Product Documentation
This document is an installation guide specifically for the OpenOTP Credential Provider for Windows. Therefore, the installation or configuration of WebADM, including token registration, is not covered here. For detailed installation and usage guides for WebADM, please refer to the RCDevs WebADM Installation Guide and the RCDevs WebADM Administrator Guide, available through the RCDevs documentation.
Product Overview
The OpenOTP Credential Provider for Windows integrates RCDevs OpenOTP authentication into the Windows login process. In the latest versions, it also captures event logs related to users authenticated with OpenOTP and sends these events to the WebADM Framework.
To set up this integration, ensure that WebADM/OpenOTP is installed and configured. For detailed instructions, refer to the WebADM Installation Guide and Manuals.
System Requirements
The OpenOTP Credential Provider runs on any x86/x64 Windows platforms starting with Windows Vista and Windows Server 2008 versions.
Your environment should meet the following requirements:
- x86/x64 Windows 2008 Server/Vista or later.
- Computer joined to an AD domain or in a Workgroup. For computers out of an AD domain, please refer to the dedicated documentation for configuration details.
- Network access.
- An instance of WebADM and OpenOTP running in your network.
- Connection to OpenOTP web service.
The OpenOTP Credential Provider operates on Server editions with Desktop Experience or Core edition. All features of OpenOTP-CP are supported with Desktop Experience, unlike Core editions.
The Core version supports the following local and Remote Desktop login scenarios:
- The RunAs scenario functions if the App Compatibility feature on demand has been installed. In this scenario, you can browse a program through explorer.exe, then right-click on it, and select "RunAs OtherUser".
Preliminary Information
Administrative/elevated permissions are necessary on any computer to correctly set up and/or change the OpenOTP Credential Provider’s configuration.
To set up the provider correctly, please gather the following information which will be required during the installation process:
-
The URI(s) of the OpenOTP web-service(s) (mandatory):
These URIs are mandatory because the client needs to know where the OpenOTP SOAP network API can be reached. They should be entered as a comma-separated list. At least one URI is necessary. -
Your local domain (optional):
This is needed to specify a domain that is not the default on the OpenOTP side. -
Custom login text or tile caption (optional):
Text displayed on the Windows login pane. -
Client ID (optionnal but recommended):
An identifier used to apply client policies configured on WebADM side. Up to three Client IDs can be configured to target different scenarios: Logon UI, CredUI, and RDP. -
Certificate Authority (CA) file (optional)
-
Certificate file (optional)
-
Certificate’s password (optional)
-
SOAP timeout delay (optional)
The login mode LDAP+OTP must be configured on the server-side in WebADM, as the Windows Domain Controller (DC) requires the complete credentials (including LDAP password) to issue a Kerberos ticket.
Installation and Configuration
The setup and configuration of the Credential Provider can be completed in approximately 5 minutes using the installer, which handles both setup and configuration. The provider can also be automatically deployed to your clients, a process covered later.
Administrative/elevated permissions are required on any workstation to correctly set up and modify the OpenOTP Credential Provider’s configuration. To proceed, please run Windows PowerShell or Command Prompt as Administrator. Right-click on Windows PowerShell and select "Run as Administrator".
Local Installation
First, you need to download the OpenOTP Credential Provider for Windows for either x86 or x64 architecture.
After downloading, extract the files from the archive onto your Windows machine(s). Locate and run the MSI file, then click on Next to proceed with the installation.
Accept the End-User License Agreement and click on Next.
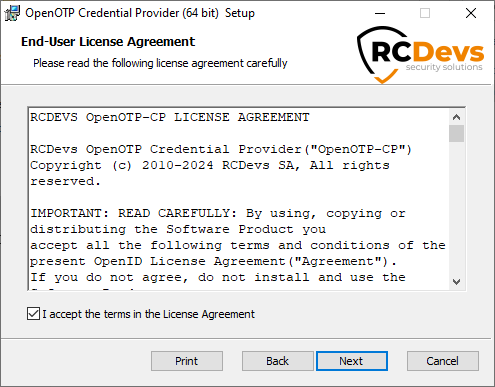
Now, you need to select which features to install. The Core Components are mandatory. Additionally, you can choose to install the Credential Provider Filter to set it as default provider and Smartcard Credential Provider. Please note that Smartcard login is supported starting from Windows 8 or Windows Server 2012 and requires a 64-bit system.
You may also adjust the default installation directory as desired. Once you have made your selections, click Next to proceed.
Installing the provider as default disables all other credential providers on the target system. Only Credential Providers provided by RCDevs will be available for login. In case of any issues, you can still log in using other providers using Windows failsafe boot. It is also possible to configure OTP login in failsafe mode, which will be discussed later.
To log in to a Windows Server via RDP client with a One-Time Password, the OpenOTP Credential Provider must be installed by default on the remote host to enable OTP login.
Starting from version 3.0.14, you can install and deploy the Event Watcher. This component captures and transmits Windows event logs to WebADM servers based on XPath rules. By default, it collects and sends all logon and logout event logs generated by users who have been previously authenticated with OpenOTP.
During testing, do not install OpenOTP Credential Provider as the default provider initially. Perform a login test before choosing OpenOTP Credential Provider as the default provider.
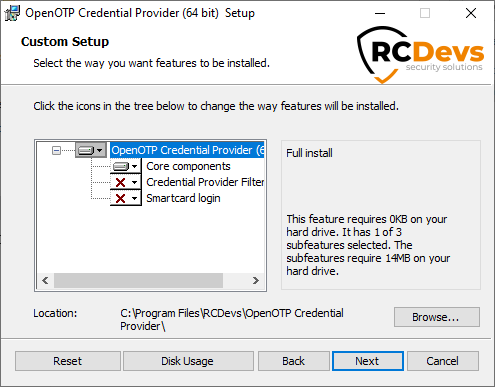
On the first configuration page, you need to configure the following elements:
-
WebADM URL settings:
- If you select Auto, fill the WebADM URL with at least one of your WebADM server URLs (e.g., https://your-webadm-ip-address-or-dns-name). Click on Configure, which will automatically populate the Server URL, additional Server URL, and Certificate Authority file fields. Note: If your WebADM URL is defined as
https://your_webadm_server, it will attempt to accesshttps://your_webadm_server:443/srvurl/openotp. If defined ashttps://your_webadm_server:8443, it will tryhttps://your_webadm_server:8443/srvurl/openotp.
- If you select Auto, fill the WebADM URL with at least one of your WebADM server URLs (e.g., https://your-webadm-ip-address-or-dns-name). Click on Configure, which will automatically populate the Server URL, additional Server URL, and Certificate Authority file fields. Note: If your WebADM URL is defined as
-
Server URL (Manual mode):
- If you select Manual, configure at least the Server URL setting with one of your OpenOTP SOAP URLs. Example:
https://your_webadm_server:8443/openotp.
- If you select Manual, configure at least the Server URL setting with one of your OpenOTP SOAP URLs. Example:
-
Loading Text (optional):
- This text is displayed during a connection attempt to WebADM. It can be useful for prompting the user, especially when using push login. For example, you could remind the user to check their mobile phone.
-
Login Text (optional):
- Optionally, define a login text that will be displayed to the user during authentication.
-
Client ID (optional): The default Client ID used in the LogonUI scenario to match an OpenOTP Client policy configured on WebADM. If RDP and CredUI Client IDs are not configured, all authentication scenarios will default to this Client ID.
Click on Next
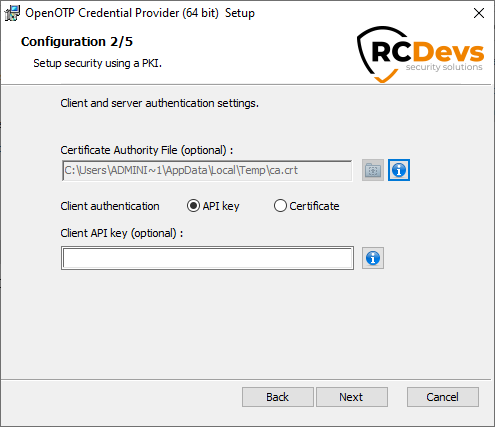
On the second configuration page, you can configure the following elements:
-
Certificate Authority File: This must contains the CA file of your WebADM servers. The file will be automatically copied into the installation folder of OpenOTP Windows Credential Provider. -
API Key(optional): if you configured OpenOTP to require an API Key, you can set it with these settings. -
Certificate FileCertificate Password: if you configured OpenOTP to require a client certificate, you can set it with these settings.
One of these two client authentication methods must be configured if you intend to publish and use the OpenOTP Web Service through WAProxy or your reverse proxy.
OpenOTP Credential Provider will automatically download the CA certificate on the default WebADM server port if you are using the automatic configuration. You can also obtain it manually with https://mywebadmserver/cacert.
Click on Next
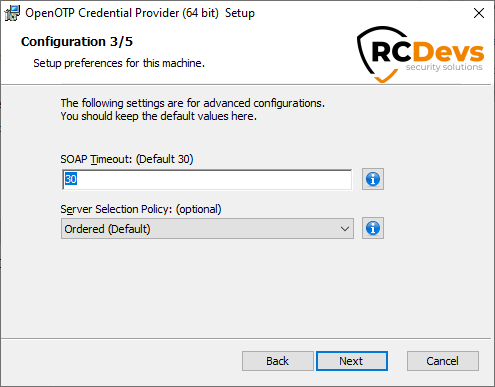
On the third configuration page, you can configure the following elements:
SOAP Timeout(Default to 30) : this is the timeout for connection to the Server URL.Server Selection Policy(Default to Ordered) : If you have more than one webadm server, this is the way the Windows OpenOTP Credential Provider will contact them.Ordered: the first server is always preferredBalanced: the server is chosen randomly for each requestConsistent: the server selection depends on the user ID
Click on Next.
