Overview
This guide demonstrates how to integrate Azure/EntraID and Office 365 with the RCDevs Identity Provider (IdP) using SAML.
For detailed information on configuring SAML federation in Azure, refer to Microsoft’s official documentation:
👉 Configuring SAML federation with Entra ID
This integration allows Azure/Office 365 to delegate authentication to RCDevs, enabling strong MFA enforcement and flexible identity management through WebADM.
This documentation covers:
- Identity residency and synchronization strategies
- Azure/EntraID domain federation with RCDevs IdP
- WebADM client policy configuration for Azure/Office 365 SAML authentication
Identities Residency Strategies
Depending on your organization’s directory design, WebADM and RCDevs IdP can integrate with several identity sources.
Each configuration determines how the ImmutableId is generated and returned in the SAML assertion.
Active Directory with WebADM (Default Enterprise Setup)
Description:
WebADM connects directly to the on-premises Active Directory through its LDAP (AD) connector defined in servers.xml, operating in read/write mode.
ImmutableId Handling:
- The
ImmutableIdincluded in the SAML assertion corresponds to the Active DirectoryobjectGUIDin base64. - When Azure AD Connect is in use, the
OnPremisesImmutableIdattribute is automatically populated in Entra ID. No additional mapping is required, as WebADM and the RCDevs Identity Provider use and transmit the same identifier.
Active Directory Synced into RCDevs Directory (WebADM Domain LDAP Connector)
Description:
