Getting Started Guide
This document provides guidance on how to address your needs and use cases with RCDevs solutions, detailing the necessary software packages and introducing the OpenOTP platform. RCDevs products are based on a client/server architecture. In any integration scenario, a server setup is required before configuring client integrations or applications.
Overview
Introduction to OpenOTP security suite
OpenOTP Security Suite is set of software provided by RCDevs installable on Linux systems. The server(s) that runs these solutions uses a product called WebADM to manage the various modules. WebADM manages secure identity access in environments using or requiring AD/LDAP(s) as an identity store. OpenOTP employs an organization-based model, where an organization typically corresponds to an AD/LDAP or a subset (e.g., Organizational Unit). However, the organization can also combine multiple LDAP directories.
The OpenOTP Security Suite includes the following features:
| Services | Details | WebADM and module names |
|---|---|---|
| MFA | Enable Push, FIDO, Passkeys, OTP, certificate, Magic Links or any method of authentication on any host, service or app. | OpenOTP |
| Access Management | Enforce authentication policies on any RADIUS, SAML, OIDC, Windows and Unix/Linux enabled host, service or app. | Client Policies |
| Identity Management | Manage multiple AD/LDAP directories and Unix/Linux server estates to a one Universal Directory and centrally manage users and groups. | Mountpoints and Domains |
| Identity Connect | Connect to one or more AD/LDAP directories to leverage identity data in access policies with needing to replicate the accounts. | Mountpoints and Domains |
| Identity Protection | Detect risky access by observing geo-velocity, location anomaly, IP reputation and user behaviour. | Client Policies/OptionSets; OpenOTP-Badging features |
| Identity Governance | Ensure regulatory compliance with trusted access workflows using digitally signed Contracts Of Access and identity verification. | Client Policies, OpenOTP-eSignature features |
| SSO/Federation | Implement IDP or SP initiated login using SAML or OIDC. | OpenOTP, OpenID & SAML Provider |
| Priveleged Access | Secure access to linux/unix server estates by adding MFA, audit trails (video recordings), identity verification, identity governance and identity protection. | Client Policies; Spankey Server/Client |
| Self Services | Include self-service workflows that enable users to self-enroll their authentication methods, reset their passwords, and more. | User Self-Service Desk; User Self-Registration; Helpdesk; Secure Password Reset |
| ZTNA | Bring legacy perimeter based estates to zero trust architecture by enabling intelligent presence based trust zones. | LDAP OptionSets/Client Policies; OpenOTP-Badging features |
Common Scenarios and Identifying Your Needs/Use Cases
- I am looking for an IAM solution?
WebADM framework is the RCDevs component which provides IAM features. In all scenarios, WebADM framework is mandatory. WebADM can not be installed without an LDAP backend already setup.
- I am looking for a Multi-Factor Authentication (MFA) solution?
OpenOTP is the RCDevs web service component handling authentication. OpenOTP is a component hosted on WebADM.
- I am looking for a Single Sign-On solution?
OpenID & SAML Provider is the RCDevs component managing SSO sessions. The authentication is based on OpenOTP service. OpenID & SAML Provider and OpenOTP are components hosted on WebADM framework.
- I want to protect Windows logins (local and RDP logins) on servers and/or workstations with MFA?
You need WebADM, OpenOTP server(s) and OpenOTP Credential Provider for Windows (client).
- I want to protect my VPN Server, Firewalls, F5, Sophos, ASA... with MFA?
You need WebADM, OpenOTP and Radius Bridge servers. These components are generally installed on the same machine but optionally you can install the Radius Bridge on another machine.
- I want to protect legacy applications supporting only the LDAP protocol with MFA?
You need WebADM, OpenOTP and LDAP Bridge (LDProxy). These components are generally installed on the same machine but optionally you can install the LDAP Bridge on another machine.
- I want to protect ADFS services and its configured applications with MFA?
You need WebADM, OpenOTP servers and OpenOTP plugin for ADFS.
- I want to protect Linux (SSH, Gnome, XDE) with MFA?
You need WebADM, OpenOTP servers, PAM OpenOTP Plugin (client) and optionally Spankey Server and Spankey Client to use LDAP identities on your Linux servers.
- I want to protect Cloud applications compatible with SAML or OpenID with MFA?