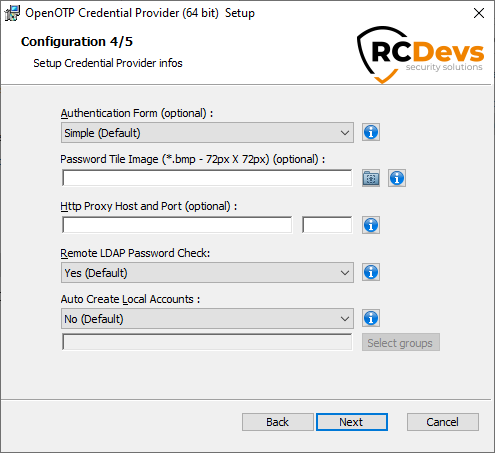
On the fourth configuration page, you can configure the following elements:
Authentication form(Default to Simple). You have 2 choices:Simple: On the Windows login page, you will have 2 fields in the first step (Username and Password LDAP), after pressinglogin, you will have a second screen with the OTP field.Normal: With this option, you will have 3 fields on the login page, one for the Username, one for the LDAP password and the last one for the OTP.
Login Tile Image(optional) : the path of the image on the filesystem displayed on the login page (must be a 128x128px 24 bit bitmap file)Http Proxy Host and Port(optional) : this config is for HTTP proxy. If you are running OpenOTP behind an HTTP proxy you need to set the host and the port of the proxy.Remote LDAP Password Check(Default to Yes) : enable this option if your OpenOTP server does not use your AD or if this host is not connected to the Windows Domain.Auto Create Local Accounts(optional): this can be enabled when the host is not connected to a Windows domain, and you want the Credential Provider to create user accounts at first login. You can also select local groups to be populated by these auto-created local accounts.
Click on Next.
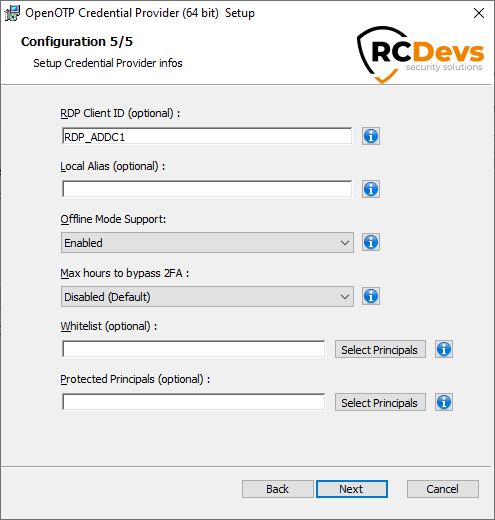
On the fifth configuration page, you can configure the following elements:
RDP Client ID(optional): TheRDP Client IDcan be configured to match a specific OpenOTP client policy for RDP authentications. If not set but theCredUI Client IDis configured, RDP authentications will default to the CredUI Client ID. If the CredUI Client ID is also not set, RDP authentications will default to the value of the default Client ID.CredUI Client ID(optional): TheCredUI Client IDcan be configured only through the Windows registry when the CP is installed. It can be used to match a specific OpenOTP client policy for CredUI scenarios. If not set, CredUI authentication scenarios will default to the value of the defaultClient ID.Local Alias(optional): when attempting a local login, the domain part of the username will be automatically replaced by the local alias before sending the OpenOTP request.Offline Mode Support(Default to Yes): enable this option if you want to use the offline mode of Windows Credential Provider. This will permit you to authenticate to your machine even if OpenOTP service is not reachable. From version 3.0.15, the offline mode is supported in CredUI scenarios.Max hours to bypass MFA(Default to Disabled): this setting can be used to define for how much time the OpenOTP Windows Credential Provider will not ask for a MFA since the last login.Whitelist(optional): List of users/groups SID separated by semicolons (;) that will bypass the OpenOTP authentication.Protected Principals(optional): A list of security principal SIDs (users and/or groups), separated by semicolons (;). Specifies the users and groups for whom the OpenOTP call will be enforced. This setting works in conjunction with the Whitelist.
For example, if you want to enforce OpenOTP authentication only for the Domain Admins group, you need to add the Domain Users group to theWhitelistand add the Domain Admin group to theProtected Principals.
You can get a user SID using this command from a cmd prompt :
wmic useraccount where (name='Username' and domain='Domain') get sid
Click on Next.
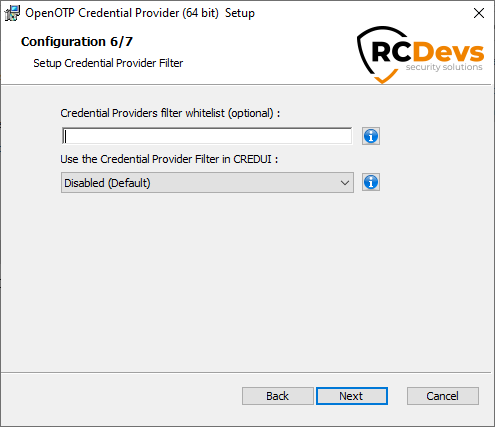
If you selected the Credential Provider Filter feature, you will be presented a sixth page.
Credential Providers Filter Whitelist(optional): If you are installing OpenOTP Credential Provider as default, no other providers will be available during login. Use this setting to override this behavior and allow specific credential providers to be used.
Please keep in mind that the login process will only be as secure as the least secure of the available credential providers!
This is a list of the allowed Credential Providers CLSID separated by ";", a CLSID is of the form {60b78e88-ead8-445c-9cfd-0b87f74ea6cd}.
All the CLSID of the registered Credential Providers on your machine can be found in the following registry location :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\
This may change depending on your Windows version and if you have installed other third party Credential Providers.
To use FIDO2 authentication for RDP logins, you must whitelist Microsoft's FIDO Credential Provider during the installation of the OpenOTP Credential Provider. The key for this Credential Provider is {F8A1793B-7873-4046-B2A7-1F318747F427}. Additionally, the following Group Policy object must be adapted if you wish to use FIDO authentication for the below scenarios.
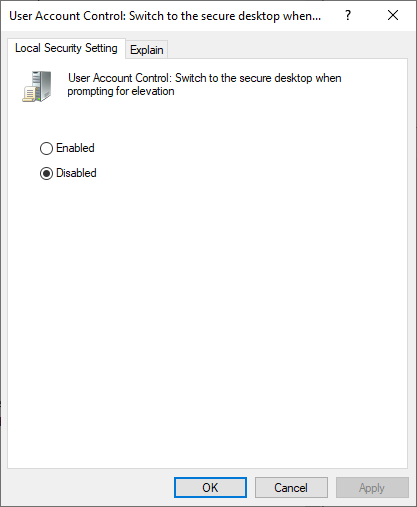
You can find them in gpedit.msc > Windows Settings > Security Settings > Local Policies > Security options:
User Account Control: Switch to the secure desktop when prompting for elevationmust be set toDisabled
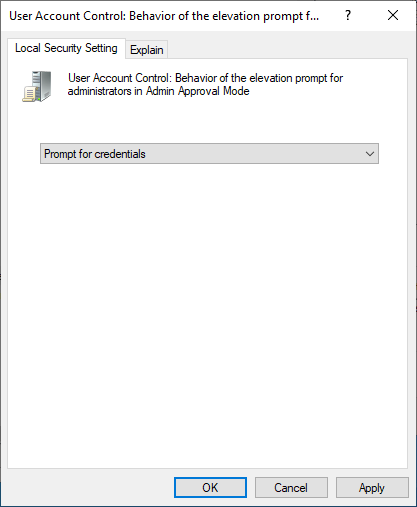
User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Modemust be set toPrompt for Credentials
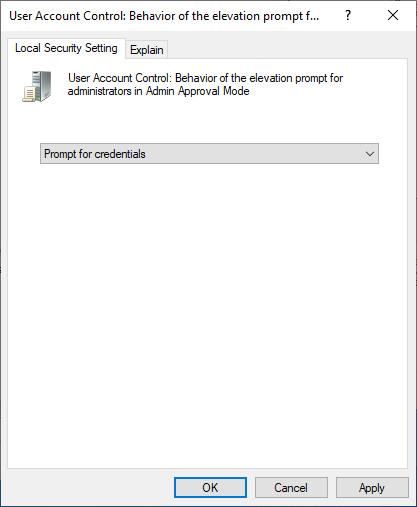
User Account Control: Behavior of the elevation prompt standard usersmust be set toPrompt for Credentials
Use the Credential Provider Filter in CREDUI(optional): this option is to enforce OpenOTP Credential Provider in CREDUI scenarios. That means when this setting is disabled, you are able to select the default Windows credential provider in CREDUI scenarios.
For example RunAsDifferentUser or RunAsAdministrator on a program or on an installer will trigger the CREDUI scenario.
If that setting is enabled, and you use Windows Remote Desktop tool to log in on a remote machine, then the OpenOTP Credential Provider will be triggered locally during the login process. If the OpenOTP-CP is also installed on the remote host as default provider, then it will also be triggered on the remote host during the login purpose. So in that scenario, the OpenOTP call will happens twice and 2 authentications will be performed with OpenOTP.
In RDP login scenario, the domain value is not automatically passed to Windows like for local logins scenario. Windows will then refuse the login if no domain value is passed in RDP scenario. This behavior is the expected behavior. If the domain value was automatically retrieved then we would encountered issues to login on a remote host which is not in the same domain.
