Overview
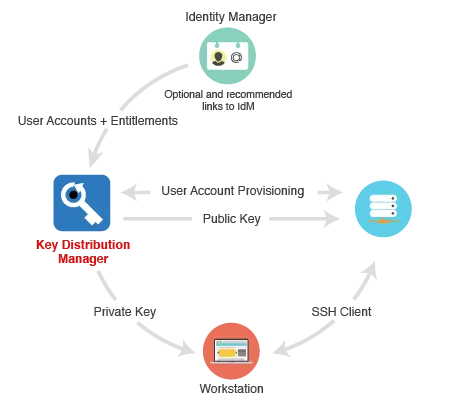
SpanKey is a centralized SSH key server for OpenSSH, which stores and maintains SSH public keys in a centralized LDAP directory (i.e. Active Directory). With SpanKey there is no need to distribute, manually expire or maintain the SSH public keys on the servers. Instead, the SpanKey agent is deployed on the servers and is responsible for providing the users’ public keys on-demand. The SpanKey server provides per-host access control with “server tagging”, LDAP access groups, centralized management from the RCDevs WebADM console, shared accounts, privileged users (master keys), recovery keys... It supports public key expiration with automated workflows for SSH key renewal (via Self-Services). SpanKey supports centralized SUDO definitions per group, user, and client system through the sudo plugin included in the SpanKey client package. Auditd rules can also be centrally managed to capture actions performed by authenticated users and forward the generated logs to the SpanKey server and, optionally, to a SIEM if one is available within the company.
SSH sessions can be graphically recorded and replayed through the WebADM Administrator portal.
Additionally, you can also enable Multi-factor authentications (LDAP password, OTP and U2F validation are supported) after the SSH key validation process. The SSH key can also be configured on a smartcard device.
For this recipe, you will need to have WebADM installed and configured. Please, refer to WebADM Installation guide before installing SpanKey server.
SpanKey server must be installed on the WebADM server(s).
Packages Installation
System Requirements
Version 2.2.0 of SpanKey Client is designed to run on Linux x86_64 with GLIBC >= 2.12. The package itself is almost but not fully standalone. To run it properly you must have the package 'net-tools' already installed on your machine, at least one WebADM server in version >=1.7.6 running OpenOTP and SpanKey server in version >=2.0.6 and at least OpenSSH 6.2 is needed.
RHEL & CentOS through RCDevs Repository
SpanKey Server Installation
dnf install spankey
After the Spankey server installation, you need to restart WebADM services:
/opt/webadm/bin/webadm restart
To enable SpanKey web service, you need to log in on the WebADM GUI. Under Applications tab, click Authentication in category box and you should find SSH Public Key Server (SpanKey). Click on REGISTER button.
SpanKey Client and NSCD Installation
The SpanKey client requires nscd and OpenSSH. NSCD is the Linux name service caching daemon which is required for caching NSS information on the Linux client. Without NSCD, any user or group ID resolution will trigger SpanKey NSS requests. Caching on the client side will prevent your servers from being overloaded with NSS requests.
dnf install spankey_client nscd
systemctl enable nscd
Be aware that at least OpenSSH 6.2 is needed. (Added a sshd_config option AuthorizedKeysCommand to support fetching authorized_keys from a command in addition to (or instead of) from the filesystem.)
Debian & Ubuntu through RCDevs Repository
SpanKey Server Installation
apt install spankey
After the Spankey server installation, you need to restart WebADM services:
/opt/webadm/bin/webadm restart
To enable SpanKey web service, you need to log in on the WebADM GUI. Under Applications tab, click Authentication in category box and you should find SSH Public Key Server (SpanKey). Click on REGISTER button.
SpanKey Client and NSCD Installation
apt install spankey-client nscd
The SpanKey client requires nscd and OpenSSH. NSCD is the Linux name service caching daemon which is required for caching NSS information on the Linux client. Without NSCD, any user or group ID resolution will trigger SpanKey NSS requests. Caching on the client side will prevent your servers from being overloaded with NSS requests.
Be aware that at leat OpenSSH 6.2 is needed. (Added a sshd_config option AuthorizedKeysCommand to support fetching authorized_keys from a command in addition to (or instead of) from the filesystem.) With Ubuntu servers, depending on your OS setup, you may need to install libldap as well.
Installation Using the Self-Installer
You first need to download the Spankey software package. You can download the latest package on the RCDevs Website. Download and copy the SpanKey server self-installer package to your server. You can copy the package file to the server with WinSCP or SCP. Then connect via SSH to your server, uncompress and run the self-installer package with:
gunzip spankey-2.0.x-x.sh.gz
bash spankey-2.0.x-x.sh
Follow the installer.
For the SpanKey client:
gunzip spankey_client-2.1.x.sh.gz
bash spankey_client-2.1.x.sh
Follow the installer and don't forget to install the NSCD package.
Configurations
SpanKey Server
Once SpanKey server package is installed, you have to enable SpanKey service in WebADM. Go to the WebADM Administrator console, click on Applications tab > Authentication and click on Register button for SSH Public Key Server. The default configuration is ready and suited for most Linux environments, but for initial tests, it is recommended to click on CONFIGURE button and set the following options in SSH Public Key Server (SpanKey server):
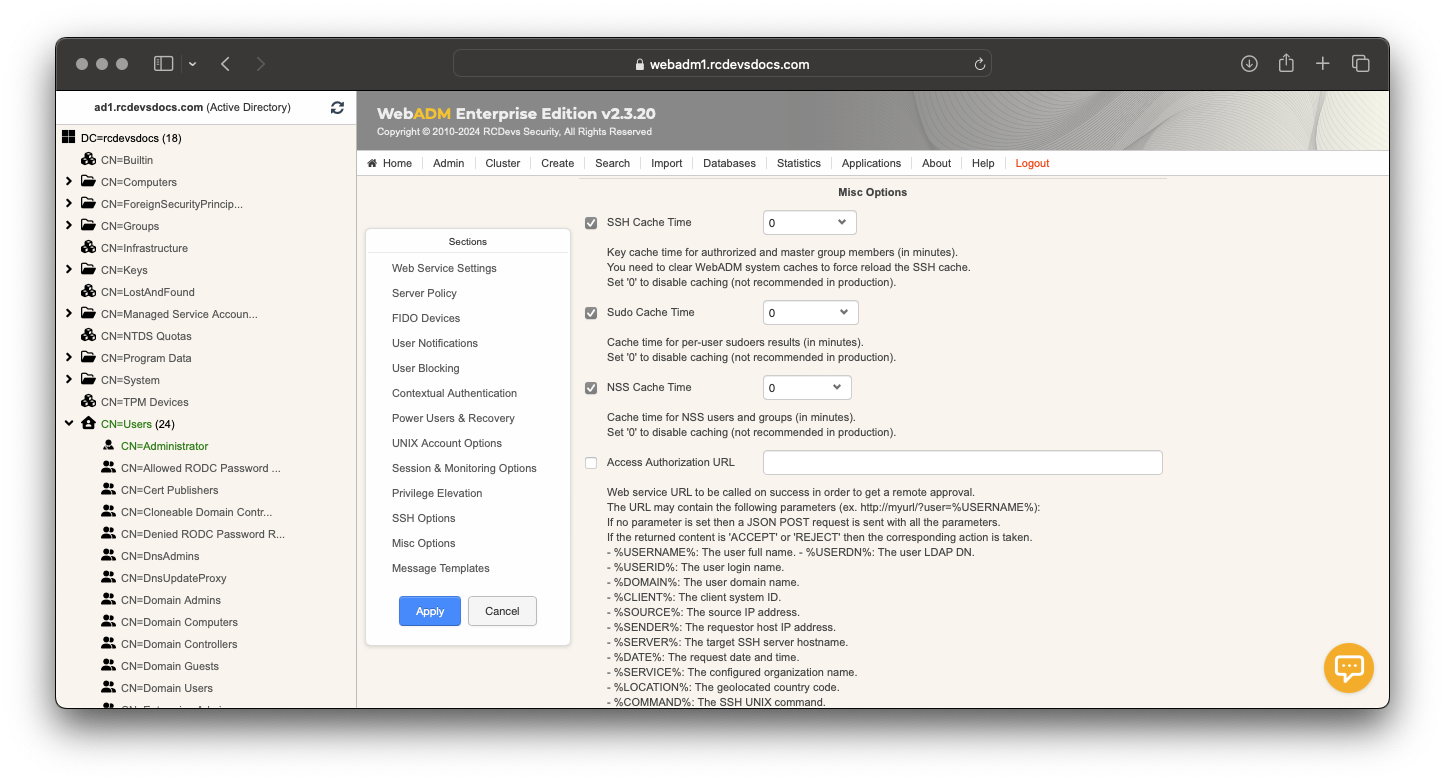
This will disable server caching, generally helpful during configuration stage and tests.
For production server caching is highly recommended!!!
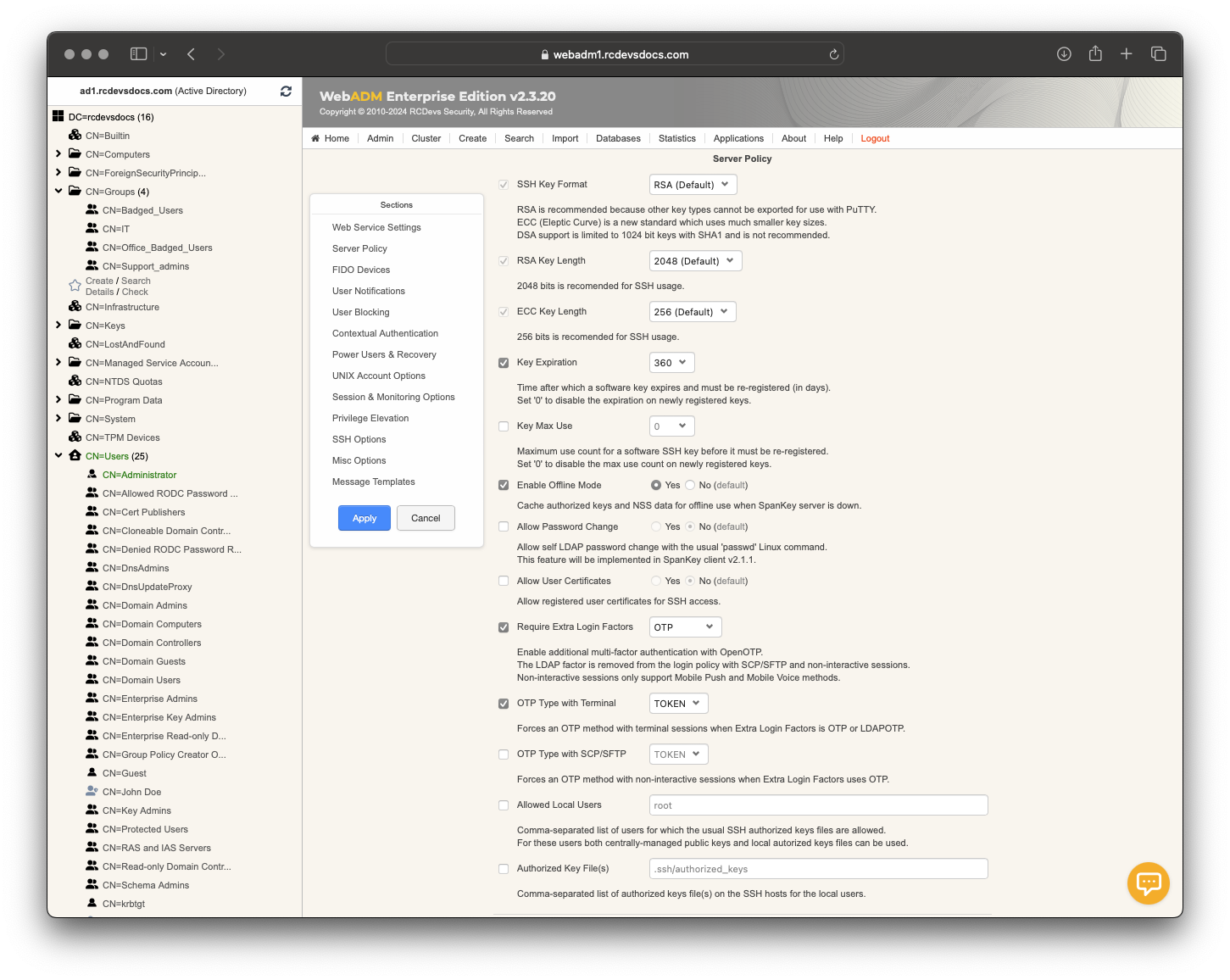
- The SSH Key format can be defined here.
- RSA Key Length can also be settled here.
- The SSH Key Lifetime can be adjusted too.
- Send Self-Registration: This option can be enabled if you want to have a new self-registration request when the SSH key has expired.
- Enable Offline Mode: Offline mode can be enabled in case of the SpanKey server is unavailable.
- Require Extra Login Factors: An OTP validation can be added during the authentication workflow.
Some other settings can be enabled on Spankey server:
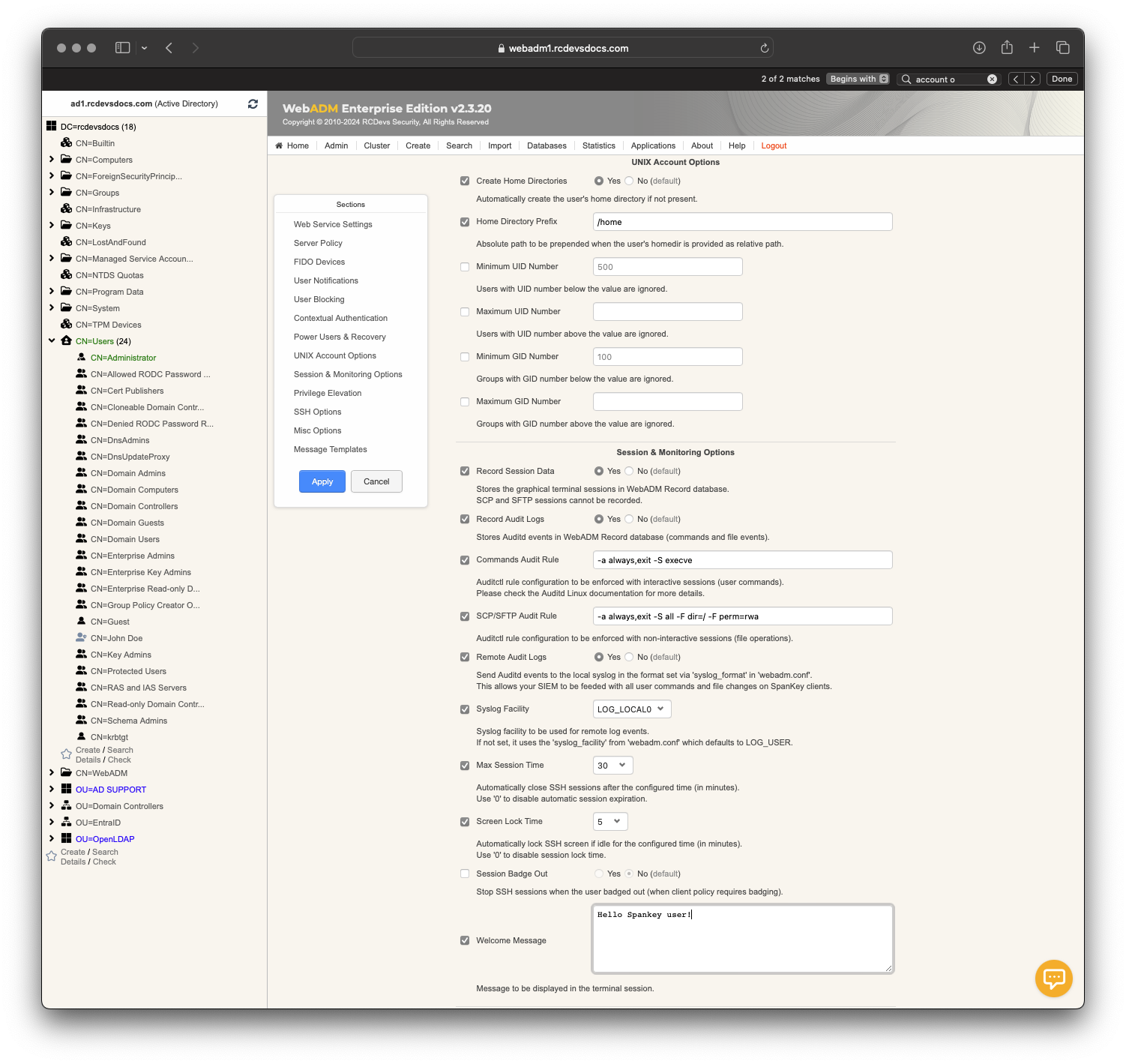
- Create Home Directory: If enabled, the user home directory will be automatically created during the first login if not present.
- Max Session Time: This setting can be settled if you want to define a maximum session time.
- Record Session Data: This is a new feature of SpanKey! This setting allows you to record and store in SQL database, terminal sessions, SFTP sessions. Sessions are replayable video which can be found in
Databasestab >Recorded Sessionsunder WebADM Admin Console.
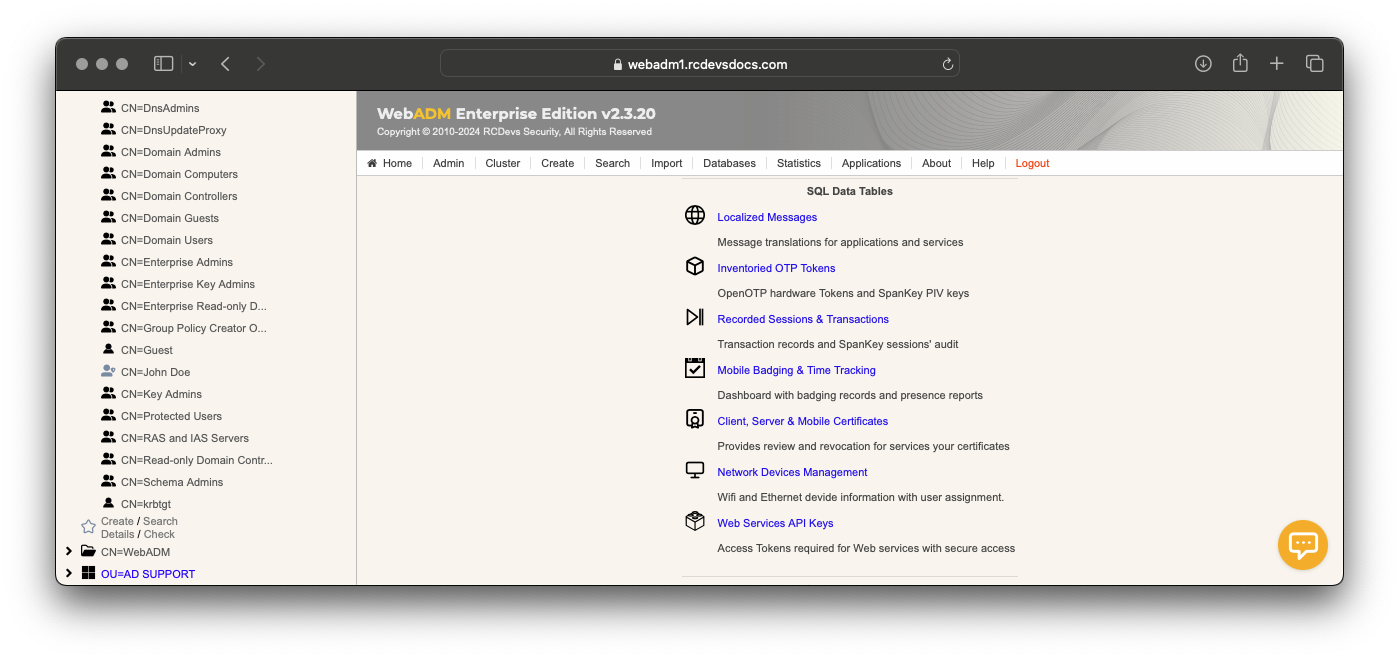
Under SSH Public Key Server configuration, you can find various configurations options to set access controls to your SSH key-based logins, such as Master Group, Backup Keys, Authorized Group, Tagging... Some of these settings are described in the chapter "Advanced Configuration".
