Overview & Concepts
Building a Unified IAM Infrastructure
In large organizations, consolidating Identity and Access Management (IAM) systems from different vendors across various locations is a daunting and often impractical task. This is especially challenging for corporate groups and companies that frequently acquire new subsidiaries, resulting in fragmented information systems. Consolidation projects are typically long, costly, and rarely yield the expected results, leaving behind a mix of well-integrated systems and legacy systems that still need to function.
RCDevs addresses these challenges by offering a federated approach to IAM and Identity Provider (IdP) management. The RCDevs solution federates multiple IAM systems, integrating them into a cohesive meta-IAM platform. This top-level meta-IAM provides a unified view of all the underlying IAM systems, allowing seamless integration with cloud or on-premises services like email, VPNs, and OpenID Connect (OIDC). With this approach, there's no need for complex IdP cascading or password management, simplifying the IAM consolidation process.
For example, consider a corporate group, MyCorp, which has acquired two companies—one using DUO and the other using local Active Directory (AD) systems—while MyCorp itself uses PingOne. RCDevs creates a meta-IAM that aggregates these disparate systems into a unified platform. This enables cross-IAM application access policies, unified UPN naming conventions, and centralized IdP services across the entire organization.
WebADM and External IAM Integration
With the introduction of WebADM version 2.3.20, RCDevs enhanced its platform with native integration capabilities for external IAM providers. This feature allows organizations to synchronize accounts and groups from their cloud IAM providers into WebADM’s LDAP tree. The synchronization is one-way—from the external IAM provider to WebADM—preserving group memberships and allowing external identities to be added to locally defined groups within WebADM.
This functionality is especially beneficial in scenarios like mergers and acquisitions, where multiple IAM systems need to be unified. By synchronizing identities from various sources, WebADM creates a centralized user directory, enabling consistent security policies, seamless IT management, and group-based access control across the entire organization.
The benefits of this approach include simplified identity management, enhanced security and compliance, flexible group management, cost efficiency, scalability, and an improved user experience through a unified access platform.
