Overview
This web application, installed on WebADM server(s), allows users to change their LDAP passwords.
Secure Password Reset is compatible with various LDAP solutions, including AD Domain, UNIX, and SAMBA passwords.
It uses the OpenOTP service to authenticate users on the Secure Password Reset Portal. By default, only a second factor, such as OTP or FIDO, is required, and the LDAP password is not needed. However, LDAP password verification can be enforced in addition to the second factor validation.
If Active Directory is your identity source configured with the WebADM framework, you can log in to the PwReset portal and validate the LDAP password even if it is flagged as expired or needs to be changed. Active Directory provides subcodes that allow WebADM to determine whether the provided password is correct, even if it is expired or requires a change. This functionality is not supported with other LDAP directories, such as OpenLDAP.
You can define password complexity policies in the PwReset configuration or allow the application to adhere to the existing LDAP password policy. In the latter case, you can simply set up a description of your password policy.
Password complexity settings include password size, character types, and verification against weak and blacklist entries.
The installation of PwReset is straightforward, consisting of running the self-installer or installing it from the RCDevs repository and configuring the application in WebADM. You do not need to modify any files in the PwReset install directory; all configurations are managed and stored in LDAP by WebADM. To configure PwReset, log in to WebADM as a super administrator, go to the Applications menu, and click on PwReset to access the web-based configuration.
PwReset application logs are accessible in the Databases menu in WebADM.
To use PwReset, some directory servers, like Active Directory, require encrypted communications (LDAPS or LDAP over TLS).
Additionally, any LDAP user must be a WebADM account to use PwReset. This means LDAP accounts must include the webadmAccount LDAP object class. You can enable WebADM features for any LDAP user or group by extending it with the webadmAccount object class (from the object extension list).
You can also embed the Web application on your website using an HTML iFrame or Object.
#Example
<object data="https://<webadm_addr>/webapps/pwreset?inline=1" />
PwReset Installation
The Secure Password Reset application is included in the webadm-all-in-one package and is available on the RCDevs repository and in the download section of the RCDevs website.
Through RPM Repository
On a RedHat, CentOS or Fedora systems, you can use RCDevs repository for installation:
dnf install pwreset -y
The Secure Password Reset application is now installed.
Through Debian Repository
On a Debian based systems, you can use RCDevs repository for installation:
apt install pwreset -y
The Secure Password Reset application is now installed.
Through the self-installer
If you downloaded the PwReset package from the RCDevs website, copy it on your WebADM server(s) and run the following commands:
[root@webadm1 tmp]# gunzip pwreset-1.3.4-1.sh.gz
[root@webadm1 tmp]# sh pwreset-1.3.4-1.sh
PWReset v1.3.4 Self Installer
Copyright (c) 2010-2024 RCDevs SA, All rights reserved.
Please report software installation issues to bugs@rcdevs.com.
Verifying package update... Ok
Install PwReset in '/opt/webadm/webapps/pwreset' (y/n)? y
Extracting files, please wait... Ok
Removing temporary files... Ok
PWReset has been successfully installed.
Restart WebADM services (y/n) y
Stopping WebADM HTTP server... Ok
Stopping WebADM Watchd server..... Ok
Stopping WebADM PKI server... Ok
Stopping WebADM Session server... Ok
Checking libudev dependency... Ok
Checking system architecture... Ok
Checking server configurations... Ok
Found Trial Enterprise license (RCDEVSSUPPORT)
Licensed by RCDevs SA to RCDevs Support
Licensed product(s): OpenOTP,SpanKey,TiQR
Starting WebADM Session server... Ok
Starting WebADM PKI server... Ok
Starting WebADM Watchd server... Ok
Starting WebADM HTTP server... Ok
Checking server connections. Please wait...
Connected LDAP server: ad1.rcdevsdocs.com (192.168.4.163)
Connected SQL server: webadm1.rcdevsdocs.com (192.168.4.160)
Connected PKI server: webadm1.rcdevsdocs.com (192.168.4.160)
Connected Mail server: mail.rcdevs.com (146.59.204.189)
Connected Session server: webadm1.rcdevsdocs.com (192.168.4.160)
Checking LDAP proxy user access... Ok
Checking SQL database access... Ok
Checking PKI service access... Ok
Checking Mail service access... Ok
Checking Cloud service access... Ok
Cluster mode enabled with 2 nodes (I'm slave)
Session replication status: Active (0.0003 sec)
Please read the INSTALL and README files in /opt/webadm/webapps/pwreset.
PwReset is now installed and can be configured under the WebADM Admin GUI.
PwReset configuration
Configuration of the PwReset application is accessible from the WebADM Administrator portal by navigating to the Applications tab, then Self-Service, and selecting Secure Password Reset (PwReset). Click the Register button if the application is not yet registered, or click the Configure button if it is already registered.