Require client certificate or API Key for SpanKey client is highly recommended for production use!
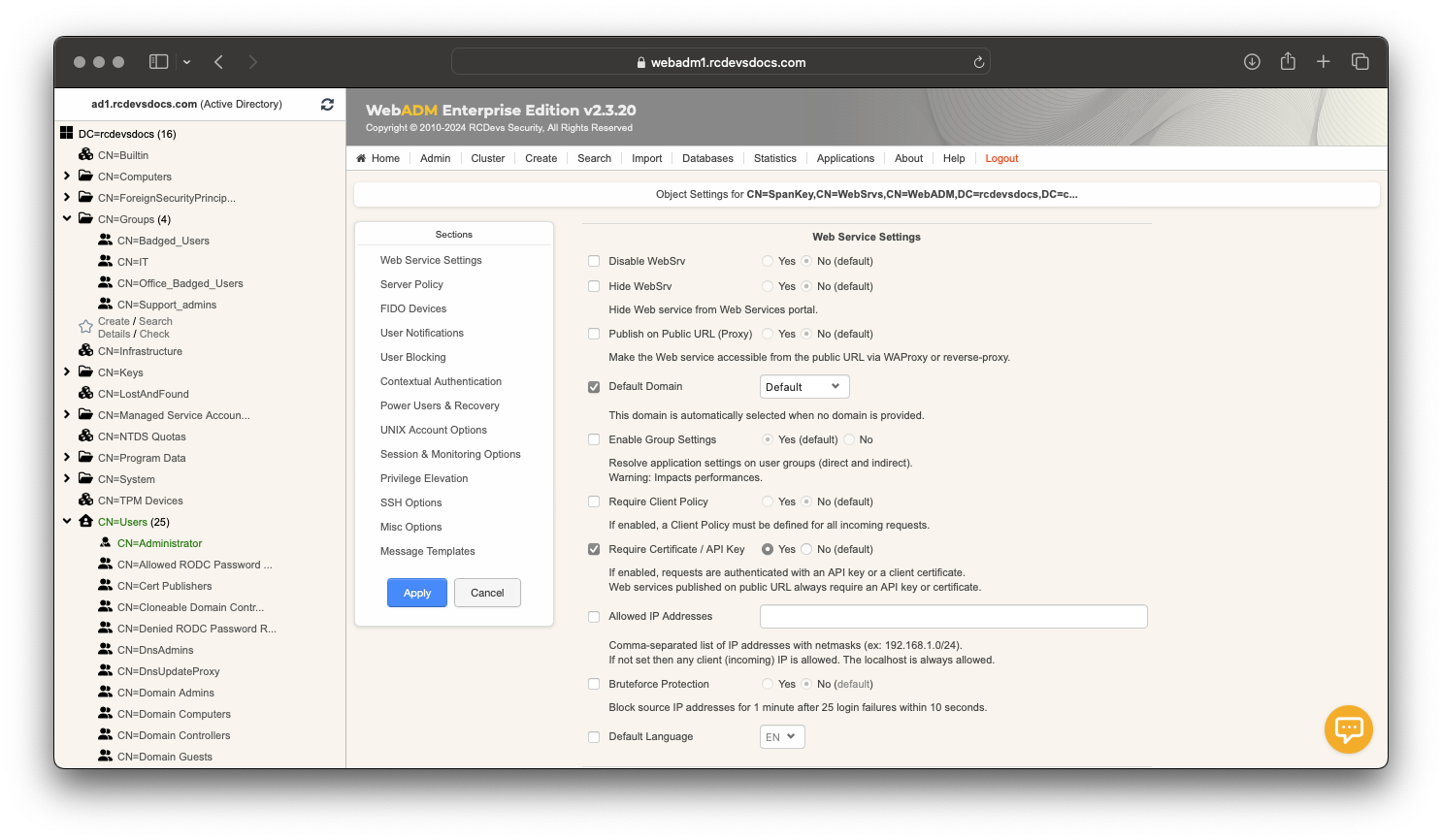
If you enable this option, every SpanKey client who actually works without a client certificate will stop working. To solve this, you can generate a client certificate through WebADM Admin GUI > Admin tab > Create Server or Client Certificate and import the generated certificate in /opt/spankey/conf/ folder of your SpanKey client.
SpanKey Client
The SpanKey client consists of two components activated at setup time.
- SSH component - provides a user login with public keys stored within a directory server (Active Directory, OpenLDAP, Open Directory…).
- NSS component - provides a native mapping of your directory users and groups to those in Linux.
SpanKey Client Setup Script
At the end of the installation of the SpanKey package, run the following command to launch setup wizard: /opt/spankey/bin/setup. The wizard will prompt you for the details similar to below:
root@ubuntu18-client:~# /opt/spankey/bin/setup
Setup has already been run for this installation. Overwrite (y/n)?: y
Overwriting...
Enter one of your running WebADM node IP or hostname []: 192.168.4.160
Do you want to enable SpanKey Client for OpenSSH server (y/n)? [N]: y
Do you want to enable SpanKey Client NSS plugin (y/n)? [Y]: y
Do you want to register SpanKey Client logrotate script (y/n)? [Y]: y
Do you want SpanKey Client to be automatically started at boot (y/n)? [Y]: y
Primary OpenOTP service URL is: 'https://192.168.4.160:8443/spankey/'
Secondary OpenOTP service URL is: 'NONE'
Enable SpanKey Client for OpenSSH server: 'YES'
Enable SpanKey Client NSS plugin: 'YES'
Register SpanKey Client logrotate script: 'YES'
SpanKey Client must be automatically started at boot: 'YES'
Do you confirm (y/n)?: y
Applying SpanKey Client settings from default configuration files... Ok
Retrieving WebADM CA certificate from host '192.168.4.160'... Ok
The setup needs now to request a signed 'SpanKey' client certificate.
This request should show up as pending in your WebADM interface and an administrator must accept it.
Waiting for approbation...
At this step, you have to log in on the WebADM Administration GUI to approve the SSL certificate request.
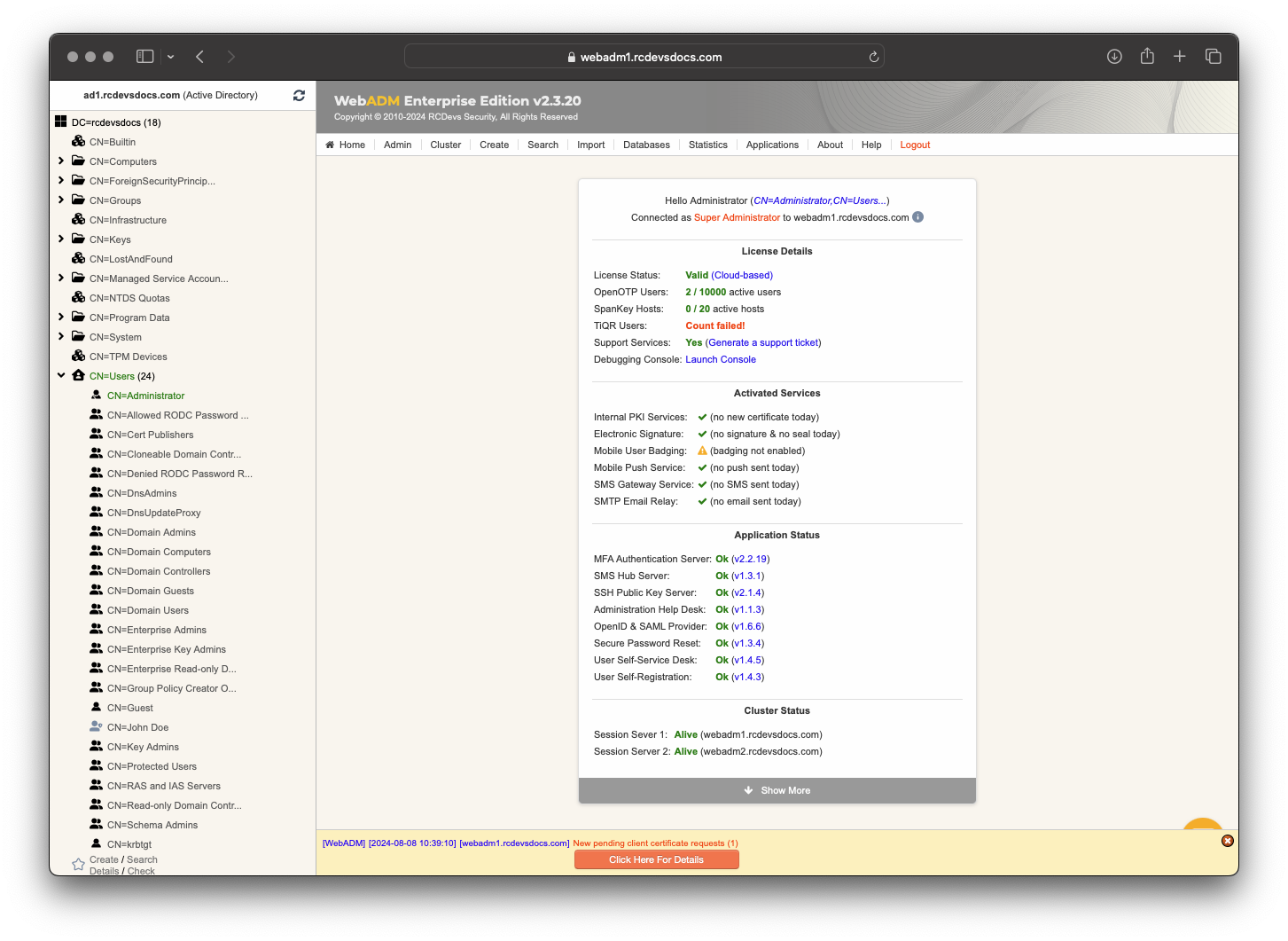
Click on the red button at the end of the home page.
On the next screen, you can show the SSL certificate request is pending:
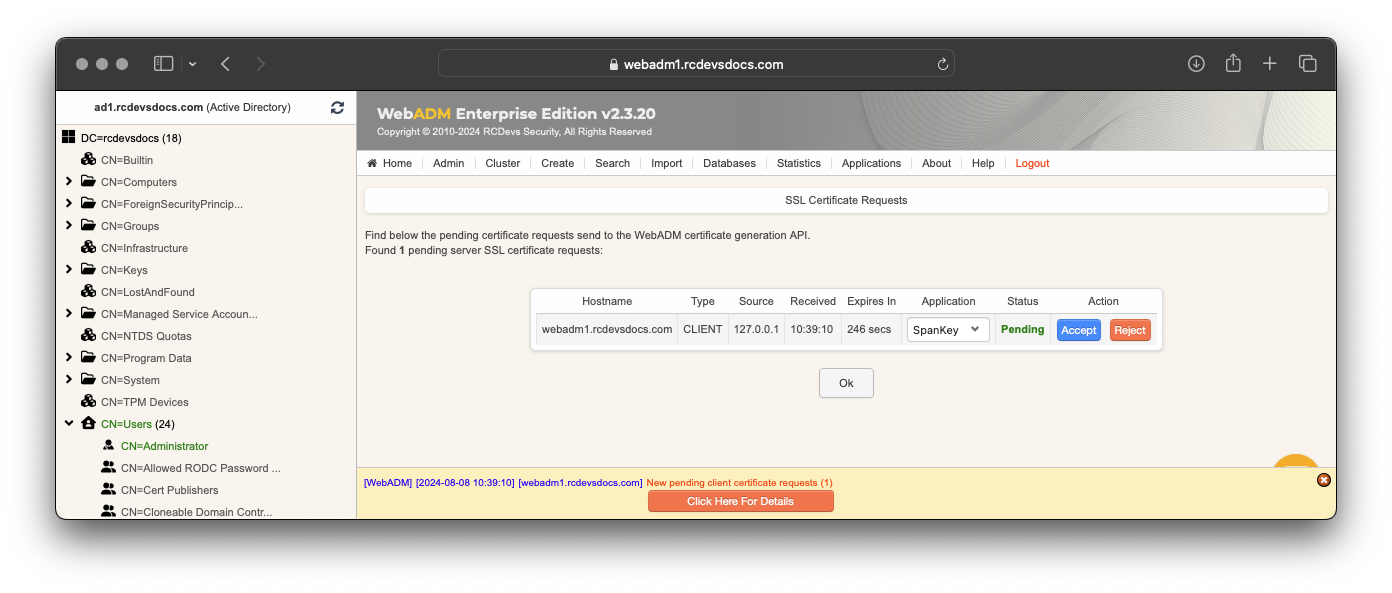
Click on the Accept button and the Spankey-client setup will continue.
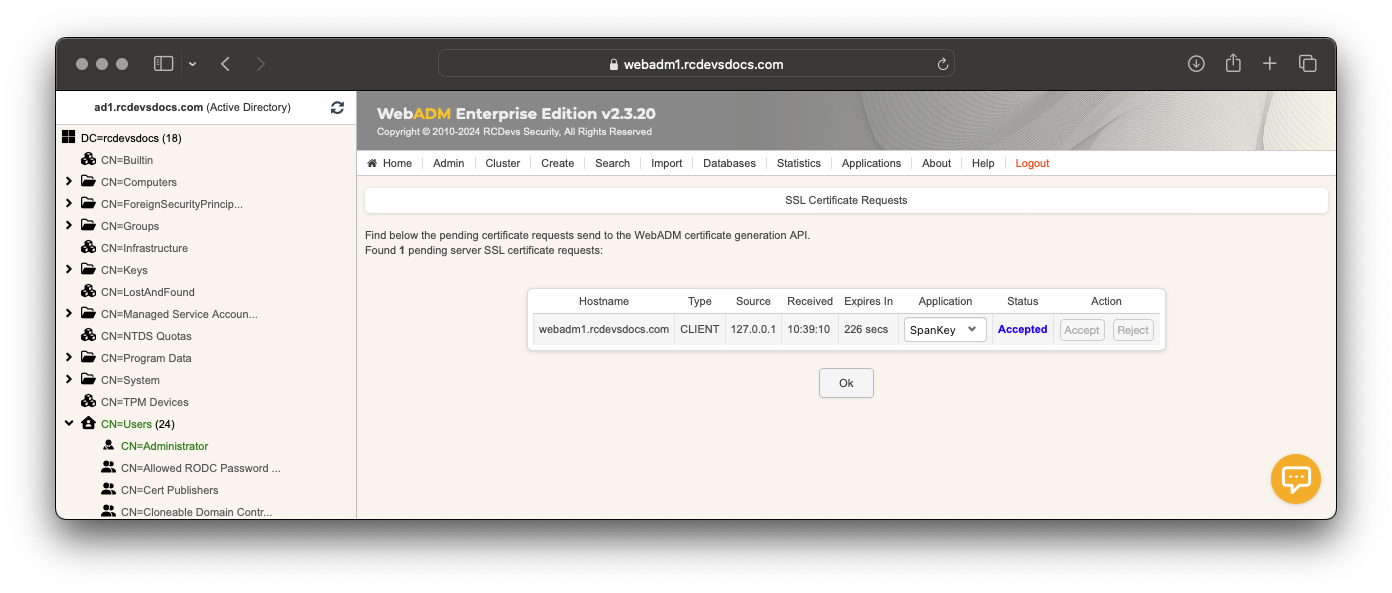
Waiting for approbation... Ok
Updating entry 'client_id' in file '/opt/spankey/conf/spankey.conf'... Ok
Updating file '/etc/ssh/sshd_config'... Ok
Updating file '/etc/nsswitch.conf'... Ok
Updating file '/etc/pam.d/common-account'... Ok
Registering SpanKey Client service...
Registering SpanKey Client service... Ok
Adding logrotate script... Ok
SpanKey Client has successfully been setup.
IMPORTANT: Do not forget to perform the following actions before you exit this session:
- Start SpanKey (/opt/spankey/bin/spankey start)
- Restart 'sshd'
- Restart 'nscd'
root@ubuntu18-client:~#
The configuration of the SpanKey client is done, you have to restart sshd, nscd and spankey-client:
root@ubuntu18-client:~# systemctl restart sshd
root@ubuntu18-client:~# systemctl restart nscd
root@ubuntu18-client:~# systemctl start spankey
SpanKey client setup is done.
SpanKey Client silent installation
Since WebADM 1.7.1, a new feature is now available for the automatic certificate approval. This setting can be useful when you massively deploy SpanKey Client. To enable this feature, log in on the WebADM Admin GUI > Admin tab > Runtime Actions > Issue Server or Client SSL Certificate > Auto Confirm Mode.
