Overview
In this documentation, we will focus on configuring your On-Premise VPN server with your OpenOTP Cloud tenant. Typically, VPN integration involves using the Radius (preferred) or LDAP Bridges or SAML/OpenID with some VPN solutions.
For SSL VPNs working with SAML or OpenID, that documentation is not explaining how to configure your VPN with SAML/OpenID. Please, refer to RCDevs Identity Provider documentation.
However, it's important to note that the Radius protocol was not specifically designed for transport over the internet. For this reason, RCDevs recommends deploying the OpenOTP Cloud Bridges Virtual Appliance, which includes Radius and LDAP Bridges components. This approach ensures a more secure integration.
If you choose not to deploy the OpenOTP Cloud Virtual Appliance, you have the option to contact RCDevs to inquire about alternative solutions. However, it's important to understand that using the Radius protocol directly over the internet without proper precautions carries certain risks, and it is done at your own discretion.
When the OpenOTP Cloud Bridge VM is set up, communication between your infrastructure and the RCDevs cloud infrastructures utilizes the HTTPS protocol with client/server certificate validation or API key authentication. This ensures a secure connection.
If the OpenOTP Cloud Bridge VM is not implemented within your network, the LDAP and Radius protocols will be transmitted over the internet.
It is crucial to consider security implications and evaluate the level of risk associated with the chosen integration method.
User creation, activation and token enrollment
The following steps outline how to create a user account in WebADM, activate the account, enroll a software token using the Push mechanism, and conduct a test login via the WebADM Admin portal before starting your integration. Instead of creating users and groups manually, you can also synchronize objects from an Active Directory infrastructure using the AD/LDAP Synchronization tool provided by RCDevs. For detailed instructions on this process, please refer to the dedicated documentation.
Account Creation
Log in to the WebADM Administrator portal with your administrator account.
Once authenticated in your OpenOTP Cloud tenant, click on the Create tab to set up a test account.
Select User/Administrator and then click Proceed.
On the next page, provide user's information and then click Proceed.
A recap is prompted, check your inputs and click create object.
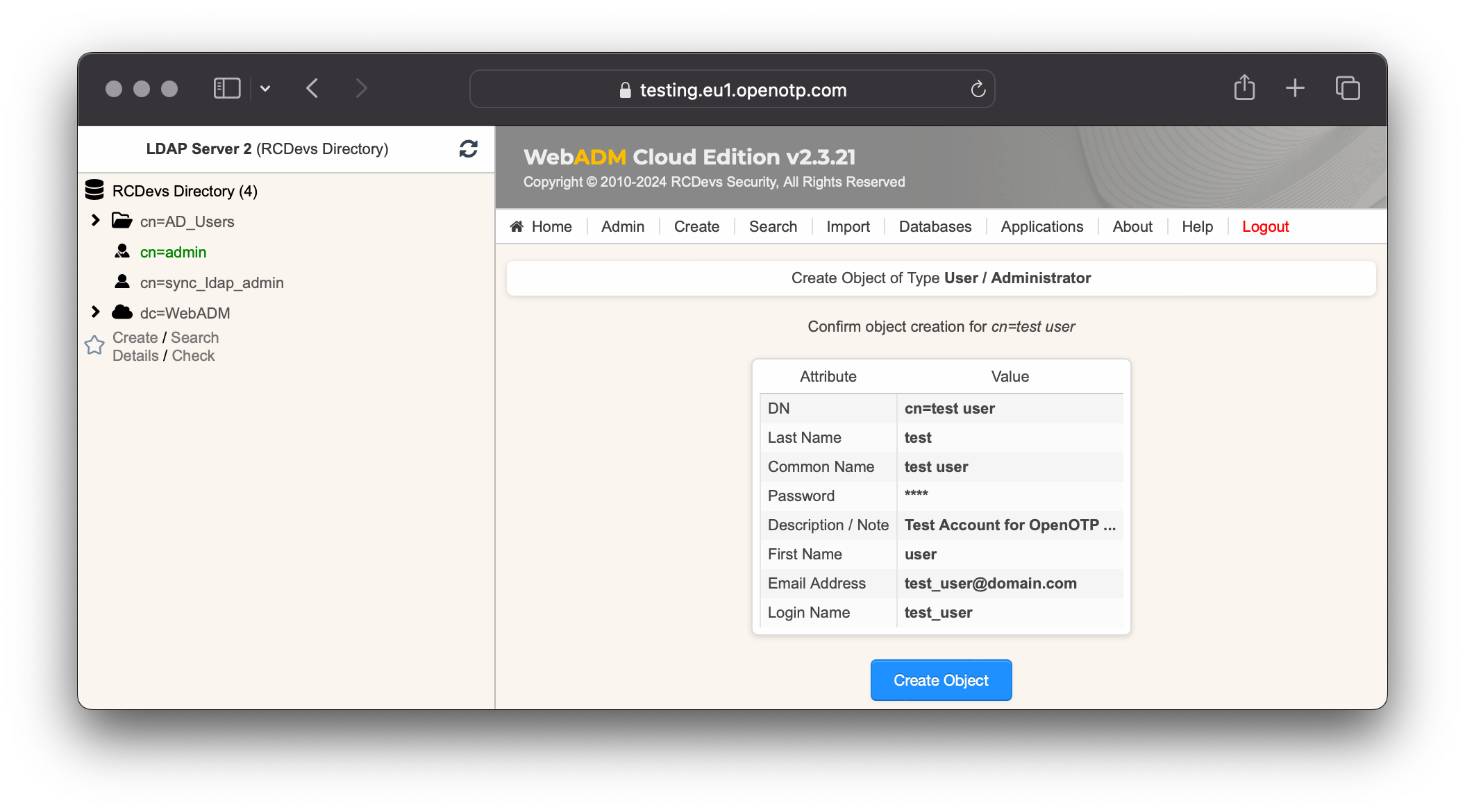
Your user account is now created.
