Overview
In this guide, we will show you how to convert token seed files (PSKC files) into a WebADM inventory file. This process enables you to utilize third-party hardware tokens with RCDevs security solutions. Additionally, we will explain how to reuse software tokens already registered on end-users' devices with RCDevs solutions.
Seeds Files Format supported by WebADM
Un-encrypted Inventory
Here is the format of an unencrypted RCDevs inventory file that can be imported into WebADM without needing any conversion:
# CSV import file for RCDevs WebADM
# Generated on April 9, 2019, 4:13 pm
Type, Reference, Description, Data
"OTP Token", "5292530833003", "RCDevs RC200-T6", "TokenKey=tdxn5faLI0joNLIjLrIMjUxaZXc=,TokenType=VE9UUA==,TokenState=MA==,OTPLength=Ng==,TOTPTimeStep=MzA="
As depicted, it is a CSV file containing four entries for each token:
- Type: Indicates the object type (TOTP, HOTP, OCRA, or YUBIKEY)
- Reference: Token serial number
- Description: Concise description of the object
- Data: Configuration data specific to the token
To view this information, navigate to WebADM Administrator portal > Databases > Inventoried Devices.
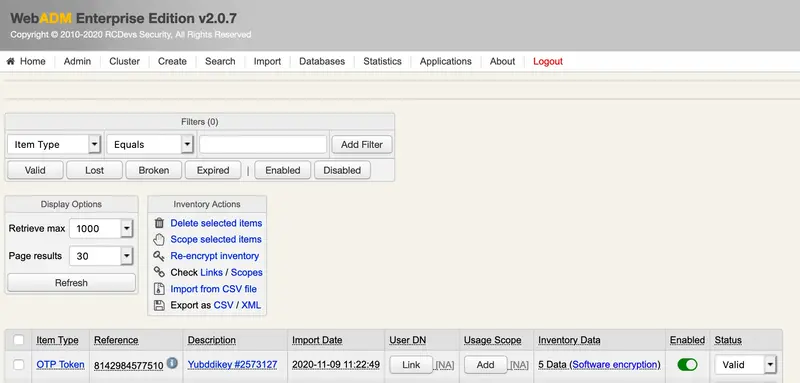
As evident from the inventory example above, the Data field includes multiple items that require adjustment based on your token properties.
All entries below must be base64 encoded for import into WebADM.
The contents of the Data field in RCDevs inventory files include the following:
- TokenKey: Token secret key value.
- TokenType: TOTP (time-based), HOTP (event-based), OCRA, or YUBIKEY based on your token type.
- TokenState: This represents the time offset value for TOTP and the counter value for HOTP tokens. It defaults to 0. If the actual value is unavailable, token resynchronization may be required.
- OTPLength: Can be 6, 8, or 10. This setting depends on the OTP length generated by your tokens.
- TOTPTimeStep: Can be 30 or 60 seconds. Particularly relevant for TOTP tokens, it must match the TOTP Time Step setting of your OpenOTP server.
Encrypted Inventory
If you have purchased RCDevs hardware tokens and are using the Enterprise Edition of OpenOTP, you will receive an encrypted inventory file. This encrypted inventory file can only be imported and decrypted by WebADM when it is running with the correct associated license file. Without the proper enterprise license, you will not be able to import the encrypted file into WebADM.
An RCDevs encrypted seeds file appears as follows:
Inventory Import File for RCDevs WebADM
Generated on June 20, 2019, 12:55 pm
Encrypted for use with <CUSTOMER> customer license
MD5: 68bc02730eefba1216570d8f38a4e7bd
-----BEGIN RCDEVS INVENTORY DATA-----
MCW7jYTpRgP9g0Z5N+Y2+7DobUzK2buPg9yVeIhAH+LwDwLQwlZVUamK+164mGx