In that scenario, you must use DOMAIN\username in username field to perform the login and target the correct domain according to where your are trying to login.
Click on Next.
If you enabled the Event Watcher, you will be prompted to configure it.
The Event Watcher component will be installed and run as a service. The configuration can be modified through the OpenOTP-CP registry. If you change the configuration through the registry after installation, the service must be restarted. After installation, you can verify that the service is running as expected by opening services.msc, locating OpenOTP Event Watcher, and checking that the service is running.
The OpenOTP Event Watcher has some limitations in its first version. These limitations are as follows:
-
If the Event Watcher session is closed at the WebADM level due to a network disruption lasting longer than 10 minutes, the Event Watcher service will be unable to "catch up" and re-attach the unsent event logs to the WebADM session log already created for that login. A new login using OpenOTP-CP is required to re-establish the session with the backend.
-
The Event Watcher only captures event logs related to a user session opened with the OpenOTP Credential Provider. If a session is not opened with OpenOTP-CP, the Event Watcher service will not send the logs to the WebADM framework. This limitation will not be present in the OpenOTP Authentication Package (AP).
The first box allows you to configure XPath rules to capture the desired information. If you don't configure it, all Logon/Logout Events will be captured and sent to WebADM.
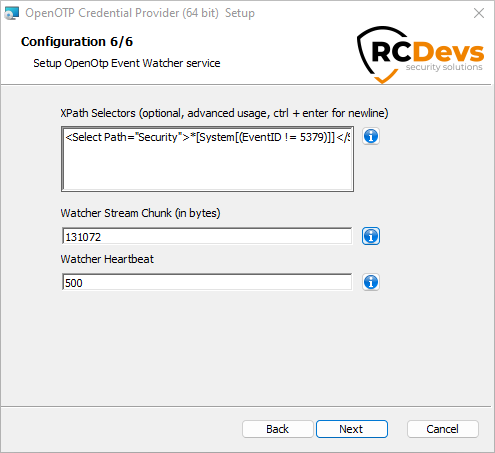
Here's an XPath query to capture file system access events (Event ID 4663):
<Select Path="Security">*[System[(EventID=4663)]]</Select>
If you want to exclude a specific event (e.g., exclude Event ID 5379) while still capturing 4663, you can use:
<Select Path="Security">*[System[(EventID=4663) and (EventID != 5379)]]</Select>
This will ensure only file access attempts (4663) are captured while ignoring 5379 or any other ID you specify.
Here’s an XPath query for User Account Control (UAC) elevation prompts:
<Select Path="Security">*[System[(EventID=4688) or (EventID=4673) or (EventID=4674)]]</Select>
Refer to the Microsoft documentation for more information about the event IDs you want to capture.
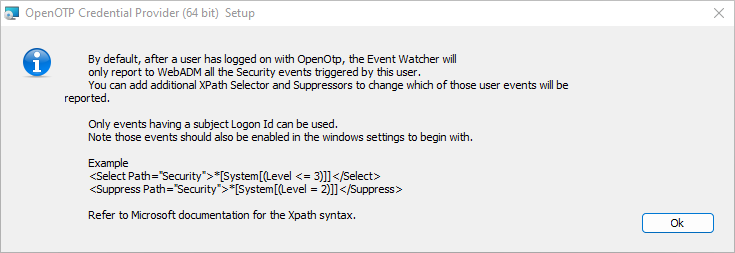
The Watcher Stream Chunk can be customized, but it is advised to keep the default value.
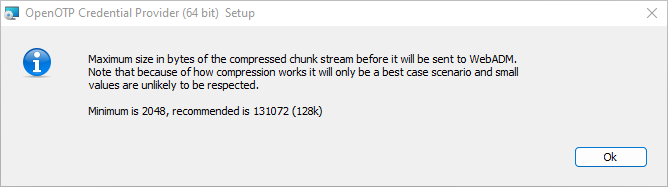
The Watcher Heartbeat can be customized, but it is advised to keep the default value.
To get the OpenOTP Event Watcher working, you need to have at least the Account Logon Events enabled in your GPO.
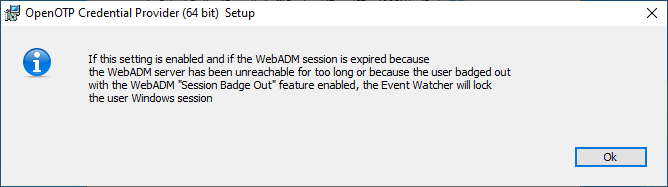
Lock the WebADM Session if the WebADM session is expired is a setting introduced in version 3.0.15. This feature works with the Event Watcher module and the OpenOTP Badging feature. When a user badges out from the OpenOTP Token application or when the Windows machine can no longer reach the OpenOTP service, the user session is automatically locked.
If you selected the Smartcard login feature, you will be presented a seventh page.
Enable additional MFA for smartcard login(Default to false). Specify whether you want an additional second factor authentication after a successful smartcard login
Click on Next
Configuration is done, you can click on Install and Finish after the installation.
Configuration for Smartcard logins
Refer to the following documentation to configure the OpenOTP SmartCard Provider for Windows
Modifying the Configuration
If you are under Testing
To configure the OpenOTP Credential Provider, navigate to the “Windows Control Panel” and select “Programs and Features”. Search for “RCDevs OpenOTP-CP Credential Provider for Windows” and click “Change”. Now the installer shows up. Select “Change” and modify the provider’s configuration as you need.
If OpenOTP Credential Provider is running in Production
To configure the OpenOTP Credential Provider, you must get the MSI installer file, for the example on your Desktop. Run command line as administrator:
- Click Start, click All Programs, and then click Accessories.
- Right-click Command prompt, and then click Run as administrator.
- If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Continue.
Run the installer, and click “Change” to update settings.
Automatic Deployment / Quiet Installation
The MSI installer package is prepared to take all configuration parameters that can be set during local installation for auto-deployment in quiet mode. Hence, you can deploy the setup to any clients and automatically install the Credential Provider without user interaction.
Example of quiet installation with PowerShell:
msiexec /qb /i OpenOTP_CredentialProvider.msi SERVER_URL=https://webadm1.rcdevsdocs.com:8443/openotp/ CA_FILE=c:\ca.crt OFFLINE_MODE=1 CLIENT_ID=windows
The parameters are as follows:
| Parameter | Value |
|---|---|
| SERVER_URL | URL pointing to one OpenOTP web‐service.Example: https://webadm1.rcdevsdocs.com:8443/openotp/ Mandatory. |
| SERVER_URL_2 | URL pointing to the second node of your OpenOTP cluster. Optional. |
| USER_IDENTIFIER_TYPE | This option defines what the Credential Provider sends as the username to OpenOTP. 1: UPN: Combination of username and domain (username@domain.com) is sent. This must correspond to the users userPrincipalName attribute. 2: Username (Default): Username is sent separately and should correspond to users samAccountName attribute. Note : Depreciated. Prefer using the 'UPN Mode' WebADM setting |
| LOADING_TEXT | The text to display during a connection attempt to Webadm. If you are using push login, it could be useful to remind the user here to check his mobile phone. |
| LOGIN_TEXT | A text that is displayed on the Windows login page. |
| CLIENT_ID | Client ID which is sent in the LogonUI scenario to match a client policy. |
| CA_FILE | The file-system path to a Certificate Authority (CA) file of WebADM. By default, it is copied in the installation folder of the Credential Provider. Mandatory. |
| CERT_FILE | The file-system path to a user certificate. Optional. |
| CERT_PASSWORD | The user certificate’s password. Optional. |
| API_KEY | Allow to provide an API Key value issued from WebADM when client authentication is required in your policies. Optional. |
| SOAP_TIMEOUT | Request timeout when connecting to OpenOTP Authentication Server URL. The default is 30 seconds (If empty it will be the 30s). Optional. |
| LOGIN_METHOD | There are two login methods available: |
| V1_BITMAP_PATH | The path of the image on the filesystem displayed on the login page. Valid for versions 2.x Optional. |
| V2_BITMAP_PATH | The path of the image on the filesystem displayed on the login page. Valid for versions 3.x Optional. |
| CHECK_LDAP | When enabled, the LDAP password is sent to OpenOTP for validation. If disabled, the LDAP password is not sent to OpenOTP and the -LDAP option is sent to OpenOTP to inform OpenOTP that the LDAP password is not going to be provided. In all scenarios, the LDAP or local user password is checked with Windows or Active Directory.
|
| AUTO_CREATE | You can enable this option when this host is not connected to the Windows Domain and you want the Credential Provider to create users accounts at first login. The local LDAP password is transparently reset at each login.
|
| LOCAL_ALIAS | You can enable this option when the host is not part of the Windows Domain and you want that the OpenOTP Credential Provider send a static value (WORKGROUP name) in order to match a WebADM domain. Sometime, the Windows API is returning the hostname which is sent as Domain value in the OpenOTP call. Configure that setting will prevent that behavior. |
| POLICY | Routing Policy. If two server URLs are defined in server URL, you can configure a request routing policy (ie. the server selection policy). There are three policies available:
|
| PROXY_HOST PROXY_PORT |
This config is for HTTP proxy. If you are running OpenOTP behind an HTTP proxy you need to set the host and the port of the proxy. |
| OFFLINE_MODE | According to this option OpenOTP will permit users to log in when server/network is not reachable, using the OpenOTP Token mobile Application.
|
| DEBUG_MODE | This setting enables or not the debug logs of the OpenOTP Credential Provider for Windows, and how verbose it should be
|
| WATCHER_DEBUG_MODE | This setting enables or not the debug logs of the OpenOTP Credential Provider for Windows, and how verbose it should be
|
| F2A_BYPASS_TIMER | This setting can be used to define for how much time in seconds the OpenOTP Windows Credential Provider will not ask for MFA since the last login, Max : 86400 (24h).