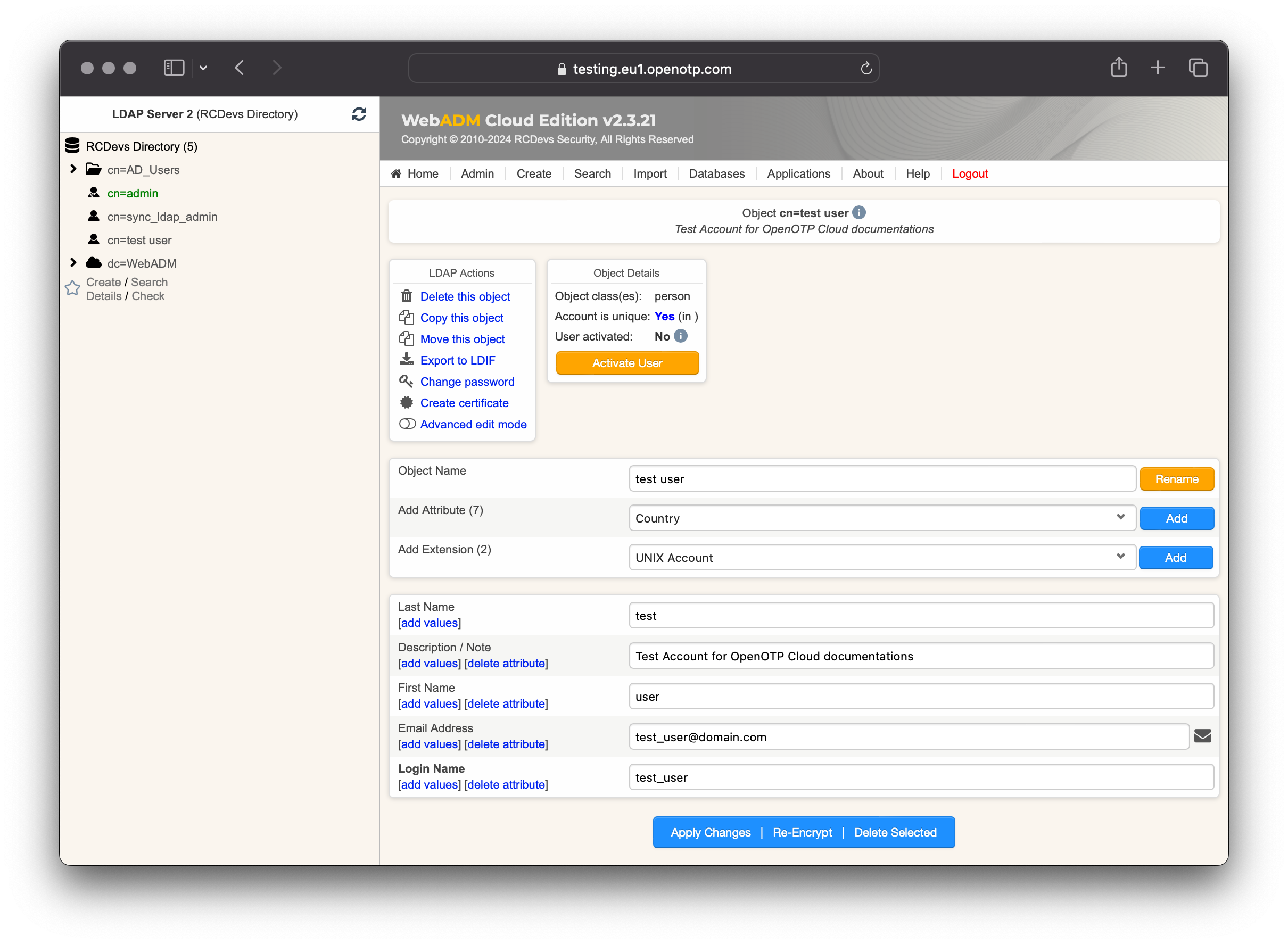
Account Activation
Now, we need to activate the account. Note that is in previous step, you created a WebADM account, the account is automatically activated (licensed). On the user account, in object details, click Activate User button followed by Proceed button.

