Overview
OpenOTP, a component of the WebADM Framework, is a versatile web service that provides a robust multi-factor authentication (MFA) solution, enhancing security by requiring additional verification beyond just a username and password. It supports various authentication methods, including FIDO2/Passkeys devices, YubiKeys, OATH hardware tokens, software tokens, push login via OpenOTP Token applications, SMS/Mail OTPs, Magic Links, and more.
Integrated with WebADM Policies, OpenOTP offers exceptional flexibility in configuring settings and selecting authentication methods for end-users. Authentication methods can be customized and enforced by user, group, client application, network, and risk levels.
OpenOTP also supports Passwordless authentication (if supported by the client application). For detailed information, refer to the Policies and Conditional Access documentation.
Additionally, OpenOTP includes electronic signature capabilities, PKI authentication APIs, and badging features. For more details, consult the dedicated documentation on e-signature and badging functionalities.
To configure the OpenOTP service, log in to the WebADM Administrator Portal, navigate to the Applications tab, and select Authentication from the Categories box.
Click on Configure button or Register button if the service is not already registered.
OpenOTP service (default configuration)
By accessing the OpenOTP global configuration, you set up the default configuration that will be applied to every authentication request. This is equivalent to the weight 1 settings described in the Policies and Conditional Access documentation.
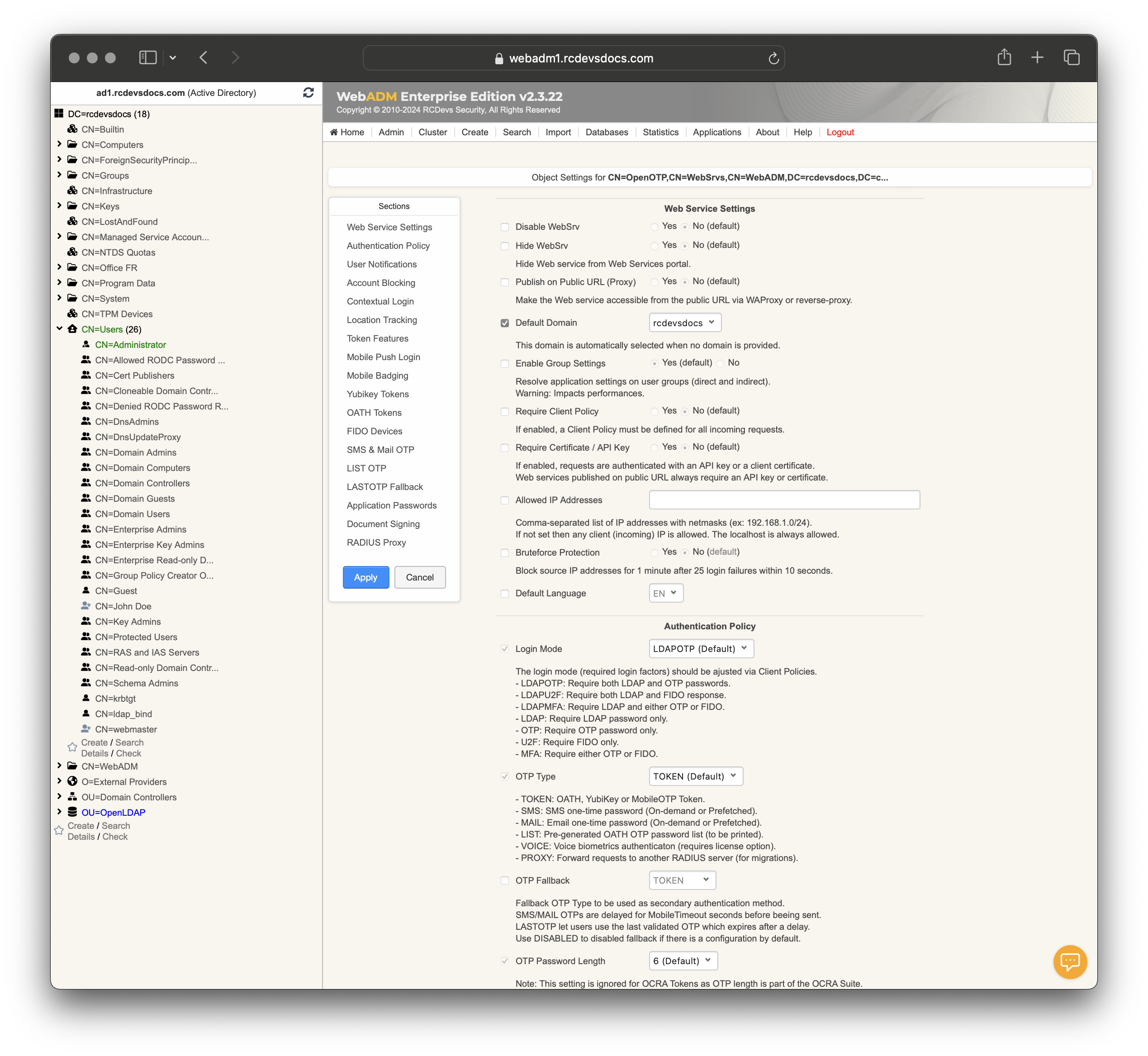
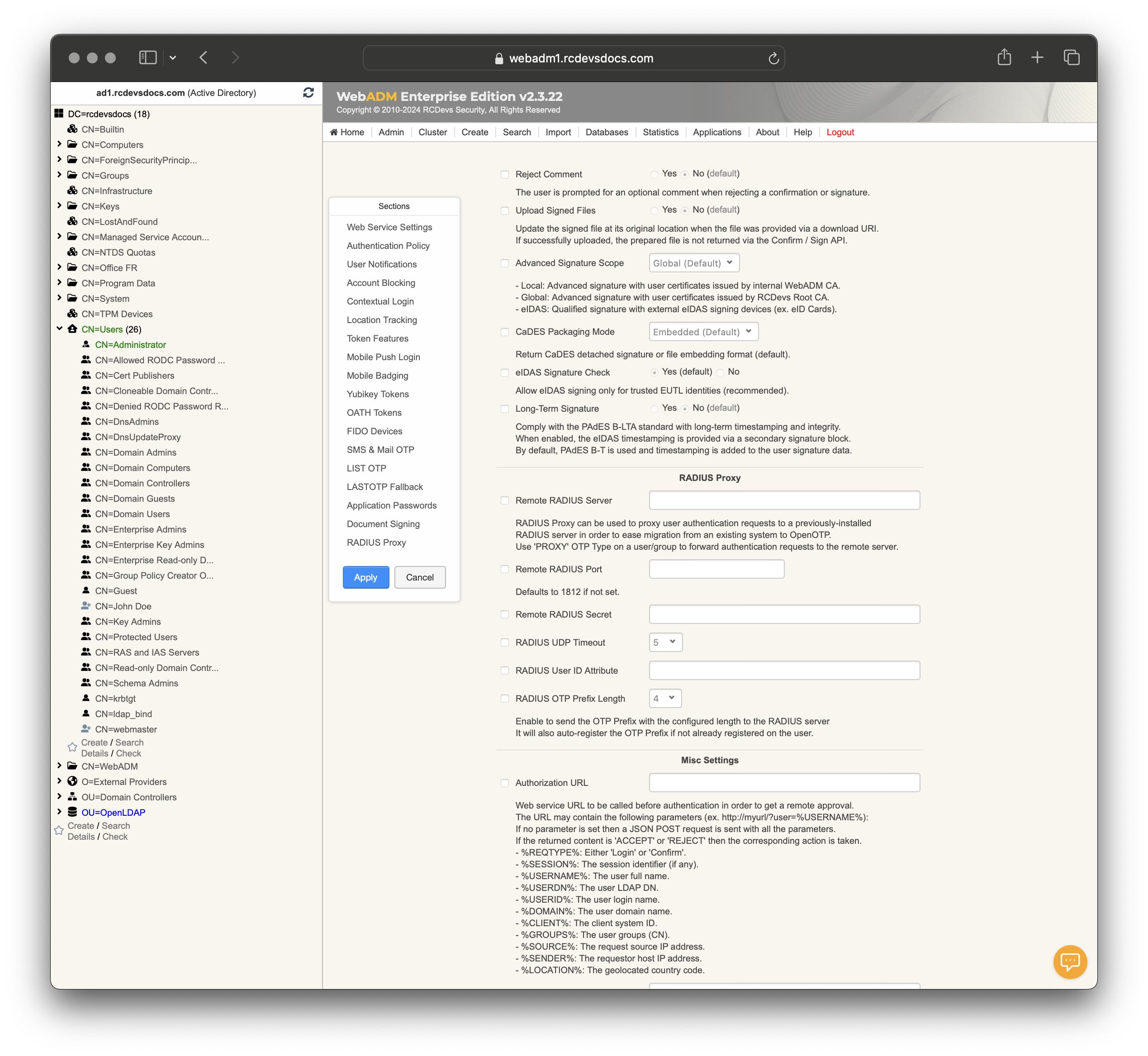
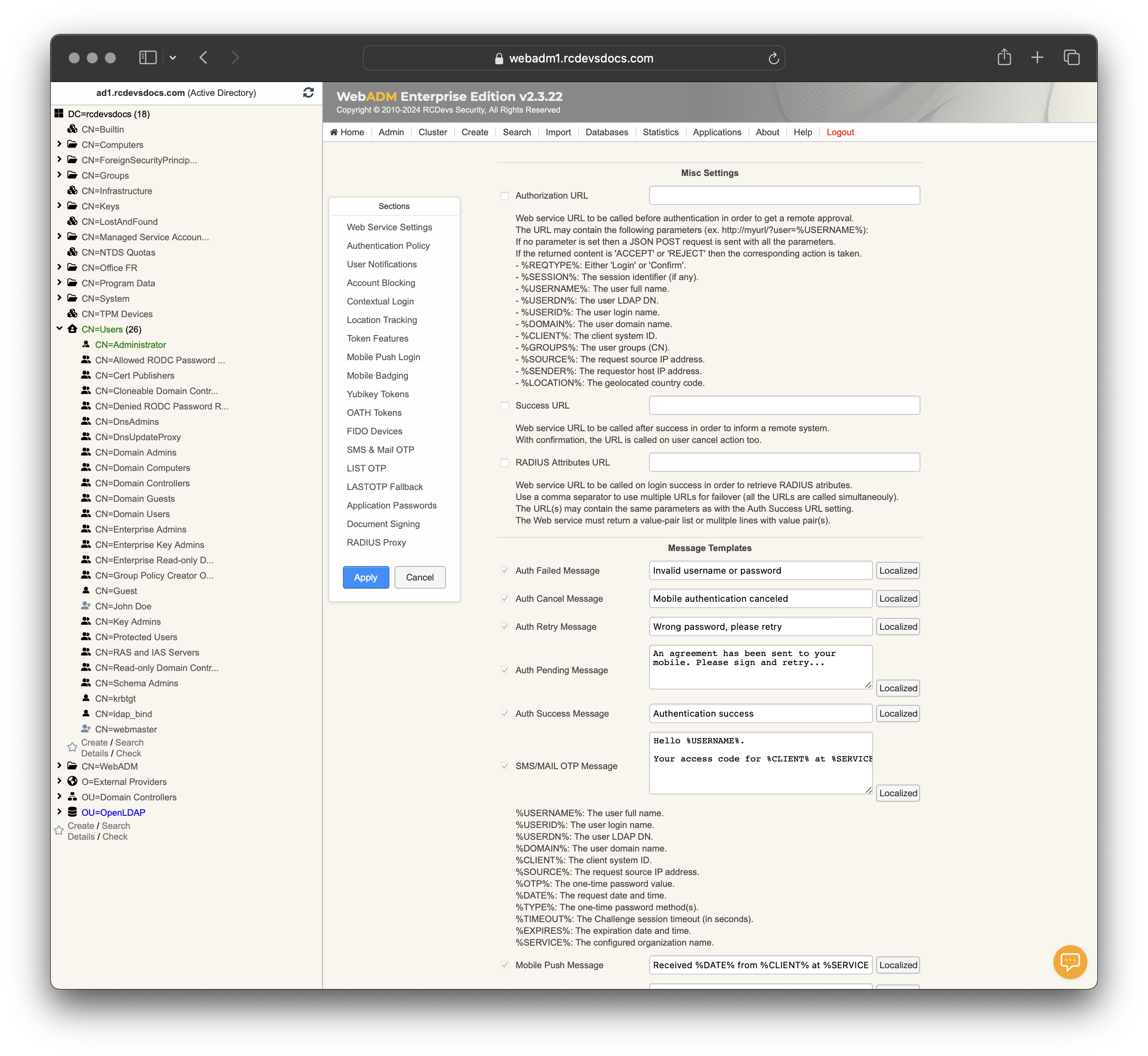
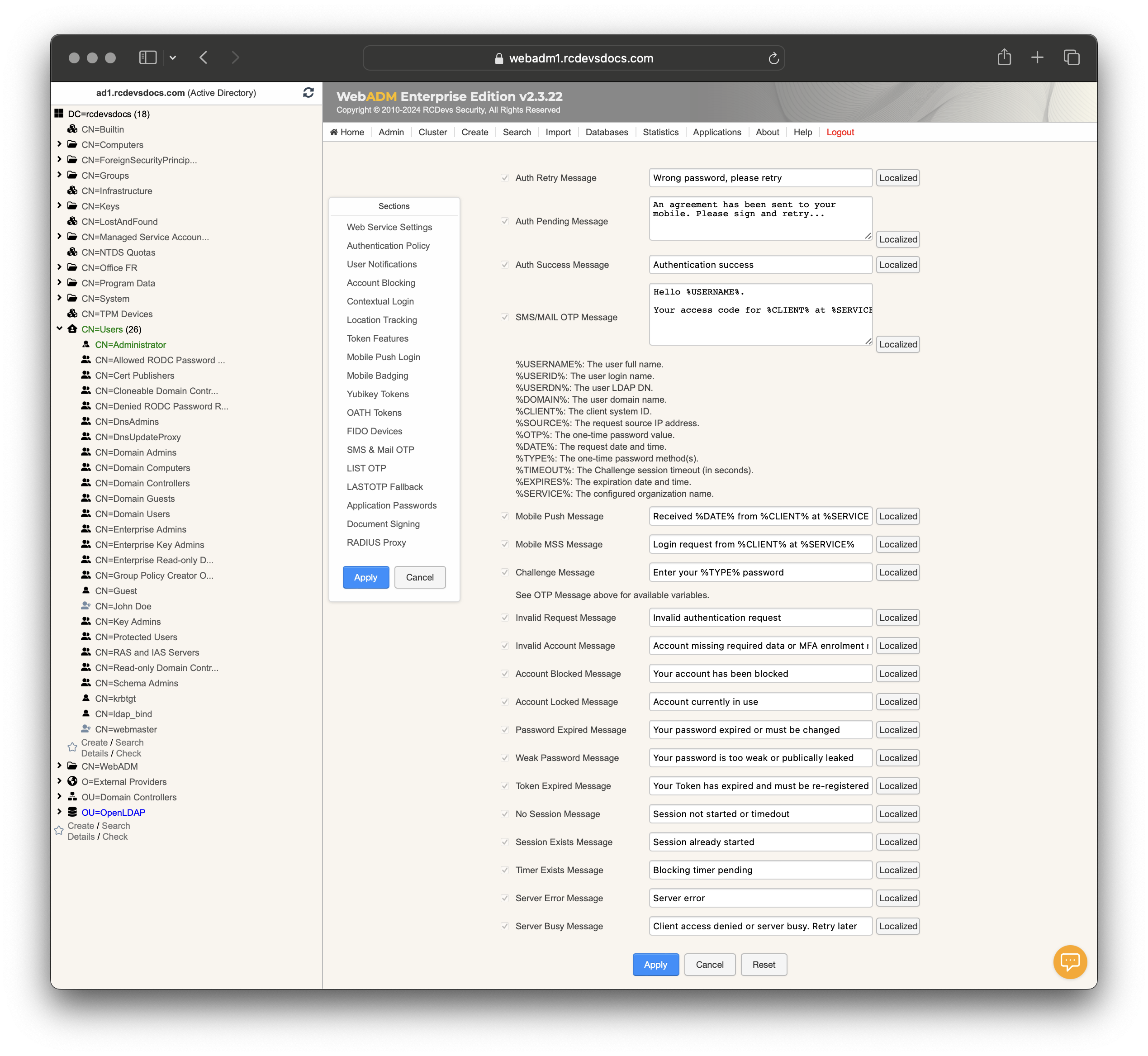
Web Service Settings:
-
Disable WebSrv: Controls whether the web service is enabled. Options are Yes or No. -
Hide WebSrv: Hides the web service from the Web Services portal. Options are Yes or No. -
Publish on Public URL (Proxy): Makes the web service accessible via a public URL through WAProxy or a reverse proxy. Options are Yes or No. A client certificate or API key must be provided by the client when requests are coming through a reverse-proxy. -
Default Domain: Specifies the default domain used when no other domain is provided. -
Enable Group Settings: Resolves application settings based on user groups. Options are Yes or No. Warning: May impact performance. -
Require Client Policy: If enabled, requires a Client Policy for all incoming requests. Options are Yes or No. -
Require Certificate / API Key: If enabled, requests must be authenticated with an API key or client certificate. Options are Yes or No. Web services published on a public URL always require an API key or certificate. -
Allowed IP Addresses: Specifies allowed IP addresses in a comma-separated list (e.g. 192.168.1.0/24). If not set, any client IP is allowed. Localhost is always allowed. -
Bruteforce Protection: Blocks source IP addresses for 1 minute after 25 login failures within 10 seconds. Options are Yes or No.