PwReset can be published through a reverse proxy or WebADM Publishing Proxy for end-user access by setting Publish on Public URL. This setting is available only when the public_hostname and reverse_proxies/waproxy_proxies settings are configured in the webadm.conf file.
If you publish PwReset on a reverse proxy or WAProxy, consider the Password Reset URL setting.
This URL should be updated to point to your reverse proxy or WAProxy if you send automatic PwReset links when users' passwords expire. The default URL for this setting is https://webadm_server_address/webapps/pwreset/. If you publish the PwReset application through WAProxy, the URL should be updated to:
https://waproxy_public_address/pwreset/
The /webapps/ folder disappears from the URL when using WAProxy.
A feature specific to Active Directory is Allow Account Unlock, which enables users to unlock their accounts themselves at the AD level. The proxy_user must have the necessary permissions to perform this action.
The other settings are described under the Secure Password Reset configuration page.

Weak and Pwned password verifications
The OpenOTP server and PwReset app include a feature to detect weak or compromised passwords starting from WebADM v2.3.10 / OpenOTP v2.2.11 / PwReset v1.3.2
Weak or compromised passwords refer to passwords that are either easily guessable, simple, or have been exposed through security breaches.
The weak/leaked password verification is done using RCDevs' Cloud infrastructure. A service fetches a large database of leaked passwords from https://haveibeenpwned.com. The end-user password never leaves your WebADM infrastructure.
To perform the verification, WebADM hashes the provided password and sends the first characters of this hash to the RCDevs cloud infrastructure, which returns a list of all hashed passwords starting with the same value. WebADM then compares the end-user password hash with the hashes returned from the RCDevs cloud infrastructure. If there is a match, it means that the user's password has been leaked.
When a leak is detected, WebADM provides the option to automatically send the user an alert with a link to access the PwReset application and reset their password.
Below are the configurable options in the OpenOTP Web Service configuration:
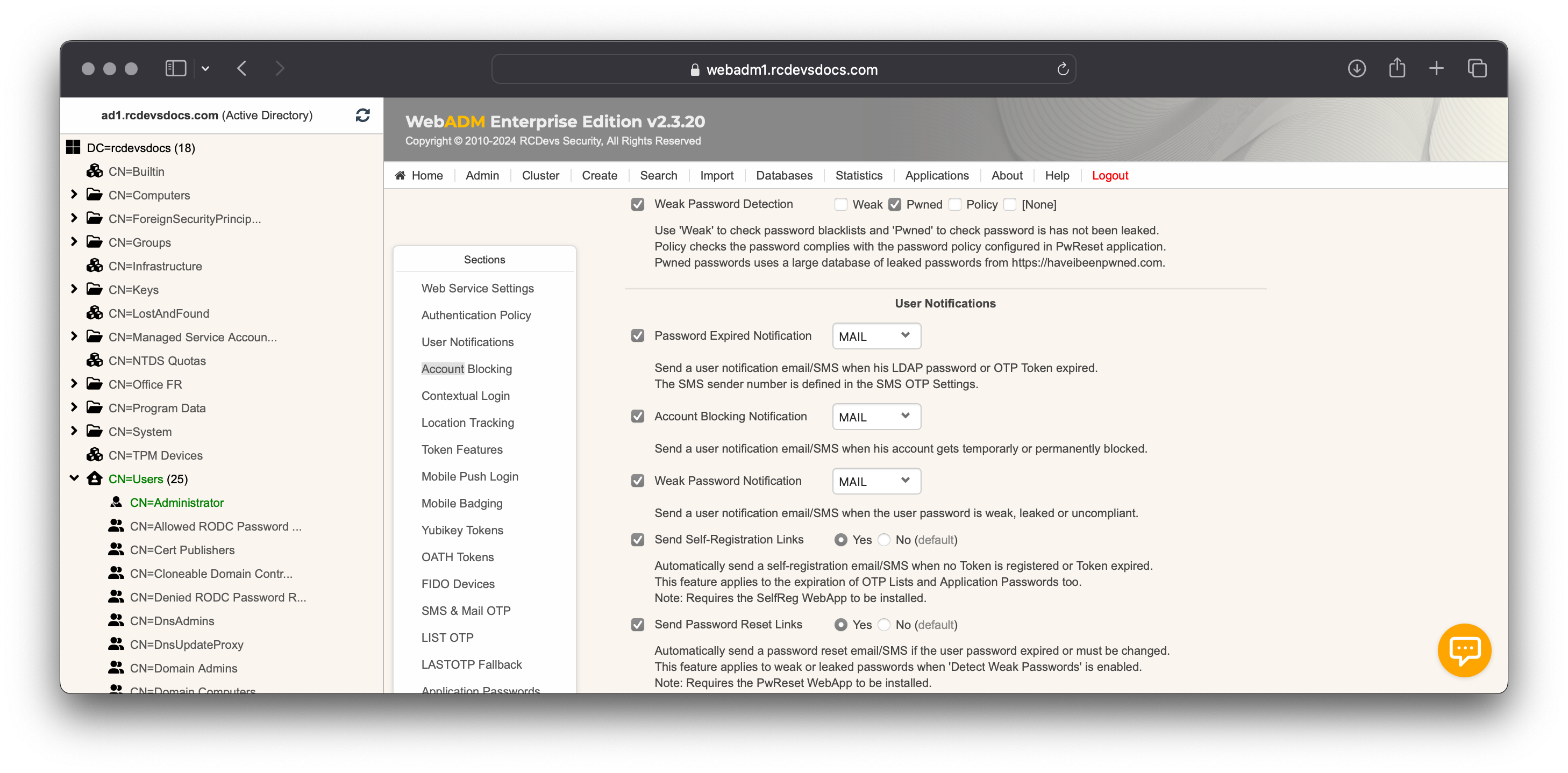
In the Account Blocking section, you will find settings to automatically block a user account if the password is not changed within a specified period after a leak is detected. Optionnaly, an alert can be sent to the administrators receiving WebADM alerts.