You need WebADM, OpenOTP and OpenID & SAML Provider (RCDevs Identity Provider). If these cloud applications are already configured with an ADFS, then you don't need OpenID & SAML Provider component and you can just install the OpenOTP Plugin for ADFS.
- I want to deploy and implement Single Sign-On features on multiple web applications?
You need WebADM, OpenOTP and OpenID & SAML Provider (RCDevs Identity Provider).
- I want to protect my enterprise Wi-Fi, switch or router with MFA or certificate-based authentication?
You need WebADM, OpenOTP and Radius Bridge servers.
- I want to implement electronic signature?
You need WebADM and OpenOTP servers and OpenOTP Token (mobile application). Multiple client integrations are supported by RCDevs to provide a convenient way for end-users to e-sign a document (Sign from Windows with a right click on a document, from Nextcloud, from Mail gateway...)
- I want to protect my OpenSSH servers based on Linux with a centralized SSH key management solution?
You need WebADM and Spankey server/client.
- On my Linux servers, I want to use my AD/LDAP accounts?
- On my Linux servers, I want to centrally define SUDO access?
- On my Linux servers, I want to centrally define auditd rules?
- On my Linux servers, I want to centrally collect auditd logs?
You need WebADM and Spankey server/client components.
- I am m looking for a VPN solution supporting MFA?
RCDevs provides MFAVPN which is a tuned OpenVPN server preconfigured to directly work with OpenOTP authentication service. MFAVPN is provided as a package which can be downloaded from RCDevs website or through RCDevs Linux repositories.
- I am looking for LDAP server?
RCDevs is providing a tuned OpenLDAP server which can be deployed in standalone or in HA mode.
- I need self-service(s) to let my users enroll their tokens, certificates, SSH keys, reset their passwords...
RCDevs provides multiple web applications. For end-user enrollments, you need the User Self-Service Desk (SelfDesk) and/or User Self-Registration (SelfReg). To allow end-users to reset their LDAP passwords, you need the Secure Password Reset application (PWReset). (Note that PWReset application used in a cloud tenant is not going to change the password on the AD account if your AD has been synced to your tenant.)
- I need a portal to delegate day-to-day administration tasks to my Helpdesk team.
To delegate day-to-day end-user tasks, you can install the Helpdesk application on your WebADM server(s).
Getting Started
In this section, we describe the major steps to get started with RCDevs.
Choose your identity residency strategy
The OpenOTP Security Suite is always deployed on top of an LDAP infrastructure and cannot function without this essential building block. All accounts (admins, users, service accounts) used with WebADM are AD/LDAP accounts. There are 3 possible scenarios:
-
In the scenario where an LDAP infrastructure is already available in your environment and you are deploying the OpenOTP Security Suite, it is highly advised to utilize it to avoid duplicating identities across multiple systems. This is the default method for on-premise installations.
-
If you have an LDAP/AD on-premise but wish to use the SaaS version of the OpenOTP Security Suite, you can synchronize your on-premise LDAP/AD data with your OpenOTP Cloud tenant. Refer to the documentation to learn how to synchronize your on-premise Active Directory with your OpenOTP Cloud tenant. This is the default deployment scenario for SaaS setups.
In SaaS deployments, RCDevs OpenLDAP is always used in your tenant. The AD synchronization script uses WebADM APIs to create the LDAP structure, accounts, groups, etc., and periodically synchronizes data from your on-premise LDAP/AD to your OpenOTP Cloud tenant. -
If you do not have any LDAP infrastructure available for your on-premise deployment scenarios, you must install the RCDevs Directory server (SLAPD) and create user identities and groups from the WebADM Administrator Portal.
Setup differences
Choose your setup type between on-premise deployment and SaaS solution. If you prefer not to manage server setup or maintenance, opt for RCDevs SaaS versions on openotp.com.
The limitations compared to on-premise deployment are as follows:
- RADIUS and LDAP-based OpenOTP client applications will require an OpenOTP Cloud Bridge VM or a server configured with RADIUS Bridge and/or LDAP Bridge. RCDevs does not natively provide LDAP APIs in the SaaS deployment. RADIUS APIs can be enabled upon request, although it is preferred to run them on-premise.
- FIDO/WebAuthN authentications will not work with on-premise ADFS.
- You cannot directly use your LDAP/Active Directory infrastructure. Users/groups must be created in your tenant (easy) or synced from your LDAP/AD to your tenant (more advanced). For production deployments, syncing identities and groups is recommended.
