmNkZXZzZG9jczEdMBsGA1UECgwUUkNEZXZzIERvY3VtZW50
YXRpb24xFzAVBgNVBGEMDlZBVExVLTAwMDAwMDAwMQwwCgYDVQQEDANEb2UxEzARBgNVBAcMCkx1e
GVtYm91cmcxDTALBgNVBCoMBEpvaG4xFTATBgNVBBQMDCszMzYxMjM0NTY3ODCCAiIwDQYJKoZIhv
cNAQEBBQADggIPADCCAgoCggIBALHQYkK/Z9oBjziU3EByWdwhFpI1c007v80nZkuMJbG6ZGSwW9T
IaFfwKCwj0pAccT+n8U+BxjUJ7oYxt6C6hkKC8CjdvNXXBra6E6gh82IS+coQ9xFx11dUIv4A09Oq
/CPpZKrPklzJdzk/EsNBHnE3X/UZpHOtQ8CEFpa30yskaMqSWvhJoHX82dbgp95D28ojRxcKfkCd2
HvzDhEz3fRVEeHZRRZsggZ+rLfDQDIPdacrMzF33Hnjo9rlqj5MkPFvVdeiioPQb9BQJw63TIncOP
XZ8kSFuCWHAwPTSeFgIfKYK3hW3fP+jiJG2NdHbsiD2spepS8mHvt1+gZh4xktQz/o2PRa5bgKkLC
hEyuPVkissumRsQhNW8ng2omZJ8kfceQY2in93ZW8zlGDTzEE61HtZqeQaFlAzgzO06GhFUr1atLb
nhYakbKfVaFlP/nT6oHtwWP5znBMfvCQ/aH4vQksKkL1o5ka/RFVoo0SJWap2/YIZWVlpXl7TMecH
107mh9xIBPfwI817le2l29/LEm3Rh2ETL2yvxH3GwsHC/zlothKPZGudiHs5YRrilP69XgroVyTf9
Ofe+LOEoazK3lTnWMEFQCDmHzHGSP4ttACb//8rnFFi0nNDN839iYK2f0IgSUOdePrCBcorBA6wFP
YRq2fsrvEpNtbW9nLAgMBAAGjggFlMIIBYTALBgNVHQ8EBAMCBeAwKQYDVR0lBCIwIAYIKwYBBQUH
AwIGCCsGAQUFBwMEBgorBgEEAYI3FAICMB0GA1UdDgQWBBQWD07vKBLVYO9f+TiAM/yRKRQswzBLB
gNVHREERDBCgRdqb2huLmRvZUByY2RldnNkb2NzLmNvbaAnBgorBgEEAYI3FAIDoBkMF2pvaG4uZG
9lQHJjZGV2c2RvY3MuY29tMHUGCCsGAQUFBwEBBGkwZzArBggrBgEFBQcwAYYfaHR0cDovL2lhbS5
yY2RldnNkb2NzLmNvbS9vY3NwLzA4BggrBgEFBQcwAoYsaHR0cDovL2lhbS5yY2RldnNkb2NzLmNv
bS9jYWNlcnQvP2Zvcm1hdD1kZXIwLwYDVR0fBCgwJjAkoCKgIIYeaHR0cDovL2lhbS5yY2RldnNkb
2NzLmNvbS9jcmwvMBMGCysGAQQBgo45AwEBBARVU0VSMA0GCSqGSIb3DQEBCwUAA4ICAQCah/71Yg
POlhpd3ZgqwIr8hINu+xK7eVackSpS5DC2mJZp4uxDn0/MqBKFVhwYNWGKsXBnTcKBosCJPK38bRj
gEqQL8mvZaFSLG+YpkjTBi1ScGww8iCSf1xC03s/2cwBSxGjRD/SuSmB5FJkQhG6ixZ1Udds1aJbM
SyTpTDj3UbBVdJ4uDIYq1BAtx8ZFlxQB6f2hFbs+fi0p+FXERTjPjz3RqoFiQfGhQyNOk6i5z2rn9
mESfF7SYMsrSFYWfgT8Xl7sqLXdd8GeYVKBngx/3k5M6jyWdSUA6m+kQCHjb+gA3K9jyjIEXRAIRo
A/ulejxycTIFixT3Z2W0IxtVCIAIdA0c2wmiFrj8x0sHPcB75ajQj5g4VHAGpPUd95yb0v5JwLp87
CqIJs4YaDZutoZmLLuCs8PY1ocy/7qx7AMIww8px3tTF+aZY6HxXd/TJiGT1zL6yMoy39YJ7XzvFq