In summary, RCDevs and WebADM provide powerful tools for overcoming the complexities of managing multiple IAM systems, enabling a cohesive, secure, and scalable identity management infrastructure.
Actions/permission required on DUO admin
Create DUO Admin API application
Login to your DUO Admin portal.
To perform operations such as locking a user account or retrieving user and group information using DUO APIs from WebADM, you'll need to create and configure an Admin API application. Click on Applications in the left tree, then click on the Manage Applications menu. On the next page, click + Add under Admin API.
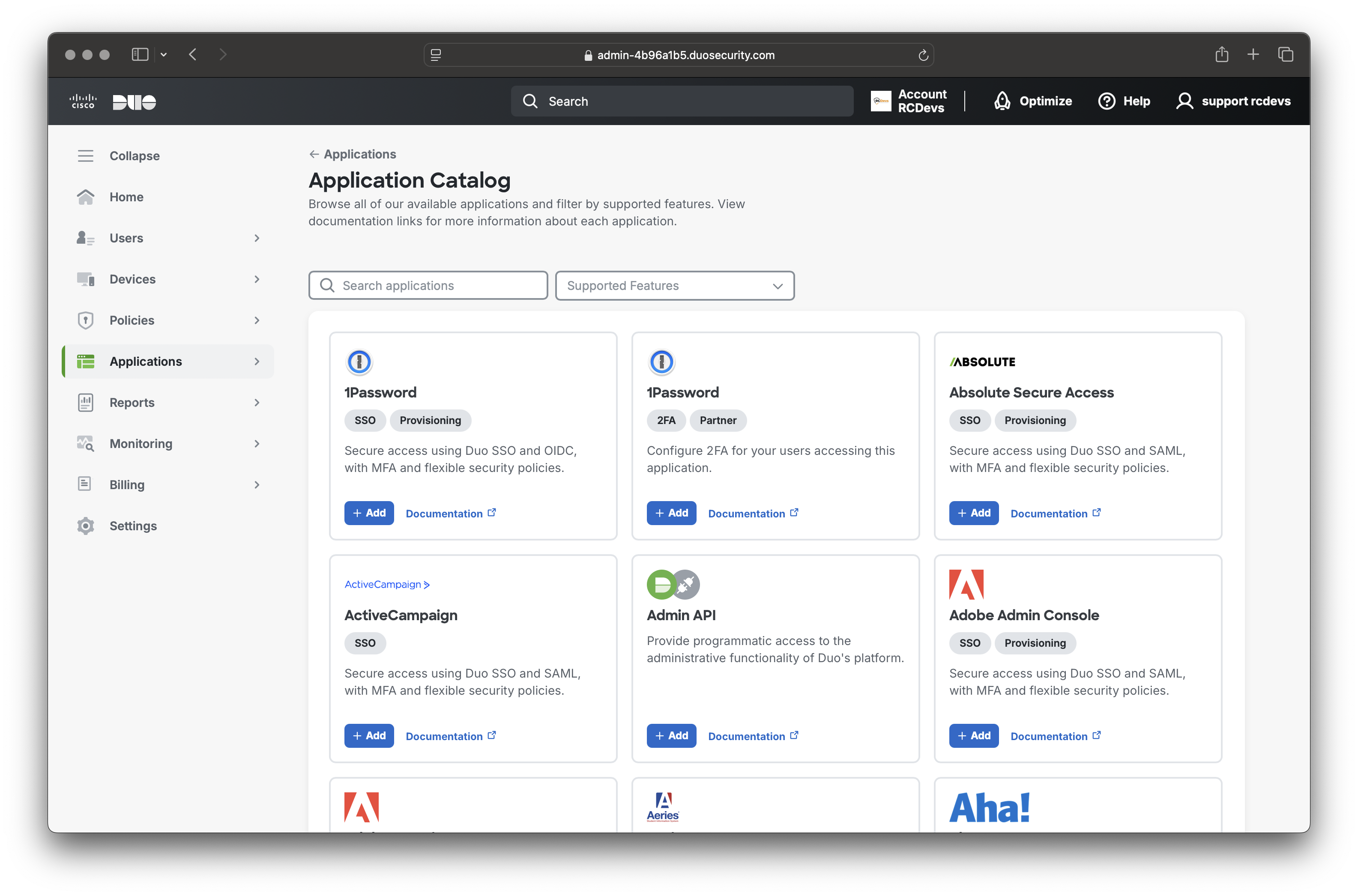
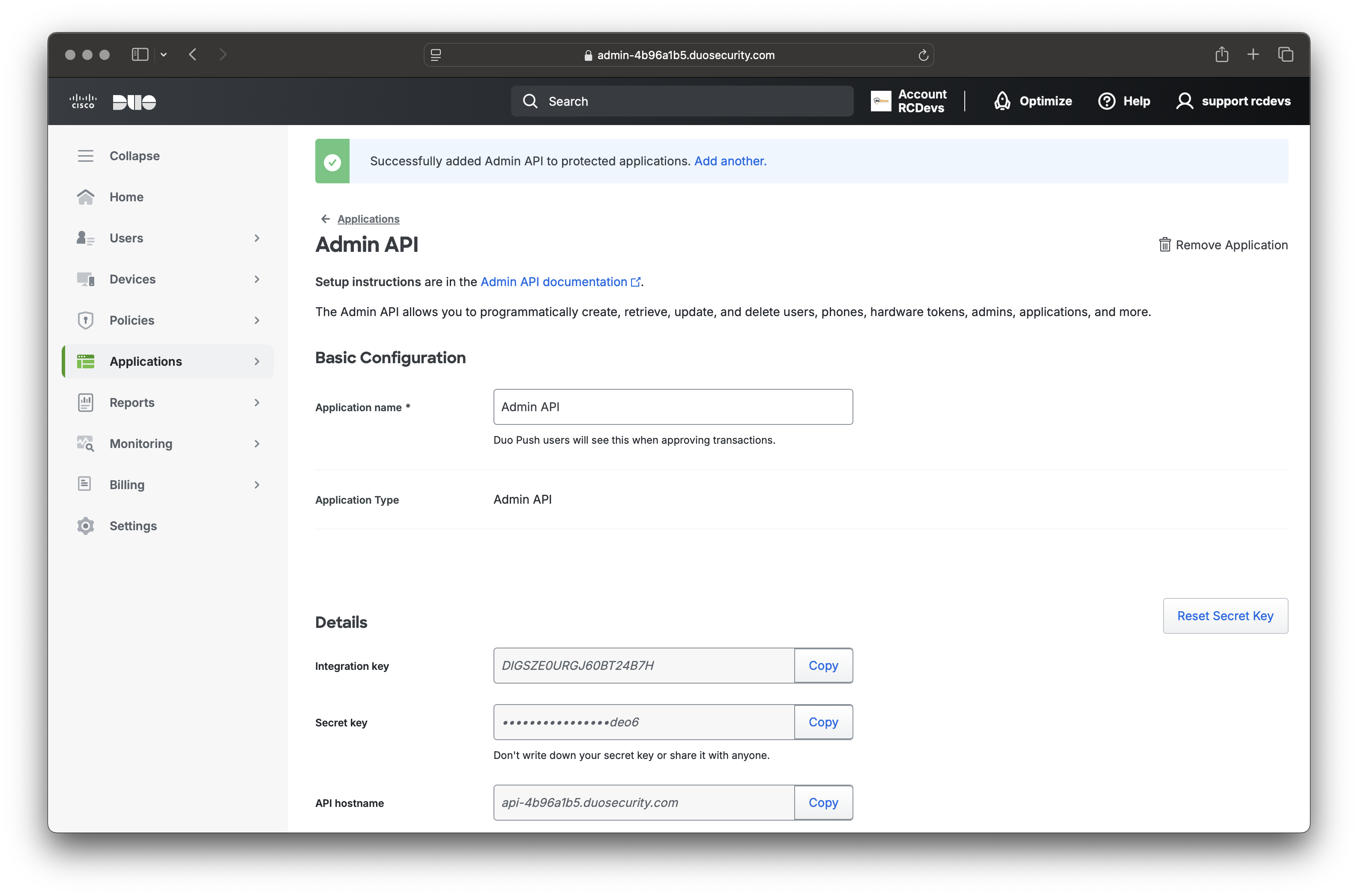
Name your application. The information provided in the Details section will be needed later when setting up your DUO tenant in WebADM.
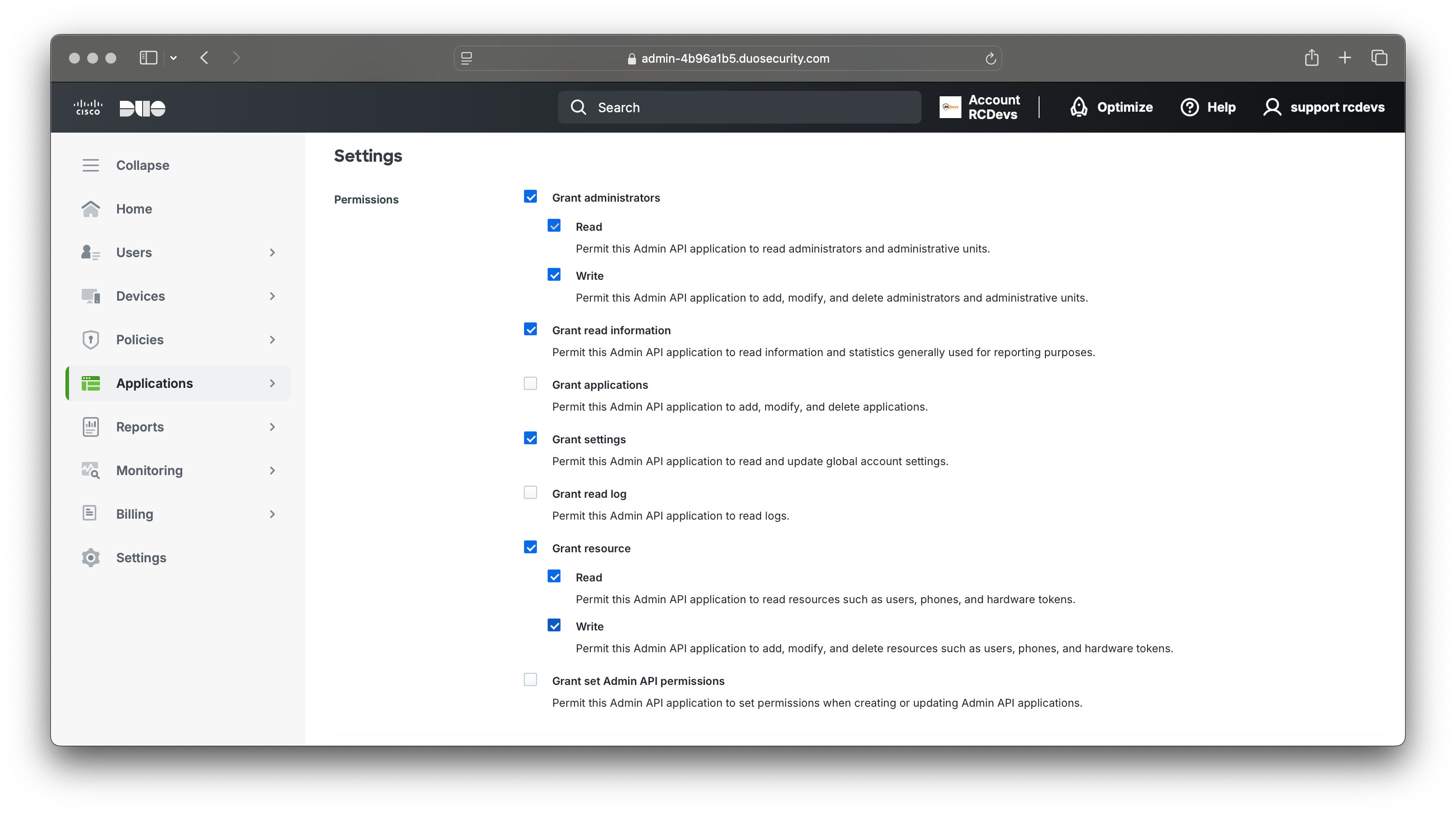
Scroll down and configure the permissions granted to WebADM for object manipulation. In this setup, we are enabling Two-Way Synchronization, so we will grant write permissions to this API application. This allows WebADM to edit user attributes and have those changes reflected in DUO objects.