All other usecases are covered with the SaaS solution.
Setups
SaaS activation
SaaS provides a dedicated environment (also called "Tenant") with nearly all features of an on-premise deployment.
The advantage of SaaS deployment is that you don't have to install and set up the WebADM framework. Features like Push logins are already configured upon creation of your tenant.
Follow instructions on the Tenant creation documentation to create your SaaS tenant and start to use your OpenOTP Security Suite solution as a service. Once your tenant is created, you can directly go to section of that documentation 4. Running the solution.
On-premise deployment
In an on-premise deployment, there are no limitations in terms of features and integrations, but it requires knowledge of Linux, networking, LDAP, and WebADM framework concepts.
If you intend to use your Active Directory infrastructure, it is recommended, for POC purposes, to use a domain administrator account for the super_admin and proxy_user accounts.
There are three common ways to set up/deploy your on-premise server:
RCDevs Virtual Appliance (2 modes)
- Quick mode: Automatic setup with the RCDevs LDAP server.
- Normal mode: Manual setup where the LDAP identity source can be chosen. (e.g: Active Directory, Novell, OpenLDAP...)
Follow the Virtual Appliance guides to set it up.
Install packages on your own
Set up your own Linux server(s), install the desired packages, and configure everything manually. Refer to the relevant RCDevs documentation for detailed instructions.
-
Provision your server: Machine Sizing/Provisioning
-
Configure the RCDevs repository and install the desired packages (preferred) or download the self-installer packages from the RCDevs website, copy them to your server, extract and install.
-
Follow the WebADM installation guide for the manual setup and cluster guide.
Docker deployment
Set up a Docker environment with the RCDevs Docker Hub and the RCDevs Docker documentation.
Running the solution