|
| RDP_CLIENT_ID | RDP client ID is used in RDP scenarios to match and apply a different client policy. |
| CredUI_CLIENT_ID | CredUI client ID is used in CredUI scenarios to match and apply a different client policy. |
| RDP_DEFAULT_ENABLED | This option is to enforce the Credentail Provider in CredUI scnearios. If this setting is not enabled, you are able to select the default Windows credential provider during an CredUI scenarios.
|
| WHITELIST (optional) : | List of user SID separated by ; that won’t be asked for 2FA/MFA to login, skipping any OpenOTP calls. |
| PROTECTED_PRINCIPALS : | List of security principals SID (users and groups) separated by ; which for the OpenOTP call will be enforced. This is basically the opposite of the above whitelist setting, and is only useful if you have whitelisted groups |
| CP_FILTER_WHITELIST (optional) : | Only relevant if you have selected the InstallAsDefault feature. List of the credential providers CLSID separated by ';' that should still be enabled, overriding the filter. All the CLSID of the registered Credential Providers on your machine can be found in the following registry location: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers |
| SMARTCARD_MFA : | Only present if you have installed the SmartcardLogin feature. If enabled, an additional authentication factor will be required after a successful smartcard login. |
In order to set the OpenOTP Windows Credential Provider as the default credential provider in case of silent or remote deployment, the option ADDLOCAL=InstallAsDefault must be added to the msiexec command line:
msiexec /qb /i OpenOTP_CredentialProvider.msi SERVER_URL=https://webadm1.rcdevsdocs.com:8443/openotp/ ADDLOCAL=InstallAsDefault CA_FILE=c:\ca.crt OFFLINE_MODE=1 CLIENT_ID=windows
You can also specify the SmartcardLogin feature, e.g. ADDLOCAL=SmartcardLogin or ADDLOCAL=InstallAsDefault,SmartcardLogin.
Windows FailSafe Mode
In order to force the use of the OpenOTP Credential Provider even in Windows failsafe mode, some registry changes need to be made.
In case of failure during the provider configuration or unreachable network, even failsafe mode will not help you to log in to a workstation that is set-up to force the use of the Credential Provider.
To register the Credential Provider enforcement, copy the following text to a new text file, name it register.reg and execute it.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers]
"ProhibitFallbacks"=dword:1
To disable and unregister the failsafe enforcement copy the following text.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers]
"ProhibitFallbacks"=-
Online Authentication Test
With OTPs/Push
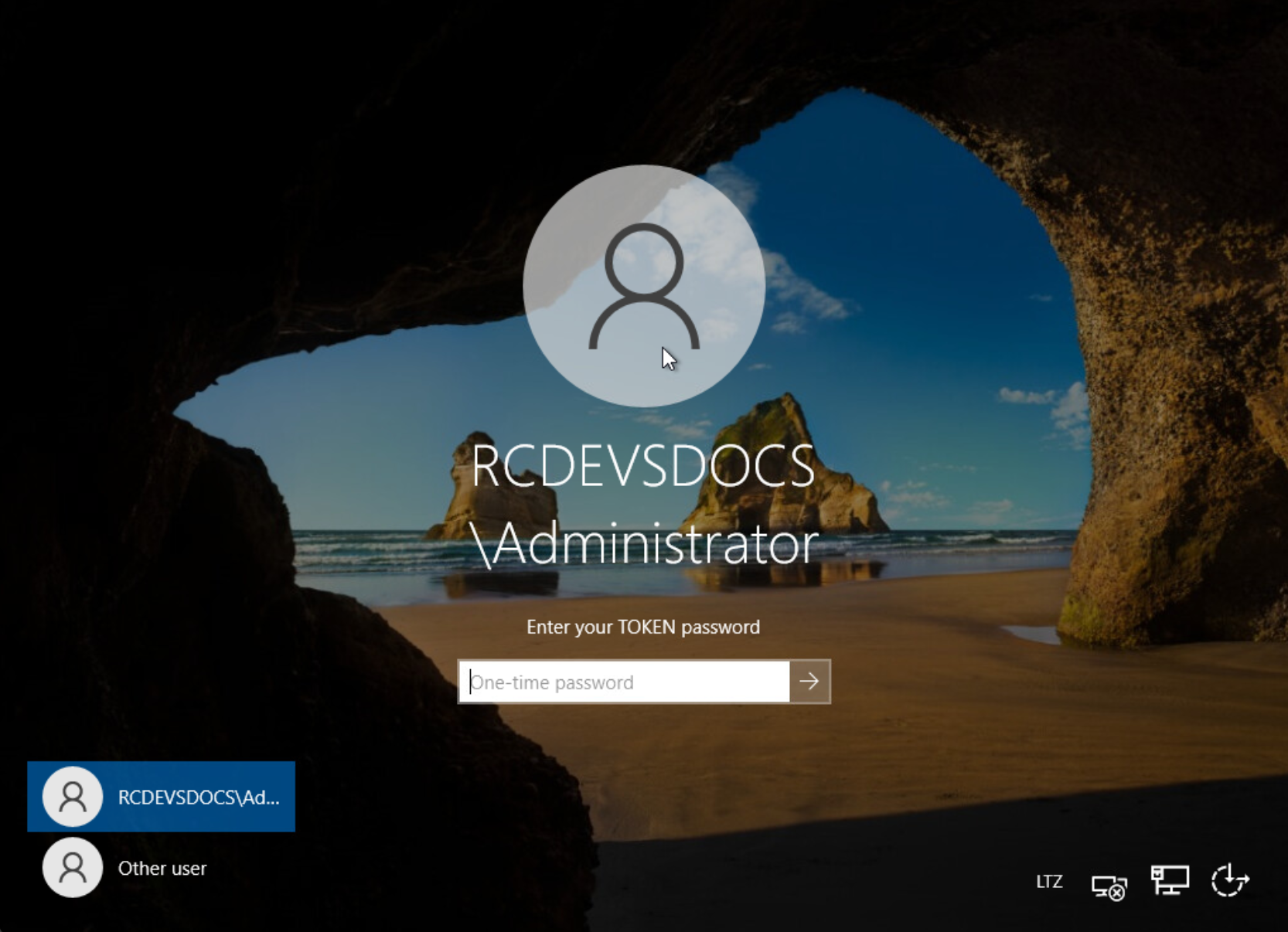
You are now able to log in your Windows machine using MFA with OpenOTP. Please log out and enter your LDAP Credentials on the first screen.

You should have a WebADM account activated and an OTP Token enrolled on your account. Follow this documentation to User Activation & Token enrollment documentation
On the next screen, your OTP is asked to finish the authentication.
Enter your OTP and you are logged in.
With Smartcards
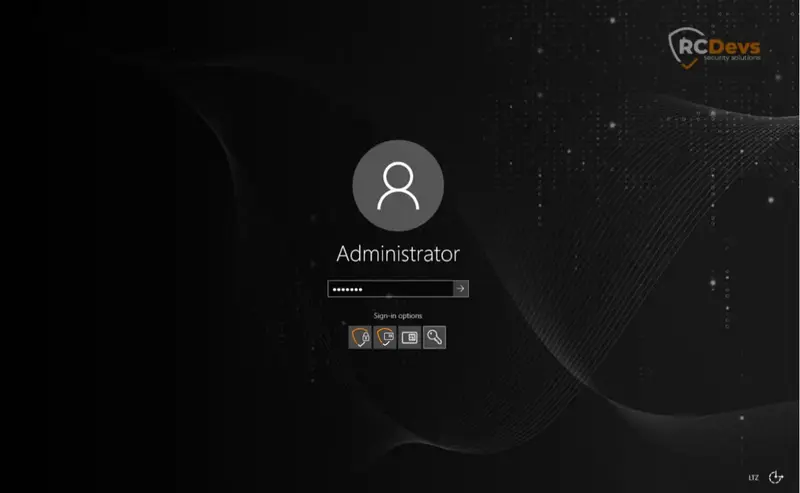
Insert your smartcard. If it is detected and the stored certificate can be used for logon, you will now have a new credential tile for smartcard logon.
Select it and enter your PIN code.
If you have enabled the additional MFA authentication during installation, you will then be prompted for the configured additional factor (OTP/Push/FIDO2 etc). Enter what is required.
You are now logged in.
With FIDO2 Keys
The client policy must be configured for FIDO2 authentication in order to use your FIDO2 key. Enter your LDAP credentials and you will be invited to touch your FIDO2 device:
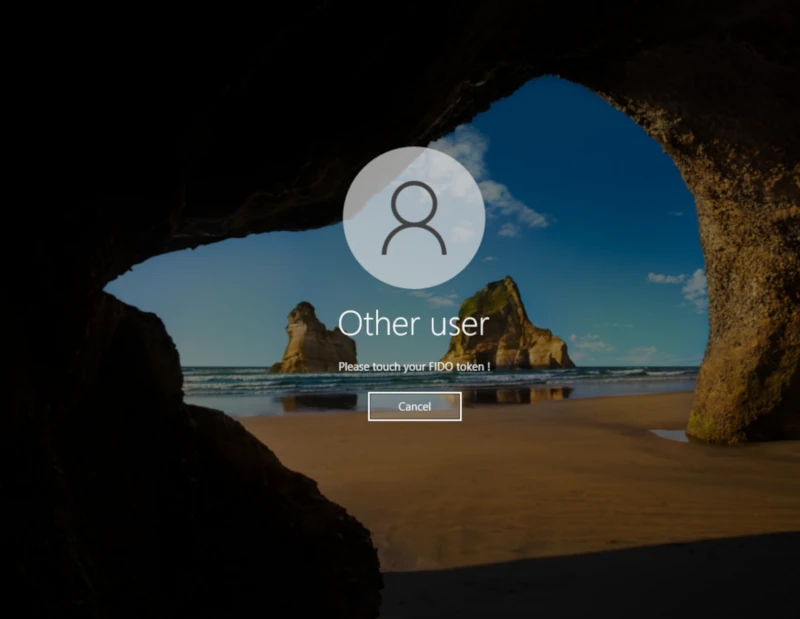
Once you successfully respond to the FIDO challenge, you will be authenticated, and your session will be opened.