Scroll down and save your configuration.
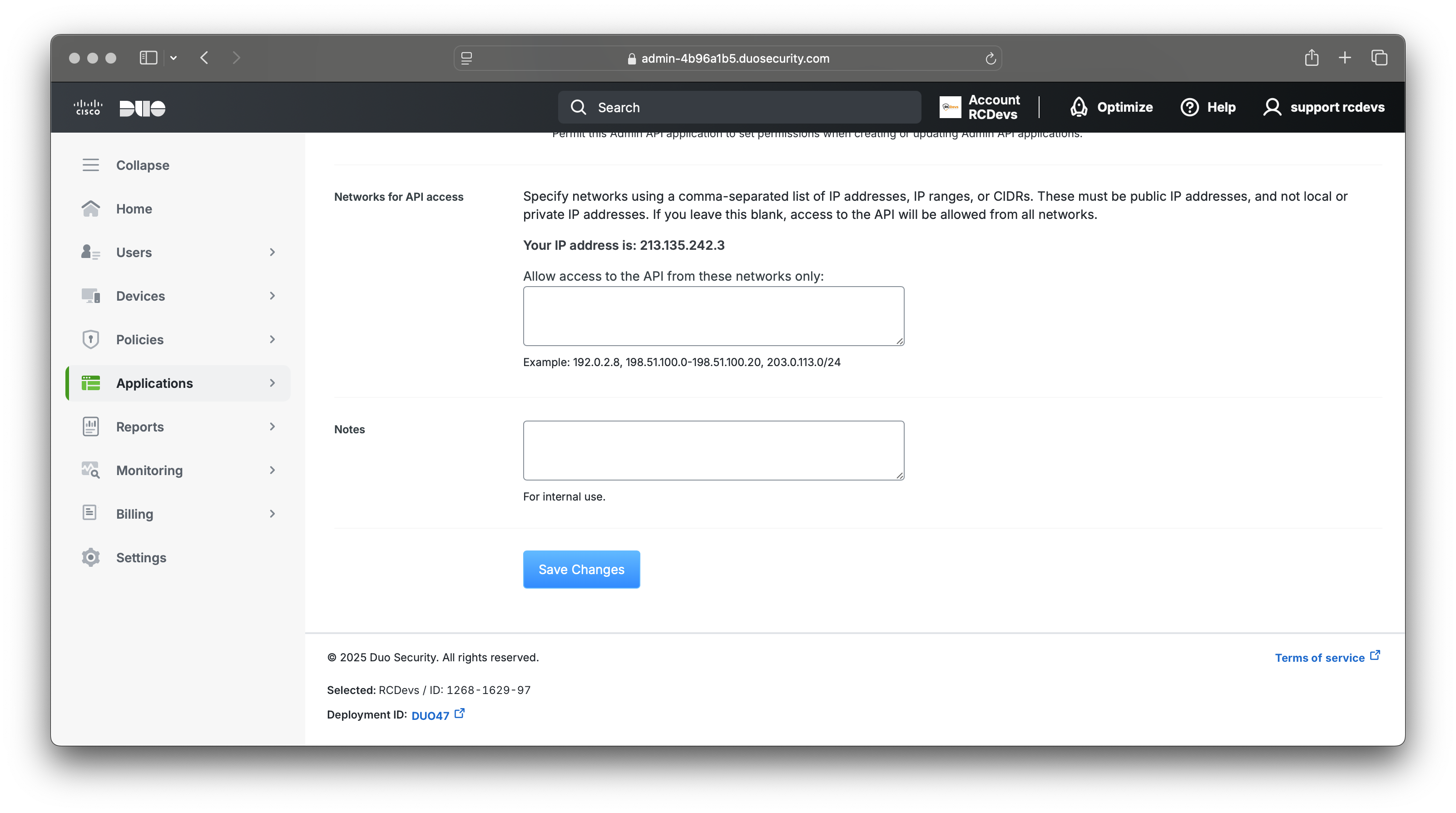
DUO API Application is done.