yckzsWlNYX97kN2CyjlwZxw/qm+Y172v9GwGbQKNRmPaLMQVt3K7X/zlYYtDW1lo
oKSDN2iNovPPTH5RjDLuCbC3qXvWkTktQN7GqrMJnOyZyAXzT6klJoleNUBVMrV6
MCRdPp44Zbefnwhq50gH0dF9g2XgIZGogmAbBuJkRlbl5QzGvj5Y3OoHR74TzprF
nJOlutexlFfKchOG0gtLjmX/GBpme4E8k/z+uaZq8BjfSxDxAoXB2mRqfkzYeZXy
Rg/hSuKmvQrg051hx4cQfPlRootYsXMudXJ4vvKQTC1h5gCJ6g8yeCR3okFhpYnk
1q7EAiaM24qo2MXq6Hg6iDwxdXuSYKOuuX9nHGngu1aFfK449Z7TrnrqDAenvyCI
kLFGZ9zgHqsmHEz4syV66PF1rjt3qiaU41AobSKOKPz2MRMlBZ8RSr6zAUcBIimj
Uexg1HUktNDvkGG5mJnNztBukrg6f79gsZNUDipb0VIjpYCXT4JkIeg/pKe44qEI
lMgRqqi+cCDoSWidWXfacdr7Vn/RTLO1katNTwP5nzluMdkCzPTfA5kJv0lQyB9y
mIRf2XoKcB8gM210hgQKQ9FIdDNMHBp9733iK4R3Ya2+Q/T82P5mtdHuYhPWRkFH
mkCy8YJ448Fi+71qwN1HrdDiK+/Xg2261DOX/dQ1AwNSuNLB5RdSDwHa0AOiq3ps
SFcK+vhK0n/OyLZpP5zOHEYS94EIkAVNQF+YFwGcRZE0ki4lySPDtgknnETZireb
hXy6OsqfHb3R3IZJxFRLU7TUqbkdxlJnx+QckJiYsDwK6JKwUn0BgBkNIJ91Wwlz
BYZimc+W0GS7iLbe1TqgCN/epZQhg3gqmtYUelHPamW9a37sq48cyFG/EB0P2G/r
FSq5Tjz+gjqYFpyAhD0VWjO9/gFqBp8QuBLg5kzoupgT3boGsogy0CDe8u0eVTkP
F3HRHg8j57CtR0oRHggo9y2alnYKqz7NdCYtc71N6IzhQNfEixU0MvcTllwTV/dy
OJtU+fTE7cbrPmBvg4+8elCMEeCEd2QwZdTqBuSM6OEI/2XenGB2K/R70MUeNtSM
k/qoOSlker0UIYvyWAl4WBqbQG9pvD926I2vp/gHkhR52l9KK2f2pB+qiO9Y2KNh
GUdes6mNTrKBZ58kES3ZH8JCgaEiPuJboOI8rRdtzuv0yLXxaGYIgdfsoyCv/ba9
aB75XuNSXwswd26jIIdc01txPRjx5idp3W9Pyskmfju03n2SZDlpjM6gybe+Axfs
K43uzVHEk6nOmrqb+1uXwjih3T81t81t7Hmql0yzaIFO7WS6QgzniQNo3mTdLgzY
RXUtiB0pRBaRbIVeFM5UzO7z+tjzyhGETPG/hX00ESvBB9zRlNSZzRQkHOkDGy5C
wiO6sF5JJvPo9M+3/UghpiII845nGKMIjd2QC5otOZwzQQdVzgb+WLqavqNRdHDd
p2x2rns+GLX6187ncvUDmcKukB/ANCScggz3iedbco1DdnNQNCv2KMQM6LHovcNZ
VVUraZ7QuVAfuGHyBZzCDUkU7vO/zwvMu7hPnuS1GVf0Xm68EApuOAeajYA615Es
s1S2YkMEa1ALimHoV6T4ND26Sw0D+GxaW6q33qBJEvWSecy0x1biUbCEl3kAjSoT
0g7SA82WoOa6NH+jQBWdY0IfID1JZu8ctJGf77iZ523WpHtcqjmNfUM8Xq0DMVjV
8g3gCObYgIpHITp7OSa4scloVhmJE723RXt7I1kCH+dcjioWBuj1/S/Oh97IEXsj
PVQQhux/BmxMwqM5IihG68k/Va0OPuWJUg5+UEHD5yx2md6riJmio228p8X6Zsvh
v2A/PnXaA7z8F9BiRFMcyTHzNQWNjTodi52Htnf0LOKm1gCIHfTBEOvGVLs5FnOx
nVupskBe/QE6E8uOXQ65Ue3qIG5iWG6cu+igHCtDPV7m0C7KX0TXCneI6k7qbNPQ
SmoC/4N627k5aR5Em/LEzcDH8vmCyde+UeaAOm5hPBEDSaDAeeolFRFrFVduO0F6
IdnBVTUjwjBolnBJ71QIjZHse6zwLw1/RBpLpR1k9v1Jf1+ZPQAogxu5vXkSBVXb
-----END RCDEVS INVENTORY DATA-----
No conversion or data extraction is possible from this type of inventory file. If your goal is to use RCDevs tokens with a solution other than WebADM, please contact the RCDevs sales team and request token seeds in the standard PSKC format.
Seeds Files Conversions for Hardware Token import
To utilize hardware tokens from another provider, you need to convert the seeds file from your provider to the format supported by WebADM.
Once you have the the file inventory file into WebADM format, you can proceed with the import of that file from WebADM GUI > Import menu.
