Overview
This documentation provides comprehensive guidance on integrating RCDevs solutions with Extensible Authentication Protocol (EAP) methods for secure and efficient user and computer authentication.
802.1X is a specific IEEE standard that deals with network access control and authentication. It is used to ensure that only authorized devices and users can access a network. Here are the key points about 802.1X:
-
Authentication: 802.1X provides a framework for authenticating devices or users before they are granted access to a network. This authentication can involve various methods, including username and password, digital certificates, or other credentials.
-
Port-Based Control: The standard is often used in Ethernet networks, and it operates at the data link layer (Layer 2) of the OSI model. It enables the control of network access based on the physical port of the network switch to which a device is connected. This means that when a device is plugged into a port on a switch, it must authenticate itself before it's allowed to communicate on the network.
-
Security: 802.1X enhances network security by preventing unauthorized devices from connecting to the network. It helps protect against unauthorized access and potential security threats.
-
EAP (Extensible Authentication Protocol): 802.1X typically uses EAP to handle the authentication process. EAP is a flexible authentication framework that supports various authentication methods.
-
In 802.1X authentication, there are three key components:
-
Supplicant: This is the device or user that's trying to gain access to the network. It initiates the authentication process.
-
Authenticator: This is the network device (e.g., a switch or wireless access point) that enforces authentication on the physical port.
-
Authentication Server: This is the server responsible for validating the credentials provided by the supplicant.
-
-
Role-Based Access Control: Once authentication is successful, 802.1X can also enforce role-based access control. This means that different users may have different levels of access or permissions within the network by assigning him a VLAN or a privilege level and more. Possibilities will depend on what it supported by your Authenticator equipment. That part is achieved by returning supported RADIUS Attribute Value Pairs IVPs to the authenticator and where attribute(s) value(s) is/are configurable and stored centrally in WebADM users or groups. As an example, I can return a different VLAN assignation based on Users' groups membership.
Overall, 802.1X is widely used in enterprise networks and provides a robust mechanism for ensuring network security and controlling access to network resources.
RCDevs solutions offer a versatile platform for implementing robust authentication mechanisms that cater to a wide range of use cases. In this document, we will explore EAP authentication methods and configurations supported by RCDevs solutions but also the custom integrations of the OpenOTPPKILogin method which is also used by Radius Bridge to deals with OpenOTP and let OpenOTP validate the certificate.
Certificate based authentication involve a PKI service. The default and recommended setup which will support all features described into that documentation is with the WebADM internal PKI service. That service is running in all WebADM infrastructure and is named Rsignd.
With that setup, you will be able to issue users and clients certificates which will be used for authentications.
Issued user certificates are always stored on the corresponding user object in the LDAP backend (in the userCertificate attribute).
Other type of certificates are stored in the SQL database configured with WebADM.
PKI Service
For a well-structured PKI infrastructure design, especially if you already have an operational PKI service within your infrastructure, we recommend configuring WebADM as a Subordinate Certificate Authority of your Enterprise CA.
It is also possible to use a user certificate issued by an external PKI service, provided that the certificate is stored on the user's LDAP object in the 'userCertificate' attribute. However, there are some limitations associated with this scenario. One notable limitation is that EAP negotiation requires certificates issued by the same certificate authority (CA). If there is a mismatch between the CA of the certificates provided by the supplicant and the CA used by the authenticator, the EAP negotiation will fail. That scenario will work in custom integrations where you implement yourself the OpenOTPPKILogin API method and on RCDevs web portals (WebADM Admin GUI, WebApps logins).
Certificates
For computer authentications based on SSL certificates, the certificate must be a Client type when you are issuing it.
For massive client certificate deployment, you can script your CSR and key generation and massively submit the CSRs to the Manager API of WebADM. The API method which can be used for this purpose is called Sign_Certificate_Request. The response will return the signed certificate in PEM format.
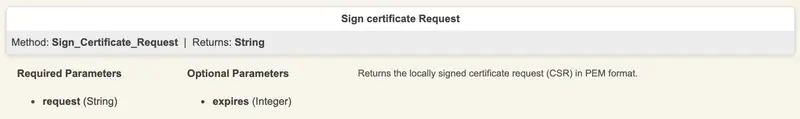
Client certificates can be issued through WebADM Manager APIs or WebADM admin GUI only by a WebADM super_admin or an other_admin.
Non-administrative users do not have the capability to issue client certificates, as this responsibility should remain within the purview of the IT/Security department(s).
For user authentication, the certificate must be a User type when you are issuing it.
User certificate can be issued by the end-user itself through the Self-Services provided by RCDevs, from the WebADM Admin portal and from Manager API. For massive user certificate deployment, you can script your CSR and key generation and massively submit the CSRs to the Manager API of WebADM. The API method which can be used for this purpose is the same as for client certificate (Sign_Certificate_Request). The response will returned the signed certificate in PEM format.
Supported EAP scenarios and transport
RCDevs solutions provide a unified authentication framework for both users and computers, ensuring secure access control across your organization.
-
User Authentication Based on User Certificate (EAP-TLS): RCDevs supports EAP-TLS (Transport Layer Security) authentication, allowing users to authenticate using digital certificates. This method enhances security by validating user identity through their unique certificates.
-
User Authentication Based on LDAP Credentials and optionally MFA (EAP-TTLS): RCDevs supports EAP-TTLS for user authentication. Additionally, you can enhance security by implementing Multi-Factor Authentication (MFA) in this mode. The asked credentials during the authentication will depend on what is configured in your authentication policy(ies) configured at the WebADM level.
-
Computer Authentication Based on Client Certificate (EAP-TLS): RCDevs supports EAP-TLS (Transport Layer Security) authentication, allowing computers to authenticate using digital certificates. This method enhances security by validating computer identity through their unique certificates.
The protocol used between supplicant and authenticator is EAP and between the authenticator and the authentication server is RADIUS.
Custom integrations for Certificate based authentications
OpenOTP provides SOAP API methods that can be integrated wherever you want to authenticate users/computers with SSL certificates. The same SOAP method is used by RADIUS Bridge to build and forward the authentication requests to OpenOTP. The API method will be described later in that documentation.
Prerequisites
You must meet the following requirements in order to set up EAP authentications:
-
Minimum WebADM version is v2.3.7: Ensure that WebADM is installed at version 2.3.7 or higher. This version of WebADM is necessary to provide the infrastructure and support for computer certificate-based authentication.
-
Minimum OpenOTP version is 2.2.9: OpenOTP is an integral part of the authentication process. Verify that OpenOTP is installed and configured, and it should be at version 2.2.9 or higher to ensure compatibility with the other components.
-
Minimum RADIUS Bridge version is 1.3.32: The RADIUS Bridge plays a crucial role in integrating EAP authentication with RADIUS-based network access control. Ensure that the RADIUS Bridge is installed and configured correctly, and it should be running version 1.3.32 or higher to maintain compatibility with WebADM and OpenOTP.
Additional resources
Please consult the Public Key Infrastructure category for comprehensive information regarding the PKI service, configure WebADM as a Subordinate CA, certificate issuance and management processes.
Radius Bridge configuration for EAP (Authentication Server)
Radius Server configuration for EAP-TLS support
We are not explaining the Radius Bridge setup in that documentation. If Radius Bridge component is not installed and configured with your WebADM, please refer to the Radius Bridge documentation.
In order to enable the certificate based authentication feature of Radius Bridge there is 2 settings that you need to enable according to your needs:
- For certificate based authentication, you have to enable the following setting in
/opt/radiusd/conf/radiusd.conflocated at the end of the configuration file:
cert_support = yes
That setting is mandatory to enable certificate based authentication for both users and computers.
Once the settings are configured, please restart Radius Bridge service.
/opt/radiusd/bin/radiusd restart
Radius Client Configuration
On your Radius Bridge server, edit the /opt/radiusd/conf/clients.conf and add the RADIUS client (with IP address, port and RADIUS secret) for your equipment supporting EAP protocols (Switches, WLAN Controllers, routers...).
Example:
client Cisco_Catalyst_Switch {
ipaddr = 192.168.4.253
secret = my_secret
}
client Cisco_WLAN_Controller {
ipaddr = 192.168.4.252
secret = testing123
}
Once your EAP clients are configured, please restart Radius Bridge service.
/opt/radiusd/bin/radiusd restart
Authenticator configuration examples
WLAN Cisco Controller
In that example, we use a Cisco WLAN controller.
The step is to configure wireless to use WPA2 Enterprise security mode and to define the RADIUS server as the authentication server for your WLAN. The specific configuration depends on the brand and model of your WLAN equipment. Please refer to your provider documentation for that part.
We must add a RADIUS AAA Server configuration to your Cisco WLAN controller:
- Login to the WLC GUI.
- Click Security and RADIUS > Authentication.
- In the RADIUS Authentication servers page appears, click New to add a new RADIUS Authentication Server.
- Enter the RADIUS server corresponding to the Radius Bridge configuration in chapter 2.
Next, configure the WLAN networks and settings:
- Open the WLANs page from the controller web interface.
- Choose an existing or create a new WLAN.
- In the "Security" tab, open the "AAA Servers" sub tab.
- Select the RADIUS server you configured as the "Authentication server".
- Click Apply to save your configuration.
The below image provides an example of Cisco Linksys wireless router configuration.
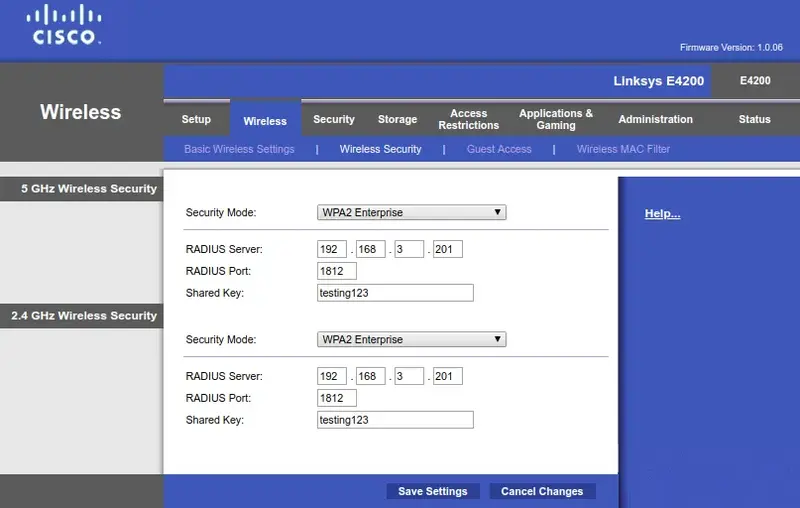
For WLAN Access Point
If you have a standalone WLAN access point or router, without a centralized controller, you must configure the RADIUS server on each access point.
Cisco Switch Catalyst
To configure 802.1X on my Switch, I followed the Cisco documentation. Please refer to your provider documentation to setup port based authentication (802.1X) on your switches.
Supplicants configurations
Windows 10/11
User certificate based authentication
Recent Windows versions have native support for the required authentication protocols, so it is possible to use certificates for authentication without additional software.
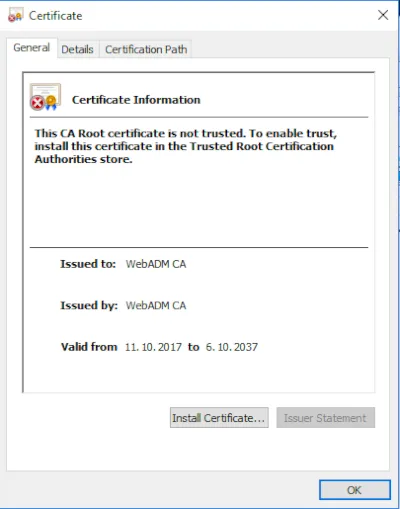
First, we must install the CA certificate of your WebADM on the Windows client. Open the CA certificate in Windows and click Install Certificate.
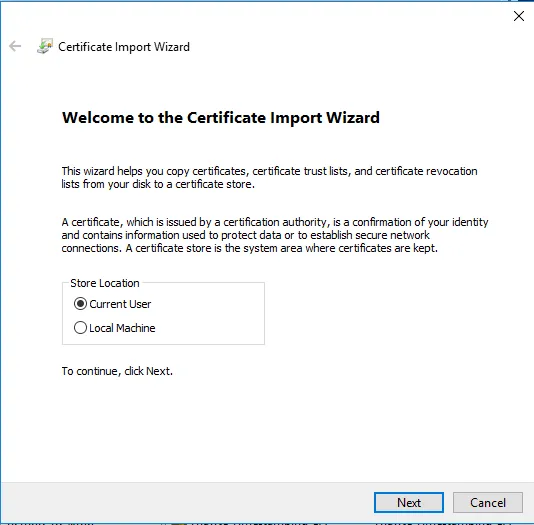
Click Next on the following page in Certificate Import Wizard.
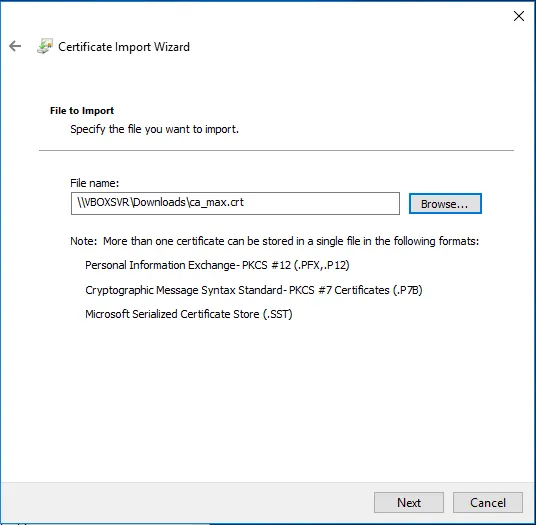
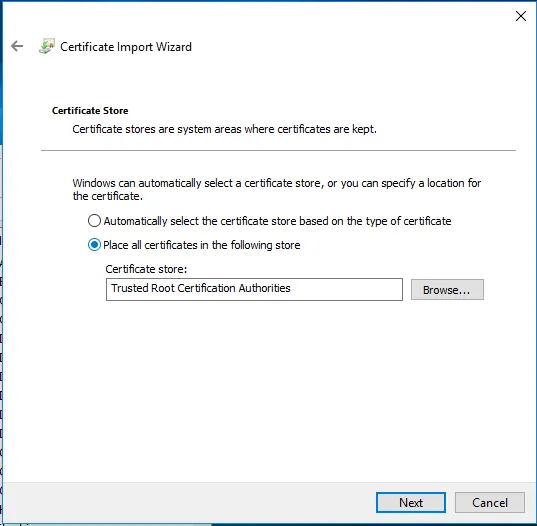
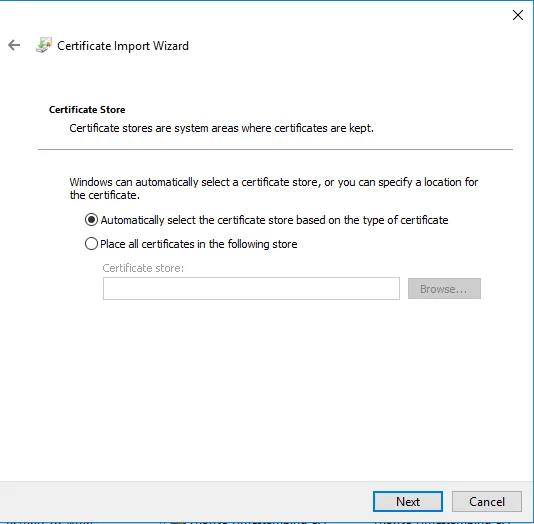
On the next page, select the certificate store in which the certificate should be installed. You must install the certificate in the "Trusted Root Certification Authorities". Click Next followed by Finish on the next page.
Next, we install the user certificate downloaded from Self-Service to the Windows client. Open the user certificate, select "Current User" in the wizard and click "Next" two times.