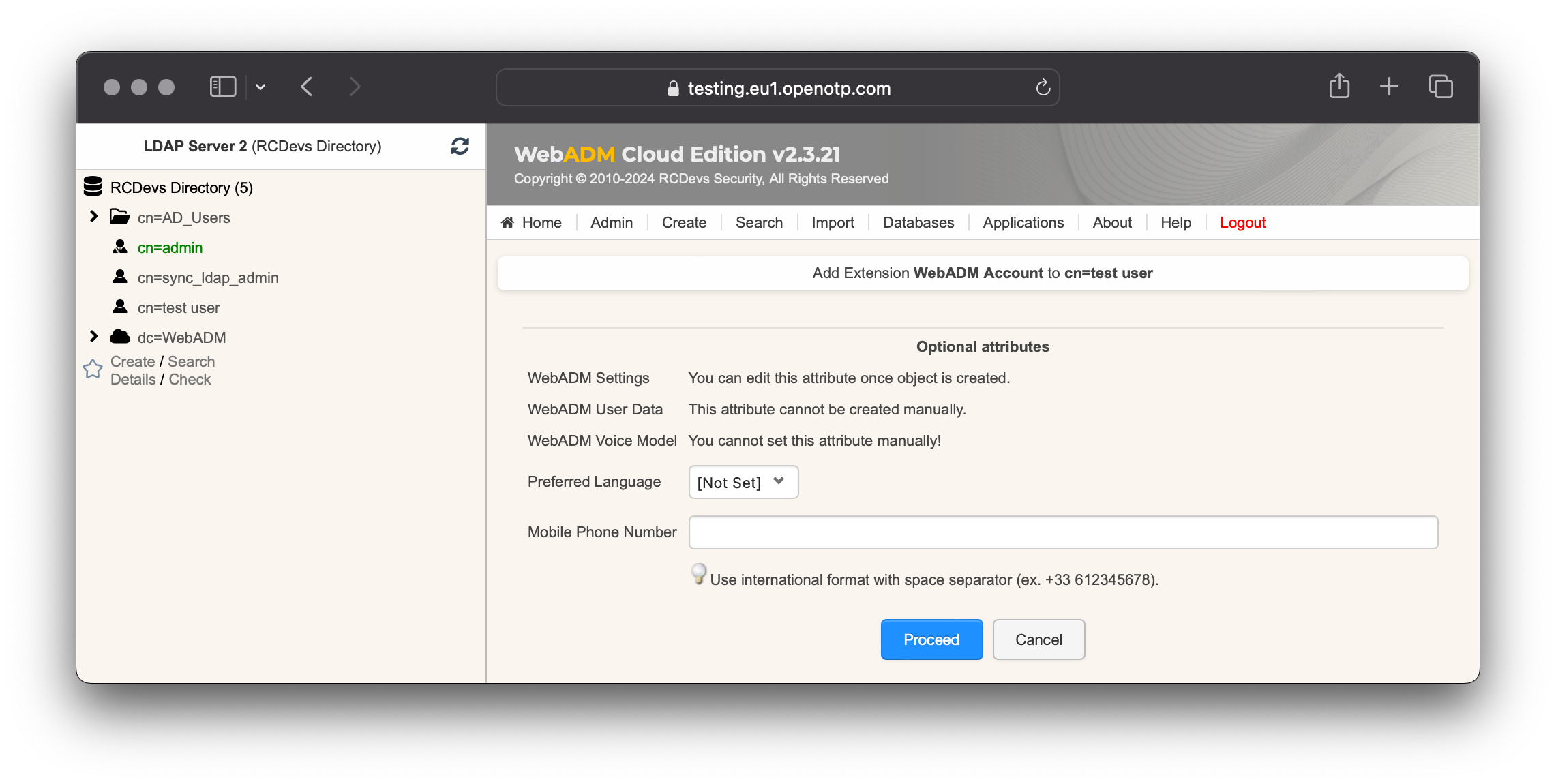
Finaly click on Extend object to proceed with the account activation.
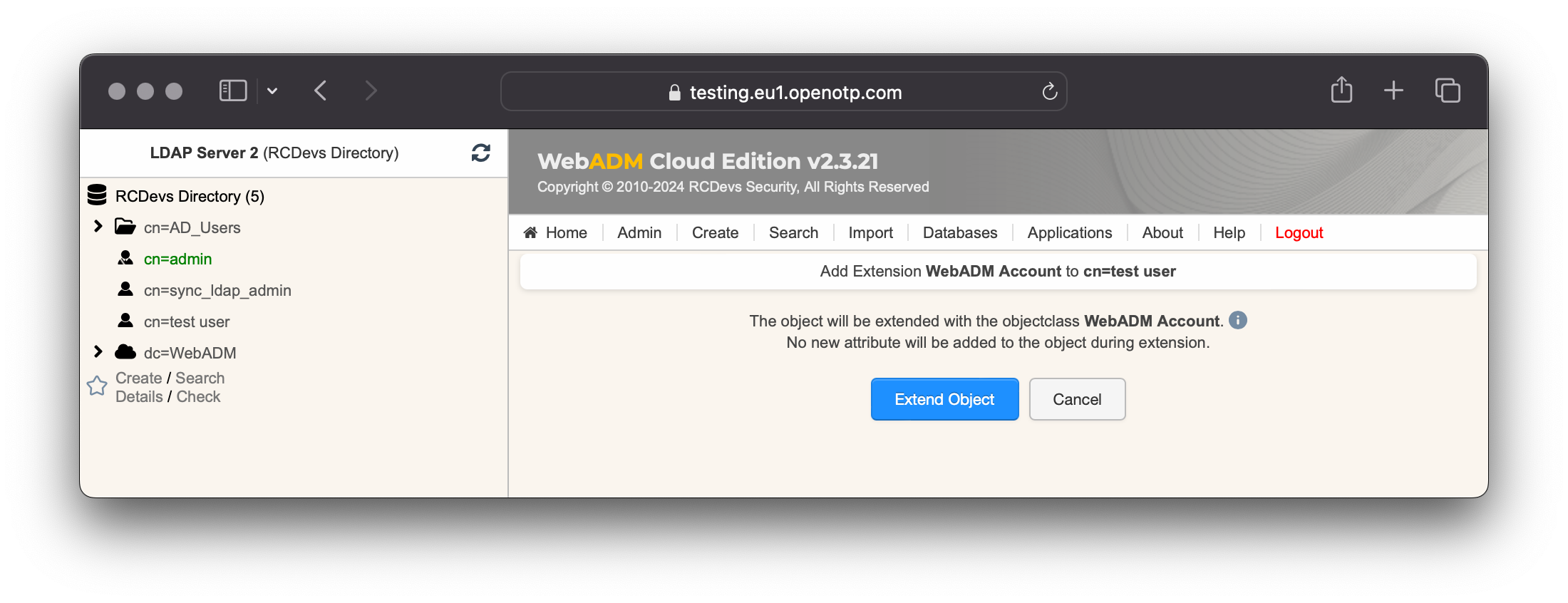
Account is now activated. You can now see the Application Actions menu from the user account view.