Deepnetsecurity Tokens (SafeID/Mini) conversion into WebADM Inventory
This is an example of Deepnet Security inventory file:
<data>
<header>
<manufacturerCode>DN</manufacturerCode>
<productCode>ST</productCode>
<encode>HEX</encode>
<encrypt>AES256</encrypt>
</header>
<tokens>
<token>
<serial>12345678</serial>
<seed>1A2B2395A3B45D11AFBADC510FE860035C4ED6925B12064B3B02D6FB99C5519A</seed>
</token>
</tokens>
</data>
In this instance, the secret is 1A2B2395A3B45D11AFBADC510FE860035C4ED6925B12064B3B02D6FB99C5519A in hexadecimal format. To use it with WebADM, you need to convert this hexadecimal value to Base64 first.
- HEXADECIMAL = 1A2B2395A3B45D11AFBADC510FE860035C4ED6925B12064B3B02D6FB99C5519A
Converted to:
- Base64 = GisjlaO0XRGvutxRD+hgA1xO1pJbEgZLOwLW+5nFUZo=
The Serial value must be used as the Reference value after conversion for WebADM. This value is utilized for hardware token assignment and should not be converted.
After conversion, the seed file appears as follows:
Type, Reference, Description, Data
"OTP Token", "12345678", "SafeID/Mini", "TokenKey=GisjlaO0XRGvutxRD+hgA1xO1pJbEgZLOwLW+5nFUZo=,TokenType=VE9UUA==,TokenState=MA==,OTPLength=Ng==,TOTPTimeStep=MzA="
You can now proceed to import that file into your WebADM inventory database.
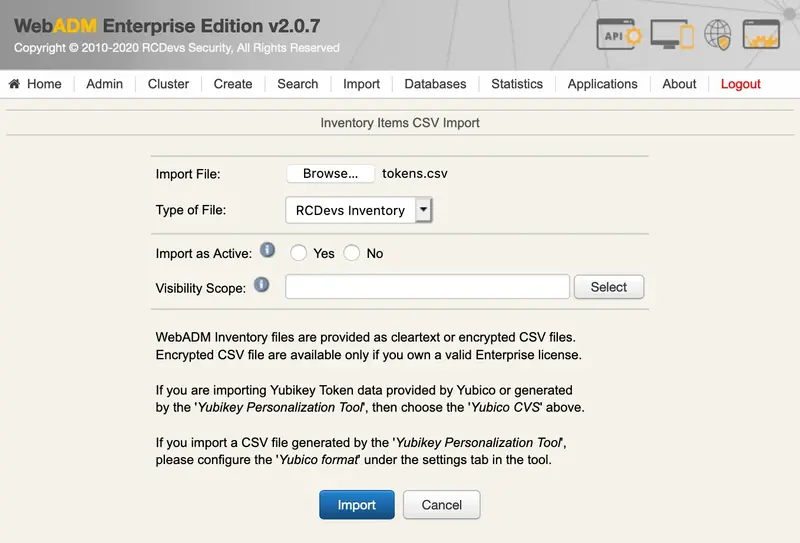
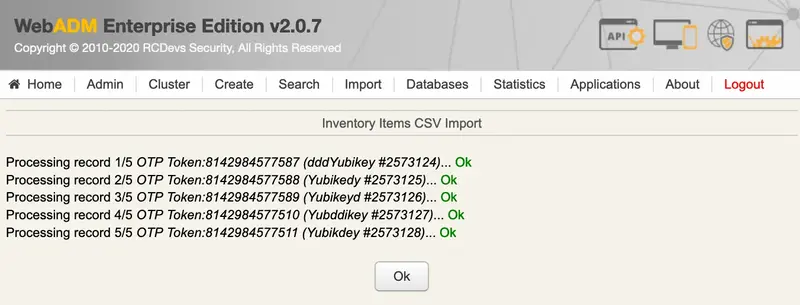

You can assign this token to a user using the token reference/serial.
If the token requires resynchronization for proper use, please refer to the last section of that documentation to perform the token resynchronization.