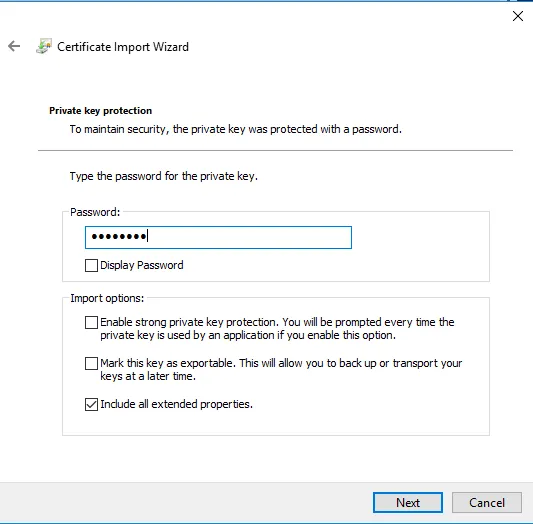
When the wizard asks for the password for the certificate, input the password you've received in the Self-Service desk when downloading the certificate.
You can let Windows select the certificate store for the user certificate automatically. Click "Next" followed by Finish.
When you are prompted for username and password, select "Connect using a certificate".
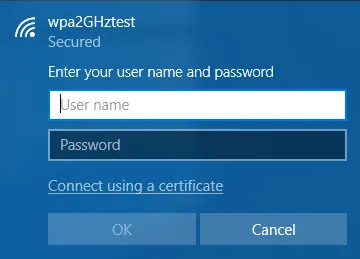
Choose the user certificate you've installed previously, click "OK" followed by "Connect".
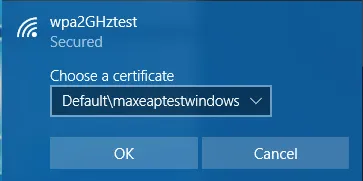
Device certificate based authentication
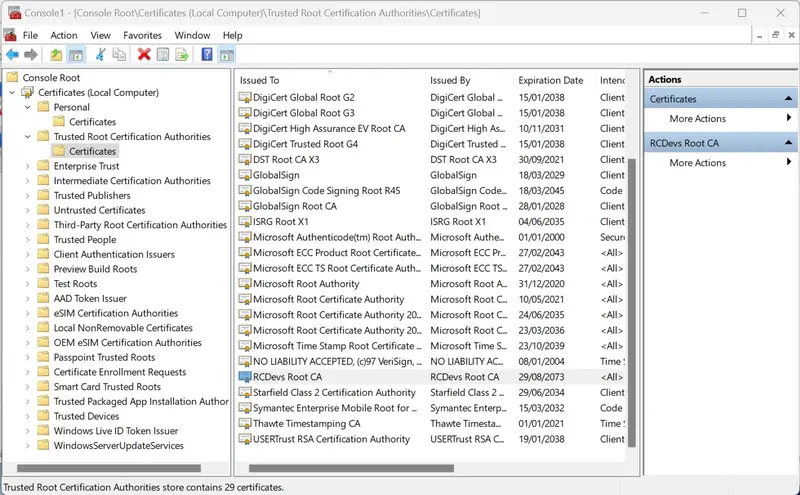
You can copy the p12 bundle previously created on your Windows machine. You also have to Trust the CA certificate of WebADM on your Windows machine. The CA certificate can be downloaded at https://webadm_server_address/cacert
You must add the CA certificate to the Trusted Root Certification Authorities in the computer store.
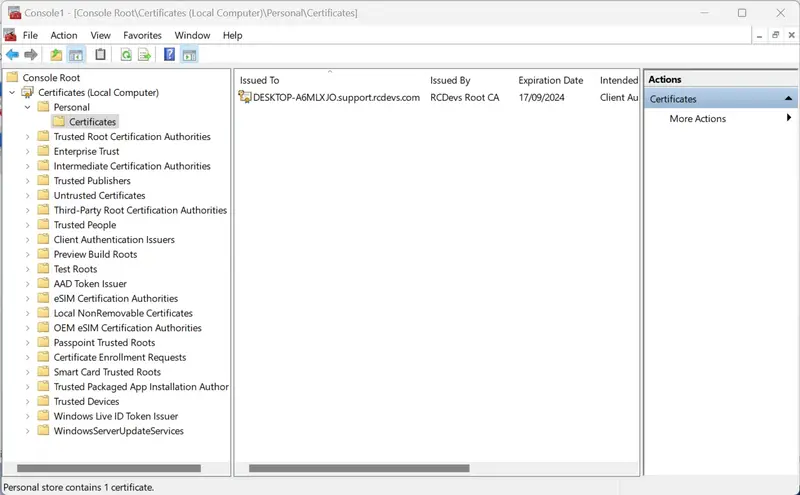
The client certificate (p12 bundle) must be installed in the Personal folder within the computer store. During the import process, you will be prompted to enter the password you set during the client certificate generation. For security reasons, you should also take measures to prevent the private key from being exported to minimize the risk of the certificate being reused on another machine.
Once the certificate import is done, you can configure your network interface to set up the 802.1x authentication.
Access the Control Panel menu then click on Network Connections. Right-click on the Ethernet adapter that you want to configure then click Properties.
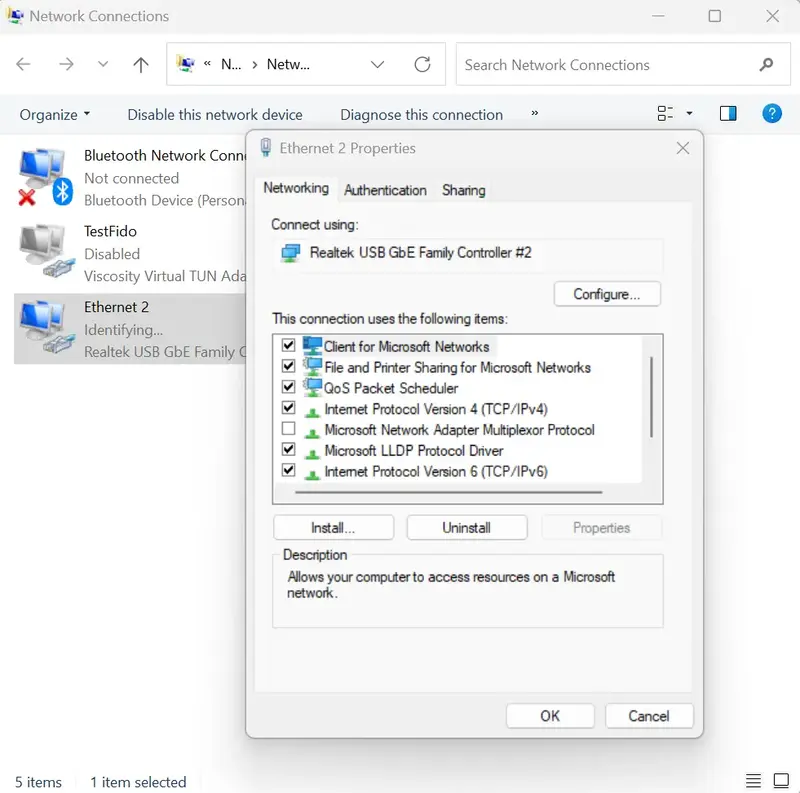
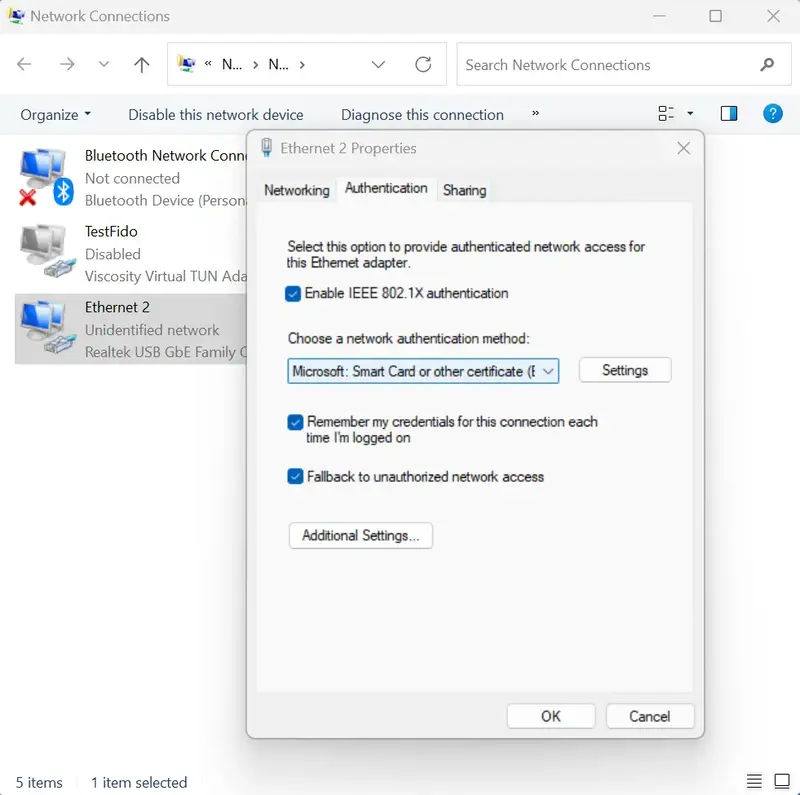
In Properties, click Authentication tab, enable the checkbox IEEE 802.1X Authentication and choose the network authentication method to Microsoft: Smartcard or other Certificate. Click then the Settings button.
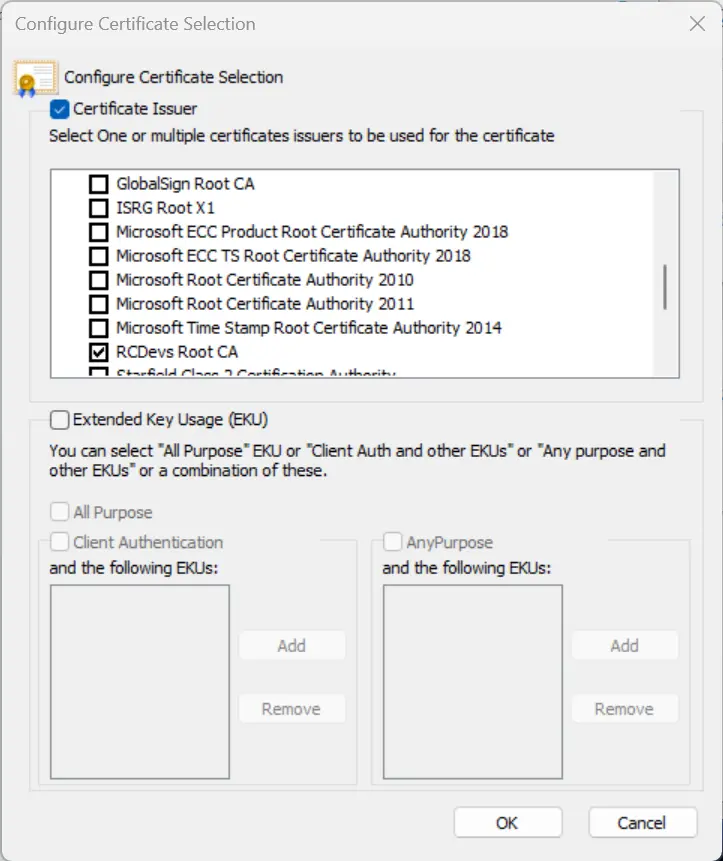
Once you are on the Configure Certificate selection view, enable the checkbox Certificate Issuer and you can choose the WebADM CA certificate previously imported in the Trusted Root Certification Authorities. Click Ok.
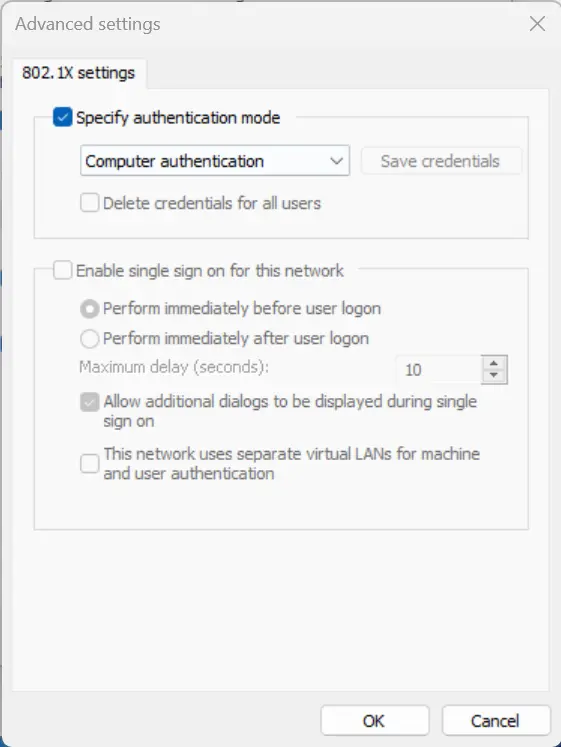
You are back to the previous page, click now the Additional Settings button.

You are redirected to the following page:
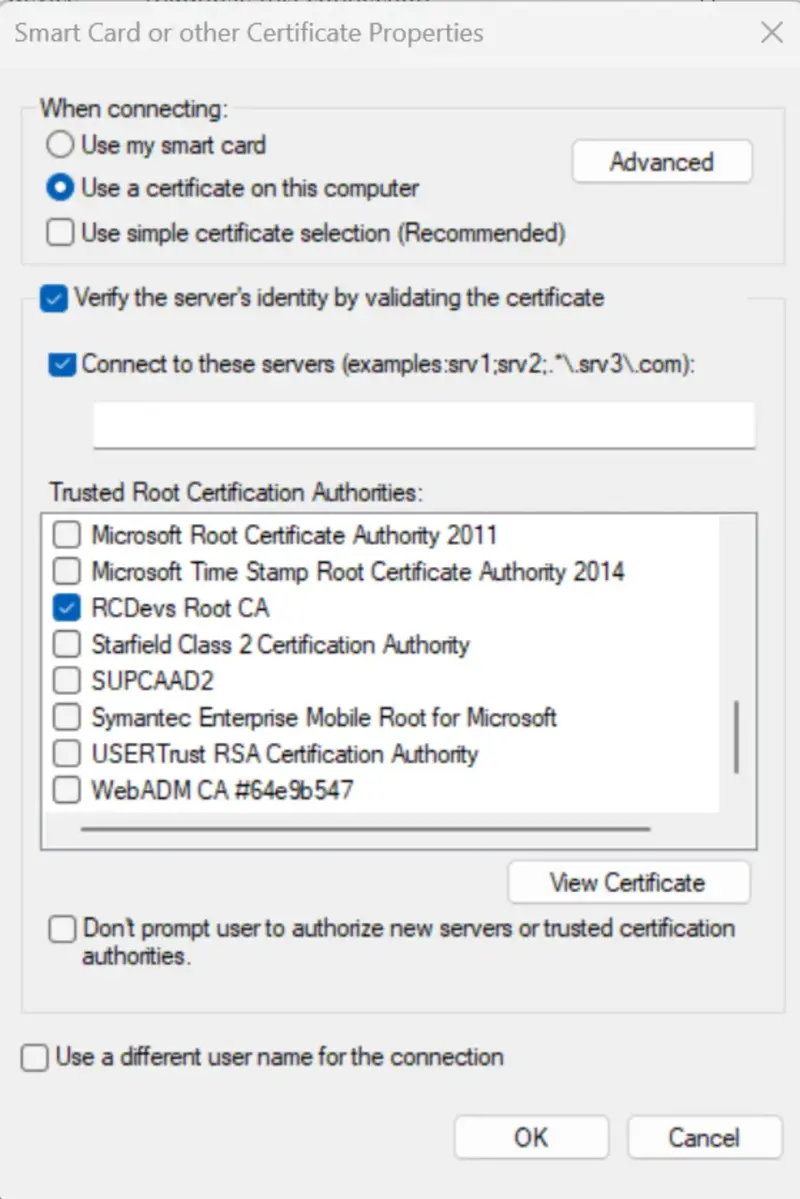
As we imported the certificate in the Computer Personal Certificate Store, I enabled the option Use a certificate from this computer. If the certificate is uploaded on a smartcard, then keep Use my smart card and the smartcard will have to be connected to the computer in order to use the certificate stored on it. Click then on Advanced button and choose the authentication mode to Computer Authentication
(0) Received Access-Request Id 173 from 192.168.4.253:1812 to 192.168.4.160:1812 length 193
(0) NAS-IP-Address = 192.168.4.253
(0) NAS-Port = 50002
(0) NAS-Port-Type = Ethernet
(0) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(0) Called-Station-Id = "00-21-1C-EA-37-42"
(0) Calling-Station-Id = "00-13-3B-A0-43-3E"
(0) Service-Type = Framed-User
(0) Framed-MTU = 1500
(0) EAP-Message = 0x0200002c01686f73742f4445534b544f502d41364d4c584a4f2e737570706f72742e7263646576732e636f6d
(0) Message-Authenticator = 0x2ac5b9393ab7c8d5d914660863a56a72
(0) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(0) authorize {
(0) eap: Peer sent EAP Response (code 2) ID 0 length 44
(0) eap: Continuing tunnel setup
(0) [eap] = ok
(0) } # authorize = ok
(0) Found Auth-Type = EAP
(0) # Executing group from file /opt/radiusd/lib/radiusd.ini
(0) Auth-Type EAP {
(0) eap: Peer sent packet with method EAP Identity (1)
(0) eap: Calling submodule eap_ttls to process data
(0) eap_ttls: (TLS) Initiating new session
(0) eap: Sending EAP Request (code 1) ID 1 length 6
(0) eap: EAP session adding &reply:State = 0x2a019a2d2a008f61
(0) [eap] = handled
(0) } # Auth-Type EAP = handled
(0) Using Post-Auth-Type Challenge
(0) Post-Auth-Type sub-section not found. Ignoring.