WRPA+fJgk76UpR0USsgLCo5ZM1U+nAht6EnOQn94ih470cpuKny483jyqZ+IJKwYlECFKfS0oq4Lu
Hx5P9ZCem4mi5L6s18G58N4SB2VsC8z9Bobqu0DhHQAf4TFyJGGPkNUT0oD0s251XuecqAAgwBshg
6+zsK5eowomeTPMmxoxhoEoPh70wXNIZnIL7zIMt0c047LxPQvrMOlLKjzIg==
givenName: John
initials: JD
distinguishedName: cn=John Doe,cn=Users,dc=rcdevsdocs,dc=com
INSTANCETYPE: 4
WHENCREATED: 20240712124050.0Z
WHENCHANGED: 20240828153428.0Z
displayName: John Doe
USNCREATED: 14219
MEMBEROF: CN=IT,CN=Groups,DC=rcdevsdocs,DC=com
USNCHANGED: 23193
name: John Doe
OBJECTGUID:: Bf2fWDfqjEWSg8kqYhO0Xw==
USERACCOUNTCONTROL: 66048
BADPWDCOUNT: 0
CODEPAGE: 0
COUNTRYCODE: 0
BADPASSWORDTIME: 133693327410327136
LASTLOGOFF: 0
LASTLOGON: 133693327410483467
PWDLASTSET: 133687213288850445
PRIMARYGROUPID: 513
OBJECTSID:: AQUAAAAAAAUVAAAA8woHk48HVhwP3f/UTwQAAA==
ACCOUNTEXPIRES: 9223372036854775807
LOGONCOUNT: 0
sAMAccountName: john.doe
SAMACCOUNTTYPE: 805306368
userPrincipalName: john.doe@rcdevsdocs.com
OBJECTCATEGORY: CN=Person,CN=Schema,CN=Configuration,DC=rcdevsdocs,DC=com
DSCOREPROPAGATIONDATA: 16010101000000.0Z
LASTLOGONTIMESTAMP: 133685301229176202
mail: john.doe@rcdevsdocs.com
mobile: +33612345678
preferredLanguage: EN
uidNumber: 500
gidNumber: 100
UNIXHOMEDIRECTORY: /home/john doe
loginShell: /bin/bash
webadmData: OpenOTP.LastConfirm=MjAyNC0wOC0yMiAxODowMDo0NQ==,OpenOTP.ConfirmCo
unt=Mg==,OpenOTP.Device1Type={wcrypt}n/pIPtZfyL5UyIZJE+VOQQ==,OpenOTP.Device1
Name={wcrypt}es6bWPErjCmKc/Mk3d10VQ==,OpenOTP.Device1Data={wcrypt}gaD+BtCKMCM
JZJZekT/v83cmHwPxcFqBBq7BjPlG4sjV70Pfbn8y8jxRACrW90O+97s7S5yhMSoHD/B4RIsKHxfG
aeORaG1CIXb5Hf6juwRXwpkRj5wkG+FtPmrz+ny+,OpenOTP.Device1State={wcrypt}FXfNdbf
KWVSPsa5e1cQB2w==,OpenOTP.ListInit={wcrypt}WshcspYjgkFtjidfxaZ592DEni6JqJJPGT
NY0x0mjxM=,OpenOTP.ListState={wcrypt}txhBDGEYnZwn5Oi2HdvJEw==,SpanKey.PublicK
ey={wcrypt}13QSiYkcjWR9FvL6yoiYIEvkyIsyLSPVx6p2iqTrR+z/RhaZO2o4oqqhdKCOAQsovo
O6HadWHm7E1x64QfbivMrqE11GY1pcA2Q+KBX3qtvEeqIG7PWl5oTBSD8G3mibBQuVxUqCtwa0ojk