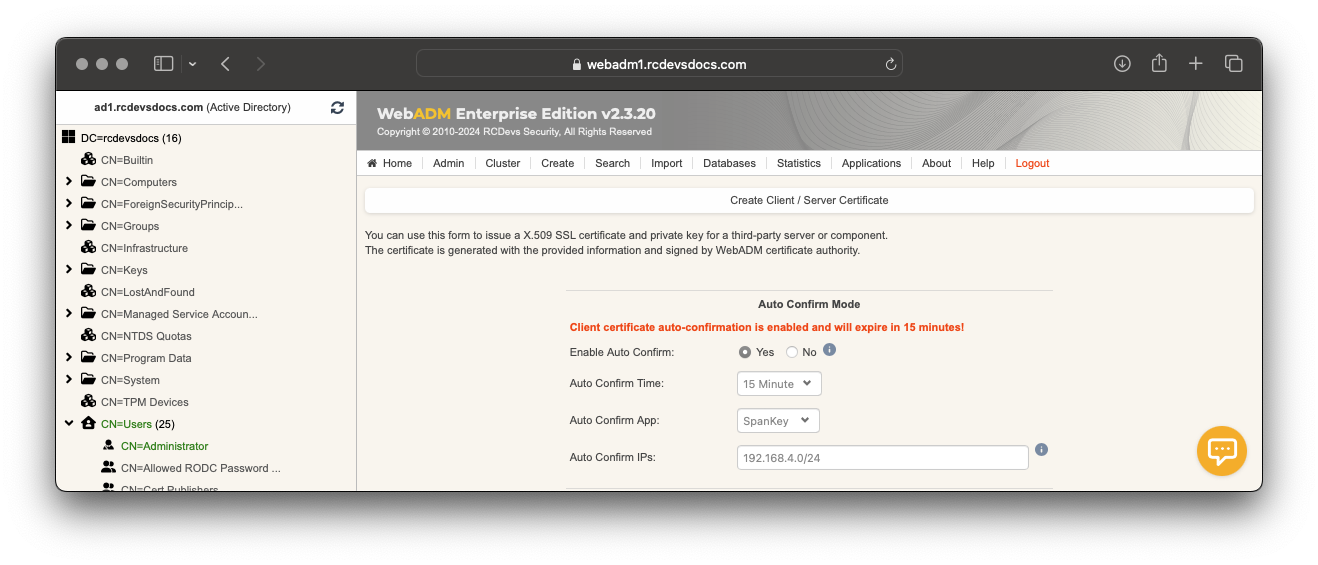
In the Auto Confirm mode, you can specify the time, application and the clients IPs where auto confirms will work. On the previous screenshot, I have configured the auto confirm valid 30 minutes for every Spankey clients coming from the network 192.168.3.0/24. To enable the auto-confirm, switch the Enable Auto Confirm button to Yes. The auto confirm is now enabled.
The SpanKey client can now be installed silently. Once the package is installed, run the following command to run the SpanKey Client setup with your parameters.
192.168.4.160is my WebADM/SpanKey server IP,my_client_idis the client_id value configured in /otp/spankey/conf/spankey.confENABLE_SSH__DEFAULT=Yis to enable SpanKey_client for OpenSSH (by default, this setting is set toNofor other scenarios)
root@ubuntu18-client:~# /opt/spankey/bin/spankey stop
Stopping SpanKey Client.... Ok
root@ubuntu18-client:~# ENABLE_SSH__DEFAULT=Y ENABLE_SUDO__DEFAULT=Y /opt/spankey/bin/setup silent 192.168.4.160 my_client_id
Primary OpenOTP service URL is: 'https://192.168.4.160:8443/spankey/'
Secondary OpenOTP service URL is: 'NONE'
Enable SpanKey Client for OpenSSH server: 'YES'
Enable SpanKey Client NSS plugin: 'YES'
Register SpanKey Client logrotate script: 'YES'
SpanKey Client must be automatically started at boot: 'YES'
Applying SpanKey Client settings from default configuration files... Ok
Retrieving WebADM CA certificate from host '192.168.4.160'... Ok
The setup needs now to request a signed 'SpanKey' client certificate.
This request should show up as pending in your WebADM interface and an administrator must accept it.
Waiting for approbation... Ok
Updating entry 'client_id' in file '/opt/spankey/conf/spankey.conf'... Ok
Updating file '/etc/ssh/sshd_config'... Ok
Updating file '/etc/nsswitch.conf'... Ok
Updating file '/etc/pam.d/common-account'... Ok
Registering SpanKey Client service...
Registering SpanKey Client service... Ok
Adding logrotate script... Ok
SpanKey Client has successfully been setup.
IMPORTANT: Do not forget to perform the following actions before you exit this session:
- Start SpanKey (/opt/spankey/bin/spankey start)
- Restart 'sshd'
- Restart 'nscd'
root@ubuntu18-client:~#
The configuration of the SpanKey client is done, you have to restart sshd, nscd and Spankey client:
root@ubuntu18-client:~# /opt/spankey/bin/spankey start;systemctl restart sshd;systemctl restart nscd
Starting SpanKey Client...
Starting daemon 'rcdevs-spankeyd'... Ok
root@ubuntu18-client:~#
Advanced Configurations
SpanKey Client
Files and Folders
SpanKey client is installed under /opt/spankey/ folder.
Find below the SpanKey client software installation file structure and important files.
-
/opt/spankey/bin/: Location for SpanKey service binaries and startup scripts.-
spankey: SpanKey executable control script for starting and stopping the service process.
To start SpanKey from the command line, issue./spankey start. To stop SpanKey, issue./spankey stop. -
setup: Initial SpanKey setup script run by the self-installer. The setup can be re-run manually at any time.
-
-
/opt/spankey/doc/: Location for spankey documentation resources. -
/opt/spankey/conf/: Location for SpanKey configuration files.spankey.conf: Main configuration file. Defines the basic SpanKey client parameters.
#-#-#-#
#
# SpanKey main configuration file.
#
#-#-#-#
#
# The entry below tells the daemon where the log file must be.
# At the very early stage (when the daemon started but did not read yet this configuration file),
# logs are sent to the standard output. Anyway, since the launcher script uses a redirection, you won't even see them.
#
log_file /opt/spankey/logs/spankeyd.log
#
# When log level is set to 'Normal', SpanKey components will log both errors and warnings only.
# 'Verbose' will make all these components just log everything.
#
log_level Normal
#
#
#-#-#-#
#-#-#-#
#
# Where to produce the SpanKey daemon's pid file.
#
#pid_file /opt/spankey/temp/spankeyd.pid
#
#
#-#-#-#
#-#-#-#
#
# A CA file is required in order to trust SpanKey servers the daemon will send requests to.
#
ca_file /opt/spankey/conf/ca.crt
#
#
#-#-#-#
#-#-#-#
#
# An optional client certificate and password spankeyd will use to communicate whith SpanKey servers
# when these are configured with 'Required Client Certificate or API Key'.
# This setting is exclusive to the 'api_key' setting.
#
client_cert_file /opt/spankey/conf/spankey.pem
#client_cert_password PaSsWoRd
#
#
#-#-#-#
#-#-#-#
#
# An optional client API key spankeyd will use to communicate whith SpanKey servers
# when these are configured with 'Required Client Certificate or API Key'.
# This setting is exclusive to the 'client_cert_file' setting.
#
#api_key ""
#
#
#-#-#-#
#-#-#-#
#
# The section below contains a list of backend servers the daemon should connect to.
# It must contain one or two target OTP server.
# Any additional server in the list will just be ignored.
#
server_urls {
url1 https://webadm1.rcdevsdocs.com:8443/spankey/
url2 https://webadm2.rcdevsdocs.com:8443/spankey/
}
#
#
# How spankeyd will relay request to the spankey backend server set.
# - "balanced" means the request will be balanced between server 1 and server 2 in a round-robin fashion.
# - "ordered" means server 2 is kept as a hot spare in case the primary server stops answering requests properly.
#
#server_policy BaLaNcEd
#
#
# When two servers are configured, spankeyd can check the server statuses
# at regular intervals by trying TCP socket connections. The status_cache is the polling interval
# between 10 and 600 seconds.
#
status_cache 30
#
#
#-#-#-#
#-#-#-#
#
# The default domain name passed to the targeted spankey backend server when the client entered a username only.
# This prevents that backend server to apply any default domain configured on its own side.
#
#default_domain_name Default
#
#
# Tells spankeyd how to extract 'domain' and 'username' from the username string entered
# in order to send them both separately to the targeted spankey backend server.
#
#domain_separator \\
#
#
#-#-#-#
#-#-#-#
#
# A comma separated list of tags from which boolean expressions attached to policies will be checked on backends.
# Further details about such boolean expressions on the servers side can be found at the following URL:
#
# https://docs.rcdevs.com/howtos/spankey/spankey/
#
#requested_tags TAG1,TAG2
#
#
#-#-#-#
#-#-#-#
#
# User settings (better configure settings in client policies).
# Fixed list of SpanKey policy settings to be passed via the SpanKey API.
#
#user_settings SpanKey.KeyExpire=10
#
#
#-#-#-#
#-#-#-#
#
# The client identifier to be sent to the targeted spankey backend server along with authentication requests.
# This allows to apply per client contextual policies on that backend server while running an authentication workflow.
#
client_id SpanKey
#
#
#-#-#-#
#-#-#-#
#
# TCP timeout for SOAP requests is by default 30.
# Just keep it as it unless you really understand all the possible consequences a change could have.
#
#soap_timeout 30
#
#
#-#-#-#
#
#
#-#-#-#
/opt/spankey/lib/: Location for SpanKey system libraries./opt/spankey/libexec/: Location for SpanKey system executables./opt/spankey/logs/: Location for log files produced by SpanKey client./opt/spankey/temp/: Location for SpanKey temporary data files. Under this directory, you will find service PID files.
SpanKey Client and Auditd
Since Spankey client v2.1.0 and SpanKey server v2.0.4-1, you can use Auditd with SpanKey. Auditd will allow you to record executed commands, SCP actions (copy, remote execution) in WebADM record database. To enable Auditd with SpanKey client, the auditd packages must be installed and running on the target machine.
If this is not installed yet, you can install it with these commands:
- for CentOS/RHEL OS:
dnf install audit - for Debian OS:
apt install auditd
If you install auditd after the installation of Spankey Client, you can copy the configuration file needed by auditd to activate audit for SpanKey Client. This file is available in /opt/spankey/lib/audisp_plugin.conf and must be copied in:
/etc/audisp/plugins.d/spankey.conffor Debian based OS./etc/audit/plugins.d/spankey.conffor CentOS/RHEL based OS.
By default, Auditd for SpanKey client is disabled. To enable it, after the Spankey client installation and configuration, edit the following file:
/etc/audisp/plugins.d/spankey.conf
# This file controls the configuration of the SpanKey Client plugin.
# It simply takes events and forwards them to the SpanKey daemon.
active = no
direction = out
path = /opt/spankey/libexec/audisp_plugin
type = always
#args =
format = string
Change the active setting from no to yes:
# This file controls the configuration of the SpanKey Client plugin.
# It simply takes events and forwards them to the SpanKey daemon.
active = yes
direction = out
path = /opt/spankey/libexec/audisp_plugin
type = always
#args =
format = string
To changes takes effect, a restart of spankey client is required. Logs are now sent to auditd and auditd forwards logs to SpanKey client daemon. The daemon will forward logs to SpanKey server.
systemctl restart spankey
Be aware, if you enable Auditd with SpanKey then all Auditd rules that have been set before on that machine will be erased. Therefore, if you are using your own Auditd rules for monitoring your machine then you can not use SpanKey with the Record Audit Logs feature.
Please refer to step Audit logs and SSH Sessions recording section of this documentation to enable auditd logs on the SpanKey server side and to know how to consult recorded logs.
SpanKey Server
Below are described some of the most relevant SSH Public Key Server configuration options.
Master Group
In SpanKey you can define master groups where the members of the group are considered as super users and can use their SSH key to access any other SpanKey account. A master group can be configured in SpanKey global configuration or in a client policy. To configure a master group, go on SpanKey global configuration or client policy and configure your Master Group.
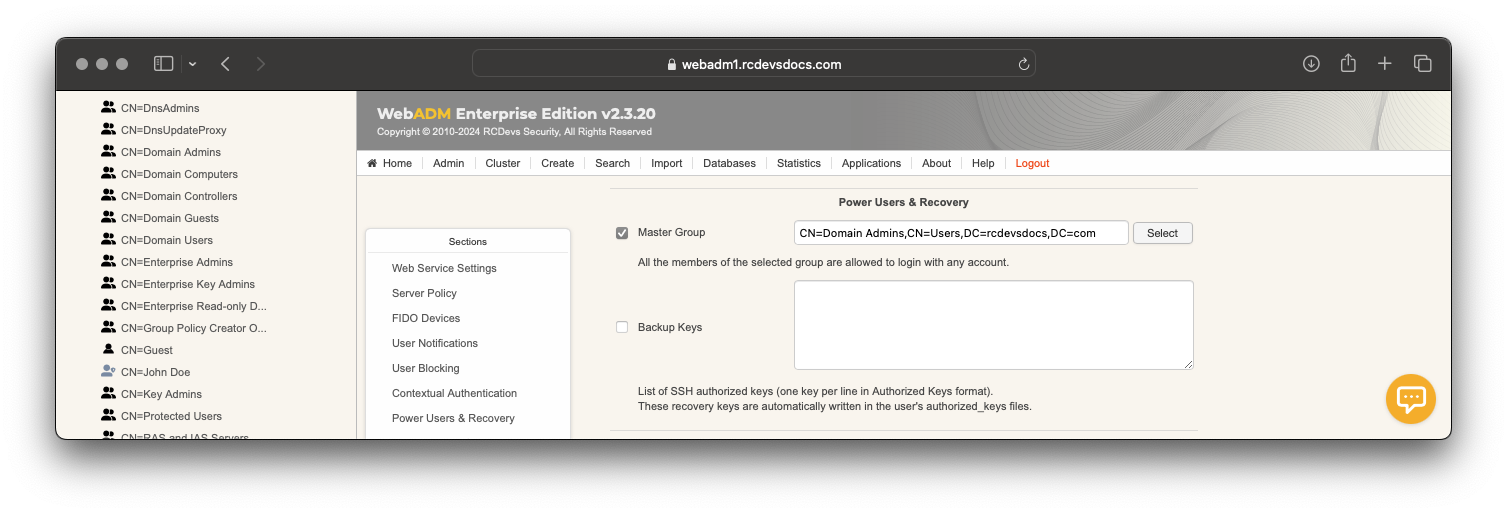
For example, my master group is CN=Administrator,CN=Users,DC=rcdevsdocs,DC=com and one member of this group is administrator account, who has a public key enrolled on his account:
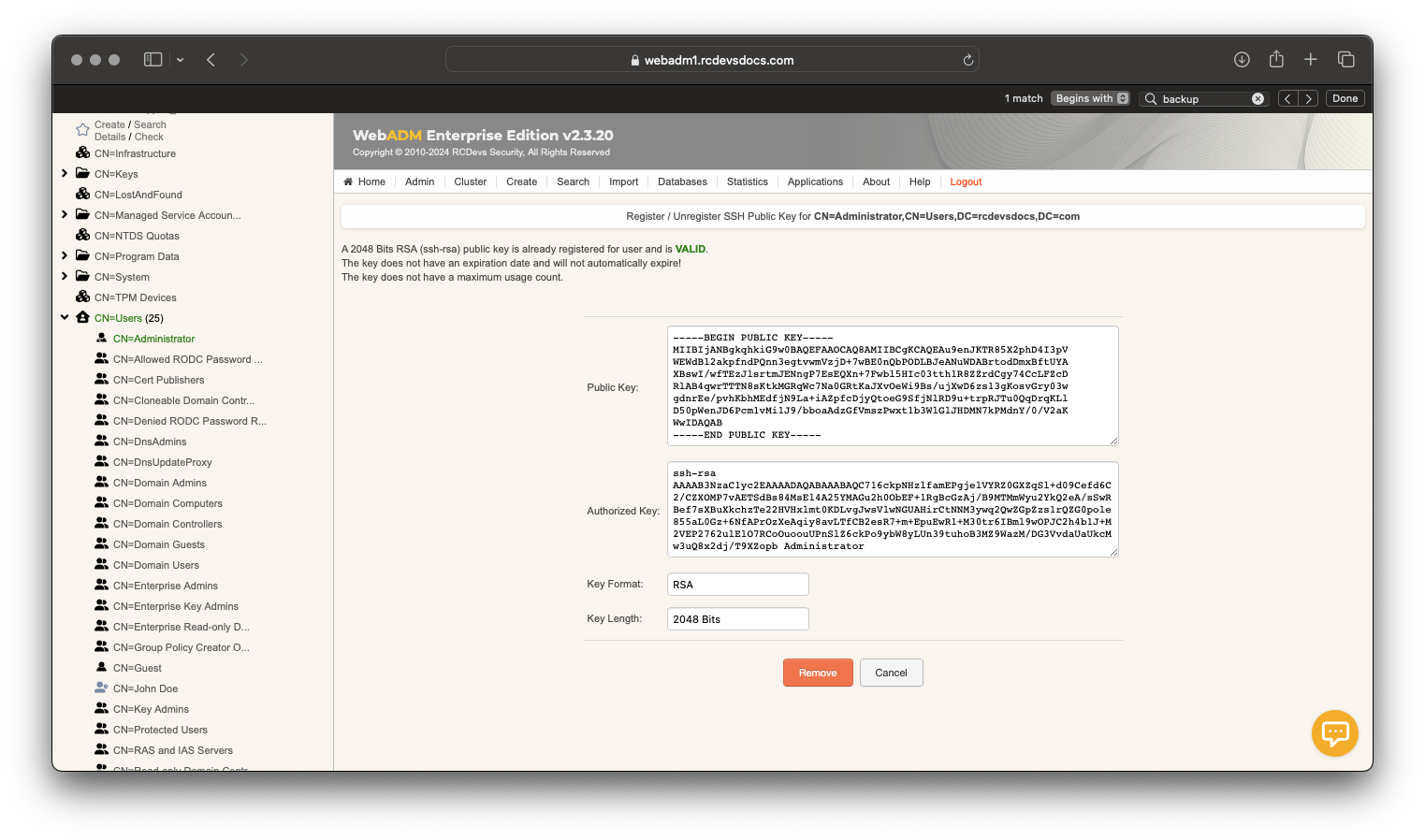
This means that the administrator account can log in to every user account using its own private key.
The administrator's public key is returned by the Spankey authorized_key command of each user account.
Below, the authorized_keys command used with Administrator account:
[root@ubuntu18-client ~]# /opt/spankey/libexec/authorized_keys administrator
environment="ONE_TIME_AUTHENTICATION_TOKEN=3D749711B6019742755496B880DDADB2",command="/opt/spankey/libexec/command_wrapper",environment="SPANKEY_USERNAME=administrator",environment="SPANKEY_DOMAIN=rcdevsdocs" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC716ckpNHzlfamEPgjelVYRZ0GXZqSl+d09Cefd6C2/CZXOMP7vAETSdBs84MsEl4A25YMAGu2h0ObEF+1RgBcGzAj/B9MTMmWyu2YkQ2eA/sSwRBef7sXBuXkchzTe22HVHxlmt0KDLvgJwsVlwNGUAHirCtNNM3ywq2QwZGpZzs1rQZG0pole855aL0Gz+6NfAPrOzXeAqiy8avLTfCB2esR7+m+EpuEwR1+M30tr6IBml9wOPJC2h4b1J+M2VEP2762ulElO7RCoOuoouUPnSlZ6ckPo9ybW8yLUn39tuhoB3MZ9WazM/DG3VvdaUaUkcMw3uQ8x2dj/T9XZopb administrator@rcdevsdocs
root@ubuntu18-client:~#
We can see 1 public keys returned for the administrator account.