Default Language: Sets the default language for the web service.
Authentication Policy
-
Login Mode: Defines the required login factors through Client Policies:LDAPOTP: LDAP and OTP passwords.LDAPU2F: LDAP and FIDO responses.LDAPMFA: LDAP and either OTP or FIDO.LDAP: LDAP password only.OTP: OTP password only.U2F: FIDO only.MFA: Either OTP or FIDO.
-
OTP Type: Specifies the OTP methods:TOKEN: OATH, YubiKey, or MobileOTP Token.SMS: SMS one-time password (On-demand or Prefetched).MAIL: Email one-time password (On-demand or Prefetched).LIST: Pre-generated OATH OTP password list.VOICE: Voice biometrics authentication (requires license).PROXY: Forward requests to another RADIUS server.
-
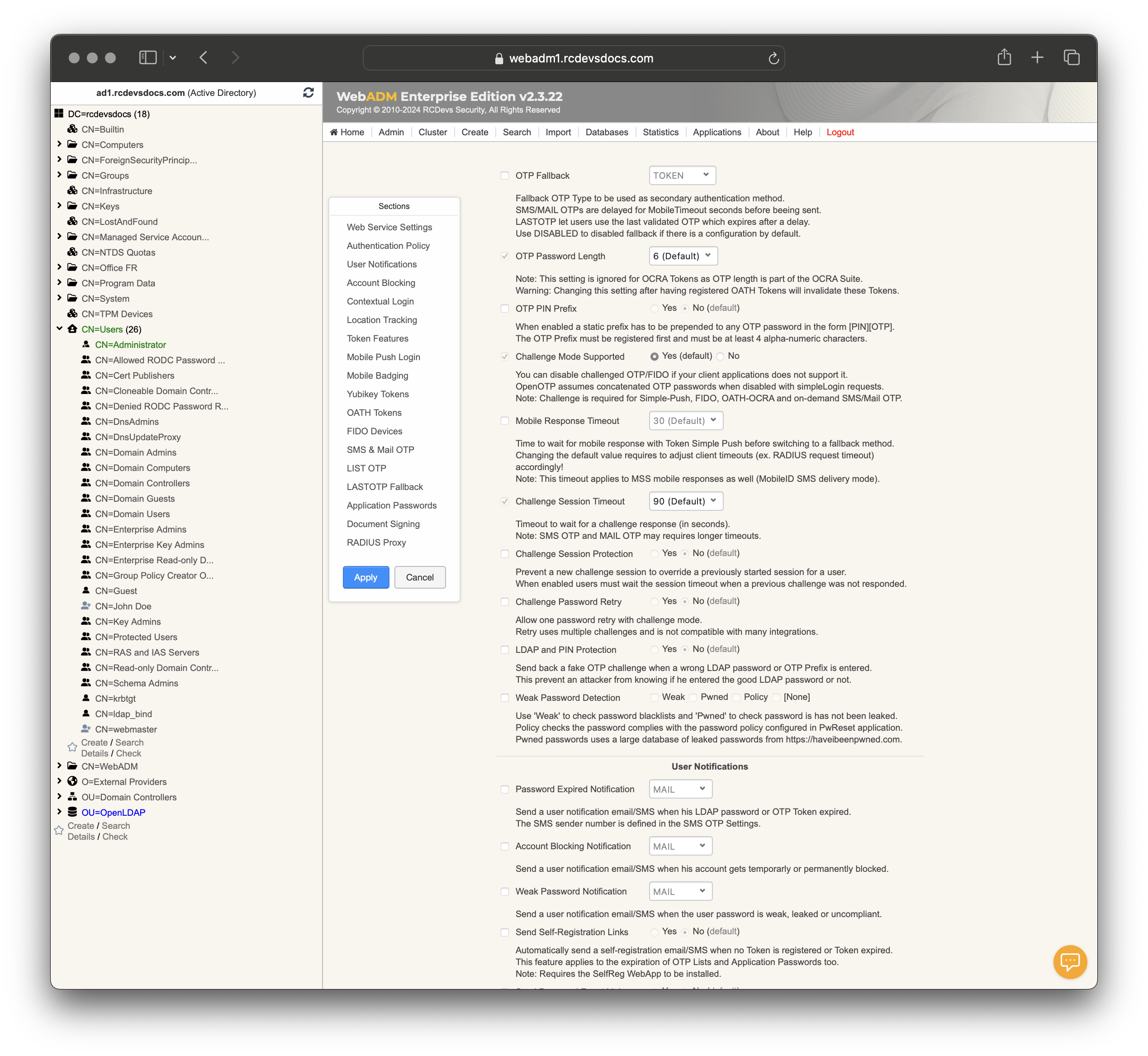
OTP Fallback: Sets a fallback OTP type. Options include SMS/MAIL, LASTOTP, or DISABLED. -
OTP Password Length: Specifies the length of OTP passwords. Note: Ignored for OCRA Tokens. -
OTP PIN Prefix: Adds a static prefix to OTP passwords. Options are Yes or No. -
Challenge Mode Supported: Allows or disables challenged OTP/FIDO. Options are Yes or No. OpenOTP assumes concatenated OTP passwords when disabled with simpleLogin requests. -
Mobile Response Timeout: Sets the timeout for mobile responses before falling back to another method. Changing the default value requires to adjust client timeouts (ex. RADIUS request timeout) accordingly! -
Challenge Session Timeout: Sets the timeout for challenge responses. -
Challenge Session Protection: Prevents new challenge sessions from overriding previous ones. Options are Yes or No.
When enabled users must wait the session timeout when a previous challenge was not responded. -
Challenge Password Retry: Allows one retry for challenge mode passwords. Options are Yes or No. Retry uses multiple challenges and is not compatible with many integrations. -
LDAP and PIN Protection: Sends a fake OTP challenge for incorrect LDAP passwords or OTP Prefixes. Options are Yes or No. This prevent an attacker from knowing if he entered the good LDAP password or not. -
Weak Password Detection: Checks passwords against blacklist (Weak) or leaked passwords (Pwned). Pwned passwords uses a large database of leaked passwords from https://haveibeenpwned.com.