User and group objects from Active Directory are synchronized into the RCDevs Directory (OpenLDAP) using WebADM’s Domain LDAP connector. Refer to this documentation for a better understanding or setup.
ImmutableId Handling:
- The
ImmutableIdremains the Active DirectoryobjectGUID, which is preserved during synchronization of users objects in WebADM. - This ensures seamless matching with Azure/Entra ID user accounts already synced via Azure AD Connect.
AzureAD/EntraID Identities Synced into RCDevs Directory (WebADM Domain Entra ID Connector)
Description:
Azure/Entra ID user and group objects are synchronized into the RCDevs Directory using WebADM’s Entra ID connector.
Optionally, if identities in Entra ID originate from an Azure AD Connect synchronization, the ImmutableId remains the Active Directory objectGUID, which is used and returned by WebADM and the RCDevs Identity Provider in the SAML assertion.
ImmutableId Handling:
- If the
onPremisesImmutableIdattribute exists on the Entra ID account, it will be used and returned by WebADM in the SAML assertion as theImmutableId. - If
onPremisesImmutableIdis not configured, WebADM returns the EntryUUID value as theImmutableId. - In bi-directional synchronization setups, WebADM can set or update the
onPremisesImmutableIdattribute in Entra ID automatically — provided the Enterprise Application used for synchronization has theUser.ReadWrite.Allpermission.
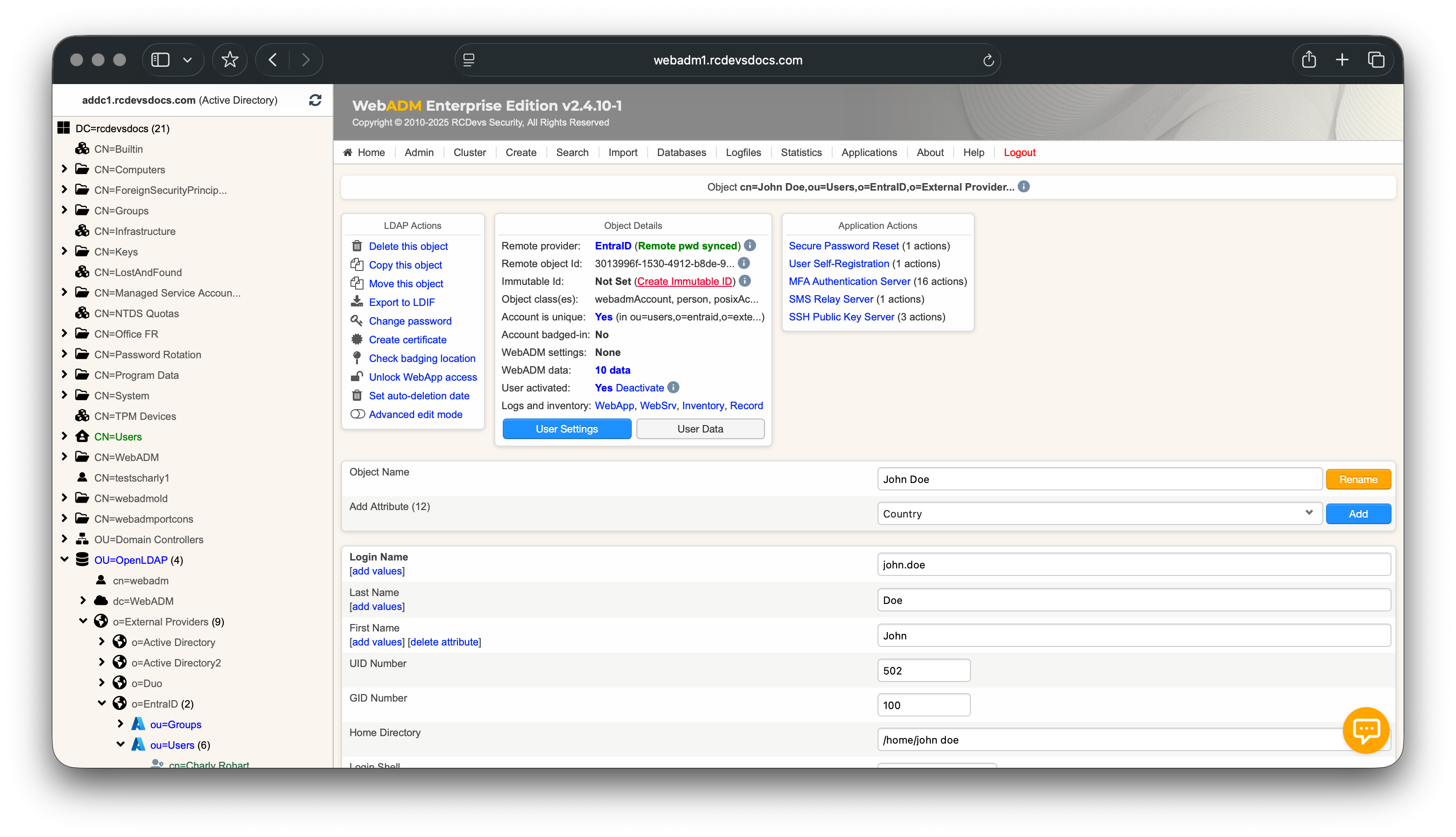
In Object Details box, you can see the Immutable Id: Not Set (Create Immutable Id). Click on Create Immutable Id to create it on the Entra ID User object.
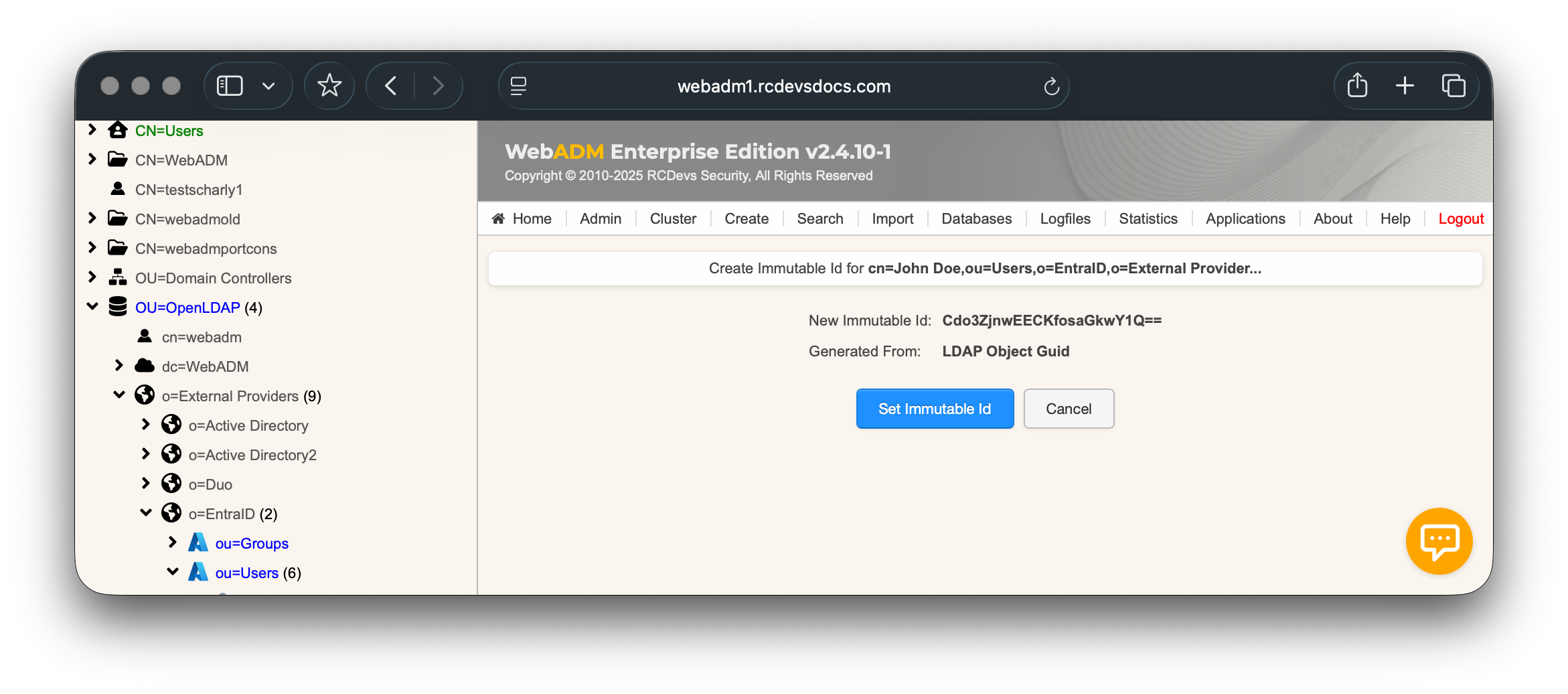
Click on Set Immutable Id and the OnPremisesImmutableId on the Entra ID account will be set.