Now, the authorized_keys command used with John Doe account:
root@ubuntu18-client:~# /opt/spankey/libexec/authorized_keys john.doe
environment="ONE_TIME_AUTHENTICATION_TOKEN=81777D5AED315AACC2BA263FB820D63D",command="/opt/spankey/libexec/command_wrapper",environment="SPANKEY_USERNAME=john.doe",environment="SPANKEY_DOMAIN=rcdevsdocs" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCJOJMIuocEeJfa01iJpDSeEW+06WDeh9fIl2SVnigPo3yo/XhG6+I5ZFhjr/takRk5AKRbPJdtqSPGU8BvXBRSjjDkGsZU98sVokngR9HAfcBVfP2gVEVQxi12lOmJrp5OZg66U5aZTQc7Gl9soBiDIvocW6ZJKx+W4ns1vOJj+6I8uAJjtomsaiuptA/09x3npCJWVC/ASKHNC5Vzv+TXBEgZ90T/T04jkV4AASkFZIYtn/PYfH36THf+Lelrntni8dG5NZDPBnqutwOHYbPHWGa+zn0/6M1xeqtJ+/sWhWDq//NpgBNV2xh4uKkm+IFl21BLocgLfLvCSHIDHx4f john.doe@rcdevsdocs
environment="ONE_TIME_AUTHENTICATION_TOKEN=81777D5AED315AACC2BA263FB820D63D",command="/opt/spankey/libexec/command_wrapper",environment="SPANKEY_USERNAME=Administrator",environment="SPANKEY_DOMAIN=rcdevsdocs" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC716ckpNHzlfamEPgjelVYRZ0GXZqSl+d09Cefd6C2/CZXOMP7vAETSdBs84MsEl4A25YMAGu2h0ObEF+1RgBcGzAj/B9MTMmWyu2YkQ2eA/sSwRBef7sXBuXkchzTe22HVHxlmt0KDLvgJwsVlwNGUAHirCtNNM3ywq2QwZGpZzs1rQZG0pole855aL0Gz+6NfAPrOzXeAqiy8avLTfCB2esR7+m+EpuEwR1+M30tr6IBml9wOPJC2h4b1J+M2VEP2762ulElO7RCoOuoouUPnSlZ6ckPo9ybW8yLUn39tuhoB3MZ9WazM/DG3VvdaUaUkcMw3uQ8x2dj/T9XZopb Administrator@rcdevsdocs
We can see 2 public keys returned.
Let's now try to log in on john.doe account and with the SSH key of the administrator account:
$ ssh -i administrator.pem john.doe@192.168.3.104
Welcome, SpanKey Tester!
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 5 minutes.
Session's max duration is 30 minutes.
john.doe@ubuntu18-client:~$ whoami
john.doe
john.doe@ubuntu18-client:~$ pwd
/home/johndoe
john.doe@ubuntu18-client:~$ exit
exit
>>>> Session's duration was aprox 11 seconds <<<<
Connection to 192.168.3.104 closed.
Backup/Recovery Keys
By default, the SpanKey agents will erase users’ authorized_keys file at runtime to prevent users from adding rogue public keys. If recovery keys are configured, then these keys are automatically written to the user’s authorized_keys file, for recovery purposes (to be used in the event where SpanKey client cannot communicate with the SpanKey server).
To configure a backup key, go on the WebADM Admin GUI, click on Applications tab, in Authentication category, you can find SSH Public Key Server, click on CONFIGURE button. You are now in SpanKey server configuration. Find the Power Users & Recovery section, check the box Backup Keys and put the public key to have an access on the target server even if SpanKey client or SpanKey server is down.
Put the public key in the authorized key format here:
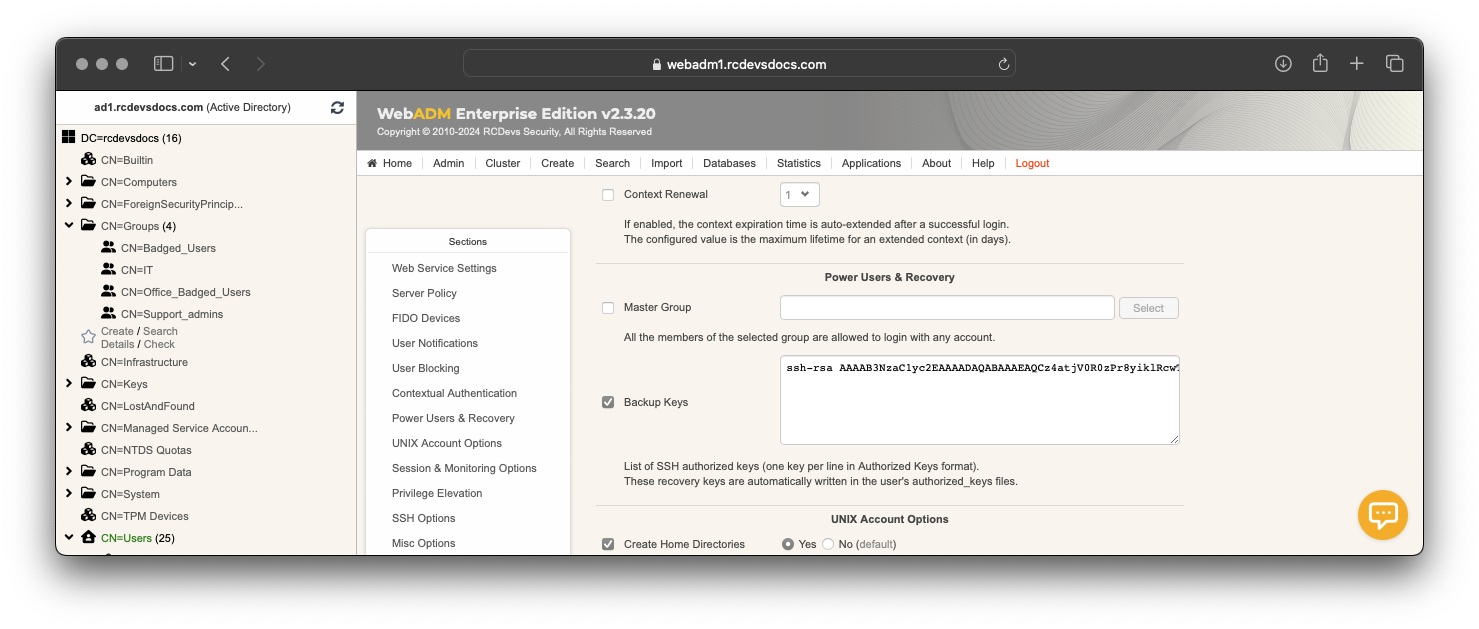
That means the private key associated with this public key will be able to log in on the target server even if SpanKey server or SpanKey client is down.
Now, we will do a test to see if the backup key is returned by the authorized key command for the john user on a SpanKey client:
root@ubuntu18-client:~# /opt/spankey/libexec/authorized_keys john.doe
environment="ONE_TIME_AUTHENTICATION_TOKEN=B3A9640B8CE1EC2768D49A75E56B9A1F",command="/opt/spankey/libexec/command_wrapper",environment="SPANKEY_USERNAME=john.doe",environment="SPANKEY_DOMAIN=rcdevsdocs" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCJOJMIuocEeJfa01iJpDSeEW+06WDeh9fIl2SVnigPo3yo/XhG6+I5ZFhjr/takRk5AKRbPJdtqSPGU8BvXBRSjjDkGsZU98sVokngR9HAfcBVfP2gVEVQxi12lOmJrp5OZg66U5aZTQc7Gl9soBiDIvocW6ZJKx+W4ns1vOJj+6I8uAJjtomsaiuptA/09x3npCJWVC/ASKHNC5Vzv+TXBEgZ90T/T04jkV4AASkFZIYtn/PYfH36THf+Lelrntni8dG5NZDPBnqutwOHYbPHWGa+zn0/6M1xeqtJ+/sWhWDq//NpgBNV2xh4uKkm+IFl21BLocgLfLvCSHIDHx4f john.doe@rcdevsdocs
environment="ONE_TIME_AUTHENTICATION_TOKEN=B3A9640B8CE1EC2768D49A75E56B9A1F",command="/opt/spankey/libexec/command_wrapper",environment="SPANKEY_USERNAME=Administrator",environment="SPANKEY_DOMAIN=rcdevsdocs" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC716ckpNHzlfamEPgjelVYRZ0GXZqSl+d09Cefd6C2/CZXOMP7vAETSdBs84MsEl4A25YMAGu2h0ObEF+1RgBcGzAj/B9MTMmWyu2YkQ2eA/sSwRBef7sXBuXkchzTe22HVHxlmt0KDLvgJwsVlwNGUAHirCtNNM3ywq2QwZGpZzs1rQZG0pole855aL0Gz+6NfAPrOzXeAqiy8avLTfCB2esR7+m+EpuEwR1+M30tr6IBml9wOPJC2h4b1J+M2VEP2762ulElO7RCoOuoouUPnSlZ6ckPo9ybW8yLUn39tuhoB3MZ9WazM/DG3VvdaUaUkcMw3uQ8x2dj/T9XZopb Administrator@rcdevsdocs
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAAEAQCz4atjV0R0zPr8yiklRcwTVRrIt0pq5jYj1cRYnHtaA4PCZA8rDNWmqCEOGZelxV25l3So5eqP1KXAQQPIGr1J/j6ujQxWu1V19jXSfx3/8fKuKJZ7ckHnbBSvt1m6a+YPyRs2eyyxtGk9L+H5LI+SotlNzsnvsFIjLzpyL2PtA627PtJUs25RG0dIaqq9rxbhqxQydX0dDg103dYR46GKKeSCKwAnnPrwQZF7oSUqlh83vn6bmkqN1KMJNpAqp8XAon6BsejmfBv7R5VoAFV5wTarVysY5nvfbbtK0OC51wxjI/aZABv78QjLV2xOHillTzDu69Y0lC6KCH8BnnmTF9iaNz64cWPRsTrwL+quRK1nPvBwh7xbwJM0TtK5Em2wi4ZhqHshSjlSY/L2S/iT2ofRXfIf/4tKTVMwwWwaU56sVFyuiRVWPSMUY0LR2V5iq6EmzpyuZpxJ8zsWOMZ7XyBCCDPvSVdBsfVL13hxBuSkrSG9pw1EYnm4STT/MCVyeF7qSVEAmfAIOu6DIMk3AQgg/e1YKmMiYNxgdhzOhpFoC1vGRQVvcBvXdxCPKhRkovghvHgNZYv3beui1JAHvk0BmKzmkBUnLqeqm5Gz0BR37Nn6uZLCmnXz13XNHFDog8KzcVRUnqDB/TiwYEeQODWyyGH8o81JzRfSEze3dKCgyZlfyDRpXJnCWGCmG00s13t6hqdT1uKHqB+gLktf8BsNHsLEnPTX+CCJ6SPbK9uy5A9301HRd1xb6cYpzKgL2CI8+gnVZBEhcVArmq5sg8vhprYQAn9qS3TBBhjDlEte1GR4zPU0Cr8R4jdaz8g0UcJtaG95SVuXb8WYm/DJSnvoIUM5tqZ9bFxIGT8CMFRgEA65kqAfAs+4oUOZblDEHgP1AGaD3FPuiIRqif2QIMH7Bva8hUH8FAxwJmVTQZtI6Xkmwd/NnmM8uxKSzRNVue+xoONZ01X8SBKKBR1hGE8nacbbpj6xvlDBmfxLhzHnTfhmNwRdUhvV+MRWjLQKsnLtlXqPqLKUwoMKsED5zSp0zO/J2fnMT1o00896/bVEivL9+LoDsyrRTxT0IDFuVZKo4j9WIY7Kv7lkD2sesr+nafvwwAszeujPoDl4w7l51zyUol/Nu4hs9XVVjMelMf9tOn2xw92ibX2baFKKbEla6Mi+u4Zj/IogkDDz+h+AcVtXlfBYlNprtytLW+bXmvsqxF1s0INjKqrx91bsFKdh5LCrAnR3JeohJL3OMQWX9DvGwkjR+Gj4SlBdaYPDn5t2CdjcO/N9VveUwbODnqbn5eDYnfRhTw2sTGBMgK0jBiaa3j2yN5QqSc+BVluiYqwvxah1CjmXvbjQBxej Backup_key
As you can see, john.doe user has his own public key returned by SpanKey server, and the Administrator key confitured in the previous section and thr recovery key previously configured in Spankey Server configuration.
Let's try a login with the backup key configured and john.doe account:
$ ssh -i backup_key.pem john.doe@192.168.3.104
Welcome, SpanKey Tester!
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 5 minutes.
Session's max duration is 30 minutes.
john.doe@ubuntu18-client:~$ whoami
john.doe
john.doe@ubuntu18-client:~$ pwd
/home/johndoe
john.doe@ubuntu18-client:~$ exit
exit
>>>> Session's duration was aprox 11 seconds <<<<
Connection to 192.168.3.104 closed.
Below are the logs from the SpanKey server side for the authorized key request:
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] New spankeyAutorizedKeys SOAP request
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] > Username: john.doe
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] > Client ID: my_client_id
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Registered spankeyAutorizedKeys request
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Resolved LDAP user: cn=john,o=Root (cached)
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Found user fullname: john
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Found 25 user settings: EnableLogin=Yes,X11Forwarding=Yes,PortForwarding=Yes,AgentForwarding=Yes,PTYAllocation=Yes,BackupKeys=[1 Items],AllowKeyFiles=No,KeyFiles=.ssh/authorized_keys,MinUID=500,MinGID=100,MailSubject=SSH Access Notification
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Found 1 user data: PublicKey
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Found 2048 bits RSA public key
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Returning 2 authorized public key
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Returning 1 backup public key
[2019-11-07 13:02:19] [192.168.3.104] [SpanKey:DDVPRKKE] Sent success response
Shared Account/Authorized Group
Authorized Groups operate on the principle of a shared account. Shared accounts are a common practice in Enterprise use of SSH. A shared account (i.e. ‘webmaster’ user) is a system account which is used concurrently by several administrators. In SpanKey you can transform any generic LDAP user into a shared SSH account simply by linking this account to a ‘shared access LDAP group’. Then all the members of that group can gain access to the shared account with their own SSH key.
For example, my shared account is webmaster and I want to allow access to webmaster account by IT group members.
Member of this group is john.doe account:
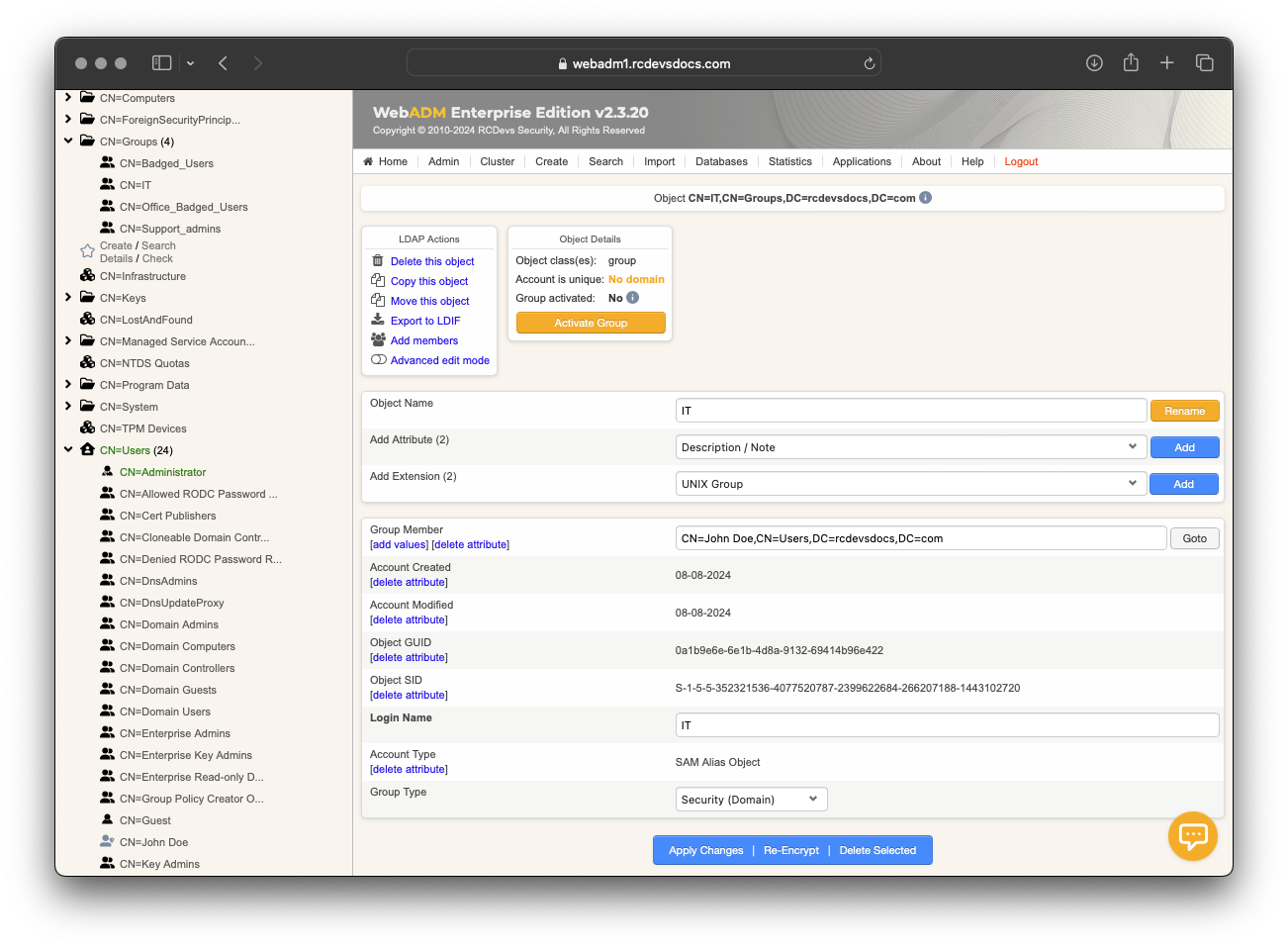
After that, I click on my webmaster account on the left tree. In Object Details box, I click on CONFIGURE button.