Now you can log in to the WebADM administrator portal to manage the different components (OpenOTP, Spankey, Self-services...). Below are the basic steps you need to perform from the WebADM interface to get your system up and running with a client integration:
Mandatory steps:
- Activate your application(s)/service(s) (for on-premise deployment) or check they are active in cloud/SaaS mode.
- User provisioning
- Perform your client integration
Optional steps:
- Define a client policy for your integration
- Manage your solution
Activate and Configure your Applications/Services
From the WebADM Administrator portal, click on the Applications tab and navigate to the Categories box to view all WebADM modules installed on your server.
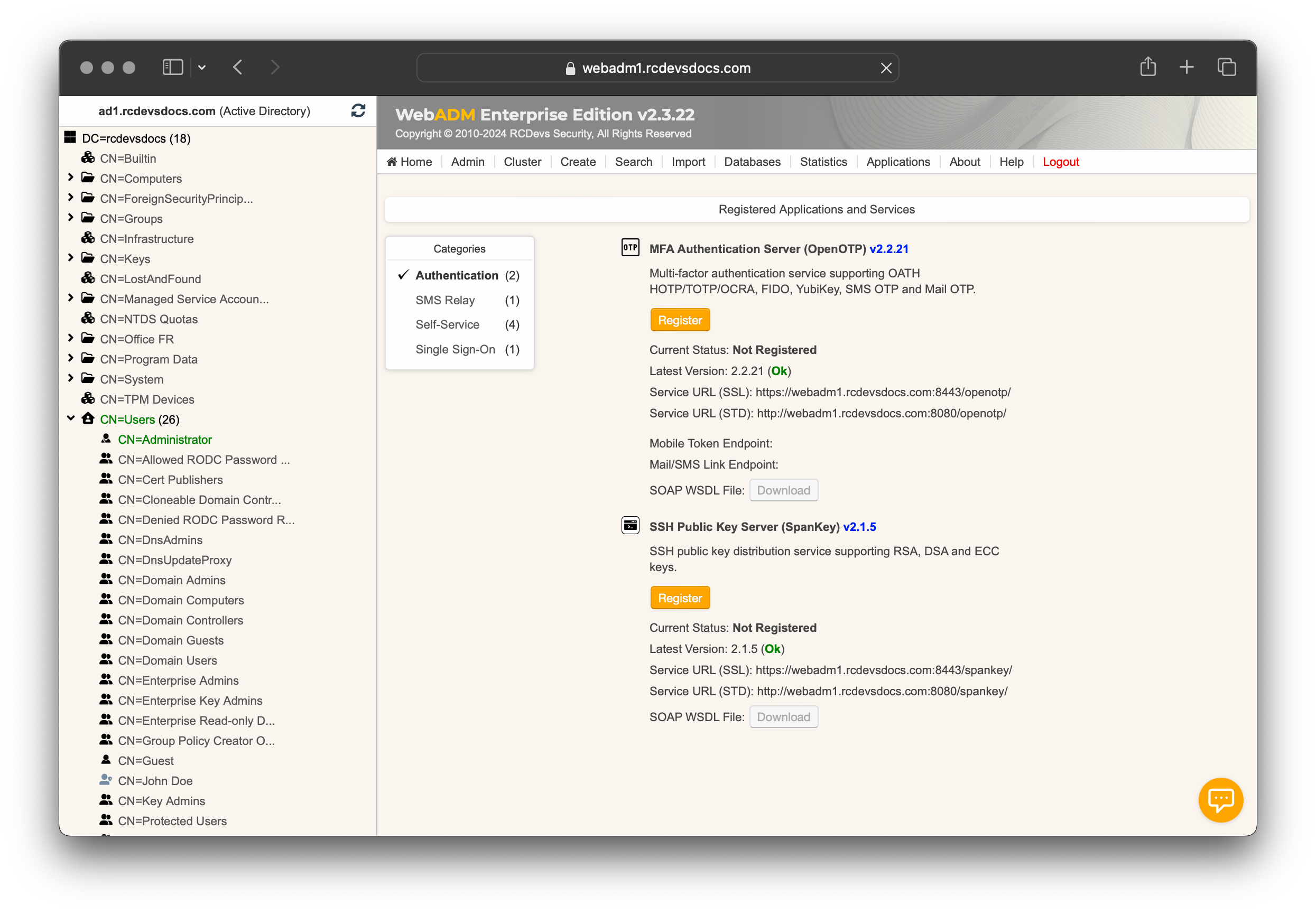
Click the REGISTER button to enable applications and services if they are not already registered.
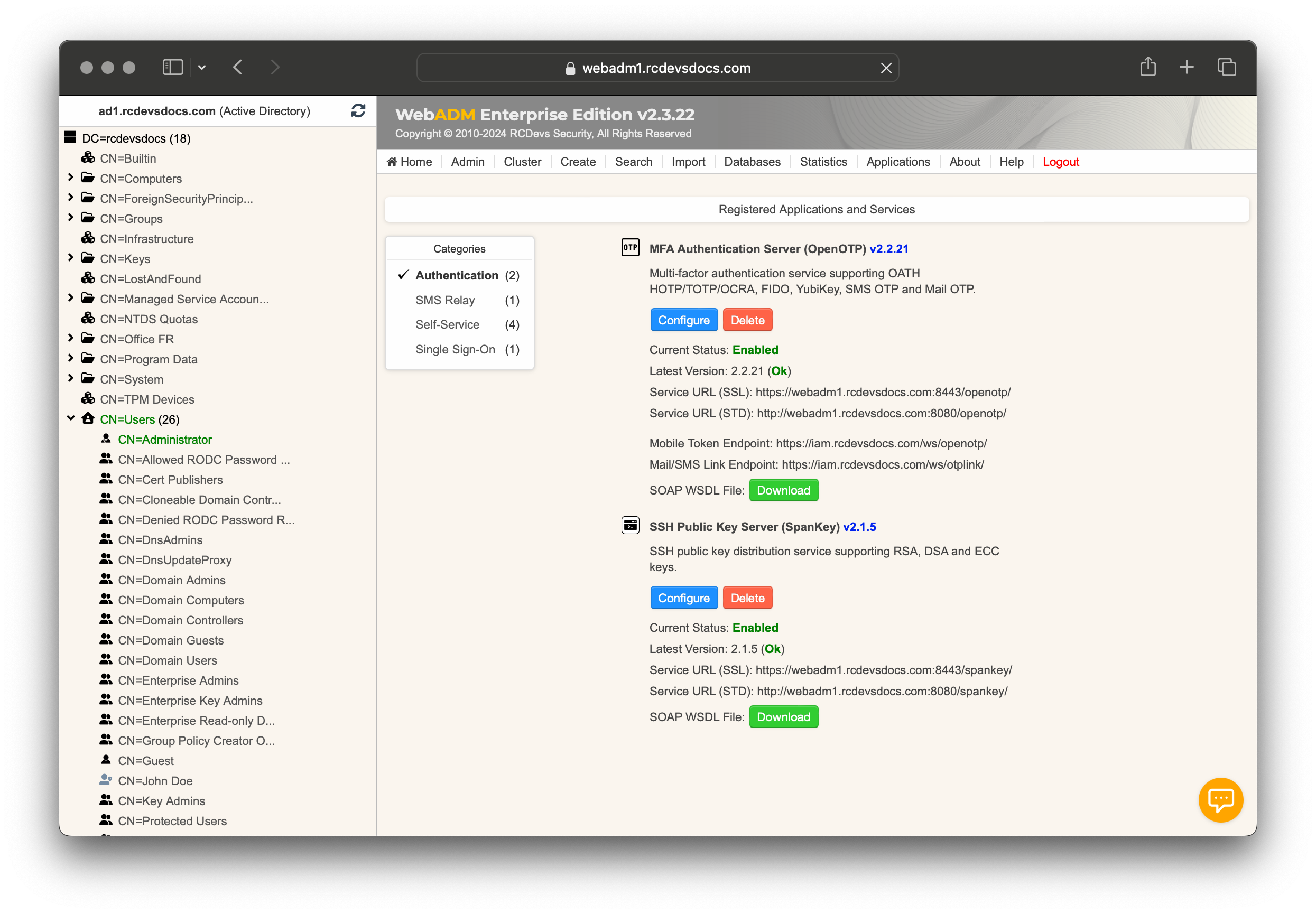
Once you have registered your applications/services, you can use the CONFIGURE button to configure the application.
User Provisioning (creation, license and OTP/MFA Method)
There are 2 to 3 steps in the user provisioning process, which are listed below:
- Create a user (only needed in SaaS deployment without AD/LDAP sync or if the on-premise setup has been done with RCDevs Directory server (SLAPD)).
- Activate the user in order to use that account with the registered services and applications.
- Register a Token through the different interfaces available on your server (WebADM admin GUI, Self-services, Helpdesk...).
Your user is now provisioned and is usable with RCDevs solutions!
Perform your client integration
Once your user is provisioned, you can proceed with client deployments and integrations. Navigate to our documentation website and look for your specific integration:
-
For MFA logins on Windows, you can follow this documentation.
-
For MFA logins on MacOS, you can follow this documentation.
-
For MFA authentication over RADIUS integrations, you can follow this documentation to setup the Radius Bridge component and this one for a few integration examples with ASA, F5, Juniper....
-