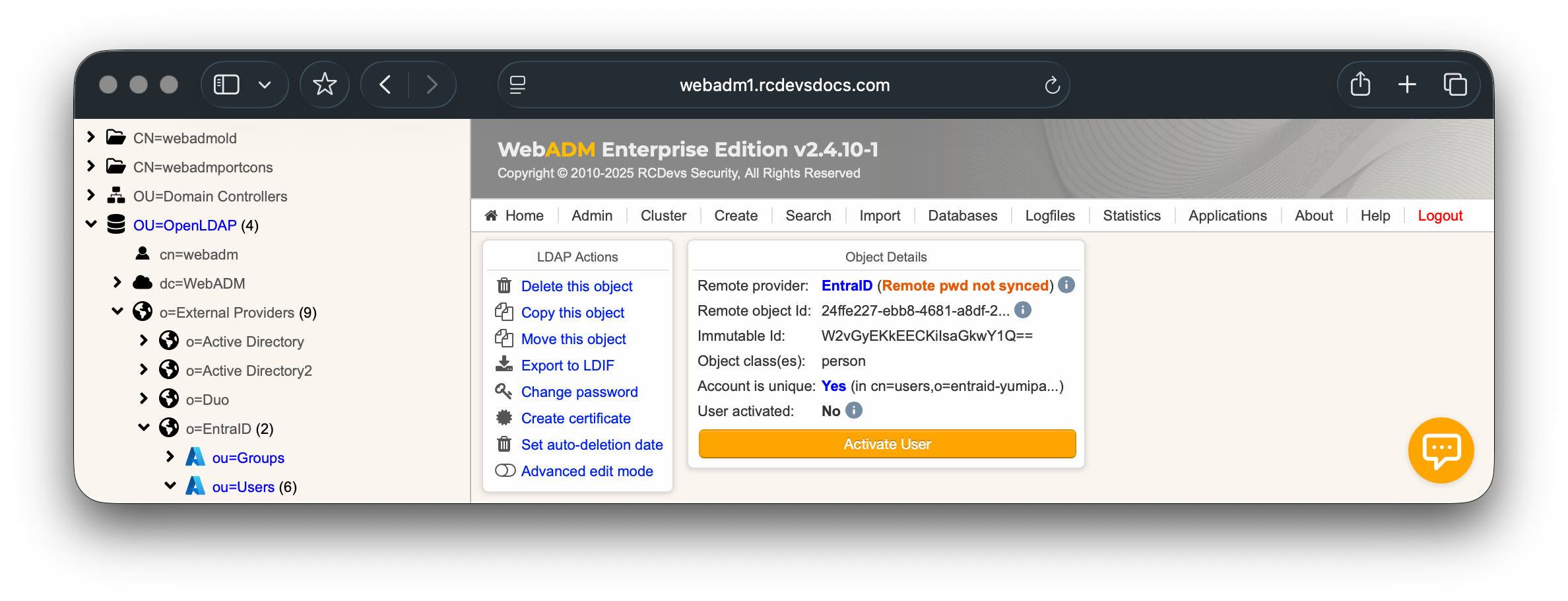
You can now see it in Object Details box:
RCDevs Directory and Identities Not Synced
Description:
In standalone setups, user accounts exist only in the RCDevs Directory (OpenLDAP) and are not synchronized from AD or Entra ID.
ImmutableId Handling:
- The
ImmutableIdreturned in the SAML response corresponds to the OpenLDAPentryUUIDattribute. - This requires manual configuration of the
onPremisesImmutableIdattribute on each corresponding Entra ID user to enable matching during SAML authentication.
The mapping can be performed using the following commands:
Connect-MgGraph -Scopes "User.ReadWrite.All"
$User = Get-MgUser -UserId "john.doe@openldap.com"
Update-MgUser -UserId $User.Id -OnPremisesImmutableId "09da3766-39f0-1040-8a7e-8b1a1a4c18d5"
Here, the OnPremisesImmutableId value 09da3766-39f0-1040-8a7e-8b1a1a4c18d5 corresponds to the EntryUUID attribute of the OpenLDAP object.
Note that the OnPremisesImmutableId attribute in Entra ID cannot be modified once it has been set on a user object, unless domain federation is temporarily disabled. This means that if you accidentally remove an OpenLDAP account and then recreate it, the EntryUUID of the new user object will differ. To update the OnPremisesImmutableId of the corresponding Entra ID object, you must first disable domain federation, make the modification, and then re-enable domain federation.
Azure/EntraID Domain Federation through SAML with RCDevs Identity Provider
Azure/Entra ID must be configured to trust the RCDevs IdP as an external SAML identity provider.