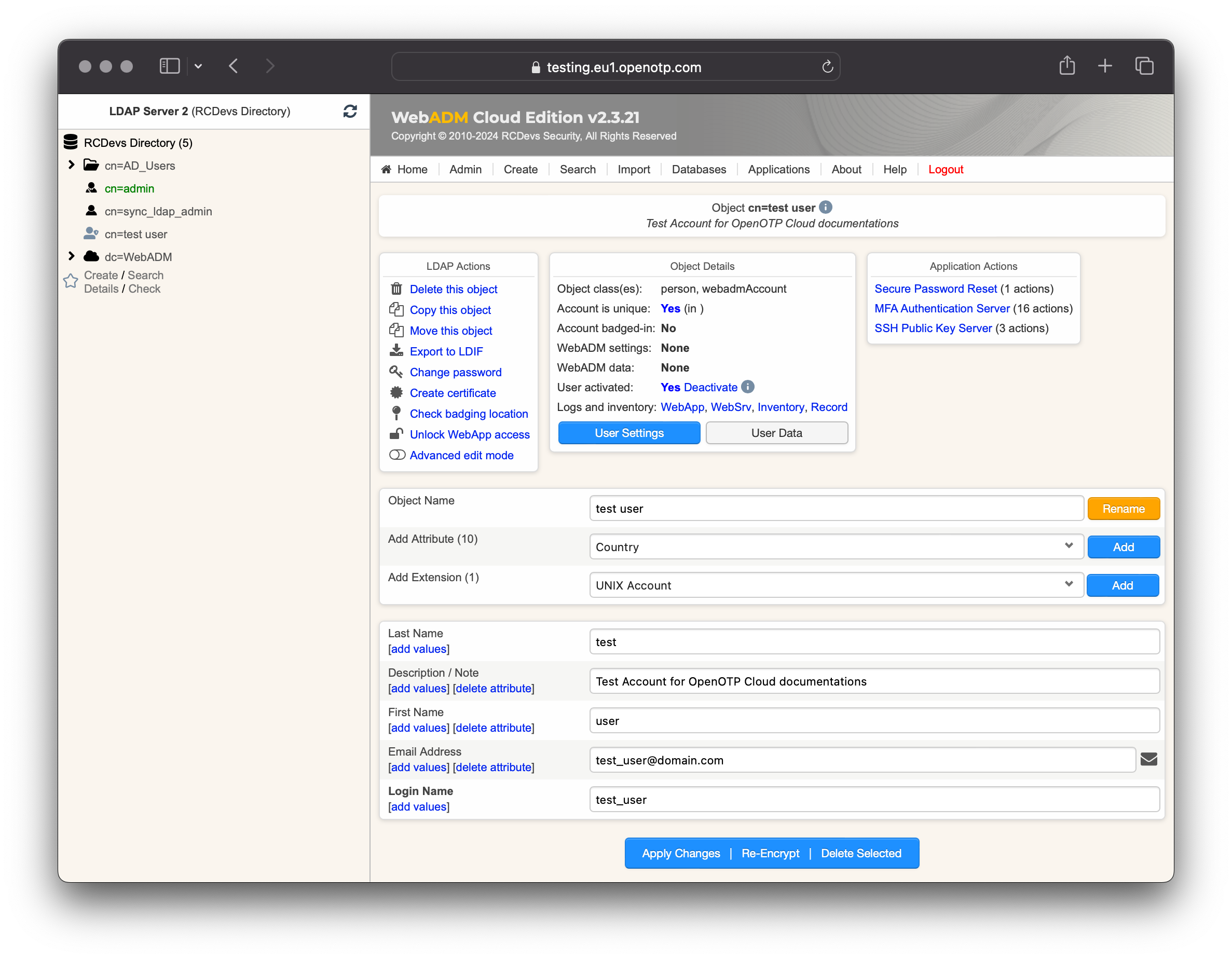
Token Enrollment
We are going now to enroll a software token. We advise you to use OpenOTP Token application in order to take advantage of all features provided by OpenOTP.
In Application Actions menu, click on MFA Authentication Server > Register/Unregister OTP Tokens. Select I use a QRCode-based Authenticator (time-based or event-based), then the enrollment QRCode is prompted. Open the OpenOTP Token application (or another authenticator app), then click the camera button and scan the QRCode.