(0) session-state: Saving cached attributes
(0) Framed-MTU = 994
(0) Sent Access-Challenge Id 173 from 192.168.4.161:1812 to 192.168.4.253:1812 length 64
(0) EAP-Message = 0x010100061520
(0) Message-Authenticator = 0x00000000000000000000000000000000
(0) State = 0x2a019a2d2a008f6172f171851926dbf8
(0) Finished request
Waking up in 9.9 seconds.
(1) Received Access-Request Id 174 from 192.168.4.253:1812 to 192.168.4.160:1812 length 173
(1) NAS-IP-Address = 192.168.4.253
(1) NAS-Port = 50002
(1) NAS-Port-Type = Ethernet
(1) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(1) Called-Station-Id = "00-21-1C-EA-37-42"
(1) Calling-Station-Id = "00-13-3B-A0-43-3E"
(1) Service-Type = Framed-User
(1) Framed-MTU = 1500
(1) State = 0x2a019a2d2a008f6172f171851926dbf8
(1) EAP-Message = 0x02010006030d
(1) Message-Authenticator = 0x298794c7ffc1e7c59739b04ca20727dc
(1) Restoring &session-state
(1) &session-state:Framed-MTU = 994
(1) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(1) authorize {
(1) eap: Peer sent EAP Response (code 2) ID 1 length 6
(1) eap: Continuing tunnel setup
(1) [eap] = ok
(1) } # authorize = ok
(1) Found Auth-Type = EAP
(1) # Executing group from file /opt/radiusd/lib/radiusd.ini
(1) Auth-Type EAP {
(1) eap: Expiring EAP session with state 0x2a019a2d2a008f61
(1) eap: Finished EAP session with state 0x2a019a2d2a008f61
(1) eap: Previous EAP request found for state 0x2a019a2d2a008f61, released from the list
(1) eap: Peer sent packet with method EAP NAK (3)
(1) eap: Found mutually acceptable type TLS (13)
(1) eap: Calling submodule eap_tls to process data
(1) eap_tls: (TLS) Initiating new session
(1) eap_tls: (TLS) Setting verify mode to require certificate from client
(1) eap: Sending EAP Request (code 1) ID 2 length 6
(1) eap: EAP session adding &reply:State = 0x2a019a2d2b039761
(1) [eap] = handled
(1) } # Auth-Type EAP = handled
(1) Using Post-Auth-Type Challenge
(1) Post-Auth-Type sub-section not found. Ignoring.
(1) session-state: Saving cached attributes
(1) Framed-MTU = 994
(1) Sent Access-Challenge Id 174 from 192.168.4.160:1812 to 192.168.4.253:1812 length 64
(1) EAP-Message = 0x010200060d20
(1) Message-Authenticator = 0x00000000000000000000000000000000
(1) State = 0x2a019a2d2b03976172f171851926dbf8
(1) Finished request
Waking up in 9.9 seconds.
(2) Received Access-Request Id 175 from 192.168.4.253:1812 to 192.168.4.160:1812 length 430
(2) NAS-IP-Address = 192.168.4.253
(2) NAS-Port = 50002
(2) NAS-Port-Type = Ethernet
(2) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(2) Called-Station-Id = "00-21-1C-EA-37-42"
(2) Calling-Station-Id = "00-13-3B-A0-43-3E"
(2) Service-Type = Framed-User
(2) Framed-MTU = 1500
(2) State = 0x2a019a2d2b03976172f171851926dbf8
(2) EAP-Message = 0x020201050d80000000fb16030100f6010000f2030386a0bc99a2f21bee48f1aa5956c7f89efff335f808418dd762d44b52d0f5ccb0200444ec26f2baecbe3ce507ea354473e31257b166231580778d8722c53ae867e8002813021301c02cc02bc030c02fc024c023c028c027c00ac009c014c013009d009c003d003c0035002f01000081000500050100000000002b0009080304030303020301000d001a001808040805080604010501020104030503020302020601060300230000000a00080006001d00170018003300260024001d00205403e7224a730c70a4ccf2887869da44813aec81f75019fe23ad025be5fce1750031000000170000ff01000100002d00020101
(2) Message-Authenticator = 0xb8625c14068a4f535607ebc48f9b1d5d
(2) Restoring &session-state
(2) &session-state:Framed-MTU = 994
(2) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(2) authorize {
(2) eap: Peer sent EAP Response (code 2) ID 2 length 261
(2) eap: Continuing tunnel setup
(2) [eap] = ok
(2) } # authorize = ok
(2) Found Auth-Type = EAP
(2) # Executing group from file /opt/radiusd/lib/radiusd.ini
(2) Auth-Type EAP {
(2) eap: Expiring EAP session with state 0x2a019a2d2b039761
(2) eap: Finished EAP session with state 0x2a019a2d2b039761
(2) eap: Previous EAP request found for state 0x2a019a2d2b039761, released from the list
(2) eap: Peer sent packet with method EAP TLS (13)
(2) eap: Calling submodule eap_tls to process data
(2) eap_tls: (TLS) EAP Peer says that the final record size will be 251 bytes
(2) eap_tls: (TLS) EAP Got all data (251 bytes)
(2) eap_tls: (TLS) Handshake state - before SSL initialization
(2) eap_tls: (TLS) Handshake state - Server before SSL initialization
(2) eap_tls: (TLS) Handshake state - Server before SSL initialization
(2) eap_tls: (TLS) recv TLS 1.3 Handshake, ClientHello
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client hello
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerHello
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server hello
(2) eap_tls: (TLS) send TLS 1.2 Handshake, Certificate
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write certificate
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerKeyExchange
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write key exchange
(2) eap_tls: (TLS) send TLS 1.2 Handshake, CertificateRequest
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write certificate request
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerHelloDone
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server done
(2) eap_tls: (TLS) Server : Need to read more data: SSLv3/TLS write server done
(2) eap_tls: (TLS) In Handshake Phase
(2) eap: Sending EAP Request (code 1) ID 3 length 1004
(2) eap: EAP session adding &reply:State = 0x2a019a2d28029761
(2) [eap] = handled
(2) } # Auth-Type EAP = handled
(2) Using Post-Auth-Type Challenge
(2) Post-Auth-Type sub-section not found. Ignoring.
(2) session-state: Saving cached attributes
(2) Framed-MTU = 994
(2) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(2) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(2) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(2) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(2) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(2) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(2) Sent Access-Challenge Id 175 from 192.168.4.160:1812 to 192.168.4.253:1812 length 1068
(2) EAP-Message = 0x010303ec0dc000000cb3160303003502000031030302d214a8f835dfda6fe8933ad05921668c24f6ce99a81546f81a258f9bd36fb700c030000009ff01000100001700001603030a8a0b000a86000a830004f4308204f0308202d8a003020102021100e146ed9003522922e87d26ff478958e7300d06092a864886f70d01010b0500304c3117301506035504030c0e52434465767320526f6f74204341310b3009060355040b0c02434131173015060355040a0c0e52434465767320537570706f7274310b3009060355040613024c55301e170d3233303931353134333732395a170d3333303931323134333732395a30363123302106035504030c1a77656261646d312e737570706f72742e7263646576732e636f6d310f300d060355040d0c0653455256455230820122300d06092a864886f70d01010105000382010f003082010a0282010100a626353e93abdfe0f3dd8b91e23f6e22640cdab9c0f44023e2cfd17642038bea3e12b5f4f98d6c575611fb3aee9f
(2) Message-Authenticator = 0x00000000000000000000000000000000
(2) State = 0x2a019a2d2802976172f171851926dbf8
(2) Finished request
Waking up in 9.9 seconds.
(3) Received Access-Request Id 176 from 192.168.4.253:1812 to 192.168.4.160:1812 length 173
(3) NAS-IP-Address = 192.168.4.253
(3) NAS-Port = 50002
(3) NAS-Port-Type = Ethernet
(3) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(3) Called-Station-Id = "00-21-1C-EA-37-42"
(3) Calling-Station-Id = "00-13-3B-A0-43-3E"
(3) Service-Type = Framed-User
(3) Framed-MTU = 1500
(3) State = 0x2a019a2d2802976172f171851926dbf8
(3) EAP-Message = 0x020300060d00
(3) Message-Authenticator = 0x05115c60ec77564bc18f7ae8bb79695f
(3) Restoring &session-state
(3) &session-state:Framed-MTU = 994
(3) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(3) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(3) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(3) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(3) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(3) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(3) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(3) authorize {
(3) eap: Peer sent EAP Response (code 2) ID 3 length 6
(3) eap: Continuing tunnel setup
(3) [eap] = ok
(3) } # authorize = ok
(3) Found Auth-Type = EAP
(3) # Executing group from file /opt/radiusd/lib/radiusd.ini
(3) Auth-Type EAP {
(3) eap: Expiring EAP session with state 0x2a019a2d28029761
(3) eap: Finished EAP session with state 0x2a019a2d28029761
(3) eap: Previous EAP request found for state 0x2a019a2d28029761, released from the list
(3) eap: Peer sent packet with method EAP TLS (13)
(3) eap: Calling submodule eap_tls to process data
(3) eap_tls: (TLS) Peer ACKed our handshake fragment
(3) eap: Sending EAP Request (code 1) ID 4 length 1004
(3) eap: EAP session adding &reply:State = 0x2a019a2d29059761
(3) [eap] = handled
(3) } # Auth-Type EAP = handled
(3) Using Post-Auth-Type Challenge
(3) Post-Auth-Type sub-section not found. Ignoring.
(3) session-state: Saving cached attributes
(3) Framed-MTU = 994
(3) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(3) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(3) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(3) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(3) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(3) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(3) Sent Access-Challenge Id 176 from 192.168.4.160:1812 to 192.168.4.253:1812 length 1068
(3) EAP-Message = 0x010403ec0dc000000cb365e0f50616561bd3e6513de7f3d235c02f1b51e30e2d3ab6bb527998a88654452c996c1638879be839c30a00173adeebbb799fa918c060ef2e47ed9a52b10dd0336dc6eb82714326fc85f34f2c53ceb07f38a41dfc2a30663a24a8ac02415895781717b32a5518a8ea878e93a6933688886e819b6f53b79d774daaece9c1956351a6dfe87afeb2777d91fe567960abea5e8a9d2f6403fc6e63c89ec503a5e8a5f877b57985156eb8574a0155bb239ffcde1425a4863377563effe103b3fda420f4a613e0d551491eafeef2d4e5634d840224702d319bf264e28484d1146cc8c8e3af6d31928e54999bf45ad5cc8def69a061e6a5d198254b07230c12e087ba551e5314bdec4757427db28f83db8fc8d929e48c4974e5da3ce0fcae913f63e580e84f2009685176b06f9add929267c4828e8ad2c73304b919bcc91eb928f7a878a8c106ddda8749f5ce56d94e4292b1a7c25418a1680ecdb40913c8000589308205853082036da0030201020214
(3) Message-Authenticator = 0x00000000000000000000000000000000
(3) State = 0x2a019a2d2905976172f171851926dbf8
(3) Finished request
Waking up in 9.9 seconds.
(4) Received Access-Request Id 177 from 192.168.4.253:1812 to 192.168.4.160:1812 length 173
(4) NAS-IP-Address = 192.168.4.253
(4) NAS-Port = 50002
(4) NAS-Port-Type = Ethernet
(4) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(4) Called-Station-Id = "00-21-1C-EA-37-42"
(4) Calling-Station-Id = "00-13-3B-A0-43-3E"
(4) Service-Type = Framed-User
(4) Framed-MTU = 1500
(4) State = 0x2a019a2d2905976172f171851926dbf8
(4) EAP-Message = 0x020400060d00
(4) Message-Authenticator = 0x59860564389662c6f35e69fcc49af4ab
(4) Restoring &session-state
(4) &session-state:Framed-MTU = 994
(4) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(4) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(4) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(4) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(4) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(4) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(4) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(4) authorize {
(4) eap: Peer sent EAP Response (code 2) ID 4 length 6
(4) eap: Continuing tunnel setup
(4) [eap] = ok
(4) } # authorize = ok
(4) Found Auth-Type = EAP
(4) # Executing group from file /opt/radiusd/lib/radiusd.ini
(4) Auth-Type EAP {
(4) eap: Expiring EAP session with state 0x2a019a2d29059761
(4) eap: Finished EAP session with state 0x2a019a2d29059761
(4) eap: Previous EAP request found for state 0x2a019a2d29059761, released from the list
(4) eap: Peer sent packet with method EAP TLS (13)
(4) eap: Calling submodule eap_tls to process data
(4) eap_tls: (TLS) Peer ACKed our handshake fragment
(4) eap: Sending EAP Request (code 1) ID 5 length 1004
(4) eap: EAP session adding &reply:State = 0x2a019a2d2e049761
(4) [eap] = handled
(4) } # Auth-Type EAP = handled
(4) Using Post-Auth-Type Challenge
(4) Post-Auth-Type sub-section not found. Ignoring.
(4) session-state: Saving cached attributes
(4) Framed-MTU = 994
(4) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(4) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(4) Sent Access-Challenge Id 177 from 192.168.4.160:1812 to 192.168.4.253:1812 length 1068
(4) EAP-Message = 0x010503ec0dc000000cb30f002062e83091a12eb1cb6c0b967dd3b1b83533e17ddd8ab58bdd705e30150f3d451d3c15cec13ba5a462a105aa86b908319b0101fbd639e092f88b85177fd3ad65f0a0934c8101798b1e615f55940e707d5d990317e1b5d05dd3e88be78b5218c2312df11648a708b2c5a178681fec0ae7529b2527604fa0a6991d8e917c668020aeb9977f1ce1a3ba5cc8bd0203010001a35d305b301d0603551d0e04160414624a8c17527066792347a4bad2c98423d4783fde301f0603551d23041830168014624a8c17527066792347a4bad2c98423d4783fde300c0603551d13040530030101ff300b0603551d0f040403020186300d06092a864886f70d01010b05000382020100a22c1eb20b596c930477214c2a2a3a7f83b49cbfbe765f787cc5c87fa133ffd03a78ea1d8ea5965bacfccf96fedd63a2e26f2beefb50d92700128507aae4304057fc110e3382496f6d8d048ffda9d930dbd7a375800e20accc6d8c83296d344e3315b8ba5e61676e
(4) Message-Authenticator = 0x00000000000000000000000000000000
(4) State = 0x2a019a2d2e04976172f171851926dbf8
(4) Finished request
Waking up in 9.9 seconds.