Since the Office 365 admin center does not support third-party IdP configuration directly, this is performed via PowerShell using the Microsoft Graph module.
Install and Connect Microsoft Graph Module
If not installed:
Install-Module Microsoft.Graph -Scope CurrentUser
Connect to Microsoft Graph with the following permissions:
Connect-MgGraph -Scopes "Domain.ReadWrite.All", "Directory.AccessAsUser.All"
Configure Environment Variables
Update the values below according to your environment:
$domain = "rcdevsdocs.com"
$params = @{
DisplayName = $domain
MetadataExchangeUri = "https://sso.rcdevsdocs.com/ws/saml/"
IssuerUri = "https://sso.rcdevsdocs.com/"
PassiveSignInUri = "https://sso.rcdevsdocs.com/openid/index.php"
SignOutUri = "https://sso.rcdevsdocs.com/openid/index.php"
PreferredAuthenticationProtocol = "saml"
FederatedIdpMfaBehavior = "enforceMfaByFederatedIdp"
SigningCertificate = @"
-----BEGIN CERTIFICATE-----
<your RCDevs IdP certificate here>
-----END CERTIFICATE-----
"@
}
Notes:
MetadataExchangeUri: The SAML metadata URL of the RCDevs IdP.IssuerUri,PassiveSignInUri,SignOutUri: RCDevs IdP endpoints.- With WAProxy, the
/webapps/path is typically omitted. - Other reverse proxies may require URL rewriting or different paths.
- With WAProxy, the
PreferredAuthenticationProtocol: Must beSAML.FederatedIdpMfaBehavior: Set toenforceMfaByFederatedIdpso Azure relies on MFA performed by the RCDevs IdP instead of Azure MFA.
The RCDevs IdP issues the MFA claim only if MFA is actually enforced for the user. If a user authenticates with password only, Azure conditional access policies that require MFA may reject the authentication and redirect the user back to the IdP.
You can retrieve your IdP metadata by visiting your SAML metadata URL:
https://sso.rcdevsdocs.com/ws/saml
This URL provides XML output similar to:
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://sso.rcdevsdocs.com">
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGfzCCBGegAwIBAgIRAM9/TyvDiZAahDgzYkWGRdIwDQYJKoZIhvcNAQELBQAwUjEXMBUGA1UEAwwOUkNEZXZzIERvY3MgQ0ExCzAJBgNVBAsMAkNBMR0wGwYDVQQKDBRSQ0RldnMgRG9jdW1lbnRhdGlvbjELMAkGA1UEBhMCTFUwHhcNMjQwNzE1MTM0OTA3WhcNMzQwNzEzMTM0OTA3WjBgMRswGQYDVQQDDBJXZWJBRE0gQ2VydGlmaWNhdGUxDzANBgNVBA0MBlNFUlZFUjEXMBUGA1UECgwOUkNEZXZzIFN1cHBvcnQxFzAVBgNVBGEMDlZBVExVLTAwMDAwMDAwMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1w3PR1Q+78jdD12g4Di3ljcthoZwvpQuwmuOm/+fBthQjrHR1UIY3HDkulCOYpBRiNNj6ED49eyF9jIeO/zVO5QXnzX4gmasZPd06ZYAD8pkDc7fnnxZD4aSHDKQcF1xwUnHESUCPzWR1Wy3t6ifwl85uRuC+QlskMv4t82LqeMQeSBdeBqNpADm9Hmg8AO5BK4Oz/NNooB46P5RYDEerY1D/qOfLkuzEDr2C2Z1rGvtG7+7EpaS+b9Ipnz/fT71QACPxJym98YWEp/1Fb/clC6QLKQuQ+AzheTVZyyeOhOYFxsoGEu+wDFAERXWWAr5sPnayDJiZdXbH+712ri35y9oFWOxZC1diATOS/MRc05bAzgAbyiQe1PrhDfwRiL4YF0EtLvuZJGBH031DZS3THdYSeONDhsImbNYFYLPpzRqb5iXssN+KBPAdCfYJ2IMfjAV4li0s1WSC40iZ5MAkwovE0HD++DVO2HHBJ9hYl6aqa35lGm/QSjkUYvw2xX3kvc3utPQcqUkYDWzF7tLIMpTzO6FtD1pR/FR6DKkqmx9NhLMdIi9eNGK4MG+MgKwCXhE1I6aJxVoRCbAihb0wgnR+Y38P4bJUYzvDCC4upE3DLc+ct5VJ/rtCo9UDyVQGsLDD9cDoywdr6feM/Pou+LpccVNAHul1FJ9CPKxyVECAwEAAaOCAUAwggE8MAsGA1UdDwQEAwIF4DATBgNVHSUEDDAKBggrBgEFBQcDATCBygYIKwYBBQUHAQEEgb0wgbowJgYIKwYBBQUHMAGGGmh0dHA6Ly8xOTIuMTY4LjQuMTYwL29jc3AvMCYGCCsGAQUFBzABhhpodHRwOi8vMTkyLjE2OC40LjE2MS9vY3NwLzAzBggrBgEFBQcwAoYnaHR0cDovLzE5Mi4xNjguNC4xNjAvY2FjZXJ0Lz9mb3JtYXQ9ZGVyMDMGCCsGAQUFBzAChidodHRwOi8vMTkyLjE2OC40LjE2MS9jYWNlcnQvP2Zvcm1hdD1kZXIwSwYDVR0fBEQwQjAfoB2gG4YZaHR0cDovLzE5Mi4xNjguNC4xNjAvY3JsLzAfoB2gG4YZaHR0cDovLzE5Mi4xNjguNC4xNjEvY3JsLzANBgkqhkiG9w0BAQsFAAOCAgEACy/zl7IPSaOn2wEZ66xQNxm9FW408jMrQS2Y6hFvfzRMNhbOh+ZwNFSgCijUJ4ASZVQeZIiYN8f/quH80Y7AJE3kcTpXvJE2LozDbUMsXe0GpkNuzDojbp3K2ZcgUitL0q/rDHPBXXExl1AEhPgpwN1I7ZyHPfZpU92XxcsoSrUi8AMmzoVwlna30RMkkCDDBsf+an1uxdrdwMQLeQddOFddAUI80NWvh0drnv1epkT34K+RpvEAU514a3suErDMIqp+h7BqTdPrdiRkIhTutgSsPquhGIDzv+WvGBzFGWPAfudQHE5jMn3lPgN3r75HrdNfMkVEv0jclpp3VhiUnwQzNQn2UzVe7LQh8ixjEg1kwtIQ8UuwX6LOZ7a51WuKkRfS1iw1yDCM1UmGNuoMGqI6bxwFbBZ1C3brgJKjXBciEpXrSpcJ+ulhDYYUrCmGnpg6xyJ6veWfT2tVExLcffv4edT0KCJuKsyTztLFtT9A9ihyV/lPBsVUtIipe2CaCXupP84812s0cgo6XkcAr99pvtPNLZg9aBLuVt7GmyJSQeLJ6z+QWlkKnsEh7HlSrV2RC/wsTYlTeTRZFmiNa1RGx4UsNyTf9Igp+EG4Nh/UBhGO1Jkn1dIRZyb/qgcF/DWCSdbwFIKxuaKA12KFJMFS4aMV1e0QLDhLfpZ1/10=</X509Certificate>
<!-- Cert Fingerprint (SHA1): 32774463a2e892150f46852b3fdcac7f5be924dc -->
<!-- Cert Fingerprint (SHA256): e0bd10584f5c3a554e279b9241619e8fdf9c3bfbe95c90da939f0342546e52ac -->
<!-- Cert Fingerprint (MD5): 639ed5b4241047c8382f897fc459a714 -->
</X509Data>
</KeyInfo>
</KeyDescriptor>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sso.rcdevsdocs.com/openid/index.php"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sso.rcdevsdocs.com/openid/index.php"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://sso.rcdevsdocs.com/openid/index.php"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://sso.rcdevsdocs.com/openid/index.php"/>
</IDPSSODescriptor>
</EntityDescriptor>
Apply the Federation Configuration
Create the domain federation:
New-MgDomainFederationConfiguration -DomainId $domain -BodyParameter $params
Verify or troubleshoot:
Get-MgDomain -DomainId $domain | Format-List *
Get-MgDomainFederationConfiguration -DomainId $domain | Format-List *
After successful configuration, Azure/Entra ID will redirect authentication requests for your domain to the RCDevs IdP.
WebADM Client Policy Configuration for AzureAD/EntraID/Office365
Azure/EntraID Configuration on the IdP (WebADM Client Policy)
The Azure/Entra ID configuration on the IdP consists of creating a Client Policy and configuring the necessary SAML/OpenID settings.
To create a client policy for Azure/Office 365:
- Log in to the WebADM Administrator Portal.
- Go to the
Admintab →Client Policies→Add Client. - Name the policy and optionally add a description.
- Click
Proceed, thenCreate Object.