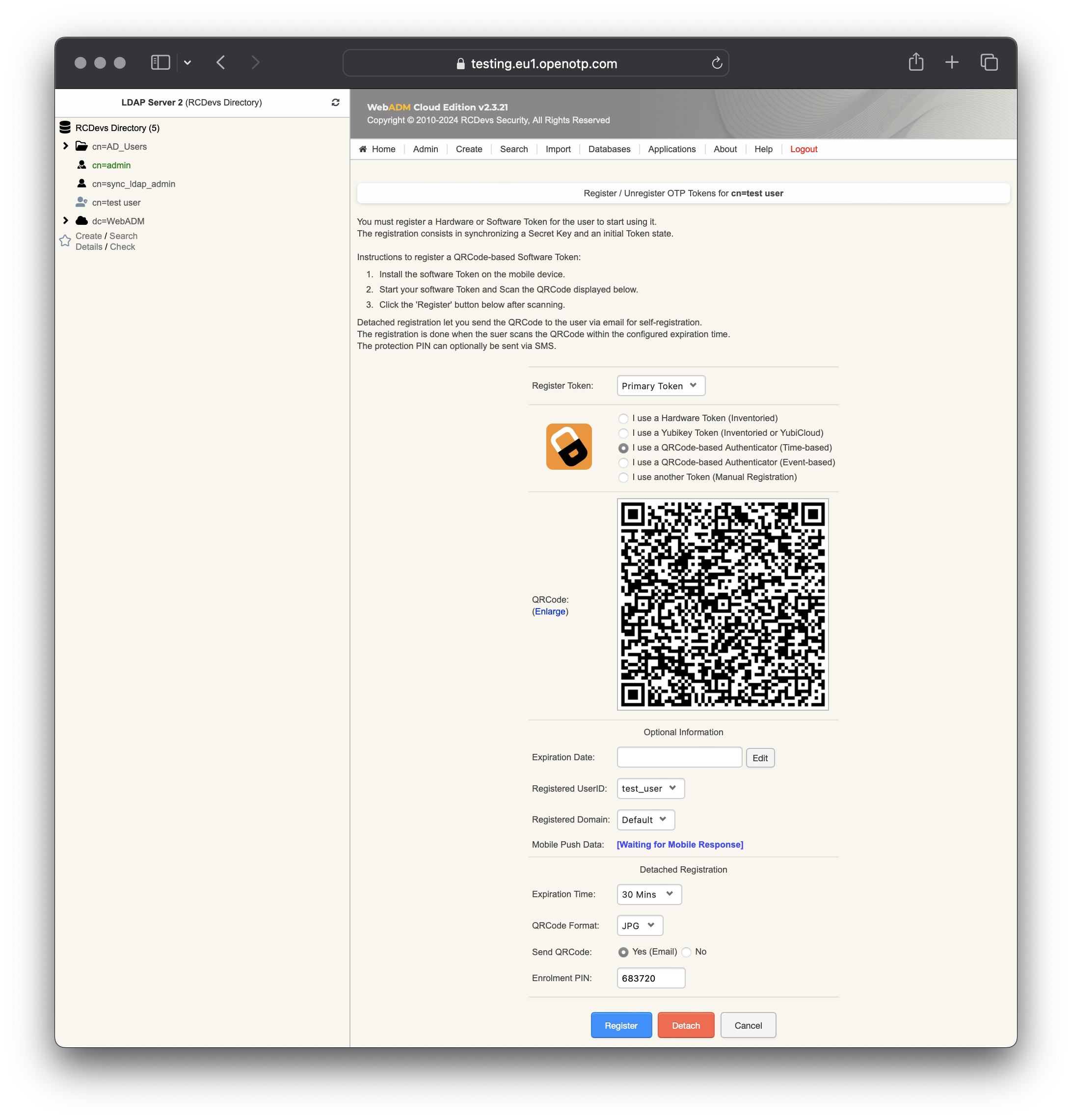
If the QRCode has been scanned with OpenOTP token, you don't need to click Register button.
If the QRCode has been scanned with another token application, you need to click Register button once the token is registered on your device.
The token has been registered successfully, we can now try to perform a login with it.
Test login
Come back on the user account, you will see now the token metadata registered on the account:
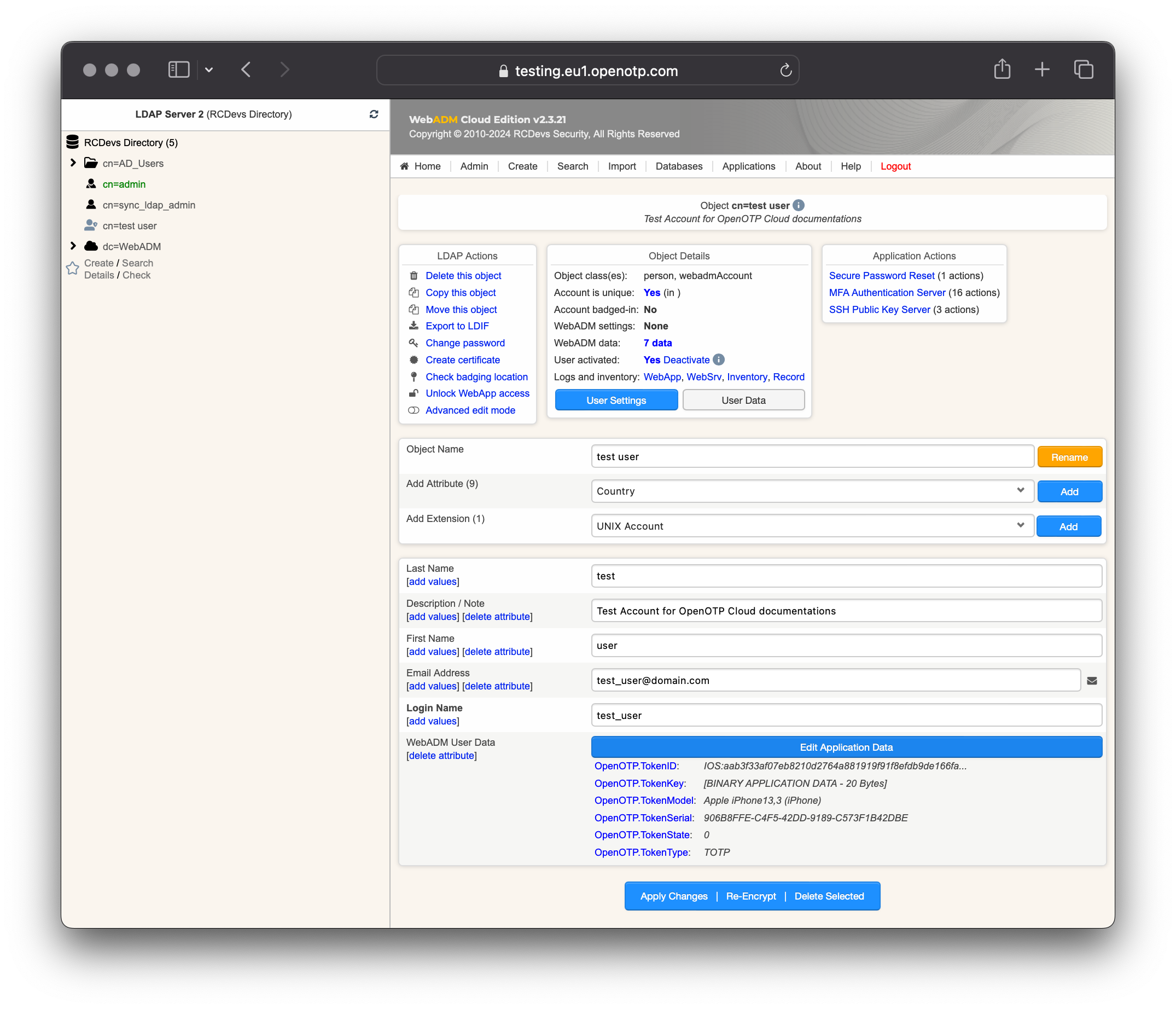
The enrollment has been completed with OpenOTP Token, and Push mechanisms are enabled by default. We will now perform a test login using Push authentication.