(5) Received Access-Request Id 178 from 192.168.4.253:1812 to 192.168.4.160:1812 length 173
(5) NAS-IP-Address = 192.168.4.253
(5) NAS-Port = 50002
(5) NAS-Port-Type = Ethernet
(5) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(5) Called-Station-Id = "00-21-1C-EA-37-42"
(5) Calling-Station-Id = "00-13-3B-A0-43-3E"
(5) Service-Type = Framed-User
(5) Framed-MTU = 1500
(5) State = 0x2a019a2d2e04976172f171851926dbf8
(5) EAP-Message = 0x020500060d00
(5) Message-Authenticator = 0x21398d5fd30706f8857b51fd3ee7ea0d
(5) Restoring &session-state
(5) &session-state:Framed-MTU = 994
(5) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(5) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(5) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(5) authorize {
(5) eap: Peer sent EAP Response (code 2) ID 5 length 6
(5) eap: Continuing tunnel setup
(5) [eap] = ok
(5) } # authorize = ok
(5) Found Auth-Type = EAP
(5) # Executing group from file /opt/radiusd/lib/radiusd.ini
(5) Auth-Type EAP {
(5) eap: Expiring EAP session with state 0x2a019a2d2e049761
(5) eap: Finished EAP session with state 0x2a019a2d2e049761
(5) eap: Previous EAP request found for state 0x2a019a2d2e049761, released from the list
(5) eap: Peer sent packet with method EAP TLS (13)
(5) eap: Calling submodule eap_tls to process data
(5) eap_tls: (TLS) Peer ACKed our handshake fragment
(5) eap: Sending EAP Request (code 1) ID 6 length 279
(5) eap: EAP session adding &reply:State = 0x2a019a2d2f079761
(5) [eap] = handled
(5) } # Auth-Type EAP = handled
(5) Using Post-Auth-Type Challenge
(5) Post-Auth-Type sub-section not found. Ignoring.
(5) session-state: Saving cached attributes
(5) Framed-MTU = 994
(5) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(5) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(5) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(5) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(5) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(5) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(5) Sent Access-Challenge Id 178 from 192.168.4.160:1812 to 192.168.4.253:1812 length 339
(5) EAP-Message = 0x010601170d8000000cb3e5c5a1a7ee59b56934c4592faba1840501006c799ebd2af51f07c58bbcec8894627f5fc8e35030611df99af24cb7ac8e963c6a1c24781cc62a7999c7058b25ccef7f1976583df3cf0355a4bd8dab1e57f87ba6f67f46df093a8f8badebba21dd02d5692fa84e0ab39655dc92ce13edb1463519715b160303008a0d00008603010240002e040305030603080708080809080a080b0804080508060401050106010303020303010201030202020402050206020050004e304c3117301506035504030c0e52434465767320526f6f74204341310b3009060355040b0c02434131173015060355040a0c0e52434465767320537570706f7274310b3009060355040613024c5516030300040e000000
(5) Message-Authenticator = 0x00000000000000000000000000000000
(5) State = 0x2a019a2d2f07976172f171851926dbf8
(5) Finished request
Waking up in 9.9 seconds.
(6) Received Access-Request Id 179 from 192.168.4.253:1812 to 192.168.4.160:1812 length 1669
(6) NAS-IP-Address = 192.168.4.253
(6) NAS-Port = 50002
(6) NAS-Port-Type = Ethernet
(6) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(6) Called-Station-Id = "00-21-1C-EA-37-42"
(6) Calling-Station-Id = "00-13-3B-A0-43-3E"
(6) Service-Type = Framed-User
(6) Framed-MTU = 1500
(6) State = 0x2a019a2d2f07976172f171851926dbf8
(6) EAP-Message = 0x020605d40dc0000006c6160303068e0b00053c000539000536308205323082031aa003020102021100d9cd10deb891f2698216842aaae5cc53300d06092a864886f70d01010b0500304c3117301506035504030c0e52434465767320526f6f74204341310b3009060355040b0c02434131173015060355040a0c0e52434465767320537570706f7274310b3009060355040613024c55301e170d3233303931383136303030395a170d3234303931373136303030395a3070312b302906035504030c224445534b544f502d41364d4c584a4f2e737570706f72742e7263646576732e636f6d310f300d060355040d0c06434c49454e5431173015060355040a0c0e52434465767320537570706f72743117301506035504610c0e5641544c552d303030303030303030820122300d06092a864886f70d01010105000382010f003082010a0282010100cab994b6c25bd1e731496149f4c710b0b6b4d79201e9670b08da8333c30d884dea13d9a12fbce5aba4ddc9325413
(6) Message-Authenticator = 0x5caf5e6d061691584c9093801846c341
(6) Restoring &session-state
(6) &session-state:Framed-MTU = 994
(6) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(6) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(6) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(6) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(6) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(6) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(6) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(6) authorize {
(6) eap: Peer sent EAP Response (code 2) ID 6 length 1492
(6) eap: Continuing tunnel setup
(6) [eap] = ok
(6) } # authorize = ok
(6) Found Auth-Type = EAP
(6) # Executing group from file /opt/radiusd/lib/radiusd.ini
(6) Auth-Type EAP {
(6) eap: Expiring EAP session with state 0x2a019a2d2f079761
(6) eap: Finished EAP session with state 0x2a019a2d2f079761
(6) eap: Previous EAP request found for state 0x2a019a2d2f079761, released from the list
(6) eap: Peer sent packet with method EAP TLS (13)
(6) eap: Calling submodule eap_tls to process data
(6) eap_tls: (TLS) EAP Peer says that the final record size will be 1734 bytes
(6) eap_tls: (TLS) EAP Expecting 2 fragments
(6) eap_tls: (TLS) EAP Got first TLS fragment (1482 bytes). Peer says more fragments will follow
(6) eap_tls: (TLS) EAP ACKing fragment, the peer should send more data.
(6) eap: Sending EAP Request (code 1) ID 7 length 6
(6) eap: EAP session adding &reply:State = 0x2a019a2d2c069761
(6) [eap] = handled
(6) } # Auth-Type EAP = handled
(6) Using Post-Auth-Type Challenge
(6) Post-Auth-Type sub-section not found. Ignoring.
(6) session-state: Saving cached attributes
(6) Framed-MTU = 994
(6) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(6) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(6) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(6) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(6) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(6) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(6) Sent Access-Challenge Id 179 from 192.168.4.160:1812 to 192.168.4.253:1812 length 64
(6) EAP-Message = 0x010700060d00
(6) Message-Authenticator = 0x00000000000000000000000000000000
(6) State = 0x2a019a2d2c06976172f171851926dbf8
(6) Finished request
Waking up in 9.8 seconds.
(7) Received Access-Request Id 180 from 192.168.4.253:1812 to 192.168.4.160:1812 length 427
(7) NAS-IP-Address = 192.168.4.253
(7) NAS-Port = 50002
(7) NAS-Port-Type = Ethernet
(7) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(7) Called-Station-Id = "00-21-1C-EA-37-42"
(7) Calling-Station-Id = "00-13-3B-A0-43-3E"
(7) Service-Type = Framed-User
(7) Framed-MTU = 1500
(7) State = 0x2a019a2d2c06976172f171851926dbf8
(7) EAP-Message = 0x020701020d00e20d42035e93afe672c521d5bb19182b78d8a423c7e3c4ce4c8b84b0445c61a4b95dbc602b073b22e94172f913a6ae52d8e814541d3e32b067c0528857bd7f7482f26336bae8a6a3bed36b1c4d5a188101285e04bdcfdea91d3e6016d13bafc21446dd121ca05a66bb5b2cfe3c1335acf1c0dff48052e5fb9dc05fce35a465556a4faeef953d05539b49336936c947f39f179117595b294c77841648c3c3f460b02836c75c90b6906beb80c8b0a5a23288bee6bc2e7261607fec5f1d5e6cbaf2d1415904d5f7b9c40314030300010116030300280000000000000000b61d36cfd271d2aad5f50759b78f5ac89ed66c64a97a1198361cdcfe735b2723
(7) Message-Authenticator = 0xd2334d833b7fb6a9701c3c158f17a322
(7) Restoring &session-state
(7) &session-state:Framed-MTU = 994
(7) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(7) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(7) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(7) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(7) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(7) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(7) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(7) authorize {
(7) eap: Peer sent EAP Response (code 2) ID 7 length 258
(7) eap: Continuing tunnel setup
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = EAP
(7) # Executing group from file /opt/radiusd/lib/radiusd.ini
(7) Auth-Type EAP {
(7) eap: Expiring EAP session with state 0x2a019a2d2c069761
(7) eap: Finished EAP session with state 0x2a019a2d2c069761
(7) eap: Previous EAP request found for state 0x2a019a2d2c069761, released from the list
(7) eap: Peer sent packet with method EAP TLS (13)
(7) eap: Calling submodule eap_tls to process data
(7) eap_tls: (TLS) EAP Got final fragment (252 bytes)
(7) eap_tls: (TLS) EAP Done initial handshake
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server done
(7) eap_tls: (TLS) recv TLS 1.2 Handshake, Certificate
(7) eap_tls: (TLS) Creating attributes from server certificate
(7) eap_tls: TLS-Cert-Serial := "5a42eea11d8d1528cd307d761cc682ec4da6aab3"
(7) eap_tls: TLS-Cert-Expiration := "20730829094146Z"
(7) eap_tls: TLS-Cert-Valid-Since := "230911094146Z"
(7) eap_tls: TLS-Cert-Subject := "/CN=RCDevs Root CA/OU=CA/O=RCDevs Support/C=LU"
(7) eap_tls: TLS-Cert-Issuer := "/CN=RCDevs Root CA/OU=CA/O=RCDevs Support/C=LU"
(7) eap_tls: TLS-Cert-Common-Name := "RCDevs Root CA"
(7) eap_tls: (TLS) Creating attributes from client certificate
(7) eap_tls: TLS-Client-Cert-Serial := "d9cd10deb891f2698216842aaae5cc53"
(7) eap_tls: TLS-Client-Cert-Expiration := "240917160009Z"
(7) eap_tls: TLS-Client-Cert-Valid-Since := "230918160009Z"
(7) eap_tls: TLS-Client-Cert-Subject := "/CN=DESKTOP-A6MLXJO.rcdevsdocs.com/description=CLIENT/O=RCDevs Support/organizationIdentifier=VATLU-00000000"
(7) eap_tls: TLS-Client-Cert-Issuer := "/CN=RCDevs Root CA/OU=CA/O=RCDevs Support/C=LU"
(7) eap_tls: TLS-Client-Cert-Common-Name := "DESKTOP-A6MLXJO.rcdevsdocs.com"
(7) eap_tls: TLS-Client-Cert-Subject-Alt-Name-Dns := "DESKTOP-A6MLXJO.rcdevsdocs.com"
(7) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage += "TLS Web Client Authentication"
(7) eap_tls: TLS-Client-Cert-X509v3-Extended-Key-Usage-OID += "1.3.6.1.5.5.7.3.2"
Certificate chain - 1 cert(s) untrusted
(TLS) untrusted certificate with depth [0] subject name /CN=DESKTOP-A6MLXJO.rcdevsdocs.com/description=CLIENT/O=RCDevs Support/organizationIdentifier=VATLU-00000000
(7) eap_tls: Starting OCSP Request
OpenOTP PKI login succeeded
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client certificate
(7) eap_tls: (TLS) recv TLS 1.2 Handshake, ClientKeyExchange
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client key exchange
(7) eap_tls: (TLS) recv TLS 1.2 Handshake, CertificateVerify
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read certificate verify
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read change cipher spec
(7) eap_tls: (TLS) recv TLS 1.2 Handshake, Finished
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read finished
(7) eap_tls: (TLS) send TLS 1.2 ChangeCipherSpec
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write change cipher spec
(7) eap_tls: (TLS) send TLS 1.2 Handshake, Finished
(7) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write finished
(7) eap_tls: (TLS) Handshake state - SSL negotiation finished successfully
(7) eap_tls: (TLS) Connection Established
(7) eap_tls: TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(7) eap_tls: TLS-Session-Version = "TLS 1.2"
(7) eap: Sending EAP Request (code 1) ID 8 length 61
(7) eap: EAP session adding &reply:State = 0x2a019a2d2d099761
(7) [eap] = handled
(7) } # Auth-Type EAP = handled
(7) Using Post-Auth-Type Challenge
(7) Post-Auth-Type sub-section not found. Ignoring.
(7) session-state: Saving cached attributes
(7) Framed-MTU = 994
(7) TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(7) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, Certificate"
(7) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, ClientKeyExchange"
(7) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, CertificateVerify"
(7) TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, Finished"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 ChangeCipherSpec"
(7) TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Finished"
(7) TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(7) TLS-Session-Version = "TLS 1.2"
(7) Sent Access-Challenge Id 180 from 192.168.4.160:1812 to 192.168.4.253:1812 length 119
(7) EAP-Message = 0x0108003d0d800000003314030300010116030300285fefc6a50b9e632a6910d6d47a124bfd5b7219f97268e13965946efe64a58b716614ef531d88b5d9
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) State = 0x2a019a2d2d09976172f171851926dbf8
(7) Finished request
Waking up in 9.8 seconds.
(8) Received Access-Request Id 181 from 192.168.4.253:1812 to 192.168.4.160:1812 length 173
(8) NAS-IP-Address = 192.168.4.253
(8) NAS-Port = 50002
(8) NAS-Port-Type = Ethernet
(8) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(8) Called-Station-Id = "00-21-1C-EA-37-42"
(8) Calling-Station-Id = "00-13-3B-A0-43-3E"
(8) Service-Type = Framed-User
(8) Framed-MTU = 1500
(8) State = 0x2a019a2d2d09976172f171851926dbf8
(8) EAP-Message = 0x020800060d00
(8) Message-Authenticator = 0xee463f6371044aff2ccfedf9e4ee3d8d
(8) Restoring &session-state
(8) &session-state:Framed-MTU = 994
(8) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.3 Handshake, ClientHello"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHello"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Certificate"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerKeyExchange"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, CertificateRequest"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, ServerHelloDone"
(8) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, Certificate"
(8) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, ClientKeyExchange"
(8) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, CertificateVerify"
(8) &session-state:TLS-Session-Information = "(TLS) recv TLS 1.2 Handshake, Finished"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 ChangeCipherSpec"
(8) &session-state:TLS-Session-Information = "(TLS) send TLS 1.2 Handshake, Finished"
(8) &session-state:TLS-Session-Cipher-Suite = "ECDHE-RSA-AES256-GCM-SHA384"
(8) &session-state:TLS-Session-Version = "TLS 1.2"
(8) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(8) authorize {
(8) eap: Peer sent EAP Response (code 2) ID 8 length 6
(8) eap: Continuing tunnel setup
(8) [eap] = ok
(8) } # authorize = ok
(8) Found Auth-Type = EAP
(8) # Executing group from file /opt/radiusd/lib/radiusd.ini
(8) Auth-Type EAP {
(8) eap: Expiring EAP session with state 0x2a019a2d2d099761
(8) eap: Finished EAP session with state 0x2a019a2d2d099761
(8) eap: Previous EAP request found for state 0x2a019a2d2d099761, released from the list
(8) eap: Peer sent packet with method EAP TLS (13)
(8) eap: Calling submodule eap_tls to process data
(8) eap_tls: (TLS) Peer ACKed our handshake fragment. handshake is finished
(8) eap: Sending EAP Success (code 3) ID 8 length 4
(8) eap: Freeing handler
(8) [eap] = ok
(8) } # Auth-Type EAP = ok
(8) Login OK: [host/DESKTOP-A6MLXJO.rcdevsdocs.com] (from client any port 50002 cli 00-13-3B-A0-43-3E)
(8) Sent Access-Accept Id 181 from 192.168.4.160:1812 to 192.168.4.253:1812 length 201
(8) MS-MPPE-Recv-Key = 0xec58342777317bb961c9ef3ff7f396221acaf7b1714eb5c1fd558878ae69267b
(8) MS-MPPE-Send-Key = 0x00af4187cd99abeb6966d121d9b4c188e529ddcfe919bf4a420242cc58ab4b08
(8) EAP-Message = 0x03080004
(8) Message-Authenticator = 0x00000000000000000000000000000000
(8) User-Name = "host/DESKTOP-A6MLXJO.rcdevsdocs.com"
(8) Finished request
Waking up in 9.8 seconds.