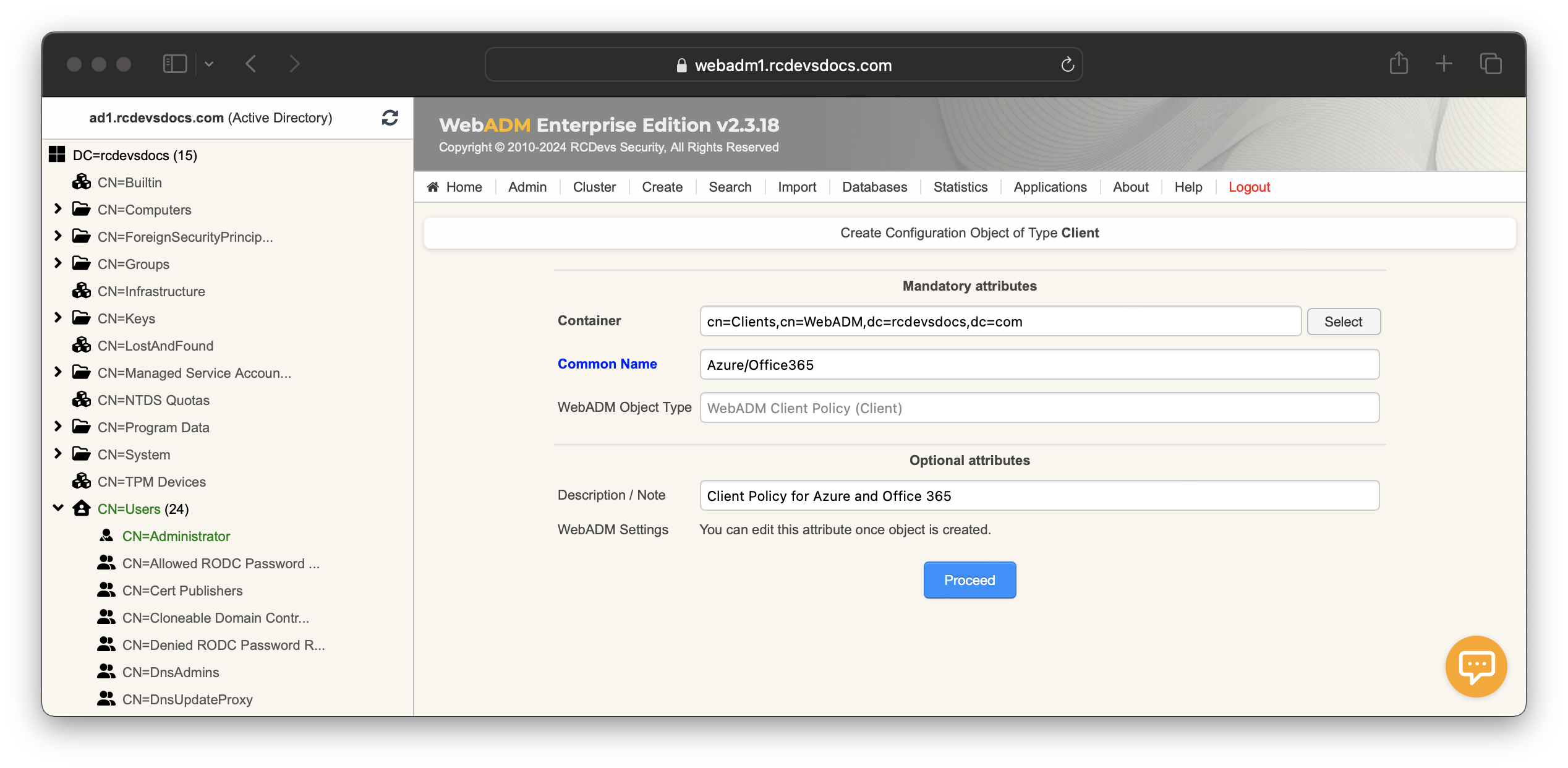
You are now entering the policy configurator.
Configure the Default Domain, a Friendly Name (optional), and set the Client Name Aliases to urn:federation:MicrosoftOnline value.
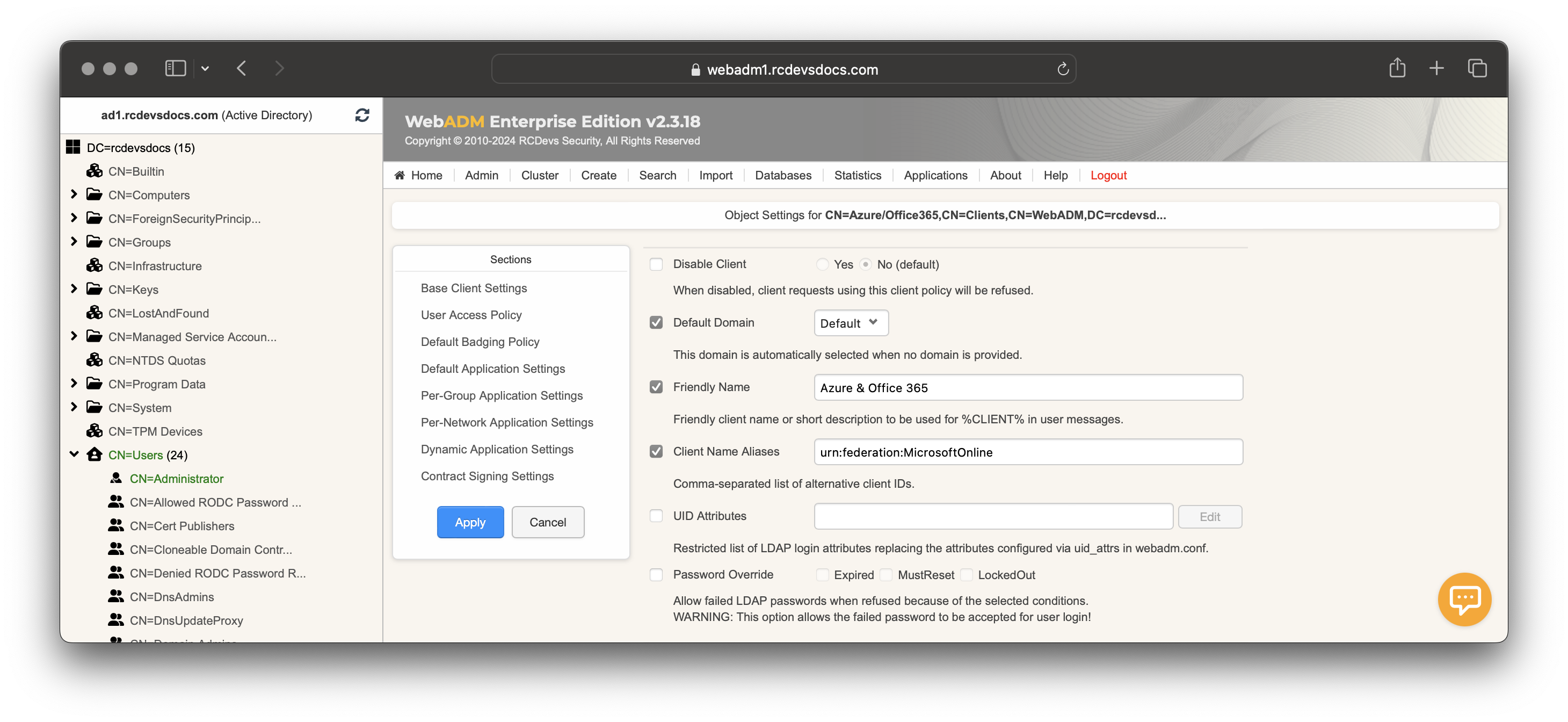