Choose SpanKey application and in Shared Account section, I configure my IT group like below:
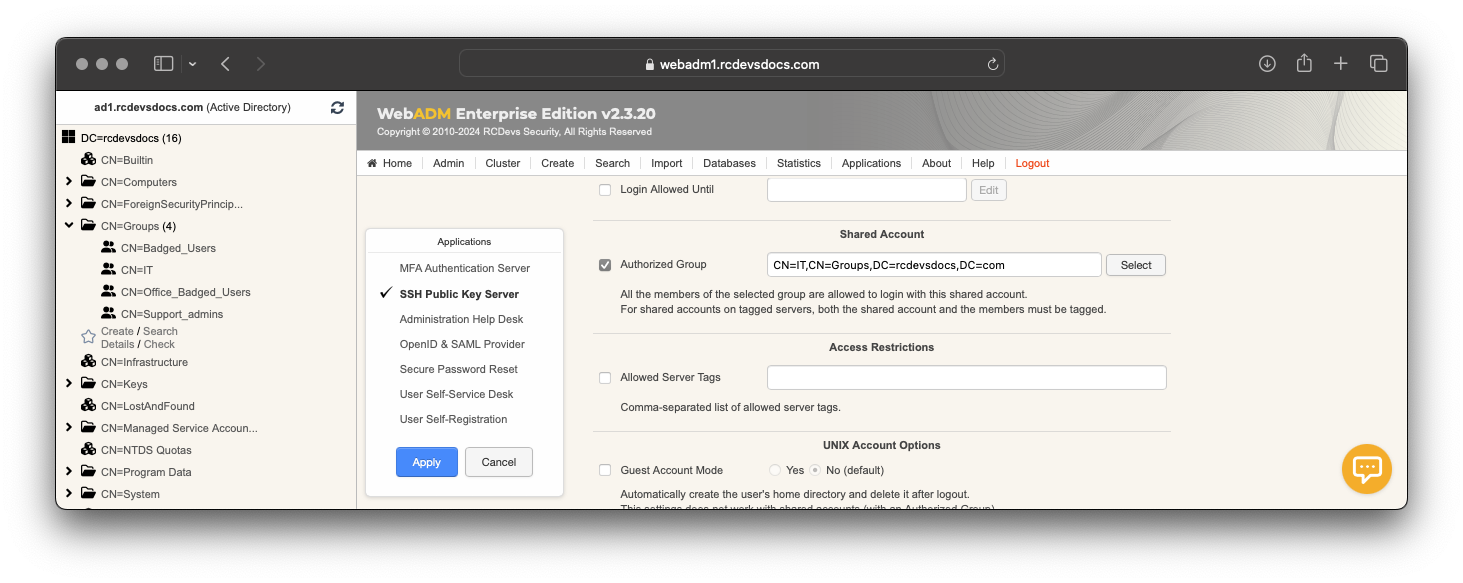
Now, I'm able to log into my SpanKey client with john private key on the shared account webmaster:
$ ssh -i johndoe.pem webmaster@192.168.3.104
Welcome, SpanKey Tester!
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 5 minutes.
Session's max duration is 30 minutes.
webmaster@ubuntu18-client:~$ whoami;pwd;exit
webmaster
/home/webmaster
exit
>>>> Session's duration was aprox 11 seconds <<<<
Connection to 192.168.3.104 closed.
$
Logs on the SpanKey server side:
New spankeyNSSInfo SOAP request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] > Database: user
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] > Name: webmaster
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] > Client ID: my_client_id
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] Registered spankeyNSSInfo request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] Found posix user 'CN=webmaster,CN=Users,DC=rcdevsdocs,DC=com'
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:VAWOC62C] Sent success response
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] New spankeyAutorizedKeys SOAP request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] > Username: webmaster
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] > Client ID: my_client_id
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Registered spankeyAutorizedKeys request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Resolved LDAP user: CN=webmaster,CN=Users,DC=rcdevsdocs,DC=com
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Found user fullname: webmaster
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Found 25 user settings: EnableLogin=Yes,X11Forwarding=Yes,PortForwarding=Yes,AgentForwarding=Yes,PTYAllocation=Yes,AllowedGroup=cn=IT,o=Root,BackupKeys=[1 Items],AllowKeyFiles=No,KeyFiles=.ssh/authorized_keys,MinUID=500,MinGID=100,MailSubject=SSH Access Notification
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Allowed group 'IT' with 2 member public keys
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Returning 2 authorized public keys
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Returning 1 backup public key
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:YFNR98A0] Sent success response
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] New spankeyNSSList SOAP request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] > Database: group
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] > Client ID: my_client_id
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] Registered spankeyNSSList request
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] Could not find any NSS group
[2019-11-07 15:15:55] [192.168.3.104] [SpanKey:P38WICLQ] Sent success response
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] New spankeySessionStart SOAP request
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Username: webmaster
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Identity: john
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Server: ubuntu18-client
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Command: /bin/bash
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Terminal: Yes
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Client ID: my_client_id
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] > Source IP: 192.168.3.233
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Registered spankeySessionStart request
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Resolved LDAP user: cn=john,o=Root
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Resolved LDAP groups: it
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Started transaction lock for user
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Found user fullname: john
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Found 21 user settings: WelcomeText=Welcome, SpanKey Tester!,MaxSessionTime=30,LockSessionTime=5,RecordSessions=Yes,RecordAuditLogs=Yes,CreateHomedir=Yes,MailSubject=SSH Access Notification,TermAuditRule=-a always,exit -S execve,FileAuditRule=-a always,exit -S all -F dir=/ -F perm=rwa,EnableLogin=Yes
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Found 1 user data: LoginCount
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Updated user data
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Started interactive terminal session of ID xPSH6AylY58fEc6S on ubuntu18-client valid for 600 seconds
[2019-11-07 15:15:56] [192.168.3.104] [SpanKey:8NJGQVC2] Sent success response
TAGs
All hosts managed by SpanKey Server can be tagged in the SpanKey client configuration.
For example, all web servers could be tagged with the acronym «WEB» in the configuration file of SpanKey client. Then you can add this Tag for all Webmaster accounts to ensure SSH access to every web server. To configure a Tag, click on a user account and in the section Object Details there is WebADM Settings. Click on the User Settings button. Go on the SpanKey application and there are the options Allowed Server Tags.
TAGs can be configured on an LDAP account or an LDAP group. To set a tag on an account or a group, go on the WebADM Admin GUI, click on your account/group, in the Object Details box, you can find WebADM settings, click on CONFIGURE. In applications box on the left, select SpanKey. You are now in SpanKey configuration for your user or your group. In Access Restriction category, check the box Allowed Server Tags and configure your TAGs. On my side, I configured web TAG for john.doe account.
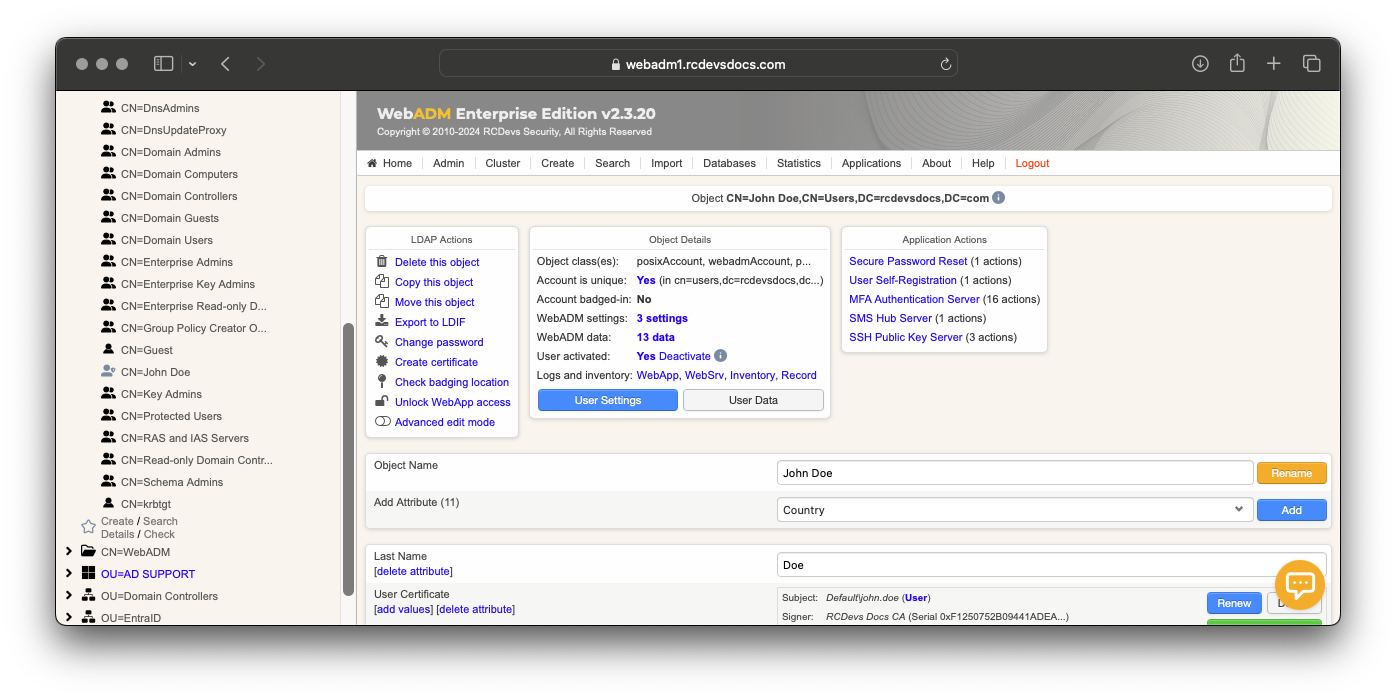
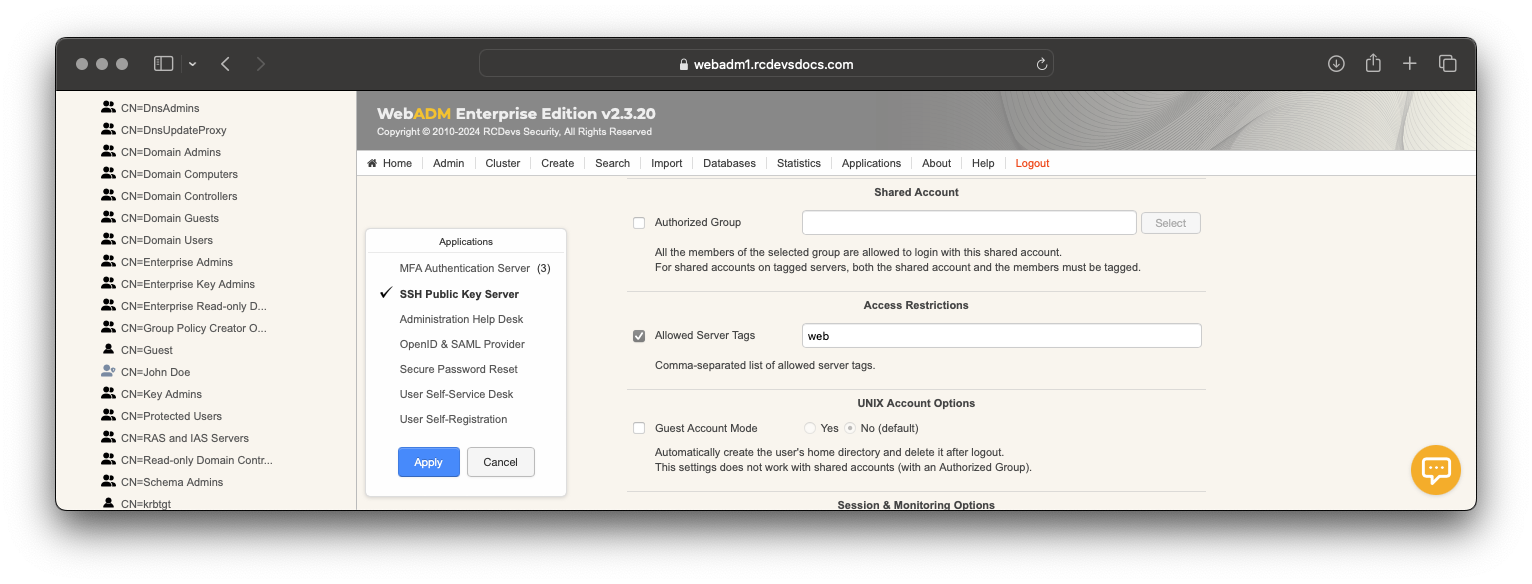
Now, I just have to TAG my servers where SpanKey client is configured. TAG should be configured in /opt/spankey/conf/spankey.conf.
root@ubuntu18-client:~# vi /opt/spankey/conf/spankey.conf
#-#-#-#
#
# spankeyd's main configuration file.
#
...
#-#-#-#
#
# A comma separated list of tags from which boolean expressions attached to policies will be checked on backends.
# Further details about such boolean expressions on the servers side can be found at the following URL:
#
# https://docs.rcdevs.com/howtos/spankey/spankey/
#
requested_tags web
#
#
#-#-#-#
...
#
#
#-#-#-#
Please, restart SpanKey Client after editing the configuration file.
root@ubuntu18-client:~# /opt/spankey/bin/spankey restart
Stopping SpanKey Client.... Ok
Starting SpanKey Client...
Starting daemon 'rcdevs-spankeyd'... Ok
root@ubuntu18-client:~#
After tagging my server, I perform a login with an account which has the same TAG configured.
$ ssh -i john.doe.pem john.doe@192.168.3.104
Welcome, SpanKey Tester!
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 5 minutes.
Session's max duration is 30 minutes.
john.doe@ubuntu18-client:~$ whoami;pwd;exit
john.doe
/home/johndoe
exit
>>>> Session's duration was aprox 6 seconds <<<<
Connection to 192.168.3.104 closed.
$
See below the result of the authentication:
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] New spankeyAutorizedKeys SOAP request
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] > Username: john.doe
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] > Tags: web
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] > Client ID: my_client_id
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Registered spankeyAutorizedKeys request
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Checking SpanKey built-in freeware license
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] License Ok (1/5 client hosts)
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Resolved LDAP groups: it
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Found user fullname: john.doe
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Found 25 user settings: EnableLogin=Yes,X11Forwarding=Yes,PortForwarding=Yes,AgentForwarding=Yes,PTYAllocation=Yes,AllowedTags=[1 Items],BackupKeys=[1 Items],AllowKeyFiles=No,KeyFiles=.ssh/authorized_keys,MinUID=500,MinGID=100,MailSubject=SSH Access Notification
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Found 1 user tags: WEB
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Found 3 user data: PublicKey,KeyExpire,KeyState
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Found 4096 bits RSA public key
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Public key expires 2020-05-30 11:00:00 (205 days)
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Public key can be used 497 more times
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Validated authorization for server tag 'WEB'
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Returning 2 authorized public key
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Returning 1 backup public key
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:NE71POJT] Sent success response
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] New spankeySessionStart SOAP request
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Username: john.doe
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Identity: john.doe
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Server: ubuntu18-client
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Command: /bin/bash
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Terminal: Yes
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Client ID: my_client_id
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] > Source IP: 192.168.3.233
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Registered spankeySessionStart request
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com (cached)
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Resolved LDAP groups: it
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Started transaction lock for user
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Found user fullname: john.doe
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Found 18 user settings: WelcomeText=Welcome, SpanKey Tester!,MaxSessionTime=30,LockSessionTime=5,RecordSessions=Yes,RecordAuditLogs=Yes,CreateHomedir=Yes,MailSubject=SSH Access Notification,TermAuditRule=-a always,exit -S execve,FileAuditRule=-a always,exit -S all -F dir=/ -F perm=rwa
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Found 2 user data: LoginCount,KeyState
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Updated user data
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Started interactive terminal session of ID auUYDYJYqkLnHnzn on ubuntu18-client valid for 600 seconds
[2019-11-07 15:26:25] [192.168.3.104] [SpanKey:7PGUMU19] Sent success response
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:I8MNHORW] New spankeySessionUpdate SOAP request
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:I8MNHORW] > Session: auUYDYJYqkLnHnzn
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:I8MNHORW] > Stop: Flagged
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:I8MNHORW] > Data: 195 Bytes
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:I8MNHORW] > Logs: 1010 Bytes
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:7PGUMU19] Found terminal session started 2019-11-07 15:26:25
[2019-11-07 15:26:35] [192.168.3.104] [SpanKey:7PGUMU19] Sent success response
It works well for the john.doe account. If you try an authentication now with the Jane Doe account, which does not have the web tag, it will fail.
$ ssh -i janedoe.pem jane.doe@192.168.3.104
See below the result of the authentication:
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] New spankeyAutorizedKeys SOAP request
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] > Username: jane.doe
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] > Tags: web
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] > Client ID: my_client_id
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Registered spankeyAutorizedKeys request
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Resolved LDAP user: CN=John Doe,CN=Users,DC=rcdevsdocs,DC=com
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Resolved LDAP groups: sql
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Found user fullname: jane
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Found 25 user settings: EnableLogin=Yes,X11Forwarding=Yes,PortForwarding=Yes,AgentForwarding=Yes,PTYAllocation=Yes,BackupKeys=[1 Items],AllowKeyFiles=No,KeyFiles=.ssh/authorized_keys,MinUID=500,MinGID=100,MailSubject=SSH Access Notification
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Found 1 user data: PublicKey
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Found 2048 bits RSA public key
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] Account is missing authorization for server tag 'WEB'
[2019-11-07 15:28:23] [192.168.3.104] [SpanKey:KC92H6FJ] No authorized public key found
[2019-11-07 15:28:24] [192.168.3.104] [SpanKey:KC92H6FJ] Sent failure response
As you can see, the authentication for Jane Doe failed failed because the account is missing an authorization for server TAG web.
Several TAGs can be requested and expressions similar to boolean expressions can be built.