You are now authenticated on your switch.
macOS / iOS
User certificate based authentication
In macOS, open the downloaded user certificate to install it into the keychain. Input the password which protect the p12 bundle.
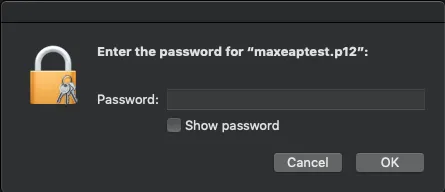
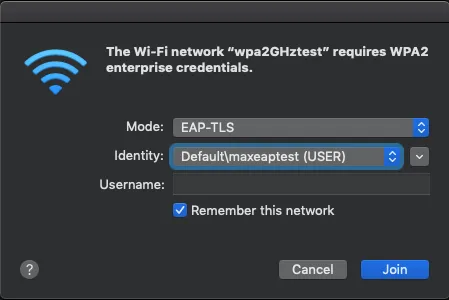
Once my certificate has been issued and imported in my keychain, I can use it for EAP-TLS authentication.
Found below, the description of the certificate that I will use for that test authentication :
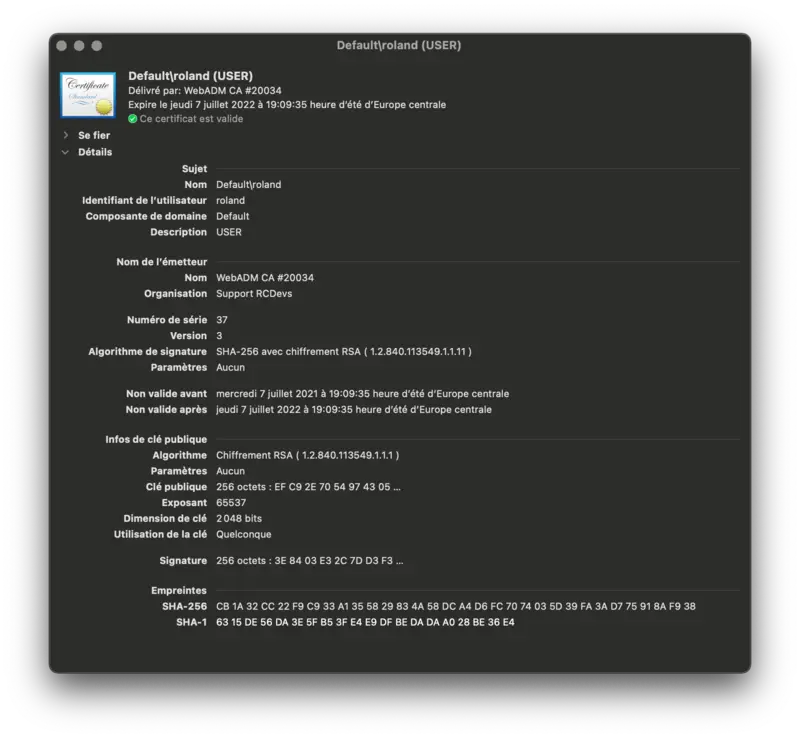
I click to connect on the Wi-Fi I configured in EAP-TLS and prompted to select the mode and the identity I want to use for the login. I choose EAP-TLS (else EAP-TTLS is involved) and the Identity (Roland)
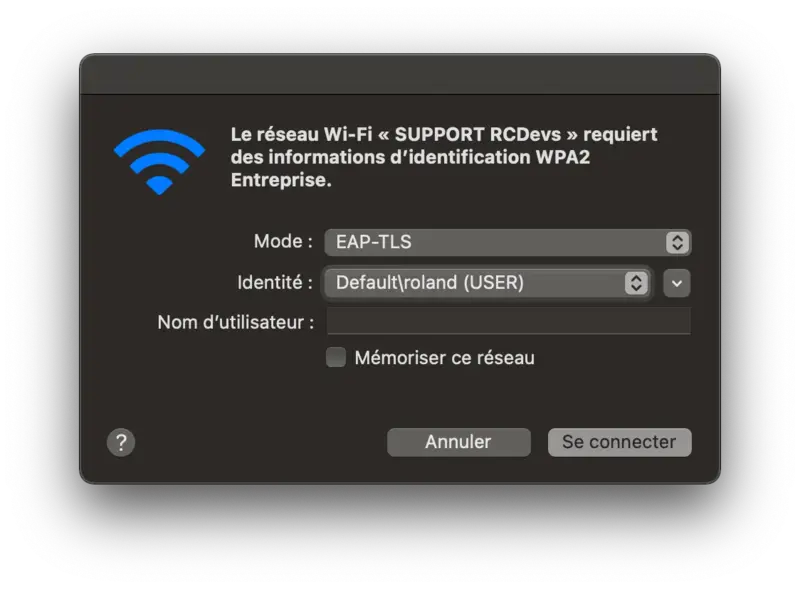
Then click Connect and few seconds after, you are connected to the Wi-Fi.
See below, the EAP-TLS debug logs from Radius Bridge:
(0) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 141
(0) User-Name = "Default\\roland"
(0) NAS-IP-Address = 192.168.4.250
(0) Called-Station-Id = "586d8fa0308d"
(0) Calling-Station-Id = "f40f2423e0c7"
(0) NAS-Identifier = "586d8fa0308d"
(0) NAS-Port = 4
(0) Framed-MTU = 1400
(0) NAS-Port-Type = Wireless-802.11
(0) EAP-Message = 0x020000130144656661756c745c726f6c616e64
(0) Message-Authenticator = 0x8cb30e6eb5c035d76b6a48ea62d0eba7
(0) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(0) authorize {
(0) eap: Peer sent EAP Response (code 2) ID 0 length 19
(0) eap: Continuing tunnel setup
(0) [eap] = ok
(0) } # authorize = ok
(0) Found Auth-Type = EAP
(0) # Executing group from file /opt/radiusd/lib/radiusd.ini
(0) Auth-Type EAP {
(0) eap: Peer sent packet with method EAP Identity (1)
(0) eap: Calling submodule eap_ttls to process data
(0) eap_ttls: (TLS) Initiating new session
(0) eap: Sending EAP Request (code 1) ID 1 length 6
(0) eap: EAP session adding &reply:State = 0xd85aceebd85bdb18
(0) [eap] = handled
(0) } # Auth-Type EAP = handled
(0) Using Post-Auth-Type Challenge
(0) Post-Auth-Type sub-section not found. Ignoring.
(0) session-state: Saving cached attributes
(0) Framed-MTU = 994
(0) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(0) EAP-Message = 0x010100061520
(0) Message-Authenticator = 0x00000000000000000000000000000000
(0) State = 0xd85aceebd85bdb18ad985fadddd9ba17
(0) Finished request
Waking up in 9.9 seconds.
(0) Cleaning up request packet ID 0 with timestamp +742
(1) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 146
(1) User-Name = "Default\\roland"
(1) NAS-IP-Address = 192.168.4.250
(1) Called-Station-Id = "586d8fa0308d"
(1) Calling-Station-Id = "f40f2423e0c7"
(1) NAS-Identifier = "586d8fa0308d"
(1) NAS-Port = 4
(1) Framed-MTU = 1400
(1) State = 0xd85aceebd85bdb18ad985fadddd9ba17
(1) NAS-Port-Type = Wireless-802.11
(1) EAP-Message = 0x02010006030d
(1) Message-Authenticator = 0x73cf20651a33a0e2a9bbb615311673c7
(1) Restoring &session-state
(1) &session-state:Framed-MTU = 994
(1) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(1) authorize {
(1) eap: Peer sent EAP Response (code 2) ID 1 length 6
(1) eap: Continuing tunnel setup
(1) [eap] = ok
(1) } # authorize = ok
(1) Found Auth-Type = EAP
(1) # Executing group from file /opt/radiusd/lib/radiusd.ini
(1) Auth-Type EAP {
(1) eap: Expiring EAP session with state 0xd85aceebd85bdb18
(1) eap: Finished EAP session with state 0xd85aceebd85bdb18
(1) eap: Previous EAP request found for state 0xd85aceebd85bdb18, released from the list
(1) eap: Peer sent packet with method EAP NAK (3)
(1) eap: Found mutually acceptable type TLS (13)
(1) eap: Calling submodule eap_tls to process data
(1) eap_tls: (TLS) Initiating new session
(1) eap_tls: (TLS) Setting verify mode to require certificate from client
(1) eap: Sending EAP Request (code 1) ID 2 length 6
(1) eap: EAP session adding &reply:State = 0xd85aceebd958c318
(1) [eap] = handled
(1) } # Auth-Type EAP = handled
(1) Using Post-Auth-Type Challenge
(1) Post-Auth-Type sub-section not found. Ignoring.
(1) session-state: Saving cached attributes
(1) Framed-MTU = 994
(1) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(1) EAP-Message = 0x010200060d20
(1) Message-Authenticator = 0x00000000000000000000000000000000
(1) State = 0xd85aceebd958c318ad985fadddd9ba17
(1) Finished request
Waking up in 9.9 seconds.
(1) Cleaning up request packet ID 0 with timestamp +742
(2) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 301
(2) User-Name = "Default\\roland"
(2) NAS-IP-Address = 192.168.4.250
(2) Called-Station-Id = "586d8fa0308d"
(2) Calling-Station-Id = "f40f2423e0c7"
(2) NAS-Identifier = "586d8fa0308d"
(2) NAS-Port = 4
(2) Framed-MTU = 1400
(2) State = 0xd85aceebd958c318ad985fadddd9ba17
(2) NAS-Port-Type = Wireless-802.11
(2) EAP-Message = 0x020200a10d800000009716030100920100008e030360e5e1d43c1356e4e327db12aa19c43cbf67a94d1177b40bf2daf0bd0cabe51d00002c00ffc02cc02bc024c023c00ac009c008c030c02fc028c027c014c013c012009d009c003d003c0035002f000a01000039000a00080006001700180019000b00020100000d00120010040102010501060104030203050306030005000501000000000012000000170000
(2) Message-Authenticator = 0xde2398f23b590bdec148204f601493a4
(2) Restoring &session-state
(2) &session-state:Framed-MTU = 994
(2) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(2) authorize {
(2) eap: Peer sent EAP Response (code 2) ID 2 length 161
(2) eap: Continuing tunnel setup
(2) [eap] = ok
(2) } # authorize = ok
(2) Found Auth-Type = EAP
(2) # Executing group from file /opt/radiusd/lib/radiusd.ini
(2) Auth-Type EAP {
(2) eap: Expiring EAP session with state 0xd85aceebd958c318
(2) eap: Finished EAP session with state 0xd85aceebd958c318
(2) eap: Previous EAP request found for state 0xd85aceebd958c318, released from the list
(2) eap: Peer sent packet with method EAP TLS (13)
(2) eap: Calling submodule eap_tls to process data
(2) eap_tls: (TLS) EAP Peer says that the final record size will be 151 bytes
(2) eap_tls: (TLS) EAP Got all data (151 bytes)
(2) eap_tls: (TLS) Handshake state - before SSL initialization
(2) eap_tls: (TLS) Handshake state - Server before SSL initialization
(2) eap_tls: (TLS) Handshake state - Server before SSL initialization
(2) eap_tls: (TLS) recv TLS 1.3 Handshake, ClientHello
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client hello
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerHello
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server hello
(2) eap_tls: (TLS) send TLS 1.2 Handshake, Certificate
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write certificate
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerKeyExchange
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write key exchange
(2) eap_tls: (TLS) send TLS 1.2 Handshake, CertificateRequest
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write certificate request
(2) eap_tls: (TLS) send TLS 1.2 Handshake, ServerHelloDone
(2) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server done
(2) eap_tls: (TLS) Server : Need to read more data: SSLv3/TLS write server done
(2) eap_tls: (TLS) In Handshake Phase
(2) eap: Sending EAP Request (code 1) ID 3 length 1004
(2) eap: EAP session adding &reply:State = 0xd85aceebda59c318
(2) [eap] = handled
(2) } # Auth-Type EAP = handled
(2) Using Post-Auth-Type Challenge
(2) Post-Auth-Type sub-section not found. Ignoring.
(2) session-state: Saving cached attributes
(2) Framed-MTU = 994
(2) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(2) EAP-Message = 0x010303ec0dc0000008ee160303003d0200003903033b6d140fdc958c73e51eb3c0cfbaea24f5211392e6b896fd4c1ecd848d1faea100c030000011ff01000100000b0004030001020017000016030306780b00067400067100031f3082031b30820203a003020102020124300d06092a864886f70d01010b050030343119301706035504030c1057656241444d2043412023323030333431173015060355040a0c0e537570706f727420524344657673301e170d3231303730363134333532335a170d3331303730343134333532335a30363123302106035504030c1a77656261646d312e737570706f72742e7263646576732e636f6d310f300d060355040d0c0653455256455230820122300d06092a864886f70d01010105000382010f003082010a0282010100d8eef68cdb1de59fde76ca30c1fe481978f1827071b3bbcc1b79ed1ab6226af1ae161ec04fe3f859a70f1111ef4373e7a184c003b2ceaec3ba75cfea74937589a2a954e554184a38c9f930165894
(2) Message-Authenticator = 0x00000000000000000000000000000000
(2) State = 0xd85aceebda59c318ad985fadddd9ba17
(2) Finished request
Waking up in 9.9 seconds.
(2) Cleaning up request packet ID 0 with timestamp +742
(3) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 146
(3) User-Name = "Default\\roland"
(3) NAS-IP-Address = 192.168.4.250
(3) Called-Station-Id = "586d8fa0308d"
(3) Calling-Station-Id = "f40f2423e0c7"
(3) NAS-Identifier = "586d8fa0308d"
(3) NAS-Port = 4
(3) Framed-MTU = 1400
(3) State = 0xd85aceebda59c318ad985fadddd9ba17
(3) NAS-Port-Type = Wireless-802.11
(3) EAP-Message = 0x020300060d00
(3) Message-Authenticator = 0x645a819abd55681138a46984c41a7c9f
(3) Restoring &session-state
(3) &session-state:Framed-MTU = 994
(3) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(3) authorize {
(3) eap: Peer sent EAP Response (code 2) ID 3 length 6
(3) eap: Continuing tunnel setup
(3) [eap] = ok
(3) } # authorize = ok
(3) Found Auth-Type = EAP
(3) # Executing group from file /opt/radiusd/lib/radiusd.ini
(3) Auth-Type EAP {
(3) eap: Expiring EAP session with state 0xd85aceebda59c318
(3) eap: Finished EAP session with state 0xd85aceebda59c318
(3) eap: Previous EAP request found for state 0xd85aceebda59c318, released from the list
(3) eap: Peer sent packet with method EAP TLS (13)
(3) eap: Calling submodule eap_tls to process data
(3) eap_tls: (TLS) Peer ACKed our handshake fragment
(3) eap: Sending EAP Request (code 1) ID 4 length 1004
(3) eap: EAP session adding &reply:State = 0xd85aceebdb5ec318
(3) [eap] = handled
(3) } # Auth-Type EAP = handled
(3) Using Post-Auth-Type Challenge
(3) Post-Auth-Type sub-section not found. Ignoring.
(3) session-state: Saving cached attributes
(3) Framed-MTU = 994
(3) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(3) EAP-Message = 0x010403ec0dc0000008ee3432363133303134395a180f32303731303431343133303134395a30343119301706035504030c1057656241444d2043412023323030333431173015060355040a0c0e537570706f72742052434465767330820122300d06092a864886f70d01010105000382010f003082010a0282010100bc70ce477f16c6d1d8de5aa815a65b0c056a1360ebe515c71ef751cb02873d32390ede8c20209af0c0631939715e0983a255716a6e5e619a46f0a84aa44d50ce6e4f6d1af231e8a13361a5ac19f5366d684c841728443dddb7daf530d310e7846ad1d7e014db486f06e54049167ee0da80644122c345405048d94954b59e9ba0755a415ddc1ce8e560d1e9f960442994e0008fed73122d18a4c81c8f2159d524bfe90e3412c1f29b957eb5e39fe97de86516a4b9ba8a4e0c754a759825517d848191508c76cb0f046ddc13660f28e7ae1bdb93b34ad1fd2d0043356f8cd4bf2937405ba1cae9207406a01c940ae7e0f48cbeeb75cdb7e2f7a30701
(3) Message-Authenticator = 0x00000000000000000000000000000000
(3) State = 0xd85aceebdb5ec318ad985fadddd9ba17
(3) Finished request
Waking up in 9.9 seconds.