For MFA logins on Linux using PAM, you can follow this documentation.
-
For RCDevs Identity Provider integrations (SAML/OpenID), you can follow this documentation. In this category, you will find several integration examples. RCDevs Identity Provider supports all applications that support SAML, OAuth, or OpenID Connect.
-
For MFA login on ADFS integrated applications, you can follow this documentation.
-
For MFA login on legacy applications supporting only the LDAP protocol, you can follow this documentation.
Find more on RCDevs documentation
Define a client policy for your integration
Defining a client policy is considered a best practice with the RCDevs solution; otherwise, you lose a layer of configuration granularity.
Refer to the following documentation to create your client policy.
Managing your solution
- User Self-Service Desk allows end-users to manage their own tokens, FIDO devices, SSH Keys, PassKeys, certificates, and more.
- Secure Password Reset enables end-users to reset their LDAP password on their own.
- Helpdesk provides a self-service portal for a pre-defined administrator group to handle day-to-day tasks such as user licensing, token registration, certificate issuing, password management, and more.
- User Self-Registration allows end-users to register their own tokens, FIDO devices, SSH Keys, PassKeys, certificates, and more via a one-time link provided by administrators or triggered automatically by the system.
- Presence based logical access is a feature in OpenOTP that integrates authentication with user presence and location. This includes Zero Trust Access capabilities, such as automatically locking LDAP accounts when users are not badged-in. This feature reduces the attack surface and prevents unauthorized access across all applications associated with the account.
Something went wrong/Troubleshooting
Check the WebADM server logs on the server at /opt/webadm/logs/webadm.log or from the WebADM Administrator portal under Databases > WebADM server log file. You can refer to the following documentation for commonly known issues.