Starting with OpenOTP Credential Provider version 3.0.12, FIDO2 security keys are supported for Remote Desktop Protocol (RDP) authentication through Windows Hello. To use this feature, you need a compatible Windows version. For more details on supported versions, please refer to the Microsoft documentation. This functionality is available exclusively with Microsoft’s Remote Desktop client.
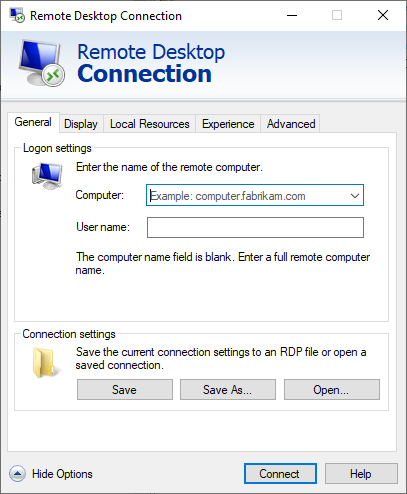
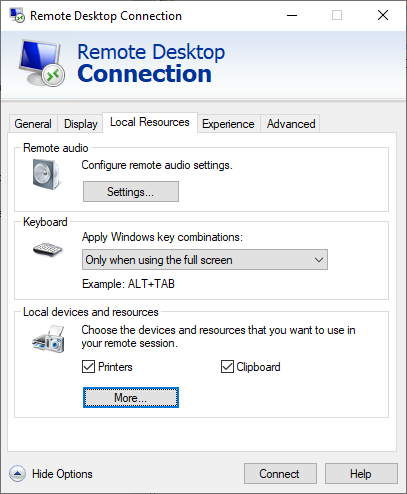
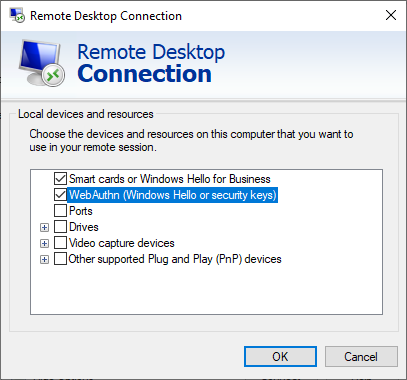
To enable this feature, activate the WebAuthn (Windows Hello or security keys) setting in your Microsoft Remote Desktop client. Open the Microsoft Remote Desktop client, navigate to the Local Resources tab, and under Local devices and resources, click the More button. Then, check the option for WebAuthn (Windows Hello or security keys). Don't forget to whitelist Microsoft's FIDO Credential Provider during the installation of the OpenOTP Credential Provider.
FIDO User Presence (touching the key) is always enforced by OpenOTP, while User Verification (such as fingerprint or PIN to unlock the key) can be managed through OpenOTP Server settings.
Offline Authentication Test
Important information for offline logins
One online login with OpenOTP is required to enable offline login mode! This is specific to the user and computer where the login is made, which means, if computers are shared in the company, all users needs to perform an online login on a specific machine to enable the offline logins for their accounts on this computer.
Procedure must be repeated on all machines they want to enable the offline login mode.
Compatible token must be registered first on the user account in order to be able to use that feature (OpenOTP Token application or FIDO2 key).
Push registered token is mandatory to use the offline mode with OpenOTP Token application.
If both kind of tokens (OTP with OpenOTP Token app and FIDO2 keys) are registered on the user account before the online login, OpenOTP will send back offline information to the OpenOTP Credential Provider for the 2 types of devices and after one online login you will be able to login offline with all compatible devices registered on the user account.
With OpenOTP token application and Tokens registered in Push mode, only the first push token (generally registered on slot 1 on the user account) is usable in offline mode!
With FIDO2 keys, all registered FIDO2 keys will work in offline mode but only one key must be plugged to the Windows machine during the authentication process.
In Offline mode, the user password is verified during the process by Windows, so in case of a Domain joined machine, please ensure that the GPO setting Interactive logon: Number of previous logons to cache (in case domain controller is not available) is configured to allow caching of credentials.
If you activated the options KeyUpdate or Token Expiration Time in the OpenOTP server configuration, the offline mode won't work anymore once the token key has been rotated on the server and the mobile application until the next online login.
To resolve this issue you need to perform an online login in order to renew the Offline state on the concerned machines and for all concerned users.
With OTPs/QRCode
Offline authentication is available for Windows and macOS login, and requires at least the following versions: WebADM 1.6, OpenOTP 1.3.6, OpenOTP Token 1.4 and OpenOTP Credential Provider 1.2.
When your laptop is offline, you are now able to log in with an OTP or a FIDO2 key. So for this test, I disable the network adapter to simulate the offline mode.
Like above, enter your LDAP Credentials on the first screen.

OpenOTP Credential Provider is not able to contact OpenOTP server so, it will switch automatically to the offline mode. The offline mode will prompt you a QRCode if using an OTP or to touch your FIDO key.
You have to scan the QRCode with the OpenOTP Token application.
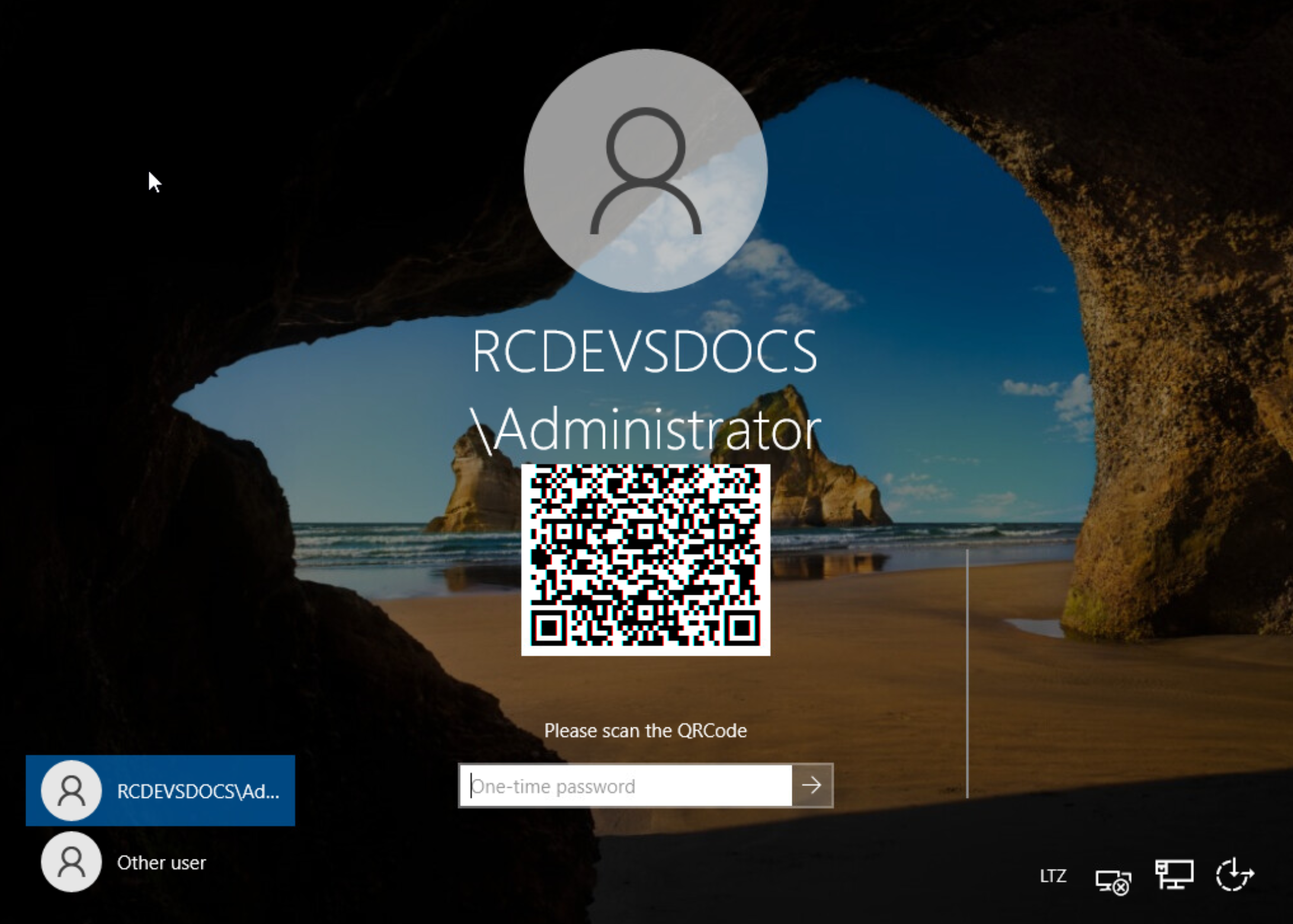
Open your OpenOTP Token application, press on the camera button and scan the QRCode.