User Notifications
-
Password Expired Notification: Sends an email/SMS when a password or OTP Token expires. -
Account Blocking Notification: Sends an email/SMS to the user when his account gets blocked. -
Weak Password Notification: Sends an email/SMS if a password is too weak or listed as leaked. -
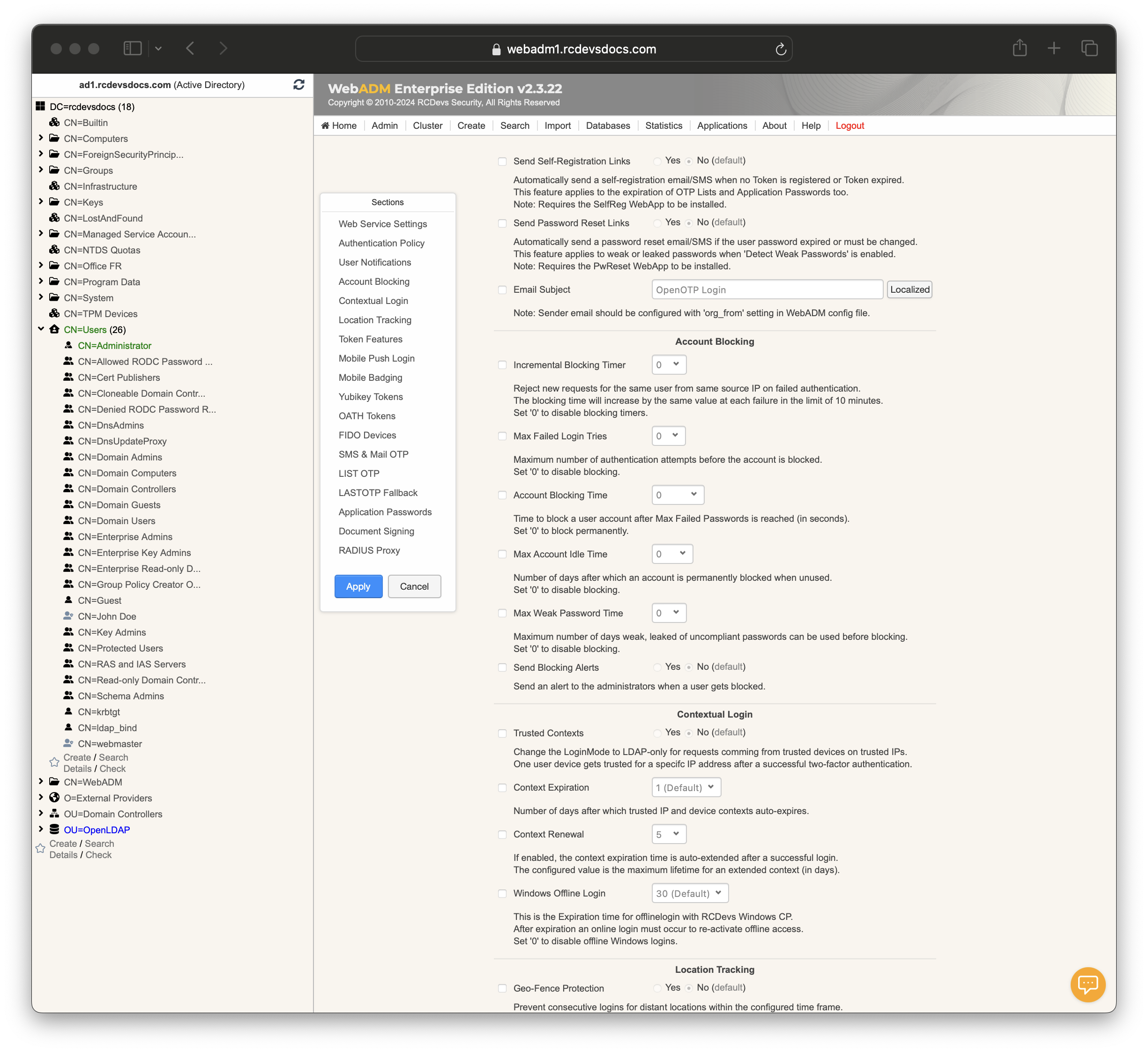
Send Self-Registration Links: Automatically send a self-registration email/SMS if the user has no Token registered or Token expired.
This feature applies to the expiration of OTP Lists and Application Passwords too. Requires the SelfReg WebApp to be installed. -
Send Password Reset Links: Sends a password reset email/SMS if the password expired or needs to be changed. Options are Yes or No (default). -
Email Subject: Configures the subject for notification emails. Sender email should be set in WebADM configuration file throughorg_fromsetting.
Account Blocking
-
Incremental Blocking Timer: This feature prevents repeated login attempts from the same user and IP address following authentication failures. Each failed attempt from the same source increments the block duration, up to a maximum of 10 minutes. Setting the block duration to0disables the blocking timer, allowing unlimited retry attempts without a delay. -
Failure Blocking Timer: Time to reject new requests after a bad password (in seconds). Set to 0 to disable. -
Max Login Tries: Maximum number of authentication attempts before blocking the account. Set to 0 to disable. -
Block Time: Time to block an account after reaching Max Login Tries (in seconds). Set to 0 to block permanently. -
Max Idle Time: Number of days an account is blocked after being unused. Set to 0 to disable. -
Max Pwned Time: Maximum number of days weak/leaked passwords can be used before blocking. Set to 0 to disable.
Send Blocking Alerts: Sends an alert to administrators when a user gets blocked. Options are Yes or No.
Contextual Login
Trusted Contexts: Changes the Login Mode to LDAP-only for requests from trusted devices on trusted IPs. Options are Yes or No.
Context Expiration: Number of days after which trusted IP and device contexts auto-expire.
Context Renewal: If enabled, extends context expiration time after a successful login.
Windows Offline Login: Expiration time for offline login with RCDevs Windows and MacOS Credential Provider. Set to 0 to disable offline logins. The value is defined in days.
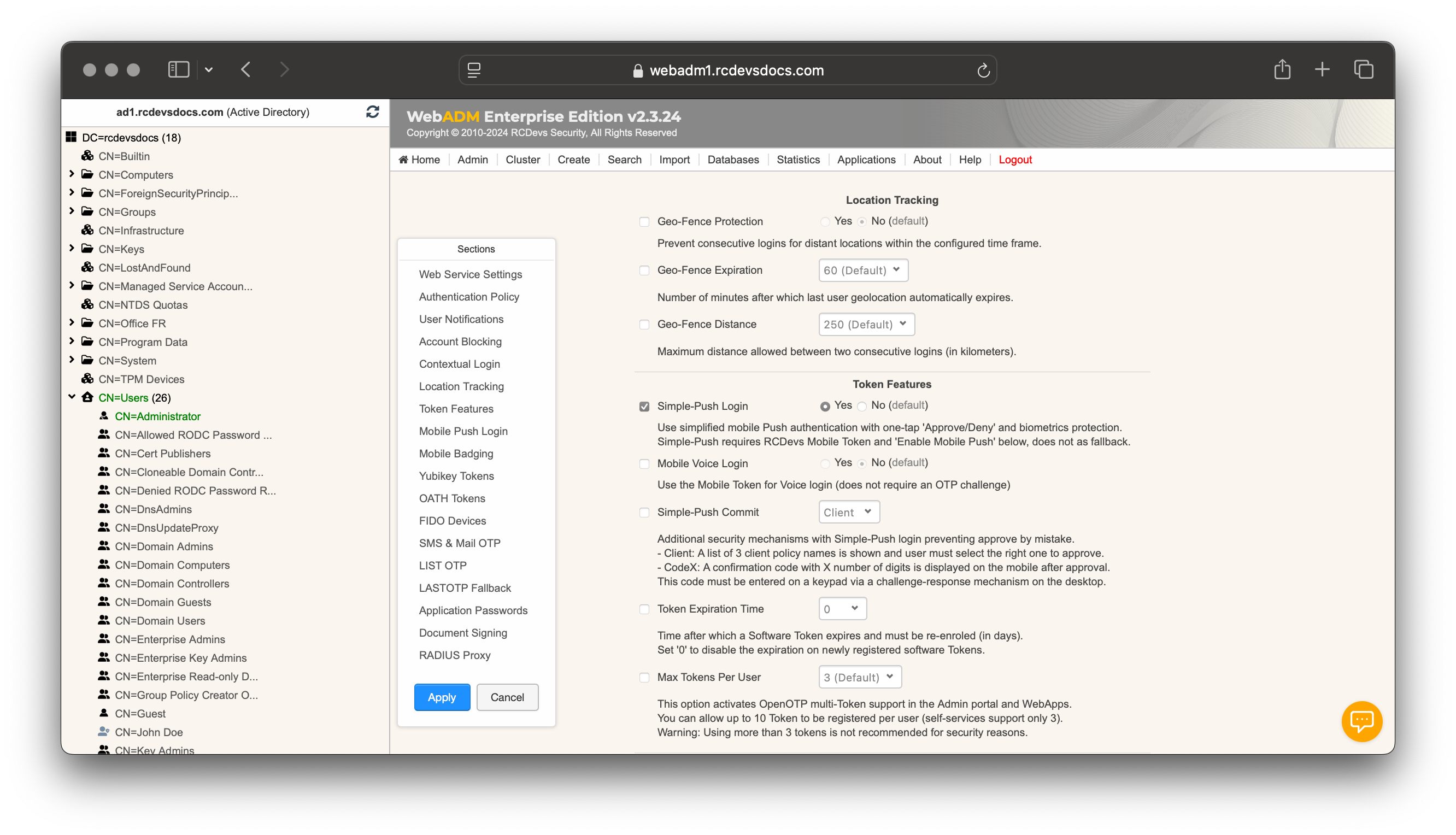
Location Tracking
Geo-Fence Protection: Prevents consecutive logins from distant locations within a configured timeframe. Options are Yes or No.
Geo-Fence Expiration: Number of minutes after which the last user geolocation automatically expires.
Geo-Fence Distance: Maximum allowed distance between two consecutive logins (in kilometers).
Token Features
Max Tokens Per User: Allows up to 10 tokens per user. Self-service supports up to 3. Warning: More than 3 tokens is not recommended for security reasons.
Simple-Push Login: Enables simplified mobile Push authentication with one-tap approval (approve/deny buttons). Options are Yes or No.
Mobile Voice Login: Uses OpenOTP Token application for Voice login. Options are Yes or No.
Simple-Push Commit: Additional security mechanisms with Simple-Push login preventing approve by mistake.
- Client: A list of 3 client policy names is shown and user must select the right one to approve.
- CodeX: A confirmation code with X number of digits (from 2 to 4) is displayed on the mobile after approval. This code must be entered on a keypad via a challenge-response mechanism on the desktop.