Scroll down to Default Application Settings, click on the checkbox followd by Edit button. In Applications section in the left corner, select OpenID & SAML Provider.
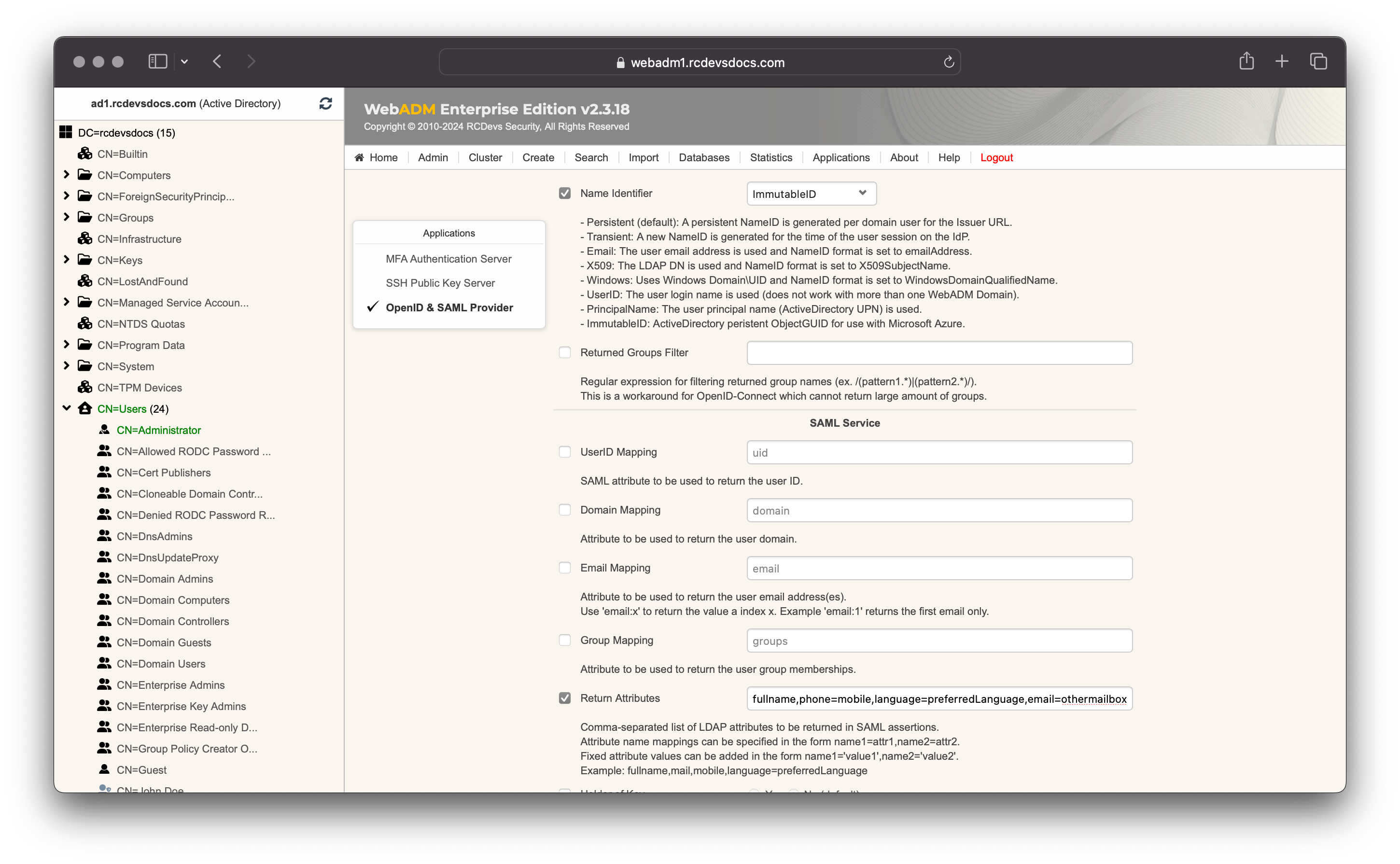
In the SAML & OpenID-Connect section, set the Name Identifier setting to ImmutableID.