(3) Cleaning up request packet ID 0 with timestamp +742
(4) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 146
(4) User-Name = "Default\\roland"
(4) NAS-IP-Address = 192.168.4.250
(4) Called-Station-Id = "586d8fa0308d"
(4) Calling-Station-Id = "f40f2423e0c7"
(4) NAS-Identifier = "586d8fa0308d"
(4) NAS-Port = 4
(4) Framed-MTU = 1400
(4) State = 0xd85aceebdb5ec318ad985fadddd9ba17
(4) NAS-Port-Type = Wireless-802.11
(4) EAP-Message = 0x020400060d00
(4) Message-Authenticator = 0x32dbe7446a81c8eb2cb17ef766684480
(4) Restoring &session-state
(4) &session-state:Framed-MTU = 994
(4) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(4) authorize {
(4) eap: Peer sent EAP Response (code 2) ID 4 length 6
(4) eap: Continuing tunnel setup
(4) [eap] = ok
(4) } # authorize = ok
(4) Found Auth-Type = EAP
(4) # Executing group from file /opt/radiusd/lib/radiusd.ini
(4) Auth-Type EAP {
(4) eap: Expiring EAP session with state 0xd85aceebdb5ec318
(4) eap: Finished EAP session with state 0xd85aceebdb5ec318
(4) eap: Previous EAP request found for state 0xd85aceebdb5ec318, released from the list
(4) eap: Peer sent packet with method EAP TLS (13)
(4) eap: Calling submodule eap_tls to process data
(4) eap_tls: (TLS) Peer ACKed our handshake fragment
(4) eap: Sending EAP Request (code 1) ID 5 length 308
(4) eap: EAP session adding &reply:State = 0xd85aceebdc5fc318
(4) [eap] = handled
(4) } # Auth-Type EAP = handled
(4) Using Post-Auth-Type Challenge
(4) Post-Auth-Type sub-section not found. Ignoring.
(4) session-state: Saving cached attributes
(4) Framed-MTU = 994
(4) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(4) EAP-Message = 0x010501340d80000008eeee8e2601ae3f80448a3fcc7735c5a67670614d68290275e0b7762b5af9b6d3d2afda3b76173b775872e5338c7a7950446eb9c0f5de58b727a66d22d64cc2ebea3c28b876fd197094340b895a1016030300cf0d0000cb03010240002e040305030603080708080809080a080b0804080508060401050106010303020303010201030202020402050206020095003630343119301706035504030c1057656241444d2043412023323030333431173015060355040a0c0e537570706f727420524344657673005b305931133011060a0992268993f22c6401191603636f6d31163014060a0992268993f22c640119160672636465767331173015060a0992268993f22c6401191607737570706f72743111300f06035504031308535550434141443216030300040e000000
(4) Message-Authenticator = 0x00000000000000000000000000000000
(4) State = 0xd85aceebdc5fc318ad985fadddd9ba17
(4) Finished request
Waking up in 9.9 seconds.
(4) Cleaning up request packet ID 0 with timestamp +742
(5) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 1426
(5) User-Name = "Default\\roland"
(5) NAS-IP-Address = 192.168.4.250
(5) Called-Station-Id = "586d8fa0308d"
(5) Calling-Station-Id = "f40f2423e0c7"
(5) NAS-Identifier = "586d8fa0308d"
(5) NAS-Port = 4
(5) Framed-MTU = 1400
(5) State = 0xd85aceebdc5fc318ad985fadddd9ba17
(5) NAS-Port-Type = Wireless-802.11
(5) EAP-Message = 0x020504fc0dc0000007f316030306630b00065f00065c00030a30820306308201eea003020102020125300d06092a864886f70d01010b050030343119301706035504030c1057656241444d2043412023323030333431173015060355040a0c0e537570706f727420524344657673301e170d3231303730373137303933355a170d3232303730373137303933355a30593117301506035504030c0e44656661756c745c726f6c616e6431163014060a0992268993f22c6401010c06726f6c616e6431173015060a0992268993f22c640119160744656661756c74310d300b060355040d0c045553455230820122300d06092a864886f70d01010105000382010f003082010a0282010100efc92e7054974305d1ce7d011f5bd66b7abf1561e24cf2c5b744f744bdcd03ed3989b4f73d10bd6ccf7efae3b90f5522ea48e444914f3a7bfbbea91c5fcb47c1a2c7ca97d18ebe2e82603277c19caef42fc89c188d7e65a06f5ce7f1cb95ab327ade9a4a073302b4f0d1922613
(5) Message-Authenticator = 0x0333c9763187fe93e3a60ef5a6432197
(5) Restoring &session-state
(5) &session-state:Framed-MTU = 994
(5) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(5) authorize {
(5) eap: Peer sent EAP Response (code 2) ID 5 length 1276
(5) eap: Continuing tunnel setup
(5) [eap] = ok
(5) } # authorize = ok
(5) Found Auth-Type = EAP
(5) # Executing group from file /opt/radiusd/lib/radiusd.ini
(5) Auth-Type EAP {
(5) eap: Expiring EAP session with state 0xd85aceebdc5fc318
(5) eap: Finished EAP session with state 0xd85aceebdc5fc318
(5) eap: Previous EAP request found for state 0xd85aceebdc5fc318, released from the list
(5) eap: Peer sent packet with method EAP TLS (13)
(5) eap: Calling submodule eap_tls to process data
(5) eap_tls: (TLS) EAP Peer says that the final record size will be 2035 bytes
(5) eap_tls: (TLS) EAP Expecting 2 fragments
(5) eap_tls: (TLS) EAP Got first TLS fragment (1266 bytes). Peer says more fragments will follow
(5) eap_tls: (TLS) EAP ACKing fragment, the peer should send more data.
(5) eap: Sending EAP Request (code 1) ID 6 length 6
(5) eap: EAP session adding &reply:State = 0xd85aceebdd5cc318
(5) [eap] = handled
(5) } # Auth-Type EAP = handled
(5) Using Post-Auth-Type Challenge
(5) Post-Auth-Type sub-section not found. Ignoring.
(5) session-state: Saving cached attributes
(5) Framed-MTU = 994
(5) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(5) EAP-Message = 0x010600060d00
(5) Message-Authenticator = 0x00000000000000000000000000000000
(5) State = 0xd85aceebdd5cc318ad985fadddd9ba17
(5) Finished request
Waking up in 9.9 seconds.
(5) Cleaning up request packet ID 0 with timestamp +749
(6) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 921
(6) User-Name = "Default\\roland"
(6) NAS-IP-Address = 192.168.4.250
(6) Called-Station-Id = "586d8fa0308d"
(6) Calling-Station-Id = "f40f2423e0c7"
(6) NAS-Identifier = "586d8fa0308d"
(6) NAS-Port = 4
(6) Framed-MTU = 1400
(6) State = 0xd85aceebdd5cc318ad985fadddd9ba17
(6) NAS-Port-Type = Wireless-802.11
(6) EAP-Message = 0x020603070d00b7e2f7a30701ef63fcc94b0203010001a350304e301d0603551d0e0416041428a7dc1346e132c0cc1421bd7726117efe230517301f0603551d2304183016801428a7dc1346e132c0cc1421bd7726117efe230517300c0603551d13040530030101ff300d06092a864886f70d01010b050003820101007e332d89c217211c22fd1312ff4e73a2360b93c31038e765b8c065ca820628721642c2ac8ad9b2a5021f6f921563334fd620770013138e53a09dc6e934d71de4948f1b79fbc78dd18a2b99fb9f18d66c5bce44e6128f06deb5412f08a5de70077a9100d0fce9b0881114f97eaed6b8eab2127b1a0c7973c14e292cc9cda9657c9a1c16455537ee77c23a81d500dda5cba5c80795f68a4866554c9df4262a4d6432a7f3d0055ac94a8c9c59a23ff4dd8a2f7812fd5f3910686a89171882549c9f058518a09cf86d59768f4ed48f6800ef97b299b1f5f25d8373d6547ad3a07beabd1aecb62c4888c976d6741dff0d63693aa1b53d928c96515fa738
(6) Message-Authenticator = 0x3a15445e85a724b07397c16d6dcda6bd
(6) Restoring &session-state
(6) &session-state:Framed-MTU = 994
(6) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(6) authorize {
(6) eap: Peer sent EAP Response (code 2) ID 6 length 775
(6) eap: Continuing tunnel setup
(6) [eap] = ok
(6) } # authorize = ok
(6) Found Auth-Type = EAP
(6) # Executing group from file /opt/radiusd/lib/radiusd.ini
(6) Auth-Type EAP {
(6) eap: Expiring EAP session with state 0xd85aceebdd5cc318
(6) eap: Finished EAP session with state 0xd85aceebdd5cc318
(6) eap: Previous EAP request found for state 0xd85aceebdd5cc318, released from the list
(6) eap: Peer sent packet with method EAP TLS (13)
(6) eap: Calling submodule eap_tls to process data
(6) eap_tls: (TLS) EAP Got final fragment (769 bytes)
(6) eap_tls: (TLS) EAP Done initial handshake
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write server done
(6) eap_tls: (TLS) recv TLS 1.2 Handshake, Certificate
(6) eap_tls: (TLS) Creating attributes from server certificate
(6) eap_tls: TLS-Cert-Serial := "0ad37ee93fdbfe67f1115f96850d4495c8da6def"
(6) eap_tls: TLS-Cert-Expiration := "20710414130149Z"
(6) eap_tls: TLS-Cert-Subject := "/CN=WebADM CA #20034/O=Support RCDevs"
(6) eap_tls: TLS-Cert-Issuer := "/CN=WebADM CA #20034/O=Support RCDevs"
(6) eap_tls: TLS-Cert-Common-Name := "WebADM CA #20034"
(6) eap_tls: (TLS) Creating attributes from client certificate
(6) eap_tls: TLS-Client-Cert-Serial := "25"
(6) eap_tls: TLS-Client-Cert-Expiration := "220707170935Z"
(6) eap_tls: TLS-Client-Cert-Subject := "/CN=Default\roland/UID=roland/DC=Default/description=USER"
(6) eap_tls: TLS-Client-Cert-Issuer := "/CN=WebADM CA #20034/O=Support RCDevs"
(6) eap_tls: TLS-Client-Cert-Common-Name := "Default\roland"
(6) eap_tls: Starting OCSP Request
(6) eap_tls: ocsp: Using responder URL "https://192.168.4.160:443/ocsp/?nosig=1&host=192.168.4.250&client=586d8fa0308d&source="
This Update: Jul 7 17:18:19 2021 GMT
(6) eap_tls: ocsp: Cert status: good
(6) eap_tls: ocsp: Certificate is valid
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client certificate
(6) eap_tls: (TLS) recv TLS 1.2 Handshake, ClientKeyExchange
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read client key exchange
(6) eap_tls: (TLS) recv TLS 1.2 Handshake, CertificateVerify
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read certificate verify
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read change cipher spec
(6) eap_tls: (TLS) recv TLS 1.2 Handshake, Finished
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS read finished
(6) eap_tls: (TLS) send TLS 1.2 ChangeCipherSpec
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write change cipher spec
(6) eap_tls: (TLS) send TLS 1.2 Handshake, Finished
(6) eap_tls: (TLS) Handshake state - Server SSLv3/TLS write finished
(6) eap_tls: (TLS) Handshake state - SSL negotiation finished successfully
(6) eap_tls: (TLS) Connection Established
(6) eap: Sending EAP Request (code 1) ID 7 length 61
(6) eap: EAP session adding &reply:State = 0xd85aceebde5dc318
(6) [eap] = handled
(6) } # Auth-Type EAP = handled
(6) Using Post-Auth-Type Challenge
(6) Post-Auth-Type sub-section not found. Ignoring.
(6) session-state: Saving cached attributes
(6) Framed-MTU = 994
(6) Sent Access-Challenge Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(6) EAP-Message = 0x0107003d0d80000000331403030001011603030028f3c248d2faf970c644015b2a2588a7eea20b7925835af5ff921dd609853023c386d99375f4faa7ca
(6) Message-Authenticator = 0x00000000000000000000000000000000
(6) State = 0xd85aceebde5dc318ad985fadddd9ba17
(6) Finished request
Waking up in 9.9 seconds.
(6) Cleaning up request packet ID 0 with timestamp +749
(7) Received Access-Request Id 0 from 192.168.4.250:32768 to 192.168.4.160:1812 length 146
(7) User-Name = "Default\\roland"
(7) NAS-IP-Address = 192.168.4.250
(7) Called-Station-Id = "586d8fa0308d"
(7) Calling-Station-Id = "f40f2423e0c7"
(7) NAS-Identifier = "586d8fa0308d"
(7) NAS-Port = 4
(7) Framed-MTU = 1400
(7) State = 0xd85aceebde5dc318ad985fadddd9ba17
(7) NAS-Port-Type = Wireless-802.11
(7) EAP-Message = 0x020700060d00
(7) Message-Authenticator = 0xa5d3c08d8cc6b9f3daf805483b0c33af
(7) Restoring &session-state
(7) &session-state:Framed-MTU = 994
(7) # Executing section authorize from file /opt/radiusd/lib/radiusd.ini
(7) authorize {
(7) eap: Peer sent EAP Response (code 2) ID 7 length 6
(7) eap: Continuing tunnel setup
(7) [eap] = ok
(7) } # authorize = ok
(7) Found Auth-Type = EAP
(7) # Executing group from file /opt/radiusd/lib/radiusd.ini
(7) Auth-Type EAP {
(7) eap: Expiring EAP session with state 0xd85aceebde5dc318
(7) eap: Finished EAP session with state 0xd85aceebde5dc318
(7) eap: Previous EAP request found for state 0xd85aceebde5dc318, released from the list
(7) eap: Peer sent packet with method EAP TLS (13)
(7) eap: Calling submodule eap_tls to process data
(7) eap_tls: (TLS) Peer ACKed our handshake fragment. handshake is finished
Detected WebADM user certificate (calling OpenOTP)
USER
OpenOTP authentication succeeded
(7) eap: Sending EAP Success (code 3) ID 7 length 4
(7) eap: Freeing handler
(7) [eap] = ok
(7) } # Auth-Type EAP = ok
(7) Login OK: [Default\roland] (from client any port 4 cli f40f2423e0c7)
(7) Sent Access-Accept Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(7) Reply-Message := "Authentication success"
(7) MS-MPPE-Recv-Key = 0xe0d02a4251196b64032224dd80309d68f240db9a2f038e3b70e878f447c16f19
(7) MS-MPPE-Send-Key = 0x13c4f8ae48ca72317a09c42288f80f0ec0cb3f491a0731bb95cf3db9ceda467f
(7) EAP-Message = 0x03070004
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) User-Name = "Default\\roland"
(7) Finished request
Waking up in 9.9 seconds.
You can see at the end of the debug logs the following which confirm the authentication has been done successfully.
(7) Login OK: [Default\roland] (from client any port 4 cli f40f2423e0c7)
(7) Sent Access-Accept Id 0 from 192.168.4.160:1812 to 192.168.4.250:32768 length 0
(7) Reply-Message := "Authentication success"
(7) MS-MPPE-Recv-Key = 0xe0d02a4251196b64032224dd80309d68f240db9a2f038e3b70e878f447c16f19
(7) MS-MPPE-Send-Key = 0x13c4f8ae48ca72317a09c42288f80f0ec0cb3f491a0731bb95cf3db9ceda467f
(7) EAP-Message = 0x03070004
(7) Message-Authenticator = 0x00000000000000000000000000000000
(7) User-Name = "Default\\roland"
Device certificate based authentication
You can copy the p12 bundle previously created on your macOS machine. The CA certificate of WebADM will be needed during for the connection setup and can be downloaded at https://webadm_server_address/cacert.
You must add the CA certificate of WebADM into the System Keychain and the p12 bundle into the System Keychain in order to be shared between the different users available on the same machine.