In Application Actions menu, click on MFA Authentication Server > Test OTP & FIDO Authentication
You arrive at the following page:
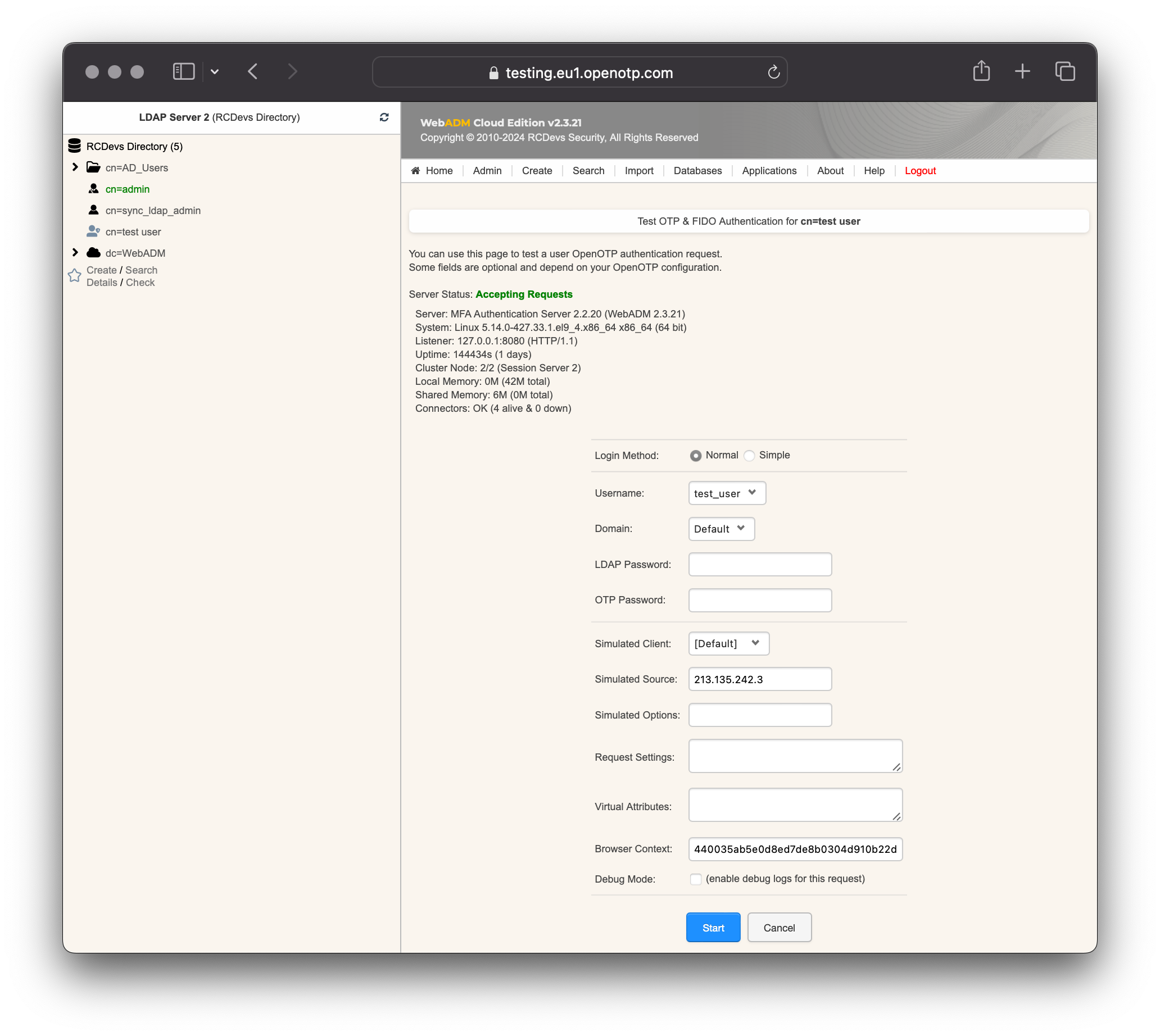
Provide the LDAP password that you previously configured during the user account creation, then click Start. A push notification should be prompted on your phone. Approve the request. The test login has been performed successfully.