Found below, how to build TAGs expressions:
Request TAG1 AND TAG2:
- TAG1,TAG2
Request TAG1 OR TAG2:
- (TAG1|TAG2)
Request TAG1 AND TAG2 OR TAG3:
- TAG1,(TAG2|TAG3)
Allow local users and local Authorized Keys File(s) usage
The SpanKey server allows you to configure local users who will be able to use the local authorized keys file(s) configured. In the SpanKey server configuration, you will find the following setting under Server Policy:
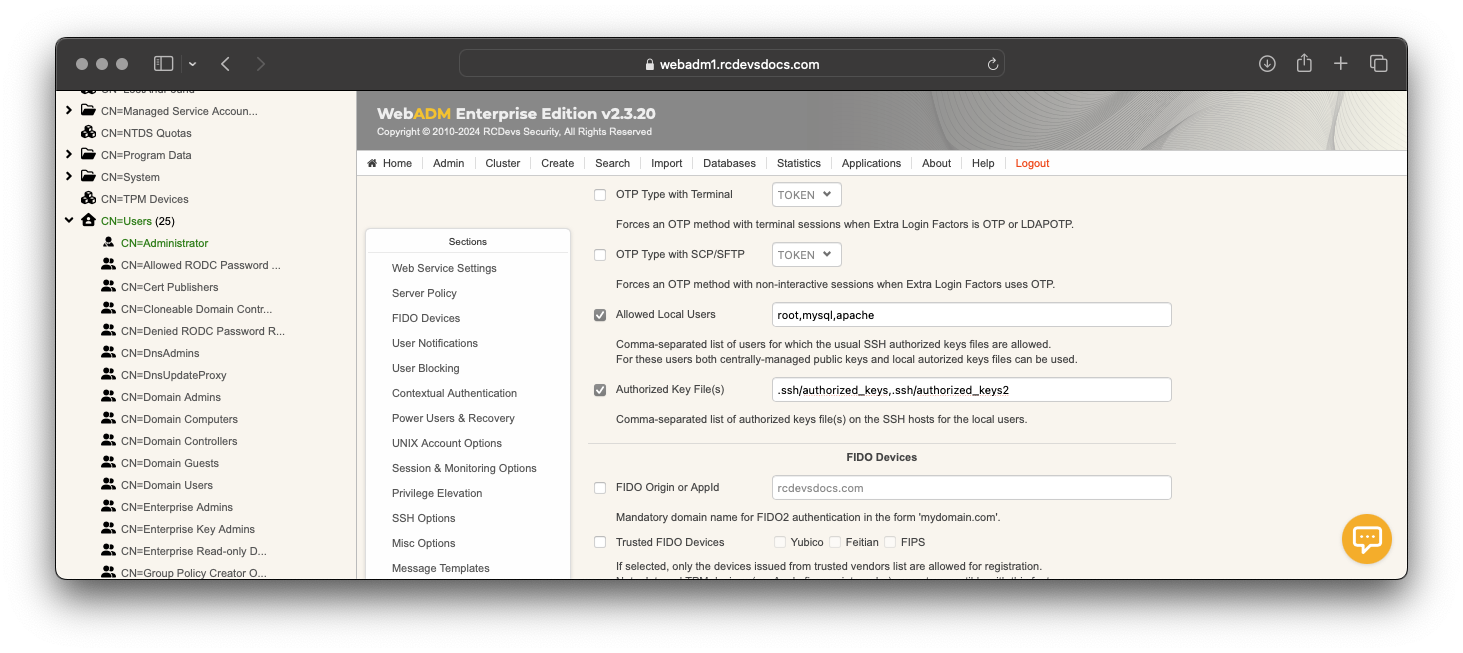
Configure your users who are able to use the local authorized keys file(s) first. After that, configure the authorized keys file(s) that your users will be able to use for local login.
Audit logs and SSH Sessions recording
For security audit, Spankey provide 2 kinds of audit logs.
The first one is the graphical session recording. All SSH sessions can be recorded and that allow you to replay every SSH sessions at any moment through the WebADM Admin interface.
The Record Session Data setting must be enabled for session recording.
Another kind of audit is the Record Audit Logs. The setting will allow you to store audit event (commands and file events) in the WebADM Record databases.
These 2 settings can be enabled under SpanKey Server configuration:
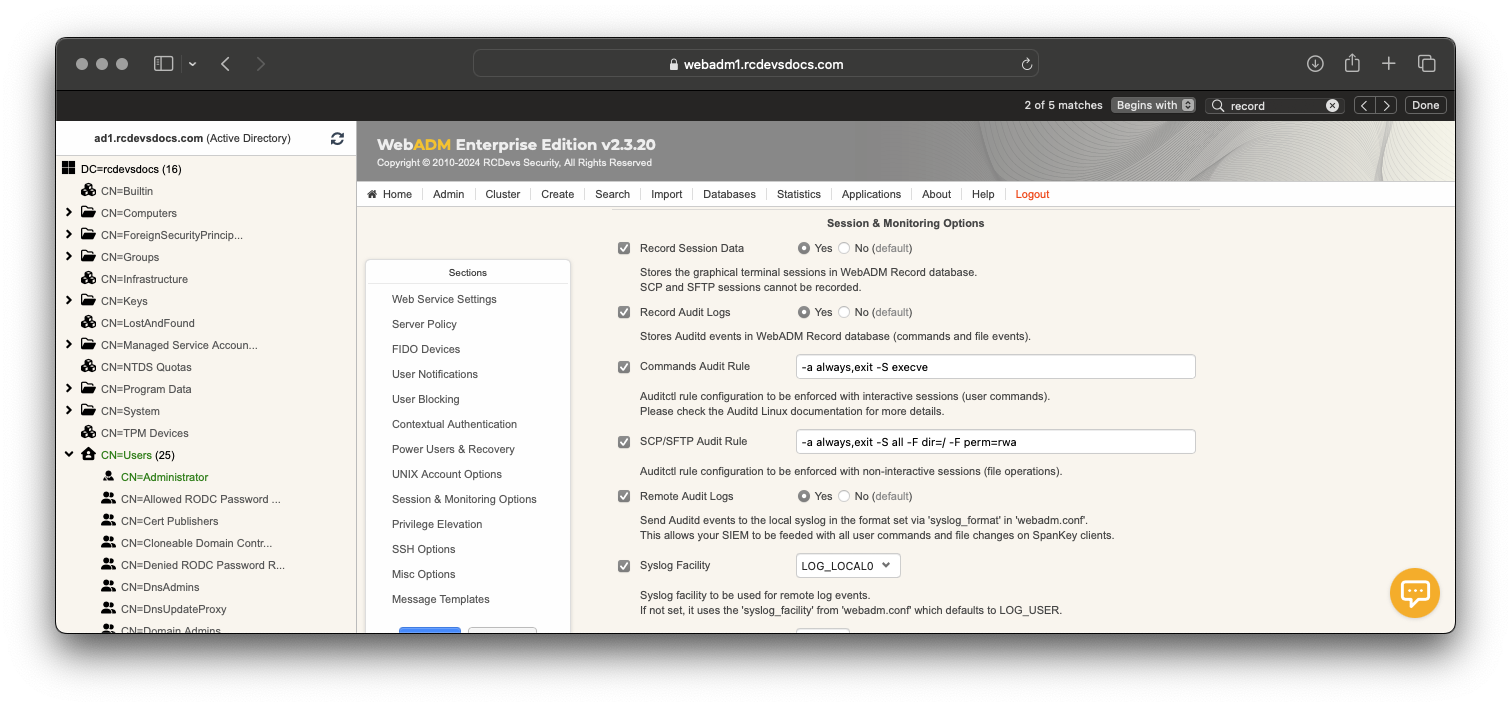
Recorded sessions and audit logs can be replayed under WebADM Administrator Portal > Databases > Recorded Sessions & Transactions
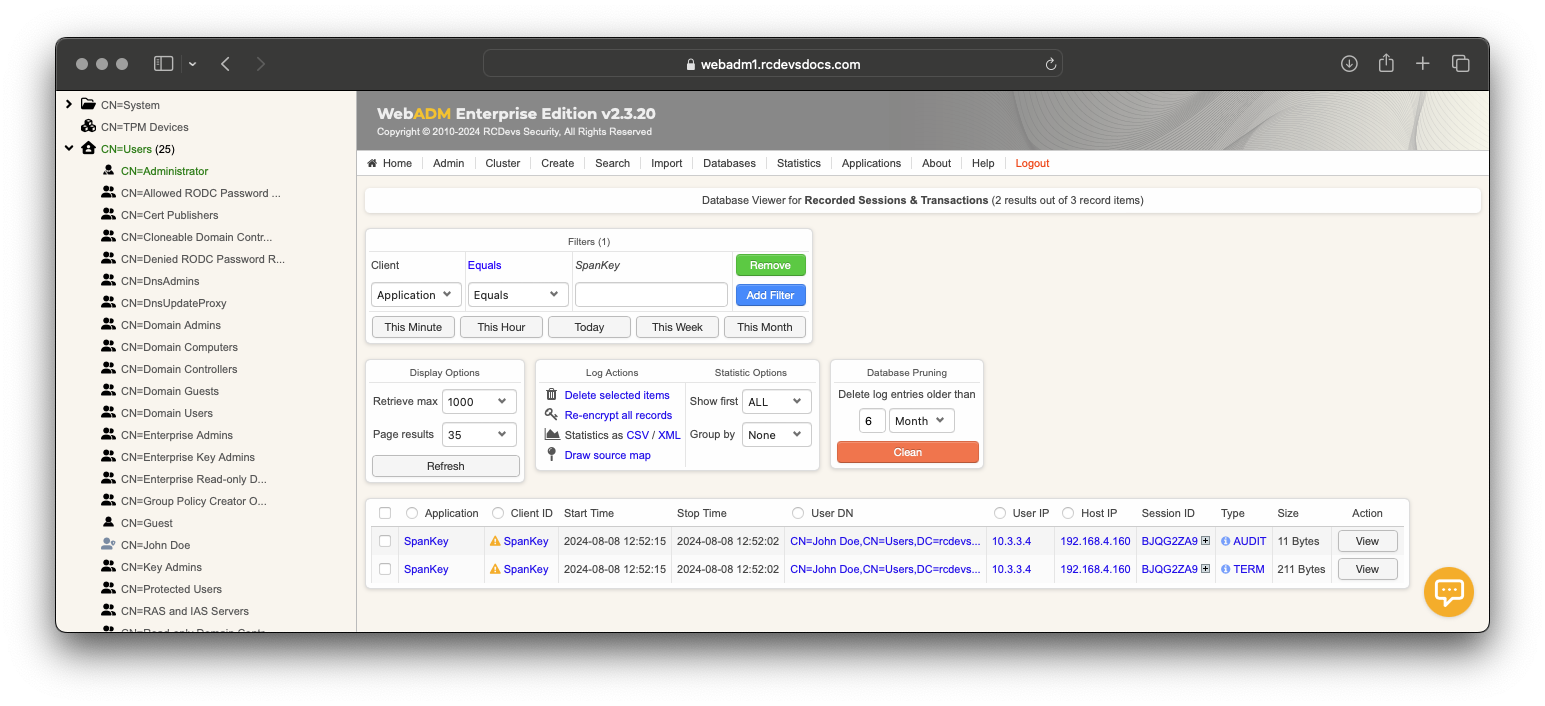
Under the Recorded Sessions databases, 2 types of record are available:
TERM: This is a graphical session recordAUDIT: This is the command and file events record
Click on view button to see the recorded sessions/logs
Other information like client, Session duration, User DN, User IP, Host IP and Session ID are also useful here.
This is an example of auditd logs available through WebADM Admin GUI under databases > Recorded Sessions. Click on View button on an AUDIT log type to consult auditd logs:
[2019-11-07 15:26:25] [3385] Executed command '/bin/bash' (pid 82610) in '/home/john.doe' as 500:100
[2019-11-07 15:26:25] [3385] > Event 'execve' returned success with code 0
[2019-11-07 15:26:25] [3386] Executed command 'groups' (pid 82618) in '/home/john.doe' as 500:100
[2019-11-07 15:26:25] [3386] > Event 'execve' returned success with code 0
[2019-11-07 15:26:25] [3387] Executed command '/bin/sh /usr/bin/lesspipe' (pid 82620) in '/home/johndoe' as 500:100
[2019-11-07 15:26:25] [3387] > Event 'execve' returned success with code 0
[2019-11-07 15:26:25] [3388] Executed command 'basename /usr/bin/lesspipe' (pid 82621) in '/home/johndoe' as 500:100
[2019-11-07 15:26:25] [3388] > Event 'execve' returned success with code 0
[2019-11-07 15:26:25] [3389] Executed command 'dirname /usr/bin/lesspipe' (pid 82623) in '/home/johndoe' as 500:100
[2019-11-07 15:26:25] [3389] > Event 'execve' returned success with code 0
[2019-11-07 15:26:25] [3390] Executed command 'dircolors -b' (pid 82625) in '/home/johndoe' as 500:100
[2019-11-07 15:26:25] [3390] > Event 'execve' returned success with code 0
[2019-11-07 15:26:32] [3391] Executed command 'whoami' (pid 82628) in '/home/john.doe' as 500:100
[2019-11-07 15:26:32] [3391] > Event 'execve' returned success with code 0
Sudoers Policy Plugin
Since SpanKey Client for Linux v2.2.0 and SpanKey Server v2.0.5-1, you can use sudo commands with SpanKey. Sudo rules can be defined at various levels in WebADM, following the framework's policy concepts of inheritance and overriding:
-
Level/Weight 1: SpanKey Server Configuration. When defined at this level, the sudo rules are inherited by all SpanKey clients.
-
Level/Weight 2: Group Settings. When defined here, sudo rules are inherited by all members of the group. Additionally, rules can be set to apply to a specific client policy that matches a SpanKey client.
-
Level/Weight 3: User Settings. When defined here, sudo rules apply only to the individual user. Additionally, rules can be set to a specific client policy matching a SpanKey client.
-
Level/Weight 4: Client Policy. When defined here, sudo rules apply to all users logging in with SpanKey, where the SpanKey client matches the specified client policy.
Once you authenticated with Spankey, you can run the sudo -V command to check if SpanKey sudoers policy plugin has been successfully loaded:
$ ssh -i centos7 centos7@192.168.3.120
Welcome to SpanKey SSH Server.
This is a demonstration by RCDEVS SA.
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 10 minutes.
Session's max duration is 30 minutes.
[centos7@centos7-client ~]$ sudo -V
Sudo version 1.8.23
SpanKey sudoers policy plugin version 2.3.0
Copyright 2010-2019 RCDevs SA, All rights reserved.
Sudoers file grammar version 46
Sudoers I/O plugin version 2.3.0
[centos7@centos7-client ~]$ exit
exit
>>>> Session's duration was aprox 6 seconds <<<<
Connection to 192.168.3.120 closed.
$
In the below example, the sudo rules are defined on a specific group for all Spankey clients.
In WebADM GUI> <USER_GROUP> > Object Details > Group Settings > SSH Public Key Server > Privilege Elevation, click on the checkbox then click Edit:
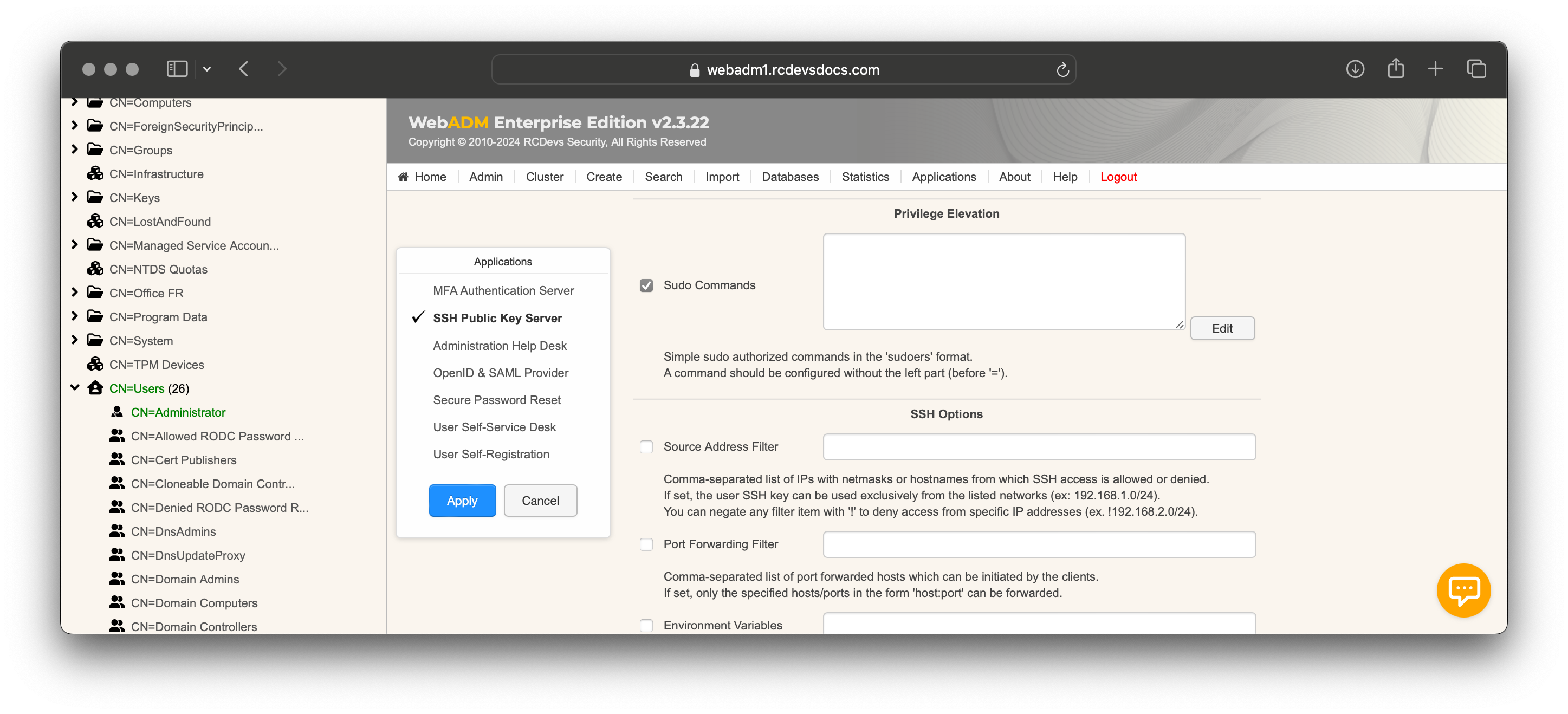
Define the desired sudo rules as needed:
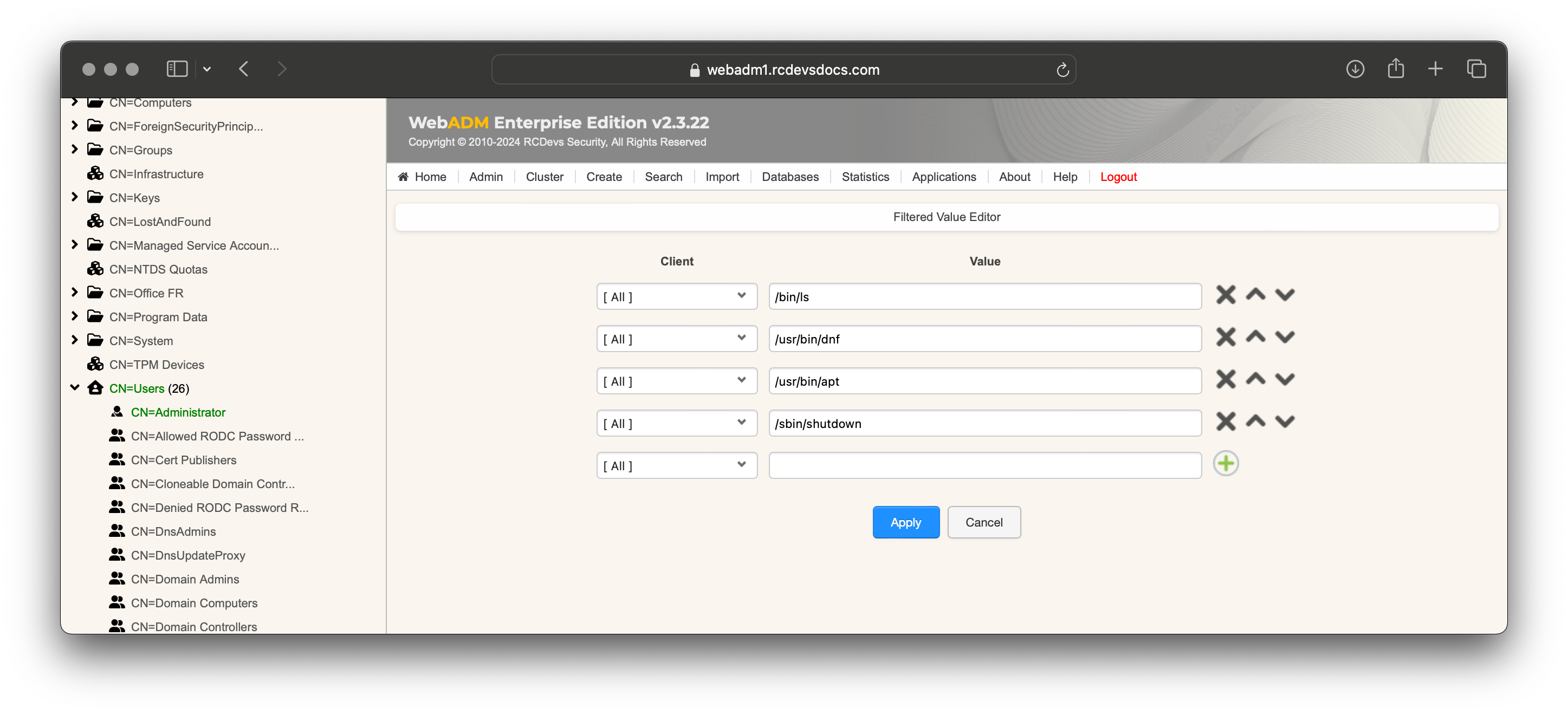
In the Client column, you can set the sudo rule for each Spankey client if you have defined a specific client policy for the client system. In this example, we haven't assigned rules to an individual client system, so the rules will apply to all Spankey clients for all members within that group.