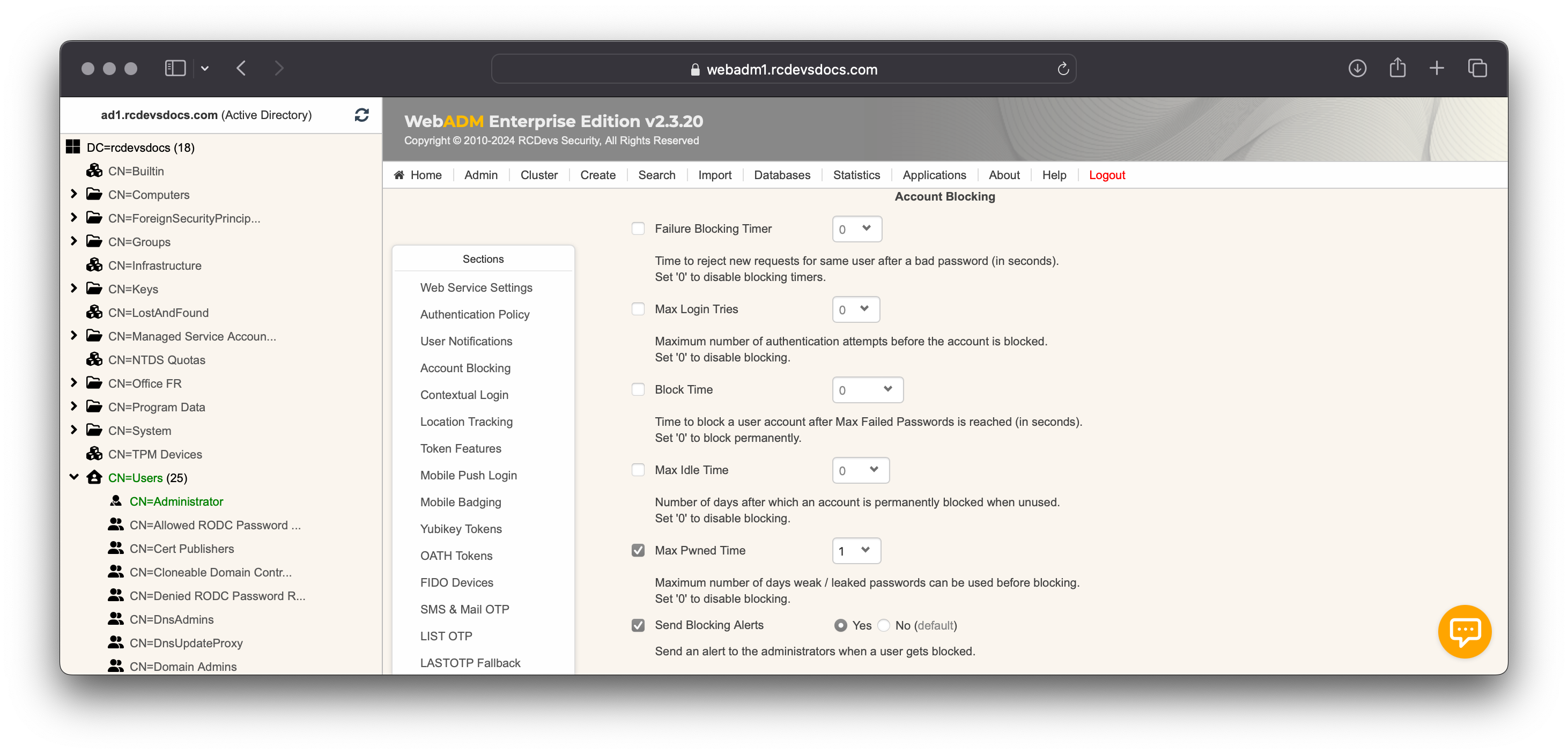
At the PwReset configuration level, there is an option named Refuse Weak Passwords which can be enabled to Pwned or Weak

In this configuration example (OpenOTP and PwReset), the Weak option is enabled at the PwReset level, and Pwned password verification is enabled at the OpenOTP level. In this scenario, a leaked password can be set through PwReset, but OpenOTP will perform the verification when the LDAP password is provided during authentication. If LDAP password validation is not performed at the OpenOTP level, the leak cannot be checked, and you should enable the Pwned option in PwReset. If you choose the Pwned option in PwReset, the user must provide a strong password that is not known to be compromised according to https://haveibeenpwned.com.