After scanning the QRCode, a window with an OTP is displayed on your smartphone like below:
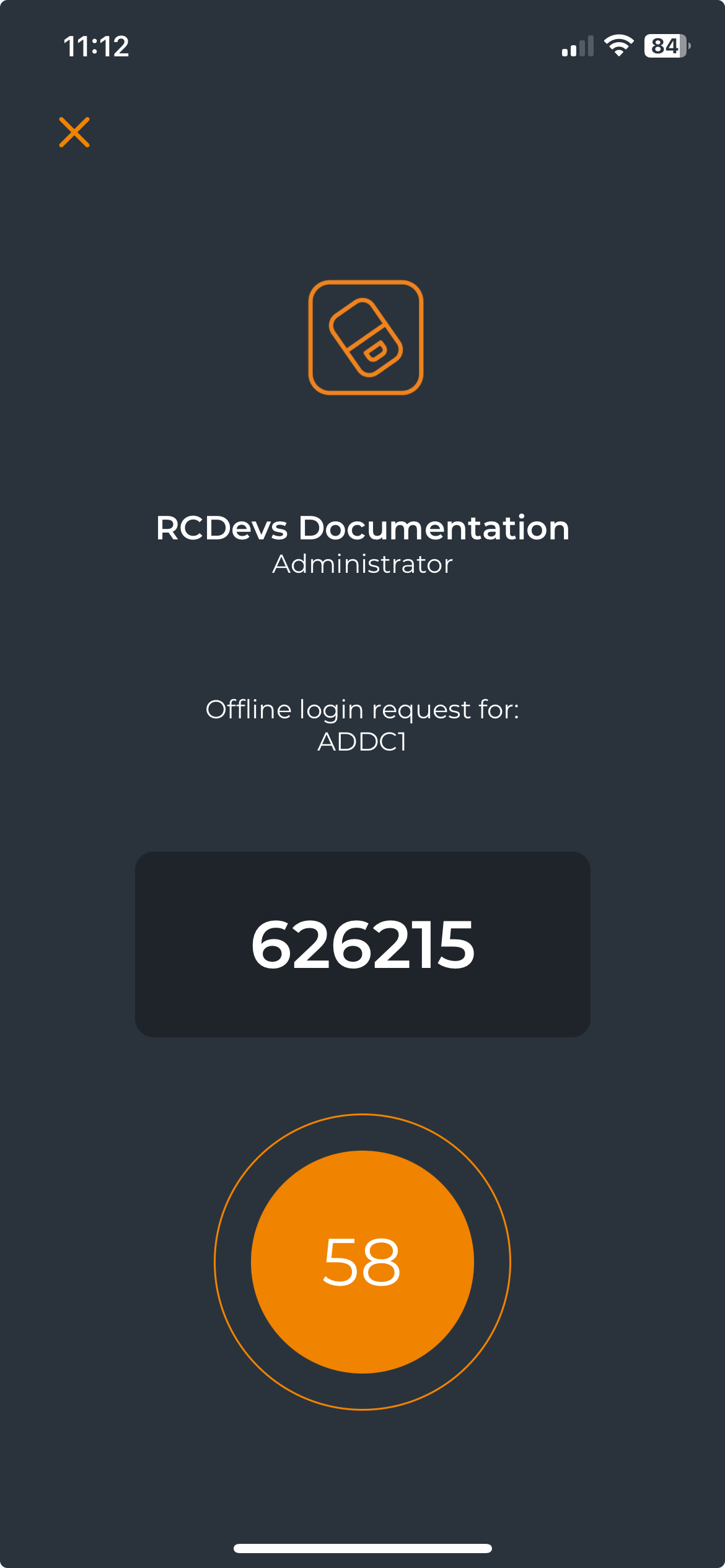
Enter your OTP and you are logged in.
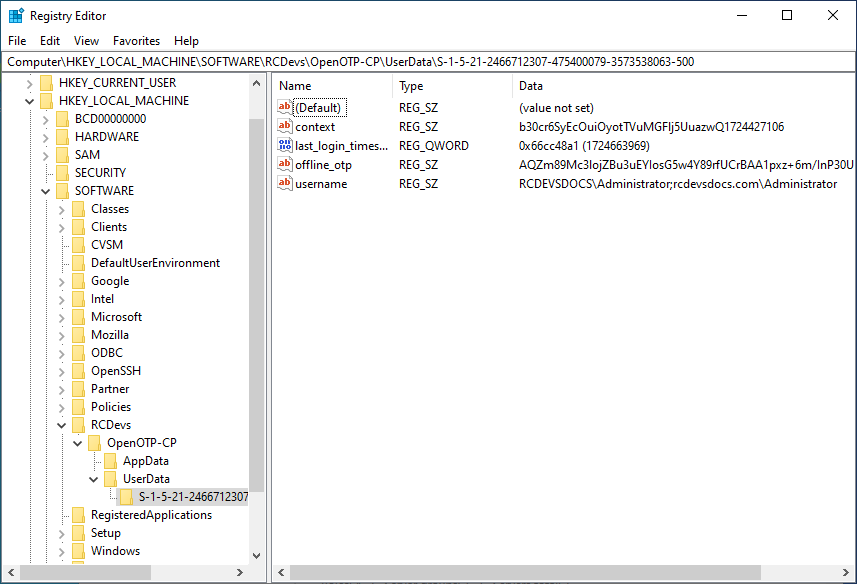
To be sure the offline mode is enabled on a specific machine for a specific user, you can check in your Registry Editor if offline metadata are present.
In your AD, it should be possible to find this offline_otp string in the file of the user concerned by going in the Registry Editor and following this path:
HKEY_LOCAL_MACHINE/SOFTWARE/RCDevs/OpenOTP-CP/UserData
With Smartcards
Offline Smartcard login is supported in offline mode from OpenOTP-CP version 3.0.15.
With FIDO2 Keys
With FIDO2 authentication method, the offline authentication is working similarly to online mode.
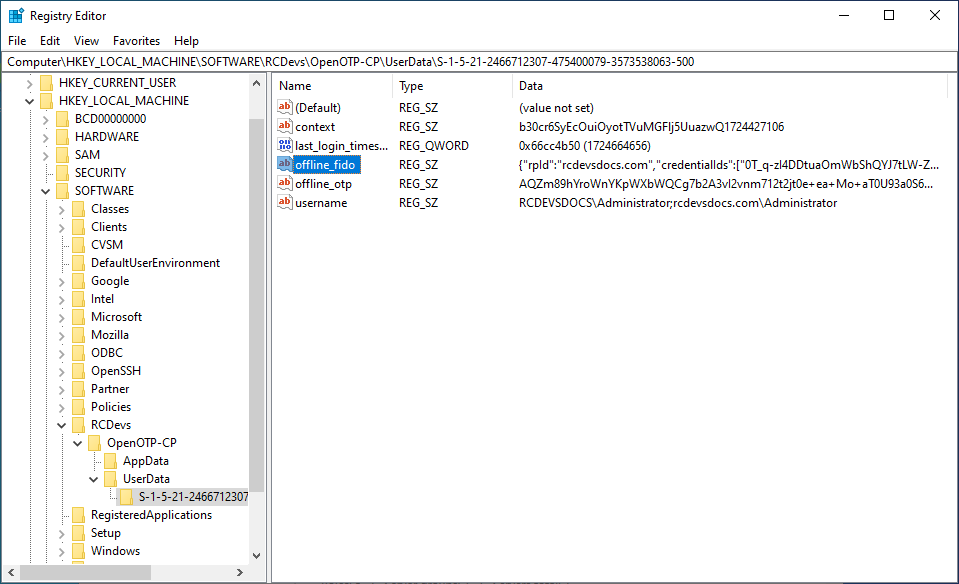
To be sure that you are in offline mode, you can check in your Registry Editor if there is an offline_fido string.
In your AD, it should be possible to find this offline_fido string in the file of the user concerned by going in the Registry Editor and following this path:
HKEY_LOCAL_MACHINE/SOFTWARE/RCDevs/OpenOTP-CP/UserData
Troubleshooting
Troubleshooting steps depend on the specific issue you are facing. Please consult the following chapters for instructions.
Authentication Issues
In case of failed authentication, the first check should be the webadm.log on the OpenOTP/WebADM server. This can be found on the server at /opt/webadm/logs/webadm.log or in the WebADM web-interface under Databases > WebADM Server Log Files.
This log should have a trace of the OpenOTP authentication and its result. In case the OpenOTP authentication is successful, but the Windows login fails, the reason is typically a missing local account or wrong local Windows password.
If the login fails and there is no trace of it in the webadm.log, then the installation is not correct. Please see chapter 8.3
Offline Authentication Issues
Offline authenticate requires a successful online login using mobile push-based authentication and RCDevs OpenOTP mobile soft token. This login must be done on the same Windows machine and with the same user account. If this prerequisite is not complete then you will receive error message: "Offline login is not available for this user."
To configure push-based authentication, please refer to RCDevs Push mecanisisms documentation.
Installation Issues
Windows settings and permissions can cause the installation to fail for various reasons. While debugging your installation and OpenOTP environment, take a look at the Windows Event Viewer.