Token Expiration Time: Time after which a software token expires and must be re-enrolled (in days). Set to 0 to disable token expiration.
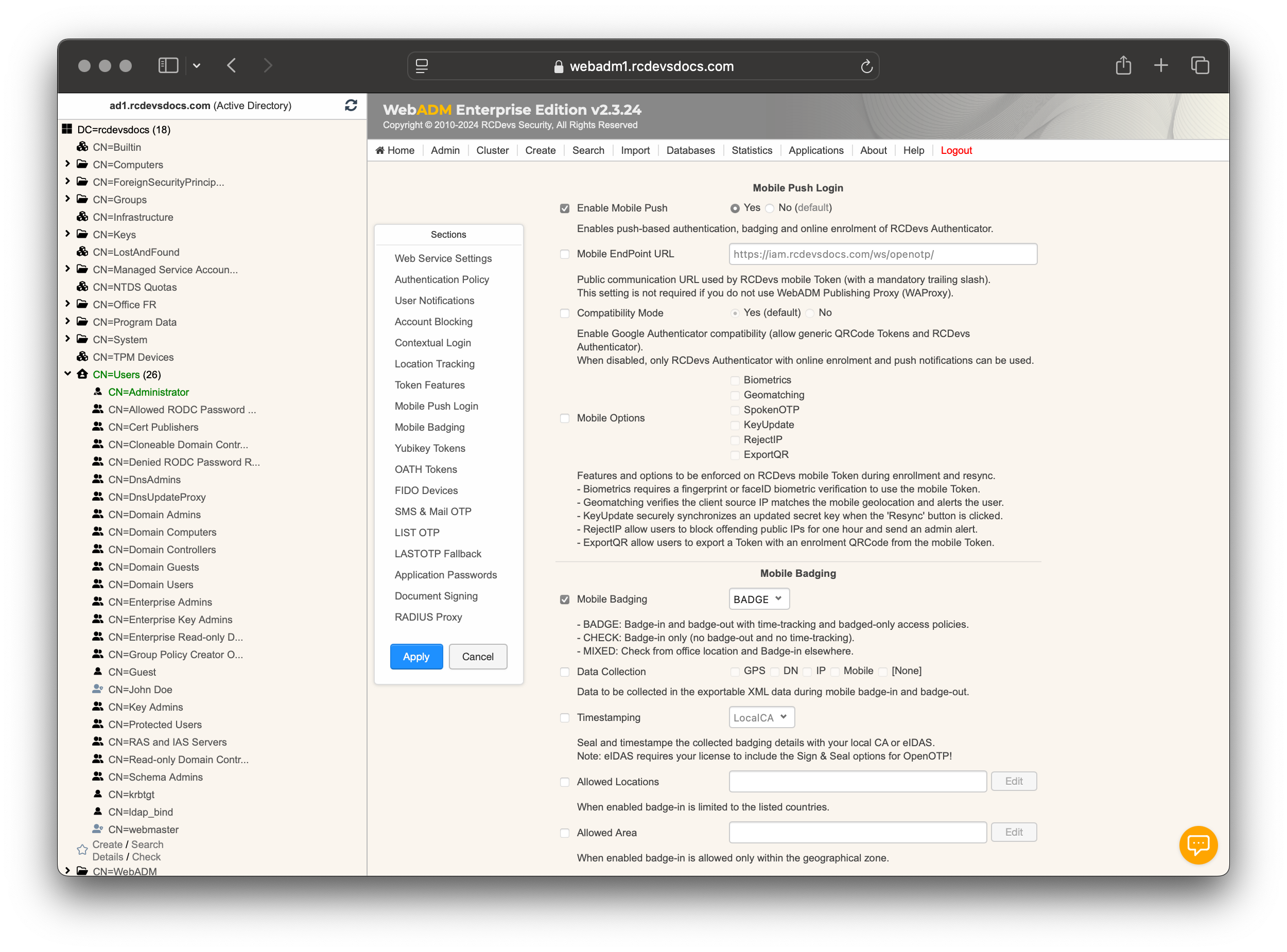
Mobile Push Login
Enable Mobile Push: Enables push-based authentication and enrollment of RCDevs Authenticator. Options are Yes or No.
Mobile EndPoint URL: Public URL used by RCDevs mobile Token. Not required if using WebADM Publishing Proxy (WAProxy).
Compatibility Mode: Enables Google Authenticator compatibility for generic QRCode Tokens. Options are Yes or No.
Mobile Options: Features and options to be enforced on RCDevs OpenOTP Token application during enrollment and resync.
KeyUpdate securely synchronizes an updated secret key when the 'Resync' button is clicked.
Biometrics: Require biometric validation before submitting the response to OpenOTP.
Geomatching: Enforce geomatching/anti-phishing protection. If the IP address performing the authentication is significantly distant from the mobile location, a warning will be displayed on the OpenOTP Mobile application when it receives the push notification. This protection is calculated on the mobile device, and GPS coordinates are not transmitted to OpenOTP.
SpokenOTP: The OTP is read aloud when a push notification is displayed.
KeyUpdate: Rotation of the token's private key: For integrations that support offline authentication (e.g., Windows/MacOS Credential Provider), users must perform an online login again to renew the offline data.
RejectIP: Allow users to block offending public IPs for one hour and send an admin alert.
ExportQR: Allow users to export a Token with an enrolment QRCode from the mobile Token.
Mobile Badging
-
Mobile Badging: Defines badging modes:BADGE: Badge-in and badge-out with time-tracking.CHECK: Badge-in only.MIXED: Check from office location and badge-in elsewhere.
-
Data Collection: Specifies data to be collected during mobile badge-in and badge-out operations. -
Timestamping: Seals and timestamps badging details. Note: eIDAS requires a license for Sign & Seal options. -
Allowed Locations: Limits badge-in to listed countries. -
Allowed Area: Restricts badge-in to a specified geographical zone.
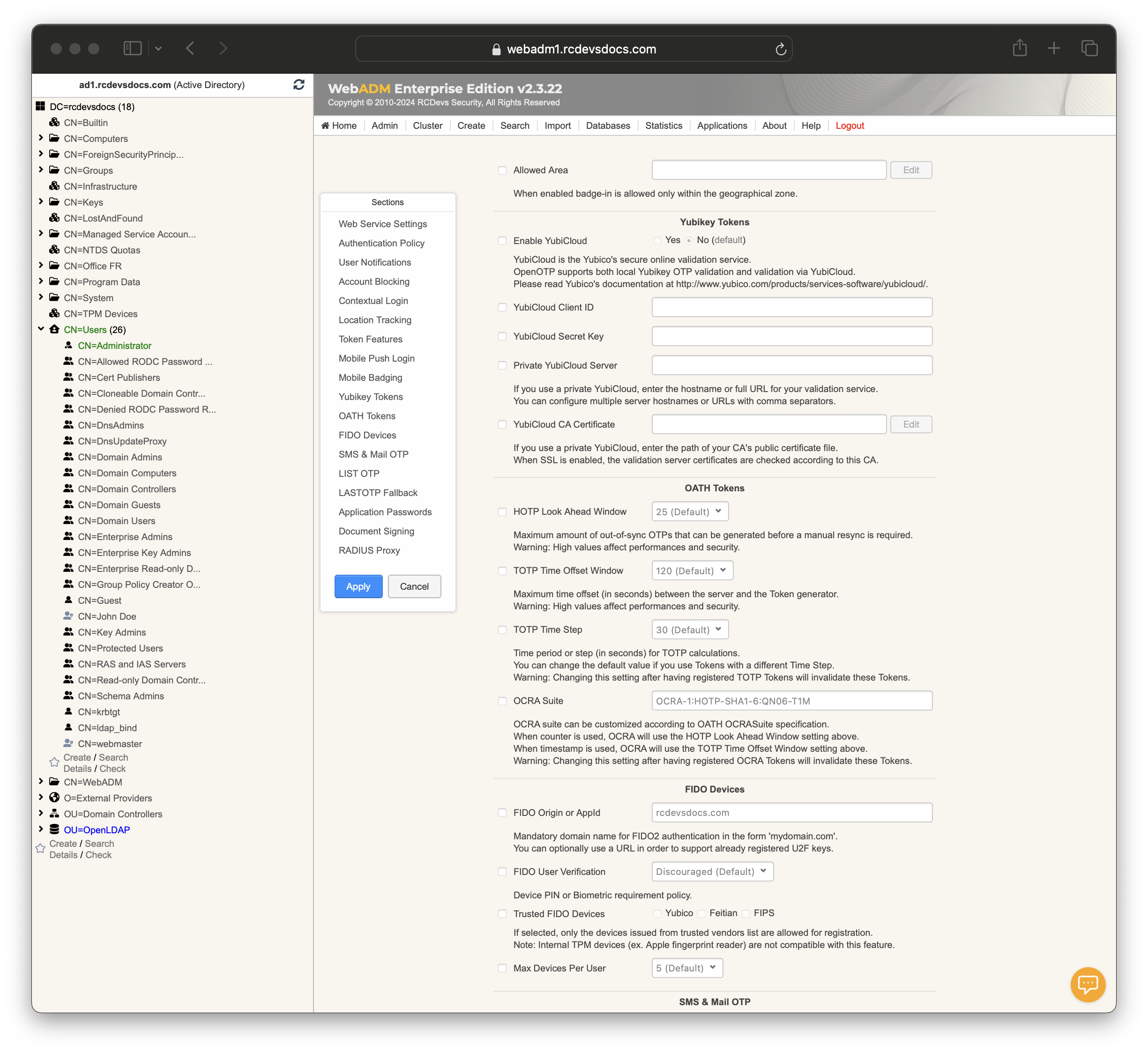
Yubikey Tokens
-
Enable YubiCloud: Supports validation via YubiCloud. Options are Yes or No. -
YubiCloud Client ID: Client ID for YubiCloud service. -
YubiCloud Secret Key: Secret key for YubiCloud service. -
Private YubiCloud Server: Specifies hostname or URL for private YubiCloud validation. Multiple entries are allowed, separated by commas. -
YubiCloud CA Certificate: Path to CA’s public certificate file for private YubiCloud.