WOLkJGjb+cNTQMbE5UJE7Lq4rVZLHGrVFRloLALjIEzhOeDKHGBgEW3kbckc6cChSO+9sfkR1DFy0
KYflbK0QvcuI+WjbnYs8FR1hPdX7Q69pw398QstmGeLB3Ha1JRxO+GOA3qCOiFsUMtslT/tb3Zu1T
GmfpyBS45HWJUGNH+il5cUNIHiPRlkTJzfSFkhxvCF5TP95y2nwHMUgKOs/NOd9s3l171H3L1df9W
A+PxINiZqCykhMmRacbN5TWcSPkrg+Og==,SpanKey.KeyType={wcrypt}ZgpdptbQditu2iVG/E
nmkg==,OpenOTP.AppKeyInit={wcrypt}/kmp+6/zF4Ny3U8lcHxZu3/nCKfvULmk/QoqB6Ggn2o
=,OpenOTP.TokenType={wcrypt}DbPpUIEX5cqdqZBYOIhgqw==,OpenOTP.TokenKey={wcrypt
}AjMDLUOo/8PKBbcOnvKJ16YO2Zlru5GXw28MgYbfTE8=,OpenOTP.TokenState={wcrypt}txhB
DGEYnZwn5Oi2HdvJEw==,OpenOTP.TokenID={wcrypt}0rpETwNJDA7KIcnnUfQHBjlebKkugkbt
5PD2/lx9Ao/F5PsJw+v7b1S6fCr0V7r/JQ+eeiyU1QnxtHPczsdC/DUm3EqDIcj8RhtwBG4EufU=,
OpenOTP.TokenSerial={wcrypt}+QlxrHOnCTbLnr1iOuMBV0kmWDsOejZOQo+lnm3wl4rYNotNM
AE4c8fQB7dtBWui,OpenOTP.TokenModel={wcrypt}ld2ZhPiDZPz1JNeiYqXI8waqMMwmLy18Bn
JIcVOu6ac=,OpenOTP.LastReject={wcrypt}NEiD1ISerBOl+MqHavTqXH+jORmrBqpYZq4h7jd
qHeY=,OpenOTP.RejectCount=Mw==,OpenOTP.LastLogin=MjAyNC0wOC0yOCAxNzozNDozOA==
,OpenOTP.LoginCount=MTI=,DataMode=A7RC9aM=
# refldap://ForestDnsZones.rcdevsdocs.com/DC=ForestDnsZones,DC=rcdevsdocs,DC=co
m
# refldap://DomainDnsZones.rcdevsdocs.com/DC=DomainDnsZones,DC=rcdevsdocs,DC=co
m
# refldap://rcdevsdocs.com/CN=Configuration,DC=rcdevsdocs,DC=com
You can also define settings manually in ldproxy.conf:
-
cert_file: OpenOTP client certificate. -
cert_password: OpenOTP client certificate's password. -
client_id: the client ID that will be set in every request to OpenOTP, who can then match requests to a client policy with the same name (or alias). -
denied_dn: a list of users who are not allowed to be authenticated by OpenOTP, they will receive an authentication failure. -
domain: the WebADM domain that will be set on every request to OpenOTP. -
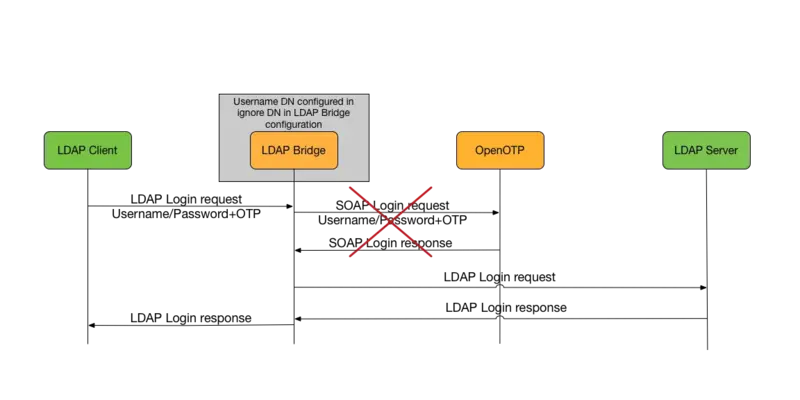
ignored_dn: a list of users who don't need to use OpenOTP, the authentication is not redirected to the OpenOTP server.