If the installation is completed but CP is not working, please check the following items:
- You should have an entry in the registry at
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\RCDevs\OpenOTP-CP\If not please check that the user you are running the installer as has got write permissions to the registry folder:Computer\HKEY_LOCAL_MACHINE\SOFTWARE\ - You should also have these two files, if not then check the effective access of the installation user to the
System32folder:
C:\Windows\System32\OpenOTPCredentialProvider.dll
C:\Windows\System32\OpenOTPCredentialProviderFilter.dll
You can use this command via PowerShell, which will generate a log file if you encounter errors during the MSI installation :
PS C:\Windows\system32> msiexec /i "C:\Users\user1\Desktop\OpenOTPCredentialProviderSetup-3.0.10.0-x64.msi" /L*V "C:\RCDevsLogs\CP-Logs"
Unable to login at all
In case you have installed the OpenOTP Credential Provider as the default credential provider and are unable to login at all, you stil have the following options to gain access to the machine again:
Remote registry modification
If you can manage the registry of the machine in question remotely, for example in case of a domain joined machine, you can remove the default credential provider registration. Remotely access the registry of the server in question and delete the below registry key:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider Filters\{5AE8C610-7541-4FF8-9845-C363410D574C}]
@="OpenOTPCredentialProviderFilter"
Boot to Windows "Safe mode"
As long as you have not enabled CP also for safe mode and can boot to it, you can use it to remove or modify credential provider Please refer to Microsoft documentation on how to boot to Safe Mode. Once in safe mode, rename or remove the two below files and reboot to log in with the regular Windows login.
C:\Windows\System32\OpenOTPCredentialProvider.dll
C:\Windows\System32\OpenOTPCredentialProviderFilter.dll
Mount disk drive on other system
In case Safe Mode boot is not available (for example on cloud deployed Windows), you need to shut down the machine, mount the C: drive and rename/remove the two DLL files in previous step. After that you should be able to boot into regular login.
Push Login issue
If you have increased the Mobile response timeout setting under OpenOTP configuration, then you also have to increase the Windows 10 lock screen timeout and the RDP login timeout on the Windows machine.
The SOAP timeout value at the OpenOTP Credential Provider level must be also configured in adequation of the mobile response timeout.
e.g : If my mobile response timeout under OpenOTP is configured to 45 seconds, then I have to configure the SOAP timeout and Windows timeouts to 60 seconds.
For the Windows lock screen timeout, you have to create a new registry key in the following container :
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\
Simply add a new DWORD value named IdleTimeout in that container and configure the timeout value in milliseconds. If your push timeout is configured to 45 seconds, then the value of the new IdleTimeout key must be at least 60 seconds.
60 seconds is equal to 60000 ms in decimal and EA60 in hexadecimal.
For the Windows RDP timeout, you have to create a new registry key in the following container only if NLA is enabled on the Windows side for RDP login :
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp\
Simply create a new DWORD key named LogonTimeout, containing the timeout value in seconds. Restart the Terminal Services service to changes takes effect.
Could not be authenticated
Server Sent No Response
Error example

Possible reasons/Solutions :
- OpenOTP URL/port configured during Credential Provider installation are invalid or not reachable from the Windows machine.
- CA file is missing, incorrect or not usable.
Check server URL and CA path through Windows registry Computer\HKEY_LOCAL_MACHINE\SOFTWARE\RCDevs\OpenOTP-CP.
Wrong Username or Password?
error example

- Double check that the username and password are correct.
- Check WebADM logs, if you can see the authentication request in logs with the following error :
[2020-04-21 10:48:09] [192.168.3.68] [OpenOTP:386DCN2T] Domain 'rcdevsdocs.com' not existing
Please refer to part Troubleshooting documentation to solve it.
Endpoint could not be initialized
To troubleshoot that kind of error, you need to enable the debug logs of the OpenOTP Credential Provider for Windows.
Enable Debug Logs
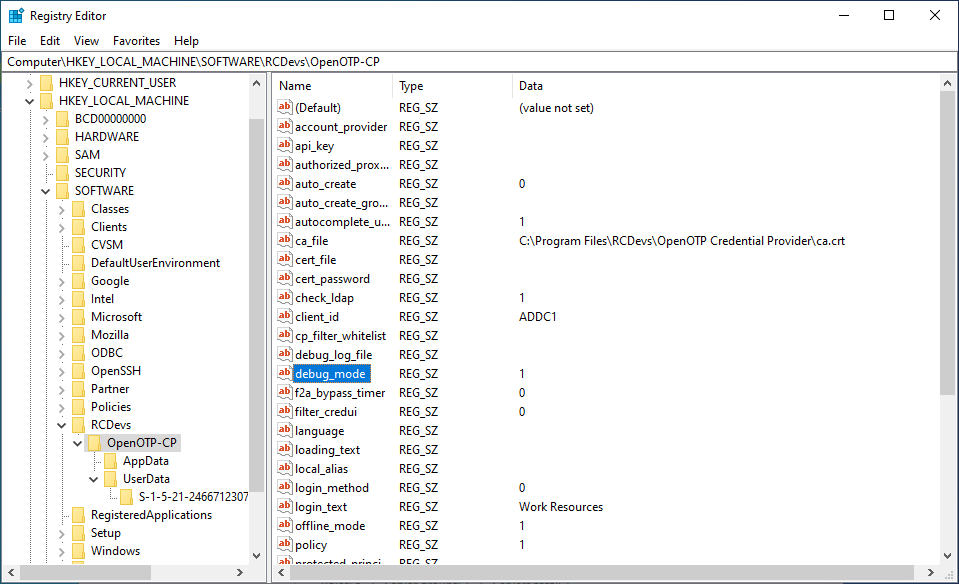
For advanced troobleshooting, debug mode can be enabled through Windows registry Computer\HKEY_LOCAL_MACHINE\SOFTWARE\RCDevs\OpenOTP-CP\debug_mode=4.
This option can be set from 0 (disabled) to 4, depending on how verbose you want it to be.
Debug logs are accessible by default in C:\RCDevsLogs\CP-Logs. If you have redefined the location using the debug_log_file registry key, the logs will be written to the specified location.
Perform a new authentication after debug_mode enabled and check debug logs.
Debug Logs
Open C:\RCDevsLogs\CP-Logs file and check logs :
[21-04-2020 11:02:51] [5724-6044] [INFO] CProvider::CProvider
[21-04-2020 11:02:51] [5724-6044] [INFO] Configuration::Init
[21-04-2020 11:02:51] [5724-6044] [INFO] Configuration::Default
[21-04-2020 11:02:51] [5724-6044] [INFO] Configuration::Read
[21-04-2020 11:02:51] [5724-6044] [INFO] Data::Provider::Init
[21-04-2020 11:02:51] [5724-6044] [INFO] CProvider::SetUsageScenario
[21-04-2020 11:02:51] [5724-6044] [INFO] CProvider::Advise
[21-04-2020 11:02:51] [5724-6044] [INFO] CProvider::GetCredentialCount
[21-04-2020 11:02:51] [5724-6044] [INFO] No serialized creds set
[21-04-2020 11:02:51] [5724-6044] [INFO] CProvider::GetCredentialAt
[21-04-2020 11:02:51] [5724-6044] [INFO] Checking for serialized credentials
[21-04-2020 11:02:51] [5724-6044] [INFO] No serialized creds set
[21-04-2020 11:02:51] [5724-6044] [INFO] No serialized creds set
[21-04-2020 11:02:51] [5724-6044] [INFO] No serialized creds set
[21-04-2020 11:02:51] [5724-6044] [INFO] Checking for missing credentials
[21-04-2020 11:02:51] [5724-6044] [INFO] Looking-up missing user name from session
[21-04-2020 11:02:51] [5724-6044] [INFO] Looking-up missing domain name from session
[21-04-2020 11:02:51] [5724-6044] [INFO] Data::General::Init
[21-04-2020 11:02:51] [5724-6044] [INFO] GetFieldStatePairFor
[21-04-2020 11:02:51] [5724-6044] [INFO] CCredential::Initialize
[21-04-2020 11:02:51] [5724-6044] [INFO] Copying user_name to credential
[21-04-2020 11:02:51] [5724-6044] [INFO] Copying domain to credential
[21-04-2020 11:02:51] [5724-6044] [INFO] rcdevsdocs
[21-04-2020 11:02:51] [5724-6044] [INFO] Init result:
[21-04-2020 11:02:51] [5724-6044] [INFO] OK
[21-04-2020 11:02:51] [5724-6044] [INFO] Checking for successful initialization
[21-04-2020 11:02:51] [5724-6044] [INFO] Checking for successful instantiation
[21-04-2020 11:02:51] [5724-6044] [INFO] Returning interface to credential
[21-04-2020 11:02:51] [5724-6044] [INFO] Non-CredUI: returning an IID_IConnectableCredentialProviderCredential
[21-04-2020 11:02:51] [5724-6044] [INFO] Hook::CredentialHooks::GetBitmapValue
[21-04-2020 11:02:51] [5724-6044] [INFO] Hook::CredentialHooks::GetSubmitButtonValue
[21-04-2020 11:02:51] [5724-6044] [INFO] GetFieldStatePairFor
[21-04-2020 11:02:51] [5724-6044] [INFO] CCredential::Advise
[21-04-2020 11:02:51] [5724-6044] [INFO] CCredential::SetSelected
[21-04-2020 11:02:51] [5724-6044] [INFO] Hook::Serialization::EndpointInitialization
[21-04-2020 11:02:51] [5724-6044] [INFO] Endpoint::Init
[21-04-2020 11:02:51] [5724-6044] [INFO] Endpoint::Default
[21-04-2020 11:02:51] [5724-6044] [INFO] Hook::Serialization::EndpointDeinitialization
[21-04-2020 11:02:51] [5724-6044] [INFO] Endpoint::Deinit
[21-04-2020 11:02:51] [5724-6044] [INFO] Endpoint::Default
[21-04-2020 11:02:54] [5724-6044] [INFO] CCredential::Connect
[21-04-2020 11:02:54] [5724-6044] [INFO] Hook::Serialization::Initialization
[21-04-2020 11:02:54] [5724-6044] [INFO] Hook::Serialization::EndpointInitialization
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::Init
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::Default
[21-04-2020 11:02:54] [5724-6044] [INFO] DataInitialization
[21-04-2020 11:02:54] [5724-6044] [INFO] Data::Gui::Init
[21-04-2020 11:02:54] [5724-6044] [INFO] Data::Gui::Default
[21-04-2020 11:02:54] [5724-6044] [INFO] Hook::Serialization::ManageUpnMode
[21-04-2020 11:02:54] [5724-6044] [INFO] Helper::SeparateUserAndDomainName
[21-04-2020 11:02:54] [5724-6044] [INFO] Loading domain from external credentials
[21-04-2020 11:02:54] [5724-6044] [INFO] Loading password from GUI
[21-04-2020 11:02:54] [5724-6044] [INFO] Loading OTP from GUI
[21-04-2020 11:02:54] [5724-6044] [INFO] Loading challenge from GUI
[21-04-2020 11:02:54] [5724-6044] [INFO] Hook::Serialization::EndpointLoadData
[21-04-2020 11:02:54] [5724-6044] [INFO] Copy username to epPack
[21-04-2020 11:02:54] [5724-6044] [INFO] Copy ldapPass to epPack
[21-04-2020 11:02:54] [5724-6044] [INFO] Copy domain to epPack
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::Call
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::ShowInfoMessage
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::ShowInfoMessage
[21-04-2020 11:02:54] [5724-6044] [INFO] Endpoint::Concrete::OpenOTPInit
[21-04-2020 11:02:55] [5724-6044] [INFO] Unable to read certification authority "C:\Program Files\RCDevs\OpenOTP Credential Provider\caa.crt"
The last line of logs interest us :
[21-04-2020 11:02:55] [5724-6044] [INFO] Unable to read certification authority "C:\Program Files\RCDevs\OpenOTP Credential Provider\caa.crt"
Possible reasons/Solutions :
OpenOTP Credential Provider for Windows is not able to read the CA file.