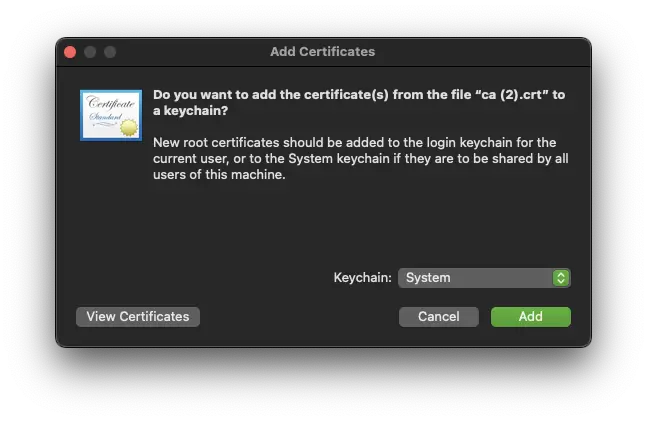
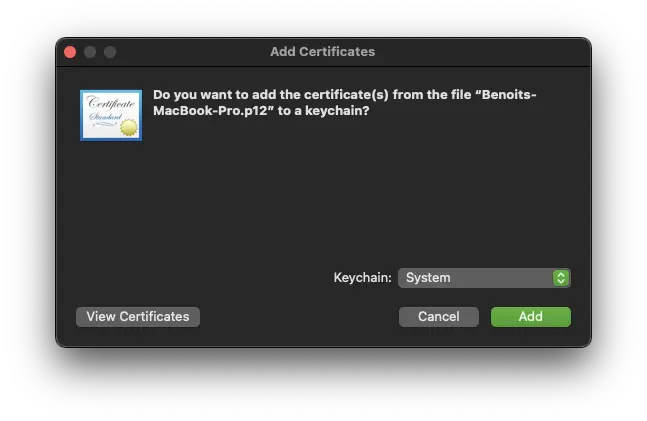
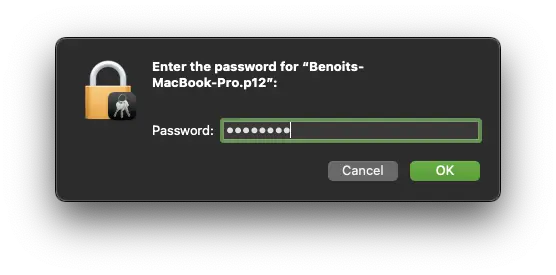
Provide the password which protect the p12 bundle and click Ok:
When you will connect the ethernet cable to your OSX device, the system will prompt you to choose the client certificate. Select the client certificate previously imported. Keep account name and password empty as we are not authenticating the user but the client machine and then press Ok:
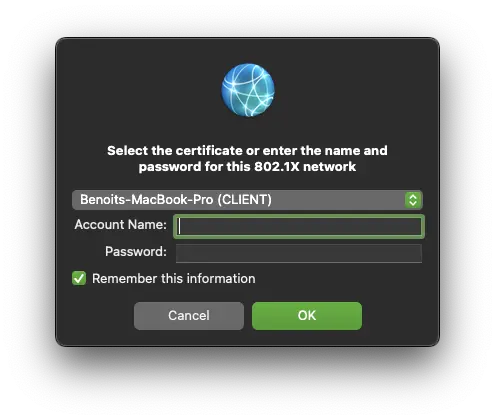
You may be prompted to trust the certificate of the authentication server as below:
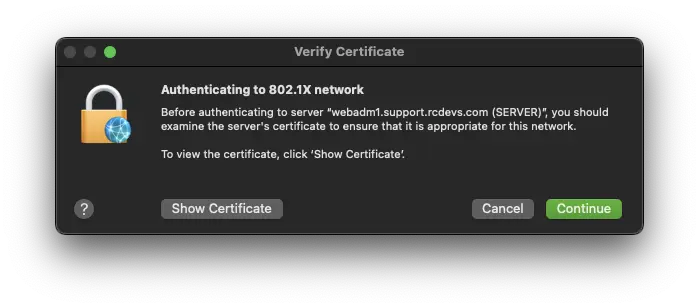
Press Continue and provide the OSX credentials to access the keychain.
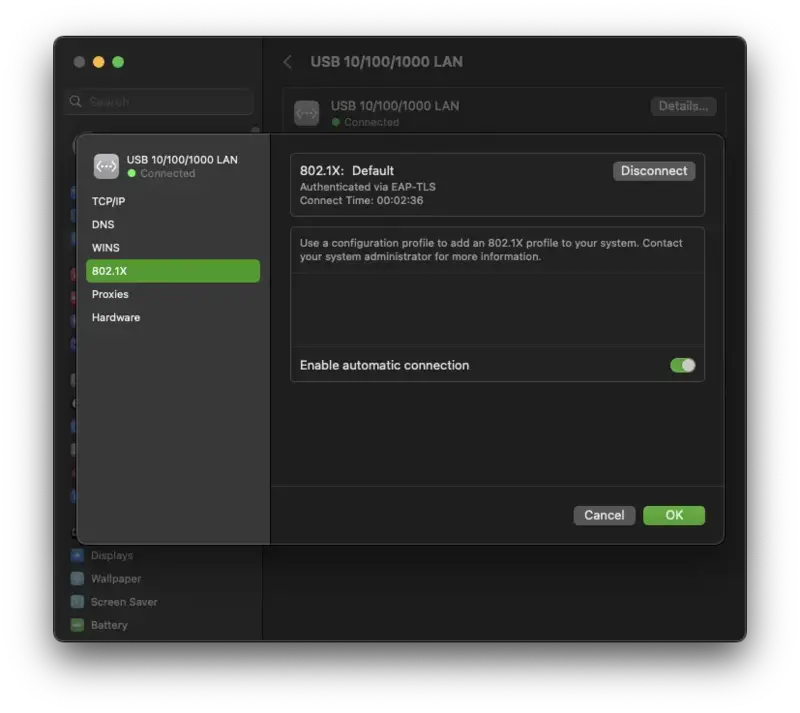
Android
User certificate based authentication
Android has native support of the required protocols, although this might depend on the specific version of Android. First, transfer the downloaded certificate to your phone, and then configure the wireless network.
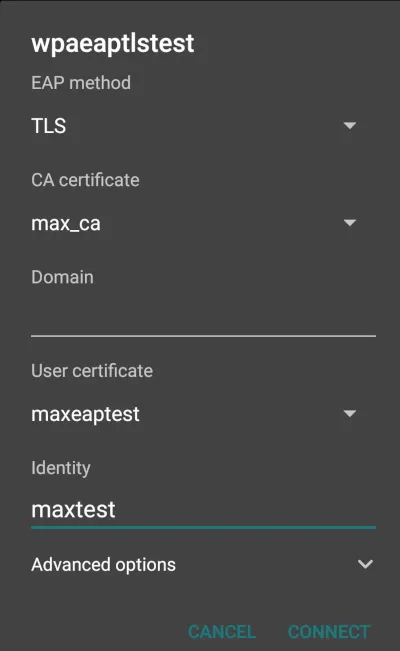
Linux
User certificate based authentication
Most Linux clients also have native support and the connection can be configured graphically. Below is a screenshot of Ubuntu 18.04 Network Manager.
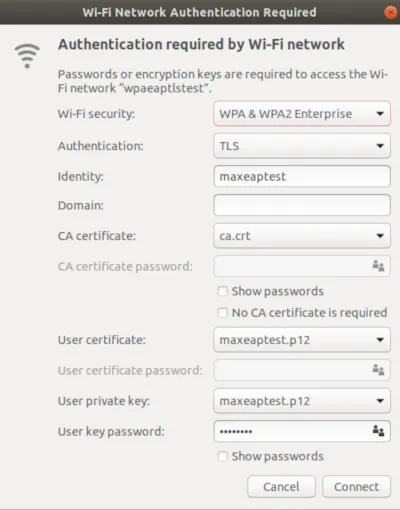
Device certificate based authentication
You can copy the p12 bundle previously created on your Linux machine. The CA certificate of WebADM will be needed during the interface setup and can be downloaded at https://webadm_server_address/cacert.
Navigate to the Network configuration of your Linux machine, then edit the Ethernet interface settings.
Configure it like below:
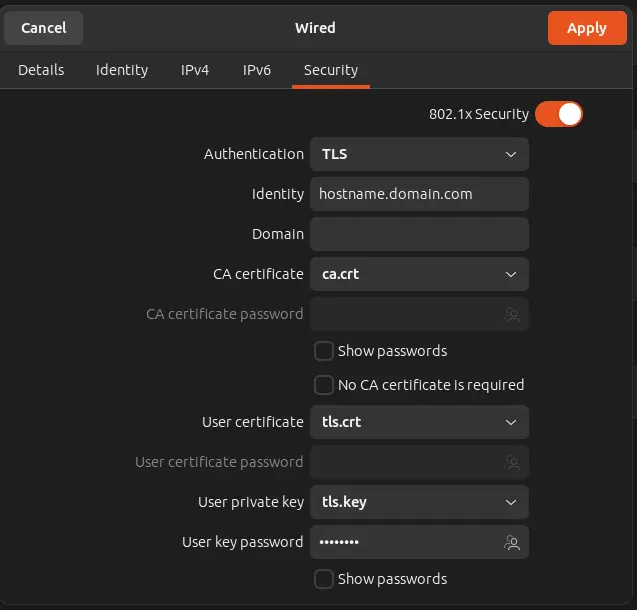
First, enable the 802.1X security setting.
The Identity and Domain settings are optional as information are retrieved from the client certificate that it is going to be used to establish the authentication and the connection.
Configure the CA certificate setting with the CA certificate of your WebADM.
Configure the User certificate and the Private key fields to the certificate p12 bundle previously generated and copied on your Linux machine.
Then, provide the p12 password in the Key password field.
You can click Apply button.
On the Details tab, you can enable the setting Make available to other users if you want to share the network configuration with other users of that computer:
You should be connected to your network after a successfull EAP-TLS authentication:
Certificate-based authentication for custom integrations (API integrations)
OpenOTP provides SOAP API methods that can be integrated wherever you want to authenticate users through user certificate. For OpenOTP to be able to validate the user certificates, you need to respect the following prerequisites:
- The certificate must be stored on the user account in the userCertificate attribute,
- The account must be activated in WebADM,
- The certificate can be issued by WebADM or another PKI, as soon as the certificate is stored on the user account, it can be used to authenticate the user.
Below, the description of the 2 methods which can be used for this purpose.
<!-- PKI Authentication Methods -->
<message name="openotpPKILoginRequest">
<part name="certificate" type="xsd:string"/>
<part name="client" type="xsd:string"/>
<part name="source" type="xsd:string"/>
<part name="settings" type="xsd:string"/>
<part name="options" type="xsd:string"/>
<part name="virtual" type="xsd:string"/>
</message>
<message name="openotpPKILoginResponse">
<part name="code" type="xsd:integer"/>
<part name="error" type="xsd:string"/>
<part name="message" type="xsd:string"/>
<part name="username" type="xsd:string"/>
<part name="domain" type="xsd:string"/>
<part name="data" type="xsd:string"/>
</message>
In that documentation, I use the SOAPUI tool to test a certificate-based authentication. What is performed by SOAPUI must be implemented on the client system you want to enable certificate-based authentication. For e.g, if you want to enable certificate-based authentication on your intranet, you must implement SOAP calls on your intranet web server and configure the login page of your intranet website to ask the users for their certificate. When the user will access the intranet through his web browser, he will have to provide the certificate issued for this purpose. The certificate will be passed through the users' web browser to your website and your website must fill in the user certificate into the certificate parameter of the SOAP API PKI authentication method. The certificate must be filled to the SOAP API in PEM format.
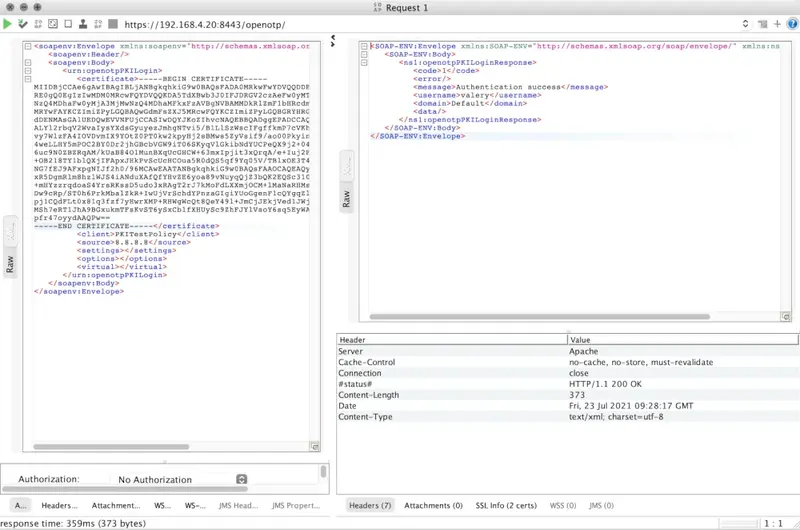
Below, the OpenOTP logs for that authentication.
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] New openotpPKILogin SOAP request
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] > Certificate: Default\valery (46)
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] > Client ID: PKITestPolicy
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] > Source IP: 192.168.4.200
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Registered openotpPKILogin request
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Resolved LDAP user: CN=valery,OU=SUPAdmins,DC=rcdevsdocs,DC=com (cached)
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Resolved source location: US
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Started transaction lock for user
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Found user fullname: valery
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Found 10 user settings: EnableLogin=Yes
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Updated user data
[2021-07-23 11:29:29] [10.2.3.6:58127] [OpenOTP:JXU40VZX] Sent login success response
As you can see in the logs, the authentication is a success.
If I remove the certificate from the user account, then the authentication is immediately rejected.
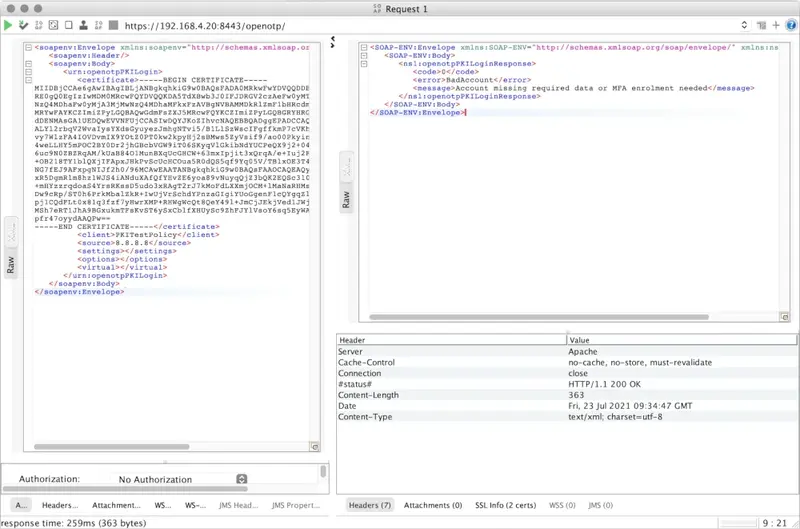
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] New openotpPKILogin SOAP request
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] > Certificate: Default\valery (46)
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] > Client ID: PKITestPolicy
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] > Source IP: 192.168.4.200
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Registered openotpPKILogin request
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Resolved LDAP user: CN=valery,OU=SUPAdmins,DC=rcdevsdocs,DC=com (cached)
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Resolved source location: US
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Started transaction lock for user
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Found user fullname: valery
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Found 10 user settings: EnableLogin=Yes
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] User has no certificate registered
[2021-07-23 11:34:47] [10.2.3.6:58211] [OpenOTP:O37D471C] Sent failure response
For custom implementation of computer certificate based authentication with the OpenOTPPKILogin method, you must pass the MACHINE value in the option parameter.