-
server_policy: the load-balancing policy of requests between OpenOTP servers, if two servers are defined in server_url. -
server_url1,server_url2: OpenOTP server(s) url(s). -
soap_timeout: the time in seconds without before LDproxy’s connection to OpenOTP times out. The LDAP clients of LDproxy must have a higher tolerance than soap_timeout to timeouts when connecting to LDproxy. -
status_cache: the time in seconds between health polls of the backend OpenOTP servers. -
user_settings: which are the public OpenOTP settings that will be passed in every request. OpenOTP must be configured with “Allow Request Settings” in WebADM. These settings will have priority over any settings defined on the users, groups, client policies and OpenOTP configuration.
Upgrades of LDAP Bridge will overwrite the file /opt/ldproxy/conf/ldproxy.conf.default, which will indicate the default values for any new configuration directive added by the upgrade. If new directives or any significant change has been added, it will be mentioned in /opt/ldproxy/RELEASE_NOTES.
LDAP sections
These sections contain per LDAP backend configurations:
-
bind_dnandbind_pw: Service account used for OTP user binds to the LDAP back-end. It must be a bindable LDAP account with no specific permission. -
domain: the WebADM domain that will be set on every request to OpenOTP. -
name: the name shown in logs. -
security: Specify a set of security strength factors -
suffix: base dn corresponding to the backend, it should not be included in a previous defined ldap backend. -
tls: tls configuration{[try-]start|[try-]propagate|ldaps}[tls_cert=<file>][tls_key=<file>][tls_cacert=<file>][tls_cacertdir=<path>][tls_reqcert=never|allow|try|demand][tls_ciphersuite=<ciphers>][tls_crlcheck=none|peer|all]. -
uri: ldap backend uri.
Client sections
ldproxy.conf can also contain client sections, which can, for requests coming from a specific IP or a subnet, override client_id, domain and ignored_dn.
client {
name my_client_ldap_application
client_addr 192.168.3.237
client_mask 255.255.255.0
client_id App_identifier
domain rcdevsdocs
ignored_dn "cn=administrator,cn=Users,dc=rcdevsdocs,dc=com"
}
Client Logs
name: It could be any name you want to give this section.client_addr: The IP address you want to assign the client configuration. It could be also a full network or subnet.client_mask: The subnet mask for the IP/network defined in client_address. Put 255.255.255.255 in case you want to use only one IP.client_id: The ID assigned to this client. Needed for WebADM Polcies.domain: You can set a specific domain here to replace the general configuration.ignored_dn: You can also set a specific ignored_dn configuration here to replace the general configuration.
Below, you can find WebADM logs for an authentication example using this client configuration.