-
Double check if CA file configured is the correct one and coming from your WebADM server. WebADM CA file can be downloaded from a web browser by accessing the following addresses :
- https://webadm_server/cacert
- https://webadm_server:8443/cacert
If you have multiple WebADM servers configured in cluster mode, the CA must be identical on all nodes. If for any reasons you have different CA certificates within the same WebADM cluster, then your WebADM setup is incorrect and you have to re-do WebADM slave setup on node(s) where the CA is incorrect.
- Check the CA path. Here the CA name configured in the registry is wrong, and it prevents the CP to access it.
Normally, the CA file is automatically downloaded during the Credential Provider setup. If not, you can manually download and configure it.
The CA file must be accessible by OpenOTP Credential Provider that is why it is advised to move the CA file in the installation folder of OpenOTP Credential Provider after CP installation.
The default OpenOTP Credential Provider installation folder is:
C:\Program Files\RCDevs\OpenOTP Credential provider\
This is required ONLY if CA file is not automatically downloaded. Registry key for CA file location must also be adapted through the registry after CA file has been moved to installation folder :
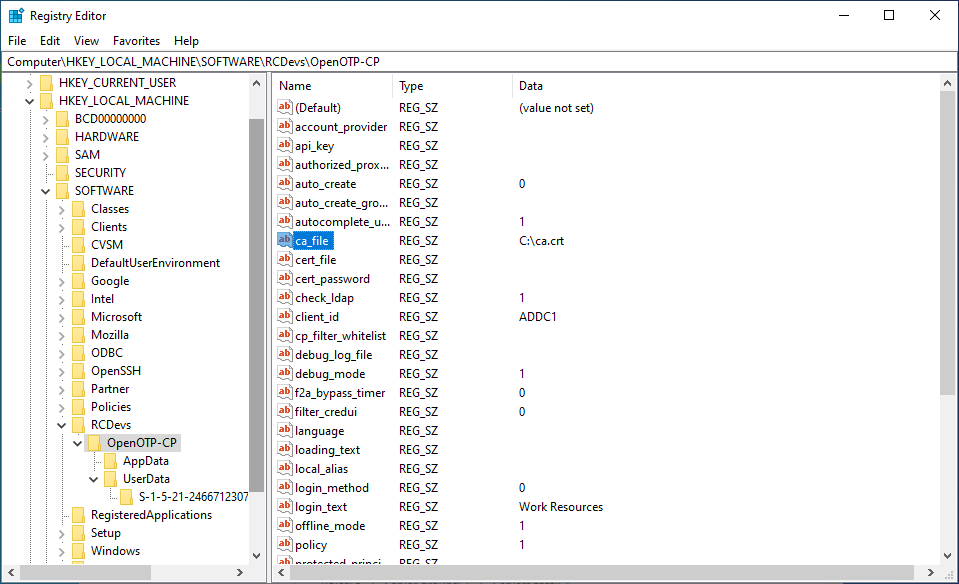
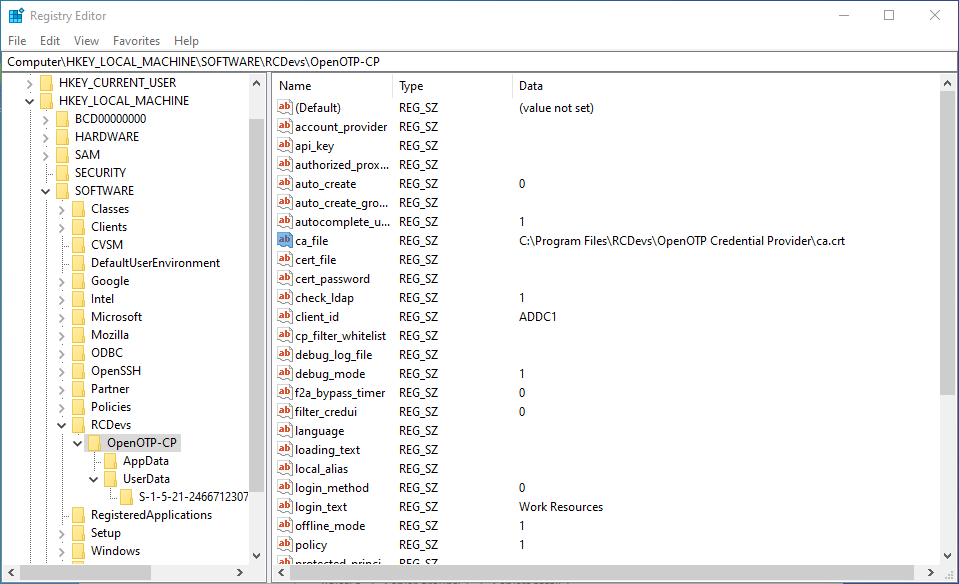
In offline mode, the CA file cannot be stored or accessed via a shared folder or network path like \\STORAGE\ca.crt. For offline authentication to work, the CA file must be locally accessible on the machine.
Disable RDP auto-reconnect bypassing OpenOTP authentication
Starting with Windows 10 version 1803 and Windows Server 2019, Microsoft introduced local client caching for credentials when reconnecting to a locked RDP session. This behavior prevents the Credential Provider from re-authenticating the user as it did in earlier versions of Windows.
To address this, you need to disable the automatic reconnection setting in the machine's registry. This can be accomplished using the Group Policy feature in Windows:
- For machines not part of a domain, use the Local Group Policy Editor.
- For domain-joined machines, use the Group Policy Management Console.
Open the following path in the policy edition:
Computer Configuration>Administrative Templates>Windows Components>Remote Desktop Services>Remote Desktop Session Host>Connections, and double-click on Automatic reconnection, then switch to Disabled, press OK, and close all group policy windows.
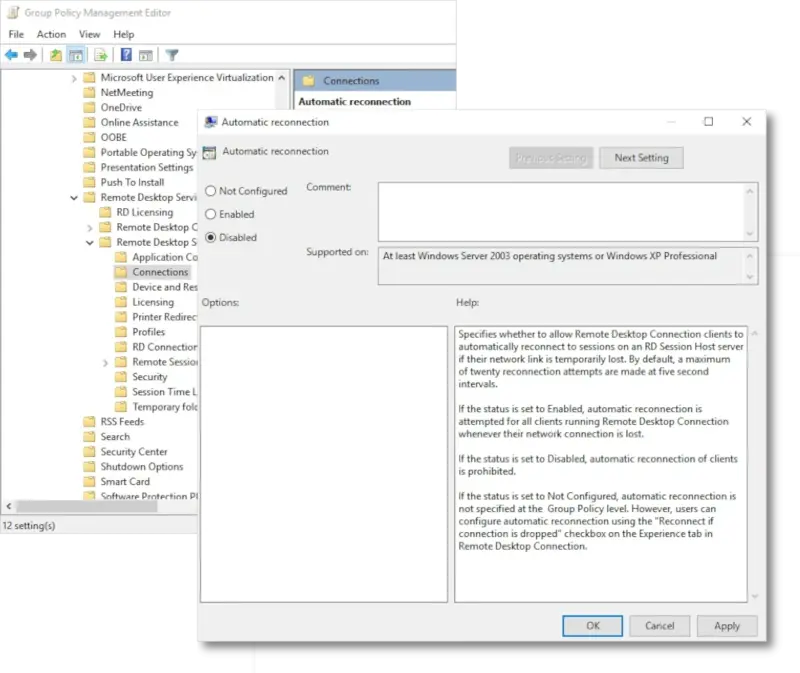
You may need to restart the machine or update Group Policy Objects (GPO) on remote machines for the settings to take effect.