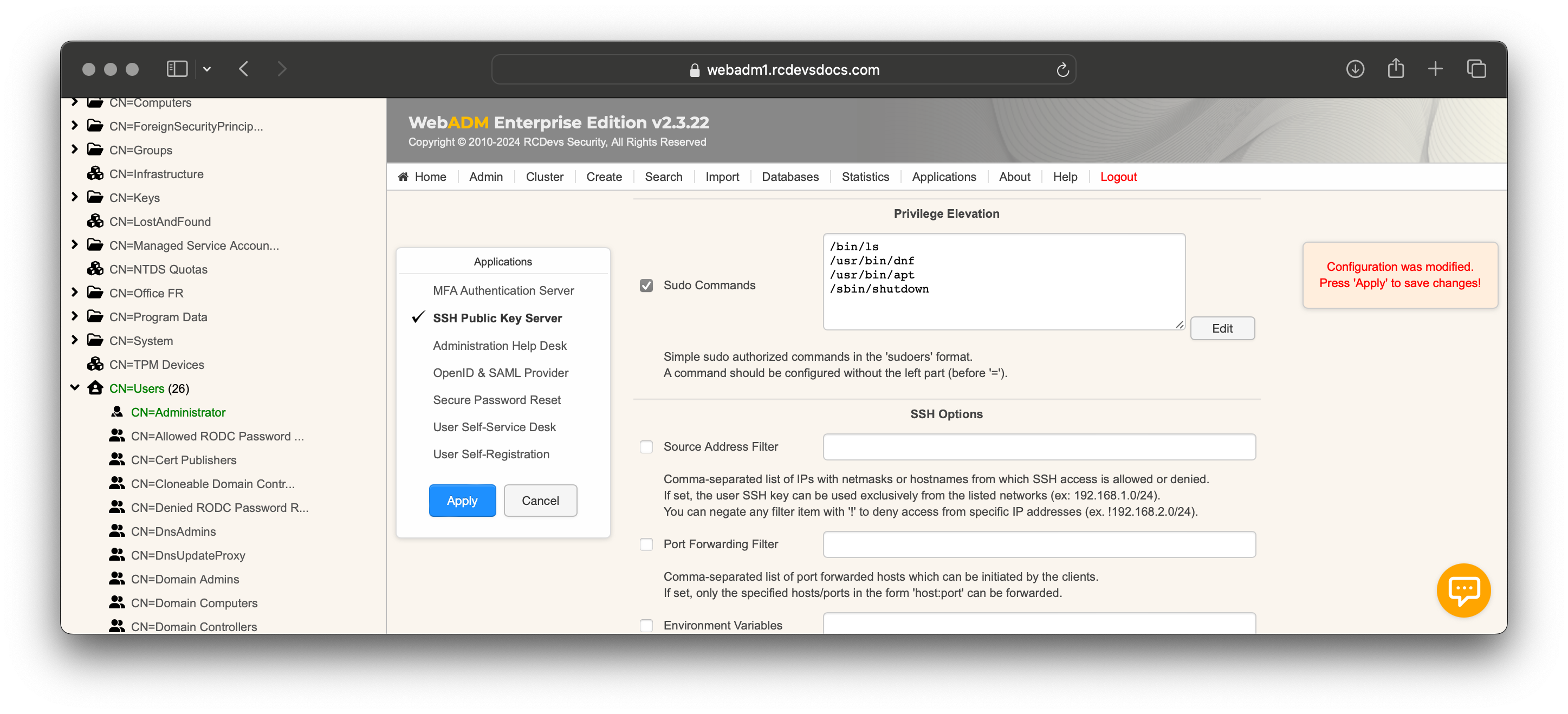
Click Apply to save your configuration. You can then perform an SSH login to verify that the rules have been applied correctly. Note that it may take a few minutes for WebADM to refresh its cache and distribute updates to the clients.
Once authenticated with Spankey, you can run the following command sudo -l to check the rights and the set of rules:
$ ssh -i centos7 centos7@192.168.3.120
Welcome to SpanKey SSH Server.
This is a demonstration by RCDEVS SA.
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 10 minutes.
Session's max duration is 30 minutes.
[centos7@centos7-client ~]$ sudo -l
User centos7 may run the following commands on centos7-client:
(ALL) /bin/ls
(ALL) /usr/bin/dnf
(ALL) /usr/bin/apt
(ALL) /sbin/reboot
(ALL) /sbin/shutdown
[centos7@centos7-client ~]$ exit
exit
>>>> Session's duration was aprox 14 seconds <<<<
Connection to 192.168.3.120 closed.
As we can see, the sudo rules are returned as expected.
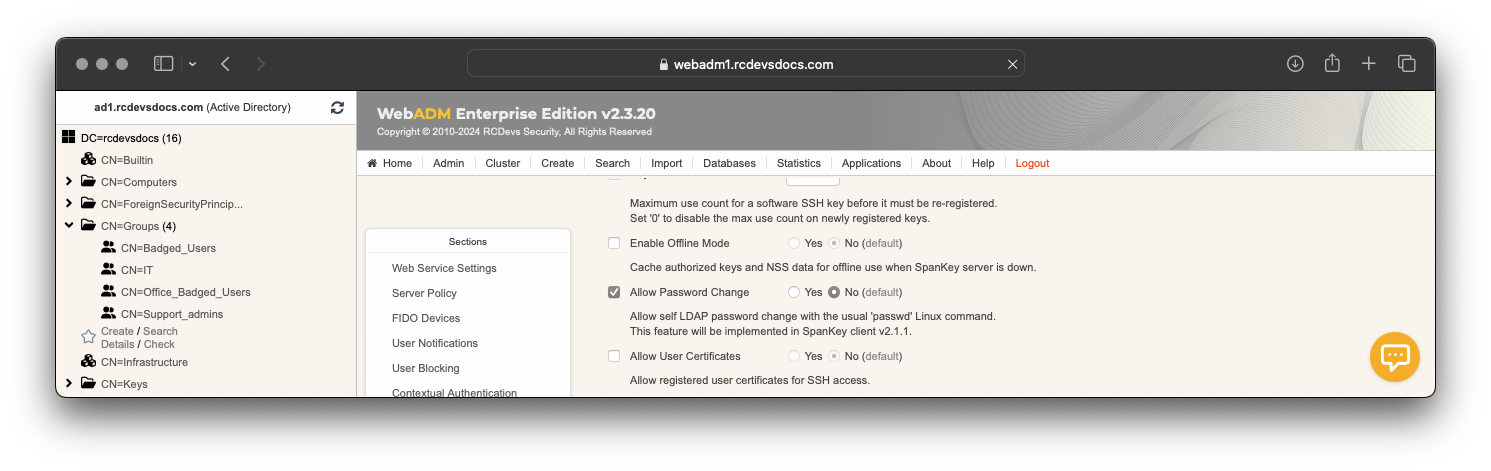
Change Password Remotely
In a Spankey installation, Users can now change their LDAP account password with the passwd command when the option is enabled in Spankey Server configuration. The setting is named Allow Password Change and must be set to Yes to benefit that feature from Spankey Clients :
ubuntu20.04:~$ passwd
Changing password for john.doe
Old password:*******
New password: ***********
Retype new password: ***********
passwd: Password changed.
The new password provided must meet the LDAP password policies. No other password policies are applied.
OpenSSH
The SpanKey client setup script asks us during the setup if we want to enable SpanKey for OpenSSH and we reply Yes to this question.
This action involves changing /etc/ssh/sshd_config configuration file. The script edit the following parameters:
AuthorizedKeysCommand /opt/spankey/libexec/authorized_keys
AuthorizedKeysCommandUser root
PermitUserEnvironment yes
UsePAM yes
Depending on the SSHd version, you might need to use AuthorizedKeysCommandRunAs instead of AuthorizedKeysCommandUser.
Restart SSHd if you change the configuration.
service sshd restart
NSS Provider
RHEL & CentOS
The SpanKey client setup script asks us during the setup if we want to enable SpanKey for NSCD and we reply Yes to this question.
This action involves changing /etc/nsswitch.conf configuration file.
The script edit the following parameters:
passwd: files spankey nscd
shadow: file nscd
group: files spankey nscd
Restart NSCD to apply the configuration:
service nscd restart
Debian & Ubuntu
The SpanKey client setup script asks us during the setup if we want to enable SpanKey for NSCD and we reply Yes to this question.
This action involves changing /etc/nsswitch.conf configuration file.
The script edits the following parameters:
passwd: compat spankey
shadow: compat
group: compat spankey
getent passwd/group tests
To check if your LDAP users are well returned on your spankey_client, you can use the following command:
getent passwd
This command should return all LDAP accounts allowed for this host. An LDAP account can be returned only if the account is extended to UNIX. Please refer to step Users/Groups Management section to know how to activate/extend an LDAP account for SpanKey usage.
[root@webadm1 temp]# getent passwd
#### The following accounts are local accounts
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:65534:65534:Kernel Overflow User:/:/sbin/nologin
systemd-coredump:x:999:997:systemd Core Dumper:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:998:996:User for polkitd:/:/sbin/nologin
tss:x:59:59:Account used for TPM access:/dev/null:/sbin/nologin
sssd:x:997:994:User for sssd:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/usr/share/empty.sshd:/sbin/nologin
chrony:x:996:993::/var/lib/chrony:/sbin/nologin
systemd-oom:x:991:991:systemd Userspace OOM Killer:/:/usr/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/sbin/nologin
#### The following accounts are LDAP accounts
administrator:x:501:100::/home/administrator:/bin/bash
john.doe:x:500:100:John Doe:/home/johndoe:/bin/bash
jane.doe:x:502:100: Jane Doe:/home/janedoe:/bin/bash
webmaster:x:503:100::/home/webmaster:/bin/bash
getent passwd command may take few seconds to yield results.
After the getent passwd command, you should have the following result in /opt/webadm/logs/webadm.log (server side) if the command has worked successfully:
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] New spankeyNSSList SOAP request
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] > Database: user
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] > Client ID: my_client_id
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] Registered spankeyNSSList request
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] Found 4 posix users
[2018-05-22 17:11:25] [192.168.3.104] [SpanKey:AFA5ES1I] Sent success response
To check if your LDAP groups are well returned on your spankey client machine, you can use the following command:
getent group
Note that only activated LDAP groups will be returned with this command. Please refer to step 5.0 Users/Groups Management to know how to activate/extend an LDAP group for SpanKey usage.
[root@webadm1 tmp]# getent group
#### The following groups are local groups
root:x:0:
bin:x:1:
daemon:x:2:
sys:x:3:
adm:x:4:
tty:x:5:
disk:x:6:
lp:x:7:
mem:x:8:
kmem:x:9:
wheel:x:10:
cdrom:x:11:
mail:x:12:postfix
man:x:15:
dialout:x:18:webadm
floppy:x:19:
games:x:20:
tape:x:30:
video:x:39:
ftp:x:50:
lock:x:54:
audio:x:63:
nobody:x:99:
users:x:100:
avahi-autoipd:x:170:
utmp:x:22:
utempter:x:35:
ssh_keys:x:999:
input:x:998:
systemd-journal:x:190:
systemd-bus-proxy:x:997:
systemd-network:x:996:
dbus:x:81:
polkitd:x:995:
dip:x:40:
tss:x:59:
postdrop:x:90:
postfix:x:89:
chrony:x:994:
sshd:x:74:
mysql:x:993:
webadm:x:1000:
ldap:x:55:
slocate:x:21:
nscd:x:28:
tcpdump:x:72:
cgred:x:992:
docker:x:991:
radiusd:x:990:
toto:x:1003:
apache:x:48:
stapusr:x:156:
stapsys:x:157:
stapdev:x:158:
#### The following groups are LDAP groups
domain admins:x:103:administrator
enterprise admins:x:100:administrator,john.doe,webmaster
it:x:101:john.doe
support_admins:x:102:
After the getent group command, you should have the following result in /opt/webadm/logs/webadm.log (server side) if the command has worked successfully:
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] New spankeyNSSList SOAP request
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] > Database: group
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] > Client ID: SpanKey
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] Registered spankeyNSSList request
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] Found 4 NSS groups
[2024-08-08 13:07:01] [192.168.4.160:47268] [SpanKey:CXF63CUA] Sent success response
Name Service Cache Daemon (NSCD)
In Linux, user and group information is often cached by NSCD (Name Service Cache Daemon). This can result in failed SpanKey login right after the installation or after creating a new user since the user is not available in the cache yet.
To resolve this issue, you can wait for the cache to be refreshed on its own, or flush the NSCD cache on your server.
To clear NSCD cache files, invalidate the passwd and group cache:
[root@centos8-client ~]# nscd --invalidate=passwd
[root@centos8-client ~]# nscd --invalidate=group
Be aware, there are limitations on cache timeouts with how NSCD works with nss_ldap and nss-pam-ldapd. This can result in failed SpanKey login.
To resolve this issue, activate the paranoia and set the restart-interval in the following NSCD configuration file /etc/nscd.conf.
Verify that the nsswitch configuration file has been modified by adding spankey.
[root@centos8 ~]# cat /etc/nsswitch.conf
# Generated by authselect on Thu Apr 8 15:07:44 2021
# Do not modify this file manually.
# If you want to make changes to nsswitch.conf please modify
# /etc/authselect/user-nsswitch.conf and run 'authselect apply-changes'.
#
# Note that your changes may not be applied as they may be
# overwritten by selected profile. Maps set in the authselect
# profile takes always precedence and overwrites the same maps
# set in the user file. Only maps that are not set by the profile
# are applied from the user file.
#
# For example, if the profile sets:
# passwd: sss files
# and /etc/authselect/user-nsswitch.conf contains:
# passwd: files
# hosts: files dns
# the resulting generated nsswitch.conf will be:
# passwd: sss files # from profile
# hosts: files dns # from user file
passwd: sss spankey files systemd
group: sss spankey files systemd
netgroup: sss files
automount: sss files
services: sss files
# Included from /etc/authselect/user-nsswitch.conf
#
# /etc/nsswitch.conf
#
# An example Name Service Switch config file. This file should be
# sorted with the most-used services at the beginning.
#
# The entry '[NOTFOUND=return]' means that the search for an
# entry should stop if the search in the previous entry turned
# up nothing. Note that if the search failed due to some other reason
# (like no NIS server responding) then the search continues with the
# next entry.
#
# Valid entries include:
#
# nisplus Use NIS+ (NIS version 3)
# nis Use NIS (NIS version 2), also called YP
# dns Use DNS (Domain Name Service)
# files Use the local files in /etc
# db Use the pre-processed /var/db files
# compat Use /etc files plus *_compat pseudo-databases
# hesiod Use Hesiod (DNS) for user lookups
# sss Use sssd (System Security Services Daemon)
# [NOTFOUND=return] Stop searching if not found so far
#
# 'sssd' performs its own 'files'-based caching, so it should
# generally come before 'files'.
# To use 'db', install the nss_db package, and put the 'db' in front
# of 'files' for entries you want to be looked up first in the
# databases, like this:
#
# passwd: db files
# shadow: db files
# group: db files
shadow: files sss
hosts: files dns myhostname
bootparams: files
ethers: files
netmasks: files
networks: files
protocols: files
rpc: files
publickey: files
aliases: files
Users/Groups Management
Users Management (Activation)
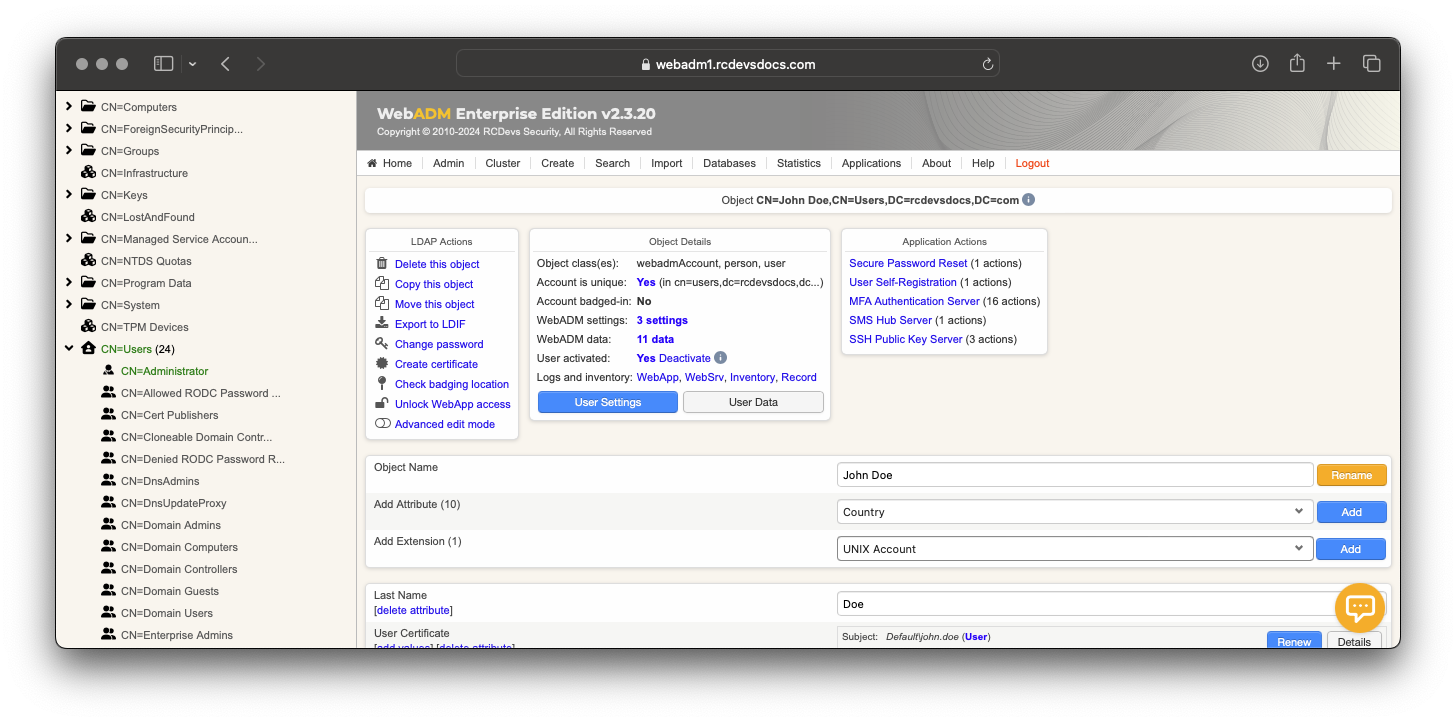
To enable your LDAP users to be propagated as Linux accounts, and to work with the SpanKey, they must be extended with “Unix Account” object class. This is done in the WebADM graphical interface (can be done as a batch jobs as well) as follows:
- Choose LDAP account that you like to extend.