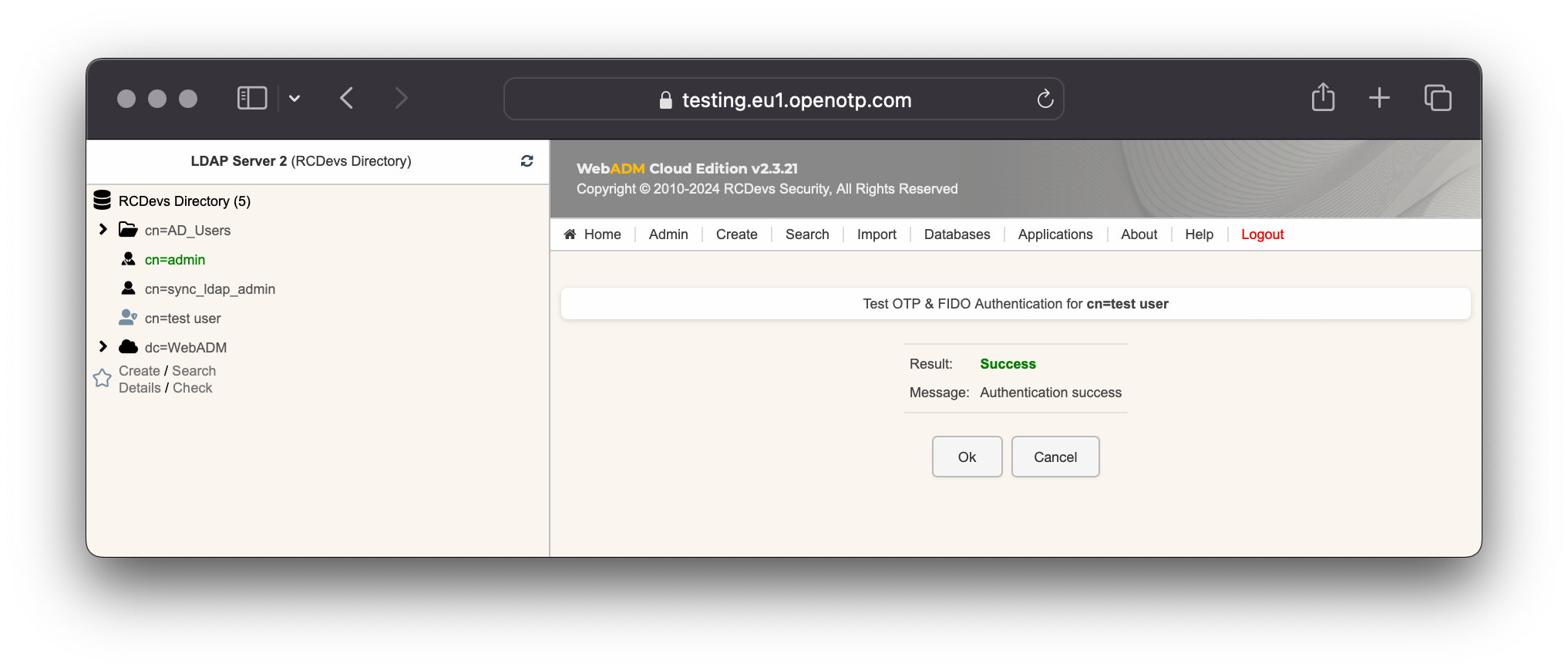
If you did not regiter the token with OpenOTP token application, then an OTP challenge is sent if you only provided the LDAP password. In that case, provide the OTP code generated by your token application and click Continue.
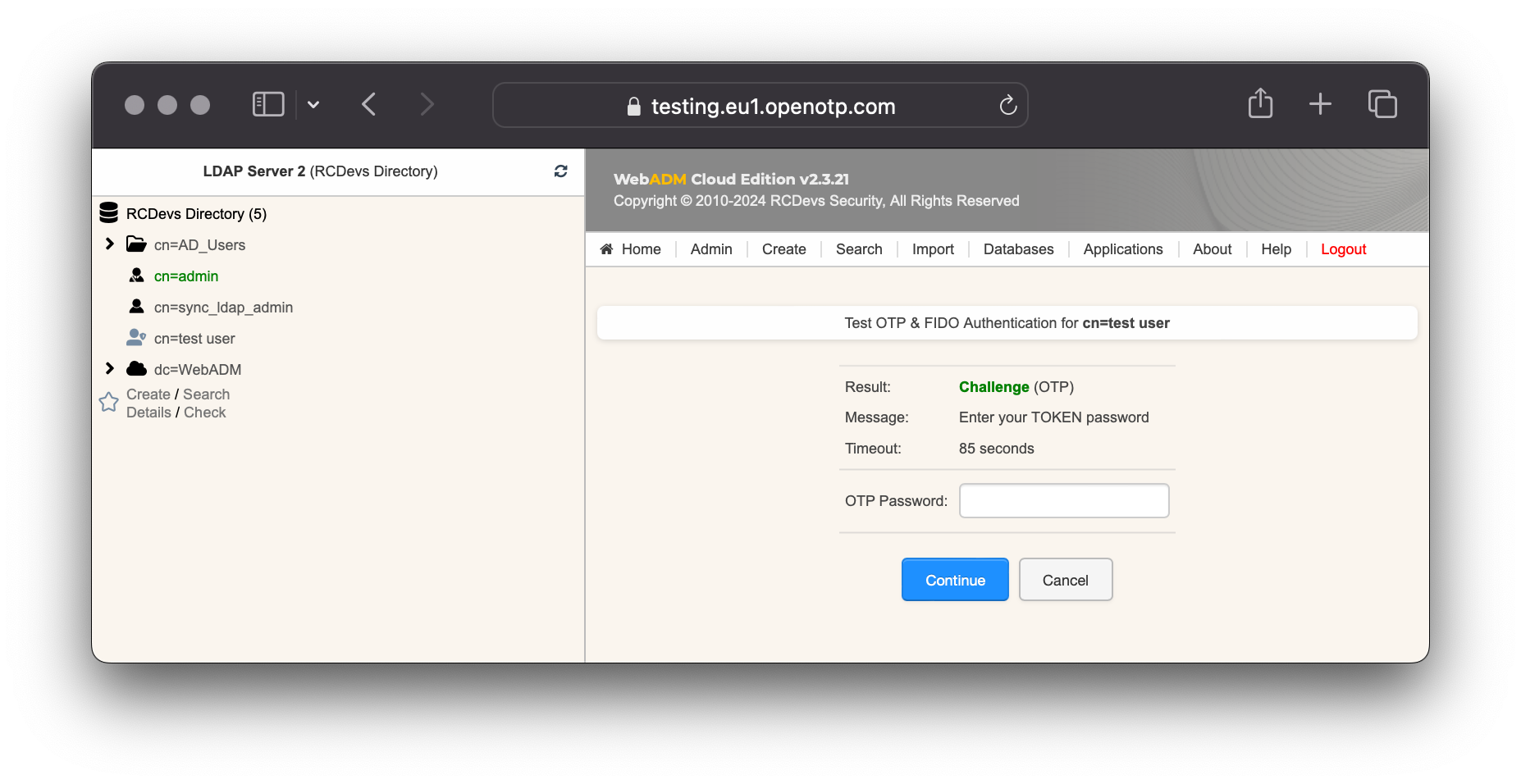
The test login has been performed successfully.