PSKC Files conversion into WebADM Inventory
If you already possess a standard PSKC file from your token provider, you can utilize the following script on your WebADM instance to convert your PSKC file into a WebADM inventory file:
[root@webadm ~]# /opt/webadm/websrvs/openotp/bin/pskc2inv
WebADM Inventory converter for OATH PSKC files
Usage: pskc2inv <pskc-file> <inventory-file> [<decryption-key>]
Here is an example of a PSKC file that can be provided by RCDevs (PSKC format is only provided by RCDevs upon customer request):
[root@webadm bin]# cat pskc.csv
<?xml version="1.0" encoding="UTF-8"?>
<!--
OATH PSKC import file for RCDevs WebADM
Generated on April 9, 2019, 4:13 pm
-->
<KeyContainer Version="1.0" xmlns="urn:ietf:params:xml:ns:keyprov:pskc" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:xenc="http://www.w3.org/2001/04/xmlenc#">
<KeyPackage>
<DeviceInfo>
<SerialNo>5292530833003</SerialNo>
<Model>RCDevs RC200-T6</Model>
</DeviceInfo>
<Key Algorithm="urn:ietf:params:xml:ns:keyprov:pskc:totp" Id="5292530833003">
<AlgorithmParameters>
<ResponseFormat Length="6" Encoding="DECIMAL"/>
</AlgorithmParameters>
<Data>
<Secret>
<PlainValue>tdxn5faLI0joNLIjLrIMjUxaZXc=</PlainValue>
</Secret>
<Time>
<PlainValue>0</PlainValue>
</Time>
<TimeInterval>
<PlainValue>30</PlainValue>
</TimeInterval>
</Data>
</Key>
</KeyPackage>
</KeyContainer>
To convert it into a WebADM inventory file, use the pskc2inv script as shown below:
[root@webadm bin]# ./pskc2inv pskc.csv webadm_inv.csv
Successfully converted 1 PSKC tokens.
[root@webadm bin]#
The new WebADM inventory file has been created and can now be imported through the WebADM admin GUI.
[root@webadm bin]# cat webadm_inv.csv
# OpenOTP Inventory export for OATH PSKC
# Generated by OpenOTP on January 3, 2020 10:03 am
"Type", "Reference", "Description", "Data"
"OTP Token", "5292530833003", "RCDevs RC200-T6", "TokenType=VE9UUA==,TokenKey=tdxn5faLI0joNLIjLrIMjUxaZXc=,OTPLength=Ng==,TOTPTimeStep=MzA="
Safenet/Gemalto Seeds File conversion into WebADM Inventory
RCDevs also provides a script to convert Safenet seeds file into a WebADM inventory file:
[root@webadm ~]# /opt/webadm/websrvs/openotp/bin/safenet2inv
WebADM Inventory converter for SafeNet files
Usage: safenet2inv <safenet-file> <inventory-file> <token-type>
Token type can be TOTP or HOTP
Software Tokens Migration from another Solution to WebADM
If you already have software tokens registered on end-user devices and still have the secret keys of these tokens, you can re-use them with WebADM and OpenOTP. This can be accomplished through manual token registration on a user account via WebADM Admin GUI, API, or Self-Services.
For manual token registration through the WebADM GUI, follow these steps:
- Navigate to
WebADM GUI><USER_ACCOUNT>>MFA Authentication Server. - Choose
Register/Unregister OTP Tokens. - Select
I use another Token (Manual Registration)and provide the necessary information about your token.
For example, I can reuse my token registered on my Google Authenticator if I know the following information about it:
- Token Type: TOTP, HOTP, or OCRA.
- Key Algorithm: SHA1, SHA256, or SHA512 (default is SHA1).
- Key Format: Hexadecimal, Base32, or Base64.
- Secret Key: The current token's secret key.
The size of the secret key depends on the chosen key algorithm:
- SHA1: 20 bytes
- SHA256: 32 bytes
- SHA512: 64 bytes
To allow non-standard key sizes, the SHA1 algorithm is assumed for all other key sizes in the WebADM.
Resynchronize HOTP/TOTP Tokens
To resynchronize a token, it must first be assigned to a user account. Once assigned, follow these steps:
- Navigate to the user account through WebADM GUI >
Application Actions>MFA Authentication Server. - Select
Resynchronize Tokens. - Enter the current OTP generated by the token and click
Resync.
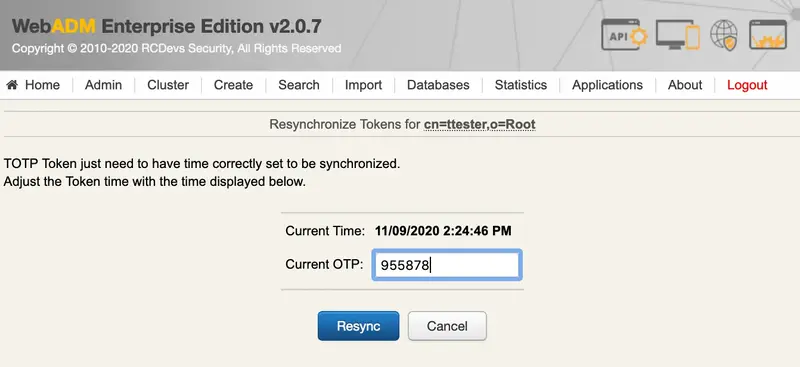
After completing these steps, you should receive a message confirming the synchronization process was successful:
For event-based tokens, resynchronization can be achieved either by providing the counter value or by generating two sequential OTPs and entering them on the resynchronization page.
Event-based tokens can be resynchronized either by providing the counter value or by generating two sequential OTP's and providing them in the resynchronization page.