OATH Tokens
-
HOTP Look Ahead Window: Maximum number of out-of-sync OTPs before manual resync is needed. Warning: High values impact performance and security. -
TOTP Time Offset Window: Maximum time offset between server and Token generator. Warning: High values impact performance and security. -
TOTP Time Step: Time period for TOTP calculations. Warning: Changing this after registering TOTP Tokens will invalidate them. -
OCRA Suite: Customizes OCRA suite according to OATH OCRASuite specification. Warning: Changing this after registering OCRA Tokens will invalidate them.
FIDO Devices
-
Max Devices Per User: Maximum number of FIDO devices per user. -
FIDO Origin or AppId: Domain name for FIDO2 authentication or URL for U2F keys. -
FIDO User Verification: Device PIN or biometric requirement policy. -
Trusted FIDO Devices: Limits registration to devices from selected vendors (e.g., Yubico, Feitian, FIPS).
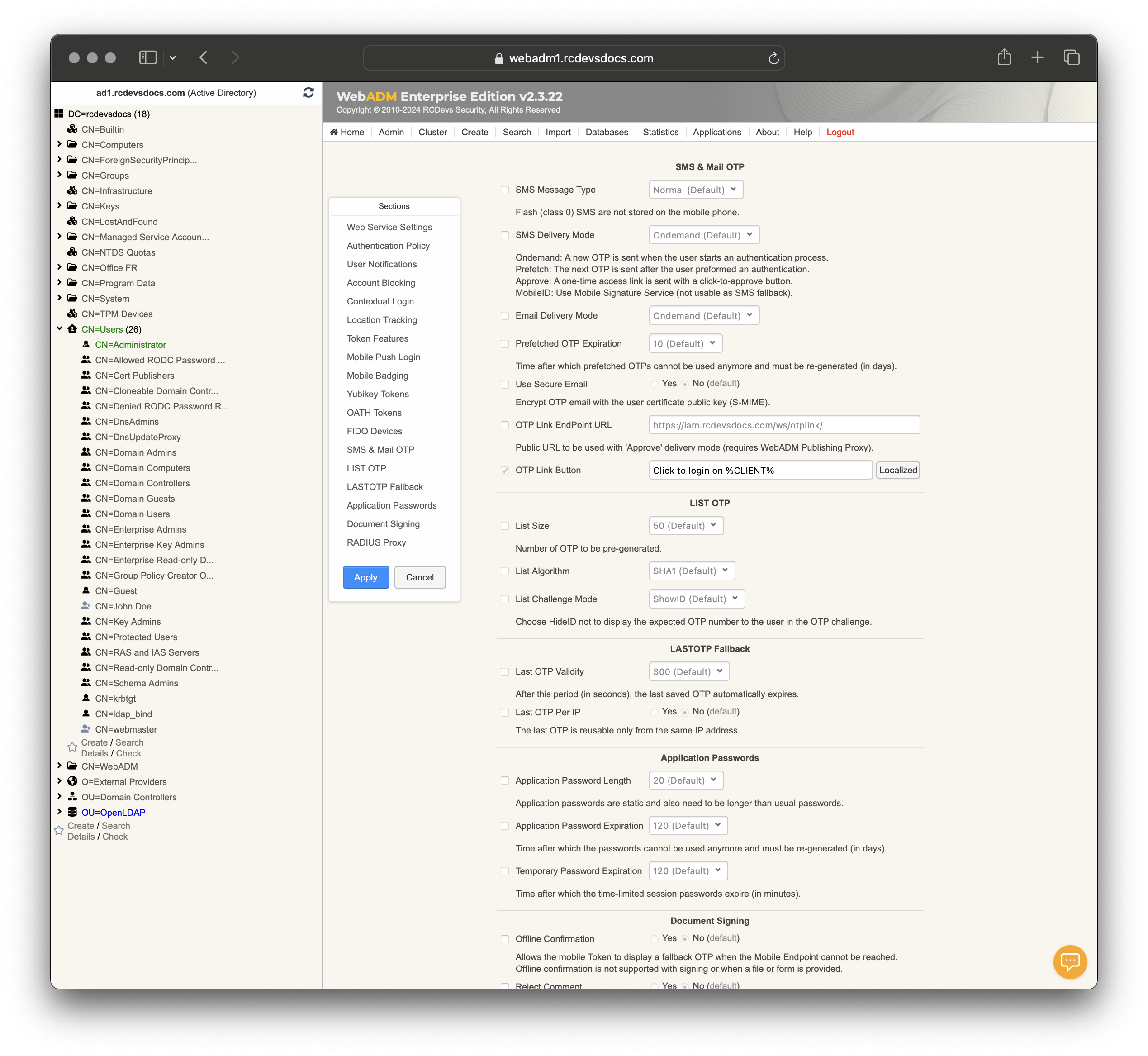
SMS & Mail OTP
-
SMS Message Type: Type of SMS message (e.g., Flash). -
SMS Delivery Mode: Options for SMS OTP delivery:Ondemand: A new OTP is sent when the user starts an authentication process.Prefetch: The next OTP is sent after the user preformed an authentication.Approve: A one-time access link is sent with a click-to-approve button. (Magic Links)MobileID: Use Mobile Signature Service (not usable as SMS fallback).
-
Email Delivery Mode: Options for email OTP delivery. -
Prefetched OTP Expiration: Time after which prefetched OTPs expire (in days). -
Use Secure Email: Encrypt OTP email with user certificate public key (S-MIME). Options are Yes or No. -
OTP Link EndPoint URL: Public URL for 'Approve' delivery mode. Requires WebADM Publishing Proxy a reverse proxy configured with WebADM.
LIST OTP
-
List Size: Number of pre-generated OTPs. -
List Algorithm: Specifies the OTP algorithm used. -
List Challenge Mode: Chooses the challenge mode for LIST OTP. HideID option prevents displaying OTP number in challenge.
LASTOTP Fallback
Allow re-use of OTP passwords. This setting is necessary when multiple authentications are chained using the same credentials. (script, bastion...)
-
Last OTP Validity: Time after which the last saved OTP expires (in seconds). -
Last OTP Per IP: Restricts last OTP use to the same IP address. Options are Yes or No.
Application Passwords
The application password must be enabled in Client Policies to be used. Once enabled in a client policy, the feature becomes available through self-service for generation.
Application Password Length: Specifies length for application passwords.Application Password Expiration: Time after which application passwords must be re-generated (in days).Temporary Password Expiration: Time after which temporary session passwords expire (in minutes).
Document Signing
-
Offline Confirmation: Allows fallback OTP when Mobile Endpoint is unreachable. Options are Yes or No. -
Reject Comment: Prompts user for an optional comment when rejecting confirmation/signature. Options are Yes or No. -
Upload Signed Files: Updates the signed file at its original location if successfully uploaded. Options are Yes or No. -
Advanced Signature Scope: Defines signature scope:Local: Internal WebADM CA.Global: RCDevs Root CA.eIDAS: External eIDAS signing devices.
-
CaDES Packaging Mode: Chooses between detached signature or file embedding format. -
eIDAS Signature Check: Allows eIDAS signing only for trusted EUTL identities. Options are Yes or No.
Long-Term Signature: Complies with PAdES B-LTA standard with long-term timestamping. Options are Yes or No.