In the SAML Service section, you can optionnaly configure the attributes returned in the SAML assertion.
e.g: fullname,phone=mobile,language=preferredLanguage,email=othermailbox
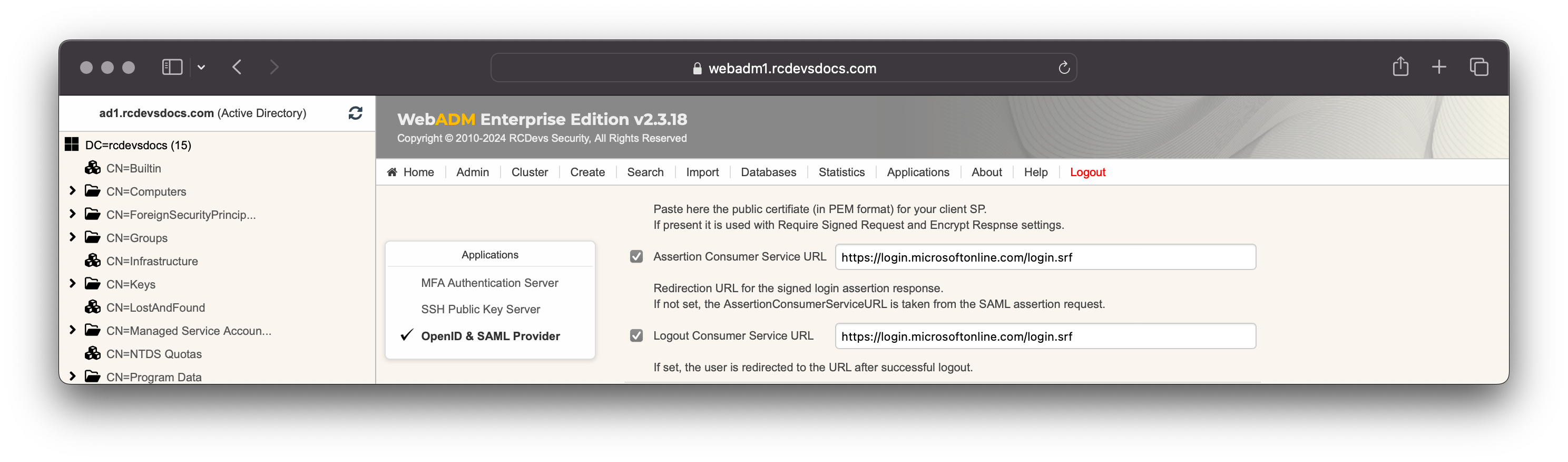
Next, set:
Assertion Consumer Service URL = https://login.microsoftonline.com/login.srfLogout Consumer Service URL = https://login.microsoftonline.com/login.srf
Configure MFA settings in the MFA Authentication Server section to enforce the desired OpenOTP settings.
Click Apply to confirm SAML/OpenOTP settings and Apply again to save the client policy.
Rollback Procedure
If you need to revert the federation configuration created with the New-MgDomainFederationConfiguration command, follow the steps below.
Identify the existing federation configuration
Run the following command to list federation configurations for the domain:
Get-MgDomainFederationConfiguration -DomainId "rcdevsdocs.com"
Note the value of the Id property for the federation entry to remove.
Remove the federation configuration
Execute the command below to delete the previously created SAML federation:
Remove-MgDomainFederationConfiguration -DomainId "rcdevsdocs.com" -InternalDomainFederationId <ID>
Replace <ID> with the identifier obtained from the previous step.
Verify deletion
Confirm that the federation has been removed:
Get-MgDomainFederationConfiguration -DomainId "rcdevsdocs.com"
If no configuration is returned, the rollback is complete.
Testing and Troubleshooting
- Navigate to the Microsoft login page and enter a username (in UPN format) from your federated domain.
- You should be redirected to your RCDevs IdP login page.
- Authenticate using the configured MFA method.
- Upon successful authentication, you will be redirected back to Microsoft and signed in.
Troubleshooting Tips
- Use a SAML debugger (e.g., SAML-tracer, Fiddler) to inspect the SAML assertion.
- Verify that the
NameIDin the SAML response matches theonPremisesImmutableIdattribute of the Entra ID user. - If Azure redirects you back to the IdP after authentication, review Conditional Access policies — they may require MFA claims not asserted by the IdP. If the MFA has not been enforced at the client policy level, the MFA claim is not returned.