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] New openotpSimpleLogin SOAP request
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] > Username: cn=administrator,cn=users,dc=rcdevsdocs,dc=com
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] > Password: xxxxxxxxxxxx
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] > Settings: ChallengeMode=No
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] > Options: DIAGMSG,NOVOICE,-U2F,LDAPDN
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Registered openotpSimpleLogin request
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Verified LDAP user: CN=Administrator,CN=Users,DC=rcdevsdocs,DC=com (cached)
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Resolved LDAP groups: group policy creator owners,domain admins,enterprise admins,schema admins,administrators,denied rodc password replication group (cached)
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Started transaction lock for user
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Found 50 user settings: LoginMode=LDAP,OTPType=TOKEN,PushLogin=Yes,MaxWeak=1,BlockNotify=MAIL,ExpireNotify=MAIL,WeakNotify=MAIL,ChallengeMode=Yes,ChallengeTimeout=90,OTPLength=6,OfflineExpire=30,MobileTimeout=30,EnableLogin=Yes,SelfRegister=Yes,PasswordReset=Yes,HOTPLookAheadWindow=25,TOTPTimeStep=30,TOTPTimeOffsetWindow=120,OCRASuite=OCRA-1:HOTP-SHA1-6:QN06-T1M,U2FPINMode=Preferred,SMSType=Normal,SMSMode=Ondemand,ReplyData=[2 Items],MailMode=Ondemand,PrefetchExpire=10,LastOTPTime=300,ListChallengeMode=ShowID
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Found 1 request settings: ChallengeMode=No
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Found 10 user data: PwnedState,Device1Type,Device1Name,Device1Data,Device1State,TokenType,TokenKey,TokenState,TokenID,TokenSerial
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Requested login factors: LDAP
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] LDAP password Ok
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Updated user data
[2024-08-28 17:48:58] [192.168.4.160:54248] [OpenOTP:6FTPFVBD] Sent login success response
LDAP Ports
LDAP Bridge provides the LDAP service over the following ports:
- TCP 10389 for un-encrypted LDAP and TLS.
- TCP 10636 for LDAP over SSL.
The LDAP Bridge’s default listening network interface and ports can be changed by creating an environment file /opt/ldproxy/conf/ldproxy.env with the following configurations:
##This is ldproxy.env example
INTERFACE=0.0.0.0
PORT_STD=10389
PORT_SSL=10636
Maintenance and Troubleshooting
This section should cover your common administrative tasks concerning LDAP Bridge. For additional support, you can contact RCDevs’ commercial support if you are a client or our Google Group if you are using the freeware edition of OpenOTP.
Starting and Stopping
If during the setup, you’ve let the installer set the LDProxy init scripts and systems service files on your machine, the LDAP Bridge should start at machine boot. You should also be able to start and stop the LDAP Bridge through your distribution’s usual commands, such as systemctl start ldproxy for distributions using systemd like RedHat Enterprise Linux 7.
Alternatively, you can use
/opt/ldproxy/bin/ldproxy start | restart | stop | debug
or systemctl:
systemctl restart ldproxy
Backup and Restore
You can back up and restore easily the configuration with these commands:
/opt/ldproxy/bin/backup /tmp/ldproxy.bkp.gz
/opt/ldproxy/bin/restore /tmp/ldproxy.bkp.gz
Upgrading and Un-Installing
If LDAP Bridge was installed using RCDevs repository, it will be updated with the system when you will execute yum update or apt-get upgrade.
If it was installed with the tar file, you can download and install it as you did for your first installation. The installer will offer you the option of upgrading your installation.
Be aware that, to do so, the installer will stop LDProxy. As a matter of principle, you should back up the /opt/ldproxy/ directory before the upgrade. You can then restore the directory if anything breaks and restart the LDProxy service.
The installer also gives you the option of removing an existing LDProxy installation.
You can reset your installation by executing /opt/ldproxy/setup reset, which removes any init, systemd and logrotate files the installer put on the machine. This will also remove the log files, SSL certificate and secret key.
Troubles and Known Issues
You can start LDAP Bridge in debug mode to get a verbose output of what the proxy does on your terminal.
/opt/ldproxy/bin/ldproxy debug <loglevel>
If you omit <loglevel>, it will be set to stats by default, but you can also choose another log level:
| log level | Description |
|---|---|
| any | enable all debugging |
| trace | trace function calls |
| packets | debug packet handling |
| args | heavy trace debugging |
| conns | connection management |
| BER | print out packets sent and received |
| filter | search filter processing |
| config | configuration processing |
| ACL | access control list processing |
| stats | stats log connections/operations/results |
| stats2 | stats log entries sent |
| shell | print communication with shell backends |
| parse | print entry parsing debugging |
| sync | syncrepl consumer processing |
| none | only messages that get logged whatever log level is set |