If the test login failed, you can browse the WebADM server logs to identify the problem. You can access the logs by accessing the Databases tab > WebADM Server Log File. Have a look on Troubleshooting documentation which can provide help and resolution on common issues.
VPN/RADIUS Client Setup with the On-Premise OpenOTP Cloud Bridge VM or RADIUS Bridge
This scenario assumes you want to ensure maximum security for communication between your infrastructure and openotp.com. To achieve this, deploy our OpenOTP Cloud Bridge VM, which can be set up following the instructions in the OpenOTP Cloud Bridge Virtual Appliance documentation.
The OpenOTP Cloud Bridge VM is a preconfigured virtual machine that includes both Radius Bridge and LDAP Bridge components. In most cases, the Radius Bridge component will suffice, as the majority of VPNs support RADIUS AAA authentication servers.
Alternatively, you can build your own server with similar configurations to achieve the same functionality. By deploying the OpenOTP Cloud Bridge VM or setting up a comparable server, you can establish a secure and reliable connection for seamless integration and authentication with your VPN.
Refer to the dedicated documentations for the OpenOTP Cloud Bridge VM or RADIUS Bridge to set them up.
VPN/RADIUS Client Setup without the On-Premise OpenOTP Cloud Bridge VM or RADIUS Bridge
If you wish to set up your VPN without deploying the OpenOTP Cloud Bridge VM or Radius Bridge component on-premise, you need to follow the steps outlined below:
- Request RCDevs to enable the Radius Service for your tenant and provide them with your public IP(s) and your tenant ID. The communication with the Cloud Radius service is filtered by IP addresses, so your public IP(s) need to be declared in the Radius service in order to allow communications.
If your public IP(s) are dynamic, you must deploy the OpenOTP Cloud Bridge VM. This is necessary as RCDevs does not want to open the Radius APIs to the entire internet for security reasons. The tenant ID can be found on yourWebADM Home page>License Detailssection >Hosted Tenantvalue.

Once you have provided RCDevs with the requested information, they will provide you with the Radius Secret. This Radius Secret needs to be configured in your Radius server configuration on your VPN server.
The Radius Secret acts as a shared secret key between your VPN server/Radius client and the OpenOTP cloud infrastructure, allowing them to authenticate and communicate securely.
- Configure a Radius Server (AAA) as the authentication server in your VPN configuration, targeting your tenant's or your private cloud's URL on openotp.com.
For example, if your OpenOTP tenant URL is "https://testing.eu1.openotp.com", you should configure testing.eu1.openotp.com as Radius server hostname with the port 1812 using UDP on your VPN server.
If your VPN server does not support hostnames, you can use the following IP addresses for the OpenOTP cloud infrastructure:
Name: openotp.com
Address: 146.59.203.4
Address: 146.59.206.40
Name: eu1.openotp.com
Address: 87.98.155.89
Address: 178.32.96.77
Please note that the IP addresses mentioned above are placeholders, and you should obtain the actual IP addresses from RCDevs for your specific OpenOTP cloud infrastructure region. Ensure that you configure the server hostname or IP address and the port correctly in your VPN server configuration to establish a successful connection with the OpenOTP cloud infrastructure.
- The Radius timeout should be configured to at least 30 seconds.
- The Radius retry should be configured to 0 or 1.
- The Radius accounting is not managed by Radius Bridge server, so it is useless to configure it on your VPN server.
- The Radius secret or Shared secret is provided by RCDevs.
- The password protocol which should be used is PAP.
It's important to note that in the scenario described here, you don't need to set up the Radius Bridge component, as it is hosted by RCDevs. The documentation will provide guidance on the necessary configurations and settings for integrating your VPN with OpenOTP cloud without the need for setting up the Radius Bridge. By following the instructions provided in the VPN provider documentation and the RCDevs documentation, you will be able to configure your VPN to work seamlessly with OpenOTP cloud for multi-factor authentication.
References and Advanced configuration
For more information on configuring your VPN/RADIUS client, please refer to the documentation provided by your VPN provider. Additionally, you can consult the RCDevs documentation.
For a complete understanding and configuration of the RADIUS Bridge component, refer to the Radius Bridge documentation provided by RCDevs.