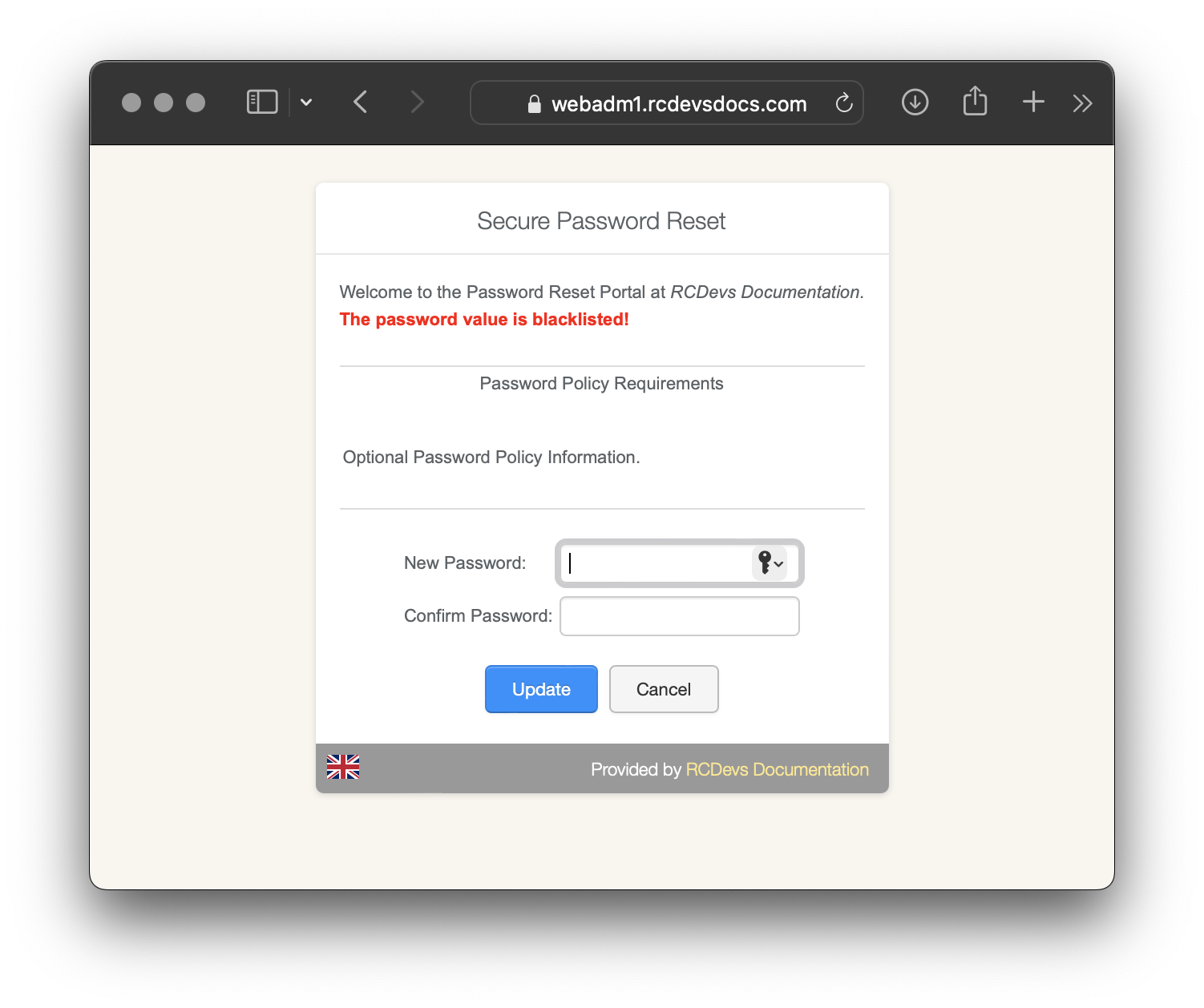
Here, we tried to set the password to Password123, which is considered weak. PwReset informs the user that the provided password is blacklisted.