RADIUS Proxy
-
Remote RADIUS Server: Proxies authentication requests to a remote RADIUS server. -
Remote RADIUS Port: Defaults to 1812 if not set. -
Remote RADIUS Secret: Secret key for the remote RADIUS server. -
RADIUS UDP Timeout: Sets the UDP timeout for RADIUS. -
RADIUS User ID Attribute: Configures the RADIUS user ID attribute. -
RADIUS OTP Prefix Length: Sends the OTP Prefix with configured length to the RADIUS server.
Misc Settings
-
Authorization URL: URL called before authentication to get remote approval. Supports parameters for various authentication details. -
Success URL: URL called after successful authentication to inform a remote system. -
RADIUS Attributes URL: URL called on login success to retrieve RADIUS attributes.
Message Templates
Auth Failed Message: Template for authentication failure messages.Auth Cancel Message: Template for authentication cancellation messages.Auth Retry Message: Template for authentication retry messages.Auth Pending Message: Template for pending authentication messages.Auth Success Message: Template for successful authentication messages.SMS/MAIL OTP Message: Template for OTP messages sent via SMS or email.Mobile Push Message: Template for mobile push notifications.Mobile MSS Message: Template for Mobile Signature Service messages.Challenge Message: Template for challenge mode messages.Invalid Request Message: Template for invalid request messages.Invalid Account Message: Template for invalid account messages.Account Blocked Message: Template for account blocking messages.Account Locked Message: Template for account locking messages.Password Expired Message: Template for password expiration messages.Weak Password Message: Template for weak password messages.Token Expired Message: Template for token expiration messages.No Session Message: Template for no session messages.Session Exists Message: Template for existing session messages.Timer Exists Message: Template for timer exists messages.Server Error Message: Template for server error messages.Server Busy Message: Template for server busy messages.
OpenOTP WSDL
This WSDL (Web Services Description Language) defines a web service interface named "openotpService" provided by "openotpPort" on the endpoint "https://webadm1.rcdevsdocs.com:8443/openotp/". Here's a breakdown of its components:
-
Messages: Defined data structures for requests and responses.
- Includes messages like
openotpSimpleLoginRequest,openotpNormalLoginRequest,openotpChallengeRequest, etc., each specifying parts such as username, domain, passwords, session identifiers, and various settings/options.
- Includes messages like
-
PortType: Defines operations that the service supports.
- Operations like
openotpSimpleLogin,openotpNormalLogin,openotpChallengefor OTP authentication. openotpPKILoginfor PKI (Public Key Infrastructure) authentication.openotpNormalConfirm,openotpConfirmQRCode, etc., for confirmation and signing operations.openotpStartBadging,openotpCheckBadgingfor mobile badging.openotpStatusfor checking service status.
- Operations like
-
Binding: Specifies how messages are transmitted.
- Uses SOAP binding (
rpcstyle) over HTTP. - Defines bindings for each operation to specify SOAP actions and message body encoding.
- Uses SOAP binding (
-
Service: Specifies where the service is located.
- Named
openotpServicewith a single port (openotpPort) using the definedopenotpBinding. - The endpoint URL (
soap:address) where the service is accessible.
- Named
Overall, this WSDL describes a comprehensive API for interacting with an OpenOTP service, encompassing various authentication methods (OTP, PKI), confirmation and signing operations, mobile badging, and service status checks.
<?xml version="1.0" encoding="UTF-8"?>
<definitions targetNamespace="http://www.rcdevs.com/wsdl/openotp/"
xmlns="http://schemas.xmlsoap.org/wsdl/"
xmlns:tns="http://www.rcdevs.com/wsdl/openotp/"
xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/"
xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/"
xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<!-- OTP & FIDO Authentication Methods -->
<message name="openotpSimpleLoginRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="anyPassword" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="options" type="xsd:string"/>
<part name="context" type="xsd:string"/>
<part name="retryId" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpNormalLoginRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="ldapPassword" type="xsd:string"/>
<part name="otpPassword" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="options" type="xsd:string"/>
<part name="context" type="xsd:string"/>
<part name="retryId" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpChallengeRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="session" type="xsd:string"/>
<part name="otpPassword" type="xsd:string"/>
<part name="u2fResponse" type="xsd:string"/>
<part name="voiceSample" type="xsd:base64Binary"/>
</message>
<message name="openotpLoginResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="session" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="concat" type="xsd:integer"/>
<part name="timeout" type="xsd:integer"/>
<part name="otpChallenge" type="xsd:string"/>
<part name="u2fChallenge" type="xsd:string"/>
<part name="offlineState" type="xsd:string"/>
<part name="u2fDataState" type="xsd:string"/>
</message>
<!-- PKI Authentication Methods -->
<message name="openotpPKILoginRequest">
<part name="certificate" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="options" type="xsd:string"/>
<part name="context" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpPKILoginResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="upn" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="pkiDataState" type="xsd:string"/>
</message>
<!-- Confirmation & Signature Methods -->
<message name="openotpNormalConfirmRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="form" type="xsd:base64Binary"/>
<part name="async" type="xsd:boolean"/>
<part name="timeout" type="xsd:integer"/>
<part name="issuer" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpNormalSignRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="mode" type="xsd:string"/>
<part name="async" type="xsd:boolean"/>
<part name="timeout" type="xsd:integer"/>
<part name="issuer" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
<part name="addCert" type="xsd:boolean"/>
</message>
<message name="openotpOfflineConfirmRequest">
<part name="session" type="xsd:string"/>
<part name="response" type="xsd:string"/>
</message>
<message name="openotpCheckConfirmRequest">
<part name="session" type="xsd:string"/>
</message>
<message name="openotpConfirmResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="session" type="xsd:string"/>
<part name="timeout" type="xsd:integer"/>
<part name="comment" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="form" type="xsd:base64Binary"/>
</message>
<message name="openotpSignResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="session" type="xsd:string"/>
<part name="timeout" type="xsd:integer"/>
<part name="comment" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="cert" type="xsd:base64Binary"/>
</message>
<message name="openotpConfirmQRCodeRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="form" type="xsd:base64Binary"/>
<part name="async" type="xsd:boolean"/>
<part name="timeout" type="xsd:integer"/>
<part name="issuer" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="qrFormat" type="xsd:string"/>
<part name="qrSizing" type="xsd:integer"/>
<part name="qrMargin" type="xsd:integer"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpSignQRCodeRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
<part name="mode" type="xsd:string"/>
<part name="async" type="xsd:boolean"/>
<part name="timeout" type="xsd:integer"/>
<part name="issuer" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="qrFormat" type="xsd:string"/>
<part name="qrSizing" type="xsd:integer"/>
<part name="qrMargin" type="xsd:integer"/>
<part name="virtual" type="xsd:string"/>
<part name="addCert" type="xsd:boolean"/>
</message>
<message name="openotpConfirmQRCodeResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="session" type="xsd:string"/>
<part name="timeout" type="xsd:integer"/>
<part name="qrImage" type="xsd:base64Binary"/>
</message>
<message name="openotpTouchConfirmRequest">
<part name="session" type="xsd:string"/>
<part name="sendPush" type="xsd:boolean"/>
<part name="qrFormat" type="xsd:string"/>
<part name="qrSizing" type="xsd:integer"/>
<part name="qrMargin" type="xsd:integer"/>
</message>
<message name="openotpTouchConfirmResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="timeout" type="xsd:integer"/>
<part name="qrImage" type="xsd:base64Binary"/>
</message>
<message name="openotpSealRequest">
<part name="file" type="xsd:base64Binary"/>
<part name="mode" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
</message>
<message name="openotpSealResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="file" type="xsd:base64Binary"/>
</message>
<message name="openotpListRequest" />
<message name="openotpListResponse">
<part name="code" type="xsd:string"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="jsonData" type="xsd:string"/>
</message>
<!-- Mobile Badging Method -->
<message name="openotpStartBadgingRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpCheckBadgingRequest">
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="office" type="xsd:boolean"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
</message>
<message name="openotpBadgingResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="address" type="xsd:string"/>
<part name="country" type="xsd:string"/>
<part name="location" type="xsd:string"/>
</message>
<!-- Service Status Method -->
<message name="openotpStatusRequest"/>
<message name="openotpStatusResponse">