- Make sure the account is a WebADM account. If not, you must first extend the account with WebADM object class.
- Choose WebADM Account in Add Selector. Click
Add. - Choose UNIX Account in the Add Extension selector. Click
Add.
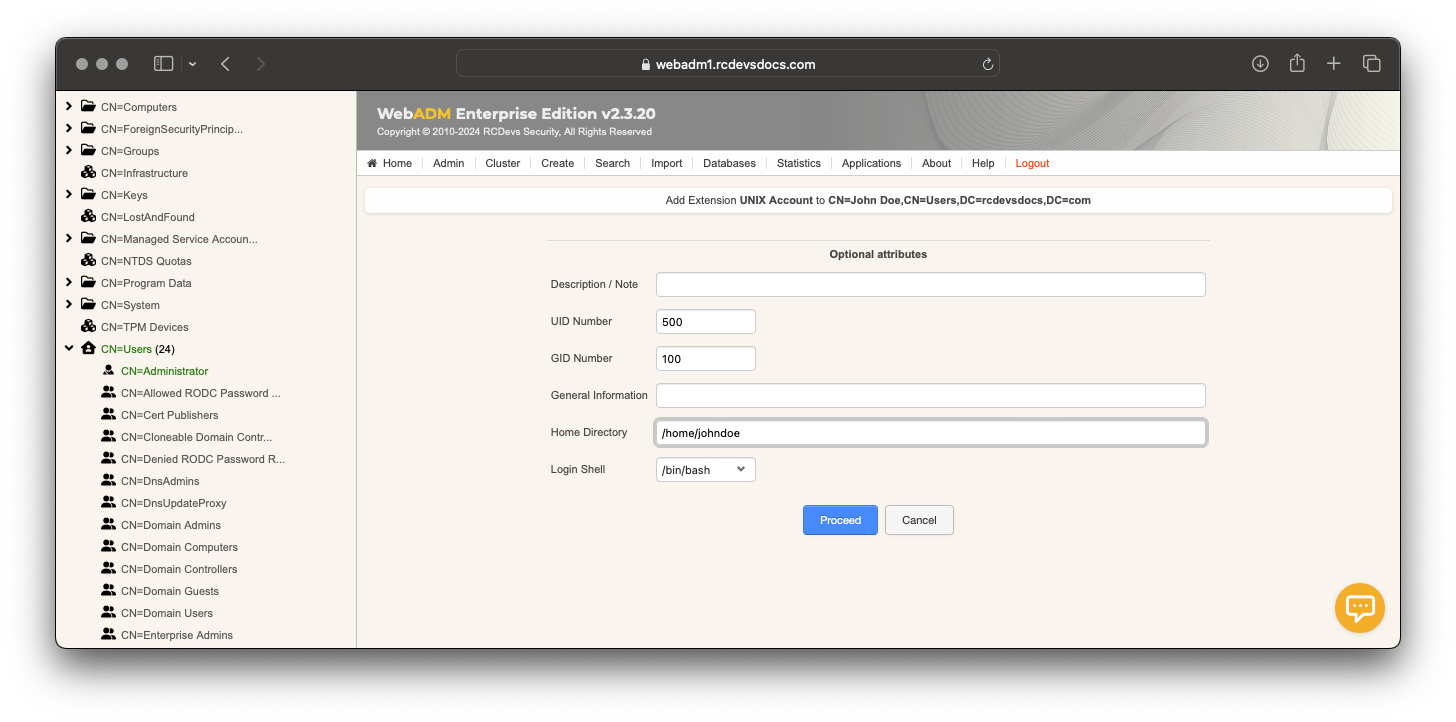
- Enter the following information and click
Proceed. Click onExtend Object.
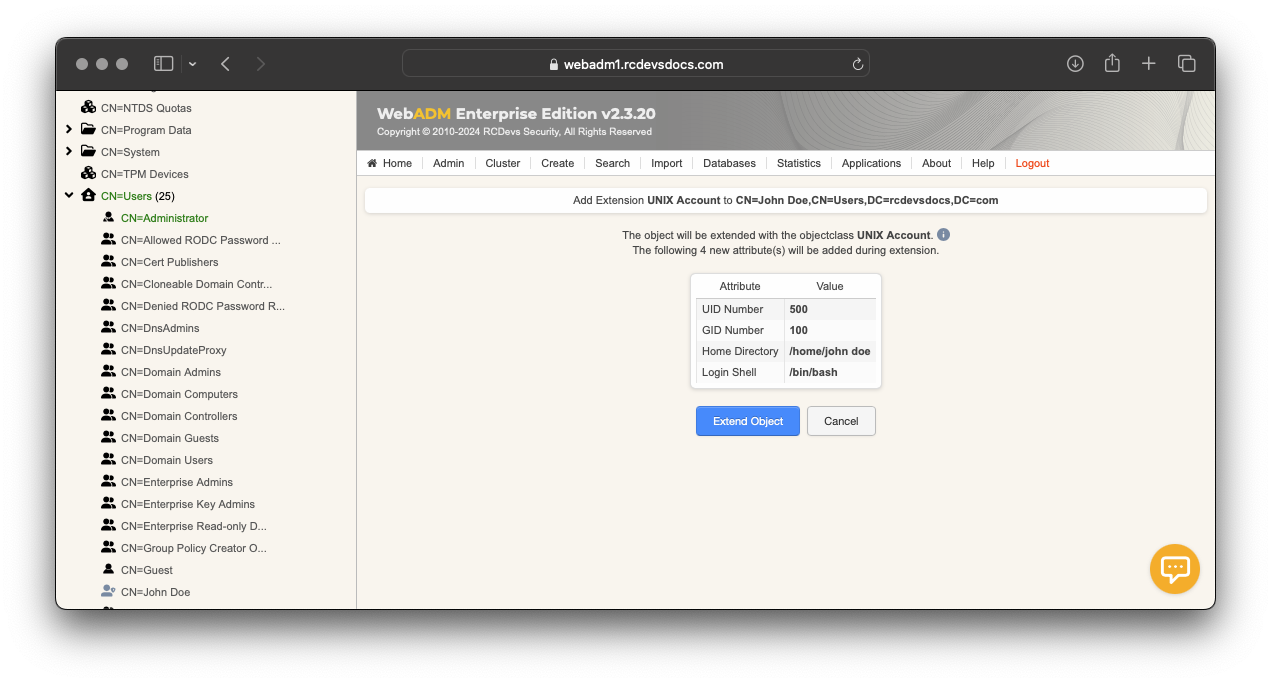
Now, the LDAP Account is extended for UNIX Authentication.
Within the extended LDAP object, click on SSH Public Key Server (Actions box) to generate an SSH Private Key for the user:
- In Application Action box, click on
SSH Public Key Server (3 actions), and select the first itemRegister / Unregister SSH Public Key.

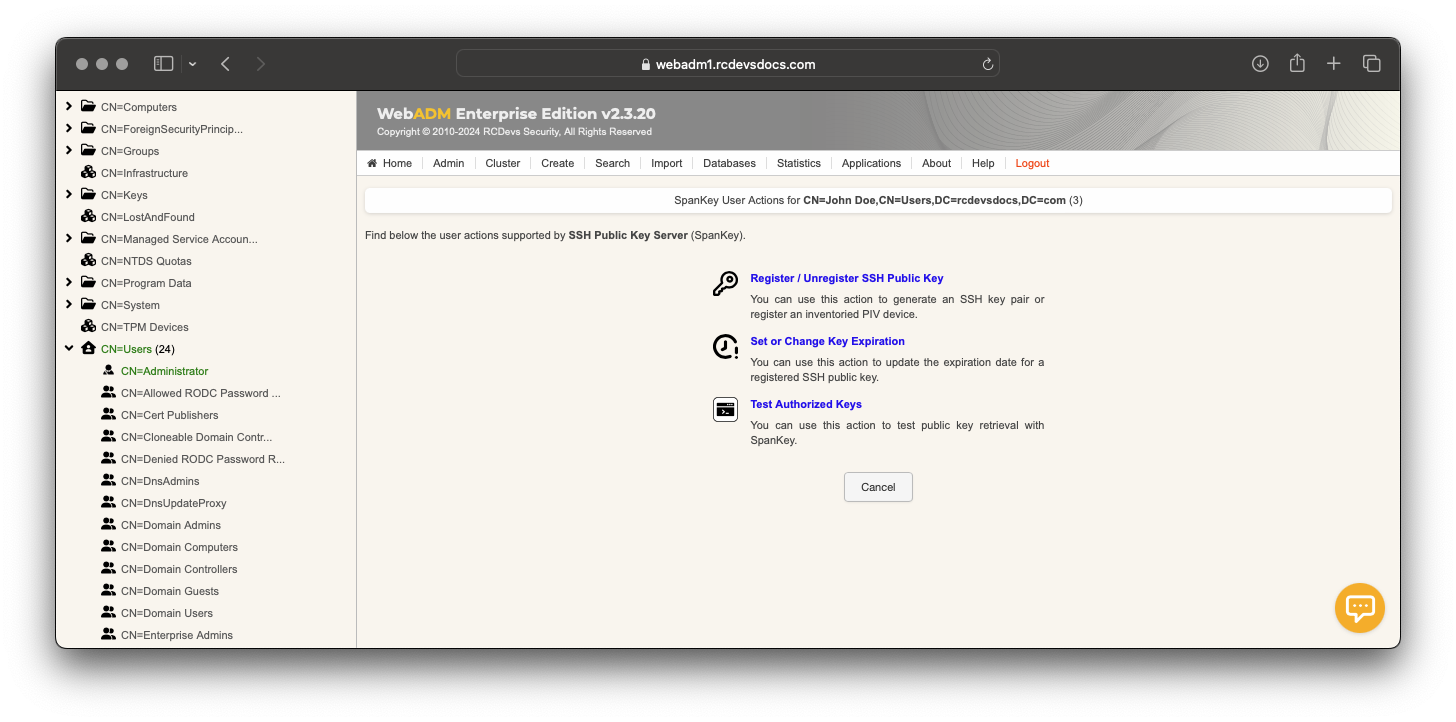
- Configure your preferred Key Format and Key Length.
- Configure key expiration (optional).
- Click on
Register.

Your Public and Private Key are now generated by SpanKey server. Choose the format of the Private Key (OpenSSH or Putty) and click on Download Private Key button.
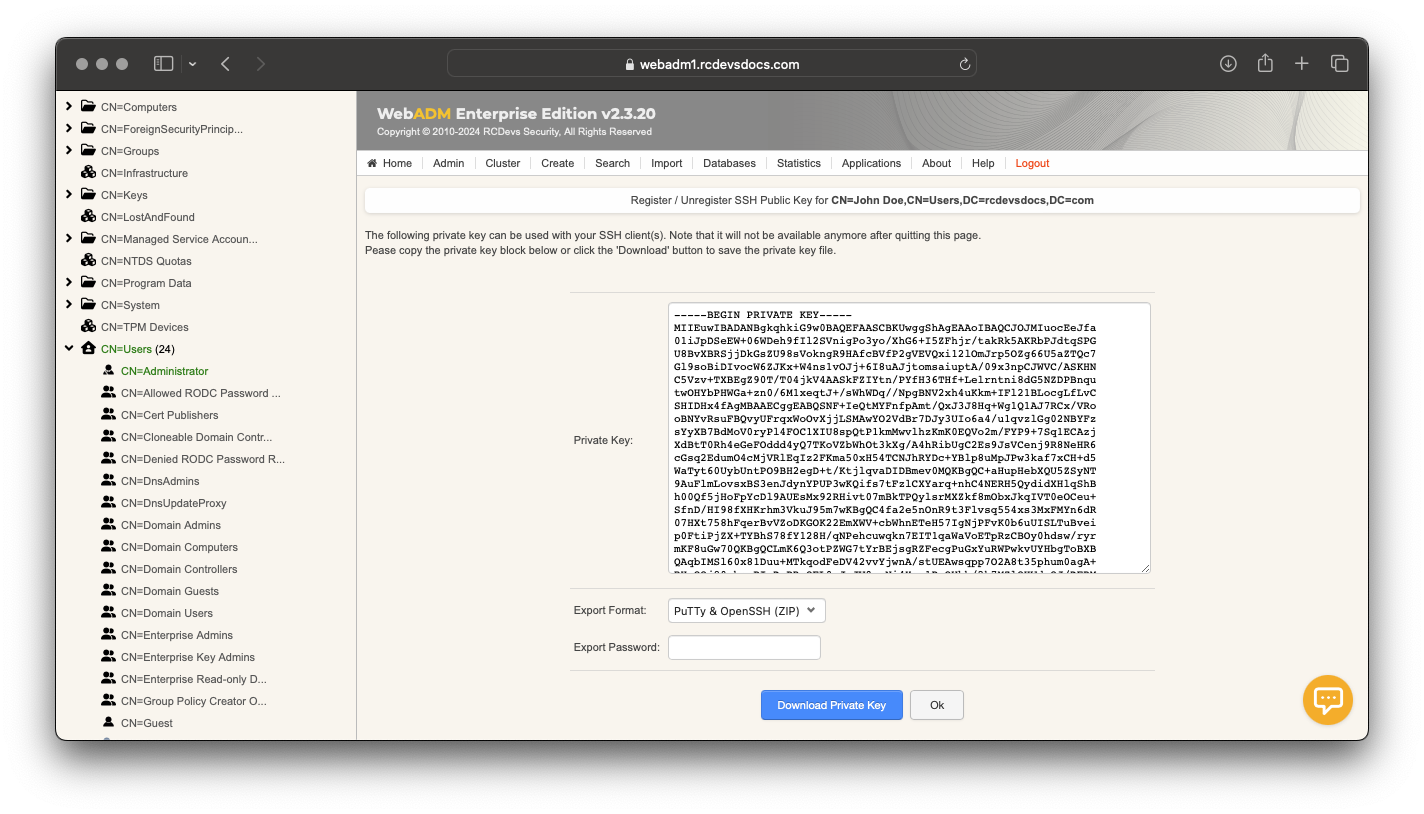
Register or Unregister of SSH Key can also be done through WebADM User Self-Services UI.
Now you can use the generated private key with your LDAP account, through SSH client or Putty and on any server where SpanKey Client is installed on. Without needing to deploy the user’s public keys in authorized_keys files.
To test, connect with your private key on a server managed by SpanKey client, like below:
$ ssh -i johndoe.pem john.doe@192.168.3.104
Welcome to SpanKey SSH Server.
This is a demonstration by RCDEVS SA.
Session recording is enabled.
Audit logs recording is enabled.
Session lock idle time is 5 minutes.
Session's max duration is 30 minutes.
john.doe@ubuntu18-client:~$ exit
exit
>>>> Session's duration was aprox 8 seconds <<<<
Connection to 192.168.3.104 closed.
$
Groups Management (Activation)
To enable your LDAP groups to be propagated as Linux groups, and to work with the SpanKey, it must be extended with Posix objectclass. This is done in the WebADM graphical interface (can be done as a batch jobs as well) as follows:
- Choose LDAP group that you like to extend.
- Choose UNIX Group in the Add Extension selector. Click
Add. - Enter the required information and click
Proceed. Click onExtend Object.
Now, the LDAP group is extended for UNIX usage.
Active Directory Permissions
If you are working with Active Directory and during the UNIX extension you have a failure, it's probably due to rights permissions. That means your super_admin doesn't have enough rights to add the UNIX objectclass to the user and/or to write values on UNIX attributes. To fix it, login on the Active Directory server and run the following command through Powershell:
dsacls "CN=Users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;objectClass'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;gidnumber'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;uidnumber'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;unixhomedirectory'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;loginshell'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;description'
dsacls "cn=users,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;gecos'
Note that cn=users,dc=rcdevsdocs,dc=com is the user search base defined in WebADM Local Domain, RCDEVSDOCS is my NetBIOS domain name and webadmadmin is my super_admin account.
For writting on AD administrators, rights previously settled are not enough because AdminSDHolder overwrites these rights every hour. So we need also to apply these rules on AdminSDHolder object and wait one hour that it’s applied on all admin users and groups of the domain:
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;objectClass'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;gidnumber'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;uidnumber'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;unixhomedirectory'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;loginshell'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;description'
dsacls "CN=AdminSDHolder,CN=System,dc=rcdevsdocs,dc=com" /I:T /G 'RCDEVSDOCS\super_admins:WPRP;gecos'