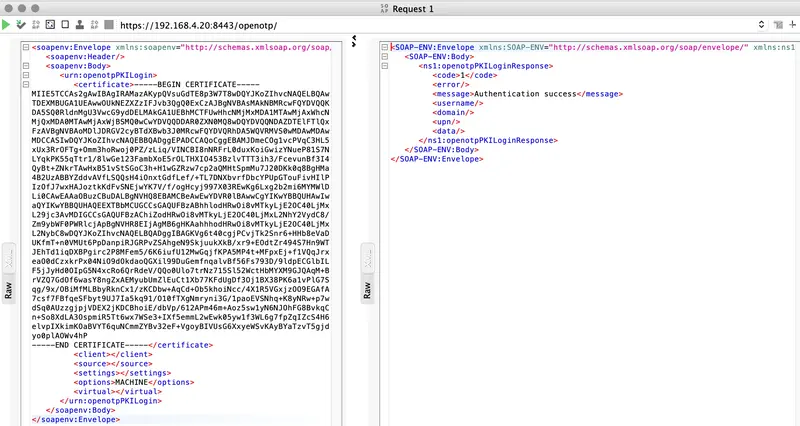
Client policies for EAP-TLS, EAP-TTLS logins
EAP-TLS policy
For certificates issued by WebADM/Rsignd PKI, OpenOTP is involved in the login process to apply WebADM client policies.
For EAP-TLS, it is useless to customize OpenOTP settings like the login factors (LDAP, OTP, LDAPOTP) or the token type because these settings are not applied in EAP-TLS authentication. Anyway, it can be useful to create WebADM client policies for your EAP systems. For example, you can allow which user domain(s) is/are able to access that system, which group(s) is/are allowed to log in on that system, configure excluded days where the logins are not allowed on that system...
Below, an example of the client policy I created for my Wi-Fi access.
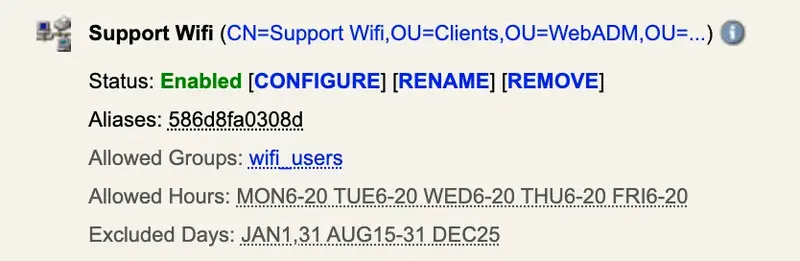
In my Support Wifi policy, I allowed my Wifi_Users group to log in and disallow my Domain Admins group. I've configured allowed hours and days to access that system. I configured the NAS-Identifier sent by my EAP system in the Client Name Aliase. This is needed to match the WebADM client policy with the client system.
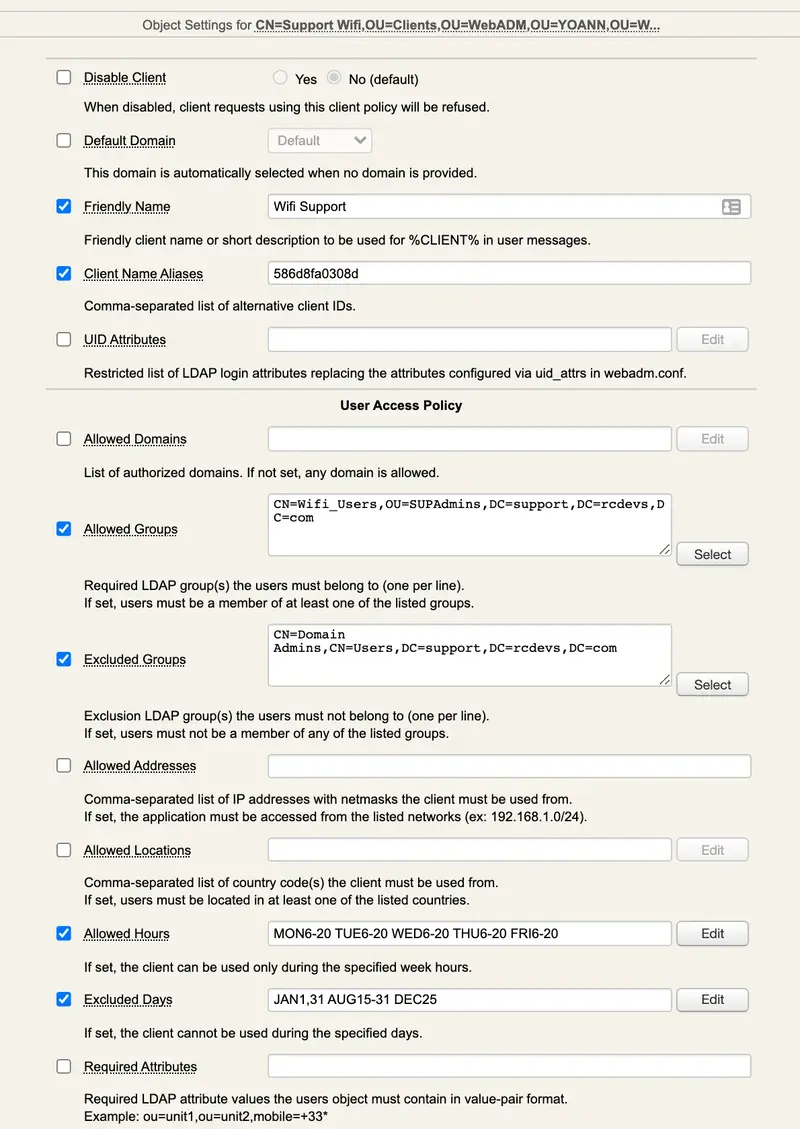
For certificates issued by an external PKI, OpenOTP can not be involved in the login process to apply WebADM client policies.
EAP-TTLS policy
For EAP-TTLS and EAP-GTC client systems, you can create WebADM/OpenOTP client policies. In that scenario, OpenOTP is involved to validate credentials provided by the user during the authentication. In that scenario, you can configure OpenOTP settings. The first OpenOTP setting you need to configure for these clients systems is the de-activation of the challenge mode support because it is not supported by EAP clients. You can choose which factor you want to validate with OpenOTP (LDAP, OTP, LDAPOTP) for EAP-TTLS/GTC logins :
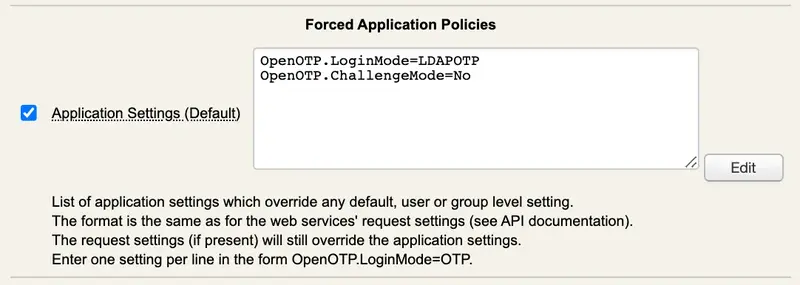
If you choose the LDAPOTP login mode, you must provide the LDAP password and the OTP in concatenated mode during the authentication.
Use that kind of login mode will prevent you to save credentials for that system because the OTP will not be valid anymore for the next authentication.
The push login is supported on that mode. It means you just need to provide an LDAP username and password during the authentication, and then you will receive a push login request to finish the login process. LDAP credentials can be saved for the next login, you will just have to approve the push request for the next logins.
Another interesting feature that can be used here is the implementation of applications passwords. When the applications passwords feature is enabled for a system, users can use a password randomly generated by WebADM to log in on a specific system. Application passwords are generated per client policy and are unique for each user. Applications passwords can be configured under OpenOTP configuration and can be generated by end-users through RCDevs self-services.
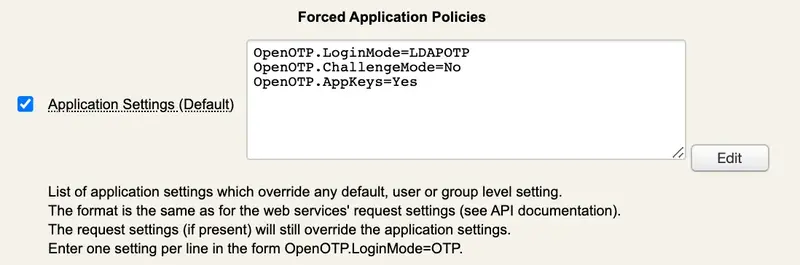
Application password and OpenOTP login mode
Applications passwords are not entering in conflict with the Login Mode configured in OpenOTP. For e.g, if the Login Mode is configured to LDAPOTP, users can log in using their application password or the LDAP and OTP passwords/Push.
E.g. of application password generated for my Wifi Support client policy through the User Self-Service Desk.
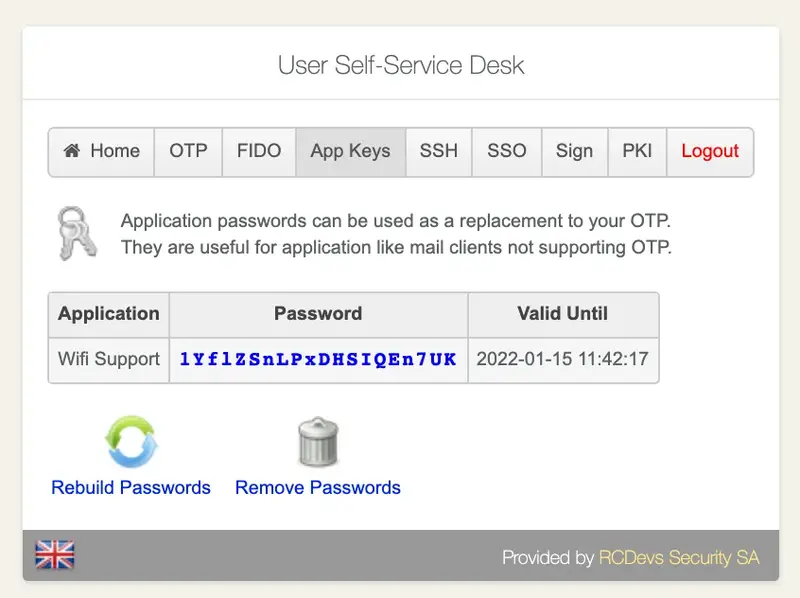
Usage of my Application password to login :
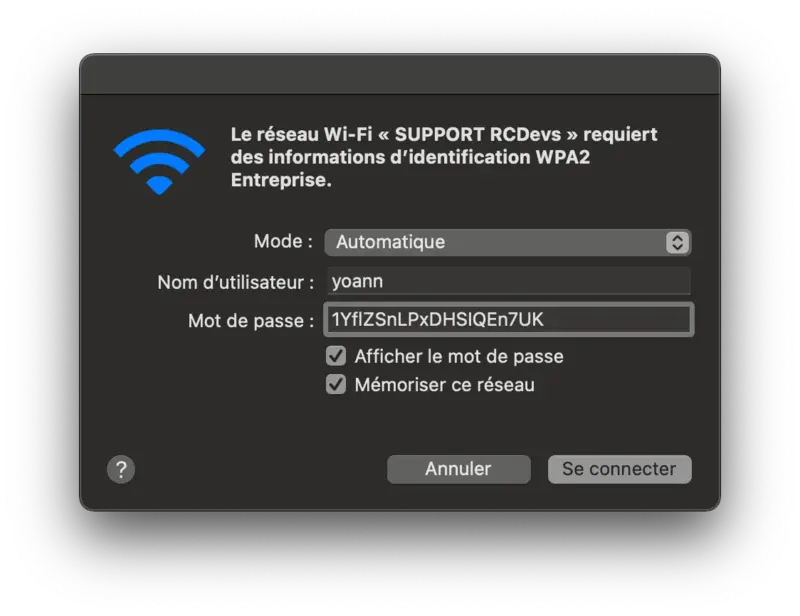
I am successfully authenticated with my application password.
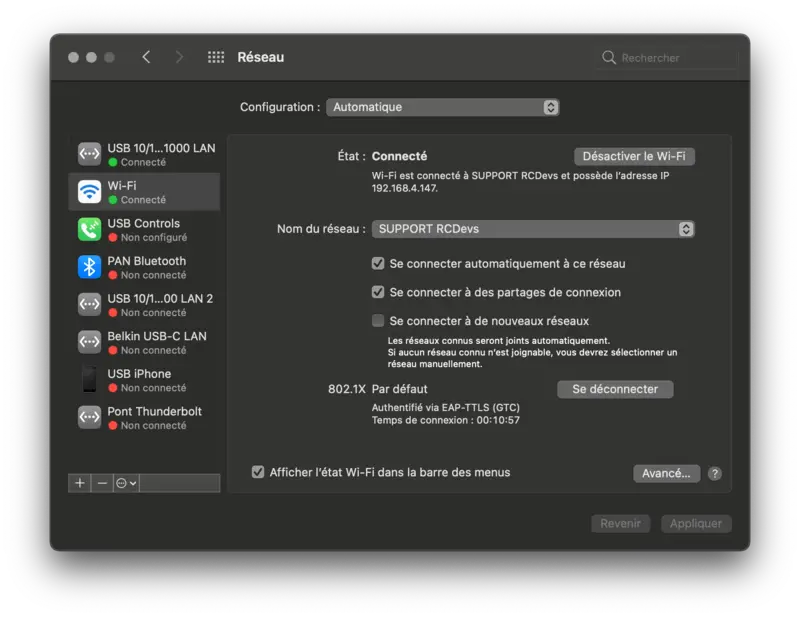
OpenOTP logs for login with an application password
Below, the WebADM/OpenOTP logs regarding the authentication performed with my application password.
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] New openotpSimpleLogin SOAP request
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] > Username: foo
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] > Password: xxxxxxxxxxxxxxxxxxxx
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] > Client ID: 586d8fa0308d
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] > Settings: OpenOTP.ChallengeMode=No
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] > Options: RADIUS,NOVOICE,-U2F
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Enforcing client policy: Support Wifi (matched client ID)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Registered openotpSimpleLogin request
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Checking OpenOTP license for RCDevs Documentation
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] License Ok (34/50 active users)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Resolved LDAP user: CN=foo bar,OU=SUPAdmins,DC=rcdevsdocs,DC=com (cached)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Resolved LDAP groups: super_admin,domain admins,schema admins,administrators,denied rodc password replication group
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Started transaction lock for user
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found user fullname: foo
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found user language: FR
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found 1 user emails: support@rcdevsdocs.com
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found 52 user settings: LoginMode=LDAPOTP,OTPType=TOKEN,PushLogin=Yes,ChallengeMode=No,ChallengeTimeout=90,OTPLength=6,OfflineExpire=30,MobileTimeout=30,EnableLogin=Yes,AppKeys=Yes,HOTPLookAheadWindow=25,TOTPTimeStep=30,TOTPTimeOffsetWindow=120,OCRASuite=OCRA-1:HOTP-SHA1-6:QN06-T1M,DeviceType=FIDO2,U2FPINMode=Discouraged,SMSType=Normal,SMSMode=Ondemand,MailMode=Ondemand,PrefetchExpire=10,LastOTPTime=300,ListChallengeMode=ShowID,ReplyData=[2 Items]
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found 1 request settings: ChallengeMode=No
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found 12 user data: ListInit,ListState,AppKeyInit,Device1Type,Device1Name,Device1Data,Device1State,TokenType,TokenKey,TokenState,TokenID,TokenSerial
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] OTP List present (0/25 passwords used)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Application passwords present (valid until 2022-01-15 11:42:17)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Found 1 registered OTP token (TOTP)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Challenge mode disabled (assuming concatenated passwords)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Requested login factors: AppKey | (LDAP & OTP)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Application password Ok (Support Wifi)
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Returning 8 RADIUS reply attributes
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Updated user data
[2021-07-19 12:45:12] [192.168.4.160:42248] [OpenOTP:8VTOGU9W] Sent login success response
Radius Attributes Value-Pairs (AVPs)
Radius AVPs can be used with both EAP-TTLS and TLS starting from WebADM 1.7.9-1 and Radius Bridge 1.3.11. This is a powerful mechanism that allows you to centrally control various characteristics of the network connection on per user/group basis, for example:
- VLAN allocation
- Access Control List Configuration
- Quality of Service Policies
- Groups membership...
Please refer to your network equipment documentation on which attributes can be used for your specific use case and follow the RADIUS Attributes Value Pairs documentation provided by RCDevs.