<part name="status" type="xsd:boolean"/>
<part name="message" type="xsd:string"/>
</message>
<portType name="openotpPortType">
<operation name="openotpSimpleLogin">
<input name="openotpSimpleLoginRequest" message="tns:openotpSimpleLoginRequest"/>
<output name="openotpSimpleLoginResponse" message="tns:openotpLoginResponse"/>
</operation>
<operation name="openotpNormalLogin">
<input name="openotpNormalLoginRequest" message="tns:openotpNormalLoginRequest"/>
<output name="openotpNormalLoginResponse" message="tns:openotpLoginResponse"/>
</operation>
<operation name="openotpChallenge">
<input name="openotpChallengeRequest" message="tns:openotpChallengeRequest"/>
<output name="openotpChallengeResponse" message="tns:openotpLoginResponse"/>
</operation>
<operation name="openotpPKILogin">
<input name="openotpPKILoginRequest" message="tns:openotpPKILoginRequest"/>
<output name="openotpPKILoginResponse" message="tns:openotpPKILoginResponse"/>
</operation>
<operation name="openotpNormalConfirm">
<input name="openotpNormalConfirmRequest" message="tns:openotpNormalConfirmRequest"/>
<output name="openotpNormalConfirmResponse" message="tns:openotpConfirmResponse"/>
</operation>
<operation name="openotpConfirmQRCode">
<input name="openotpConfirmQRCodeRequest" message="tns:openotpConfirmQRCodeRequest"/>
<output name="openotpConfirmQRCodeResponse" message="tns:openotpConfirmQRCodeResponse"/>
</operation>
<operation name="openotpOfflineConfirm">
<input name="openotpOfflineConfirmRequest" message="tns:openotpOfflineConfirmRequest"/>
<output name="openotpOfflineConfirmResponse" message="tns:openotpConfirmResponse"/>
</operation>
<operation name="openotpCheckConfirm">
<input name="openotpCheckConfirmRequest" message="tns:openotpCheckConfirmRequest"/>
<output name="openotpCheckConfirmResponse" message="tns:openotpConfirmResponse"/>
</operation>
<operation name="openotpCancelConfirm">
<input name="openotpCancelConfirmRequest" message="tns:openotpCheckConfirmRequest"/>
<output name="openotpCancelConfirmResponse" message="tns:openotpConfirmResponse"/>
</operation>
<operation name="openotpTouchConfirm">
<input name="openotpTouchConfirmRequest" message="tns:openotpTouchConfirmRequest"/>
<output name="openotpTouchConfirmResponse" message="tns:openotpTouchConfirmResponse"/>
</operation>
<operation name="openotpNormalSign">
<input name="openotpNormalSignRequest" message="tns:openotpNormalSignRequest"/>
<output name="openotpNormalSignResponse" message="tns:openotpSignResponse"/>
</operation>
<operation name="openotpSignQRCode">
<input name="openotpSignQRCodeRequest" message="tns:openotpSignQRCodeRequest"/>
<output name="openotpSignQRCodeResponse" message="tns:openotpConfirmQRCodeResponse"/>
</operation>
<operation name="openotpCheckSign">
<input name="openotpCheckSignRequest" message="tns:openotpCheckConfirmRequest"/>
<output name="openotpCheckSignResponse" message="tns:openotpSignResponse"/>
</operation>
<operation name="openotpCancelSign">
<input name="openotpCancelSignRequest" message="tns:openotpCheckConfirmRequest"/>
<output name="openotpCancelSignResponse" message="tns:openotpSignResponse"/>
</operation>
<operation name="openotpTouchSign">
<input name="openotpTouchSignRequest" message="tns:openotpTouchConfirmRequest"/>
<output name="openotpTouchSignResponse" message="tns:openotpTouchConfirmResponse"/>
</operation>
<operation name="openotpSeal">
<input name="openotpSealRequest" message="tns:openotpSealRequest"/>
<output name="openotpSealResponse" message="tns:openotpSealResponse"/>
</operation>
<operation name="openotpList">
<input name="openotpListRequest" message="tns:openotpListRequest"/>
<output name="openotpListResponse" message="tns:openotpListResponse"/>
</operation>
<operation name="openotpStartBadging">
<input name="openotpStartBadgingRequest" message="tns:openotpStartBadgingRequest"/>
<output name="openotpStartBadgingResponse" message="tns:openotpBadgingResponse"/>
</operation>
<operation name="openotpCheckBadging">
<input name="openotpCheckBadgingRequest" message="tns:openotpCheckBadgingRequest"/>
<output name="openotpCheckBadgingResponse" message="tns:openotpBadgingResponse"/>
</operation>
<operation name="openotpStatus">
<input name="openotpStatusRequest" message="tns:openotpStatusRequest"/>
<output name="openotpStatusResponse" message="tns:openotpStatusResponse"/>
</operation>
</portType>
<binding name="openotpBinding" type="tns:openotpPortType">
<soap:binding style="rpc" transport="http://schemas.xmlsoap.org/soap/http"/>
<operation name="openotpSimpleLogin">
<soap:operation soapAction="openotpSimpleLogin"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpNormalLogin">
<soap:operation soapAction="openotpNormalLogin"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpChallenge">
<soap:operation soapAction="openotpChallenge"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpPKILogin">
<soap:operation soapAction="openotpPKILogin"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpNormalConfirm">
<soap:operation soapAction="openotpNormalConfirm"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpConfirmQRCode">
<soap:operation soapAction="openotpConfirmQRCode"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpOfflineConfirm">
<soap:operation soapAction="openotpOfflineConfirm"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpCheckConfirm">
<soap:operation soapAction="openotpCheckConfirm"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpCancelConfirm">
<soap:operation soapAction="openotpCancelConfirm"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpTouchConfirm">
<soap:operation soapAction="openotpTouchConfirm"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpNormalSign">
<soap:operation soapAction="openotpNormalSign"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpSignQRCode">
<soap:operation soapAction="openotpSignQRCode"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpCheckSign">
<soap:operation soapAction="openotpCheckSign"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpCancelSign">
<soap:operation soapAction="openotpCancelSign"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpTouchSign">
<soap:operation soapAction="openotpTouchSign"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpSeal">
<soap:operation soapAction="openotpSeal"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpList">
<soap:operation soapAction="openotpList"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpStartBadging">
<soap:operation soapAction="openotpStartBadging"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpCheckBadging">
<soap:operation soapAction="openotpCheckBadging"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
<operation name="openotpStatus">
<soap:operation soapAction="openotpStatus"/>
<input><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></input>
<output><soap:body use="literal" namespace="urn:openotp" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/></output>
</operation>
</binding>
<service name="openotpService">
<port name="openotpPort" binding="tns:openotpBinding">
<soap:address location="https://webadm1.rcdevsdocs.com:8443/openotp/"/>
</port>
</service>
</definitions>
In the next section, we are going to describe the different methods.
Method descriptions
Authentication
These methods are used to send an authentication request based on username/password(s) or based on user certificates.
openotpSimpleLoginRequest and openotpNormalLoginRequest
The request contains the following attributes:
- username: User login name (mandatory).
- domain: User login domain (optional if OpenOTP as a default domain setting set).
- ldapPassword (openotpNormalLogin): User LDAP password (mandatory if OpenOTP login mode setting is LDAPOTP or LDAP).
- otpPassword (openotpNormalLogin): One-time password (optional and usable only with Token OTPs).
- anyPassword (openotpSimpleLogin): LDAP password or one-time password.
- client: Client identifier (NAS) to be used in service logs (defaults to the client IP address).
- source: IP address of the end user system (optional).
- settings: List of OpenOTP settings which will override the user/group/application server-side
settings (ex. LoginMode= LDAPOTP, OTPType=SMS).
The response contains the following attributes:
- code:
- 0 means an authentication failure.
- 1 means an authentication success.
- 2 means an authentication challenge.
- message: The server reply message to be displayed to the user. With code 2, the message contains the challenge message.
- session: With challenge, this is the session ID to be passed in the openotpChallenge request.
- timeout: With challenge, this is the remaining session time to send the challenge response.
- data: This attribute contains the ReplyData set in the LDAP user or group settings.
- u2fChallenge: The list of U2F challenges in the form
<JSON Challenge 1>,<JSON Challenge 2>.
openotpChallengeRequest
This method is used when the openotpLogin returned a challenge (code 2). This is the second request to be sent containing the user one-time password.
The request contains the following attributes:
- username: User login name (mandatory).
- domain: User login domain (optional if OpenOTP as a default domain setting set).
- session: The session ID returned in the openotpLogin response.
- otpPassword: The user one-time password (i.e. challenge response).
- u2fResponse: The U2F response in JSON format (U2F challenge response).
The response contains the following attributes:
- code:
- 1 means authentication success.
- 0 means authentication failure.
- message: The server reply message to be displayed to the user.
- data: See openotpLogin response above.
openotpPKILoginRequest
- certificate: User certificate value received in PEM format.
- client: Value sent in the request to identify the client system and match client policies.
- source: IP address of the end user system (optional).
- settings:
- options:
- context:
- virtual