DUO configuration on WebADM
The DUO configuration on WebADM consists of:
- Creating a Container, Organizational Unit, or Organization object in your LDAP tree where the DUO tenant will be synced.
- Creating a WebADM
User Domainsand configuring the tenant information of your DUO tenant.
Container Creation
Let's first create the container where objects will be synced in.
Login on the WebADM Administrator Portal with a super_admin account, and click on the Create tab.
In this example, we create an Organization object named DUO inside an existing Organization object named External Providers
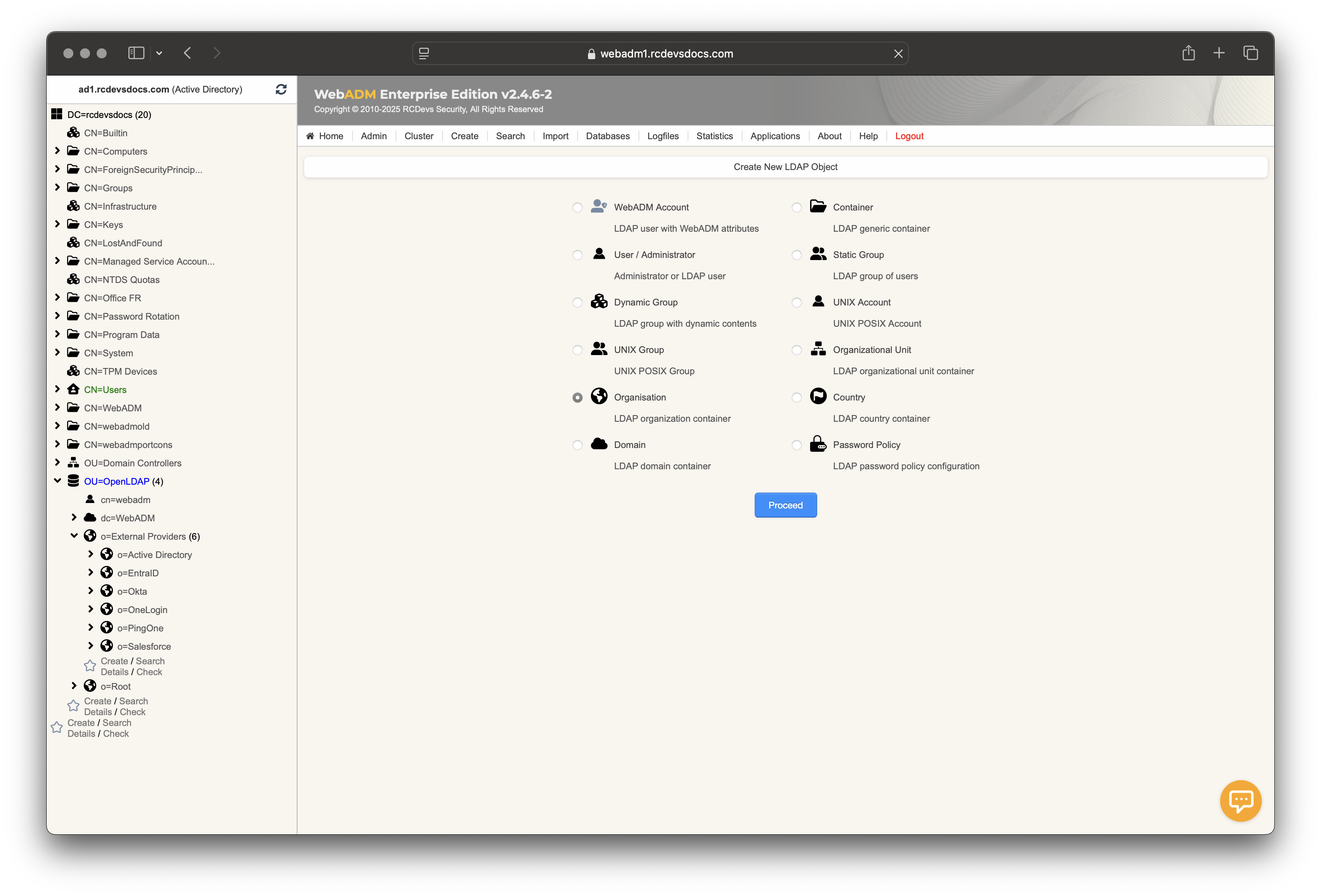
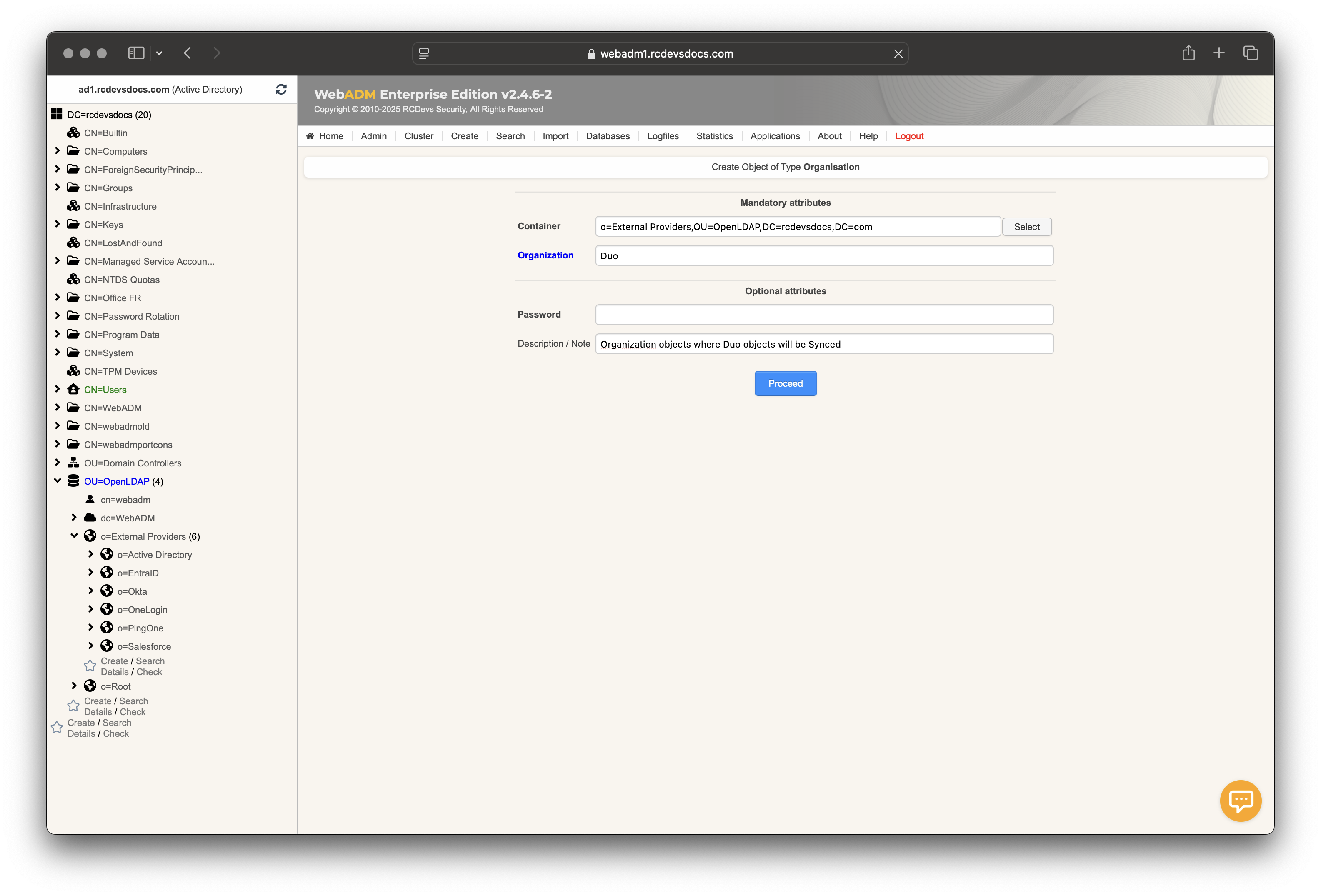
Name your organization object and click Proceed and then Create object.

Your Duo organization object is created.
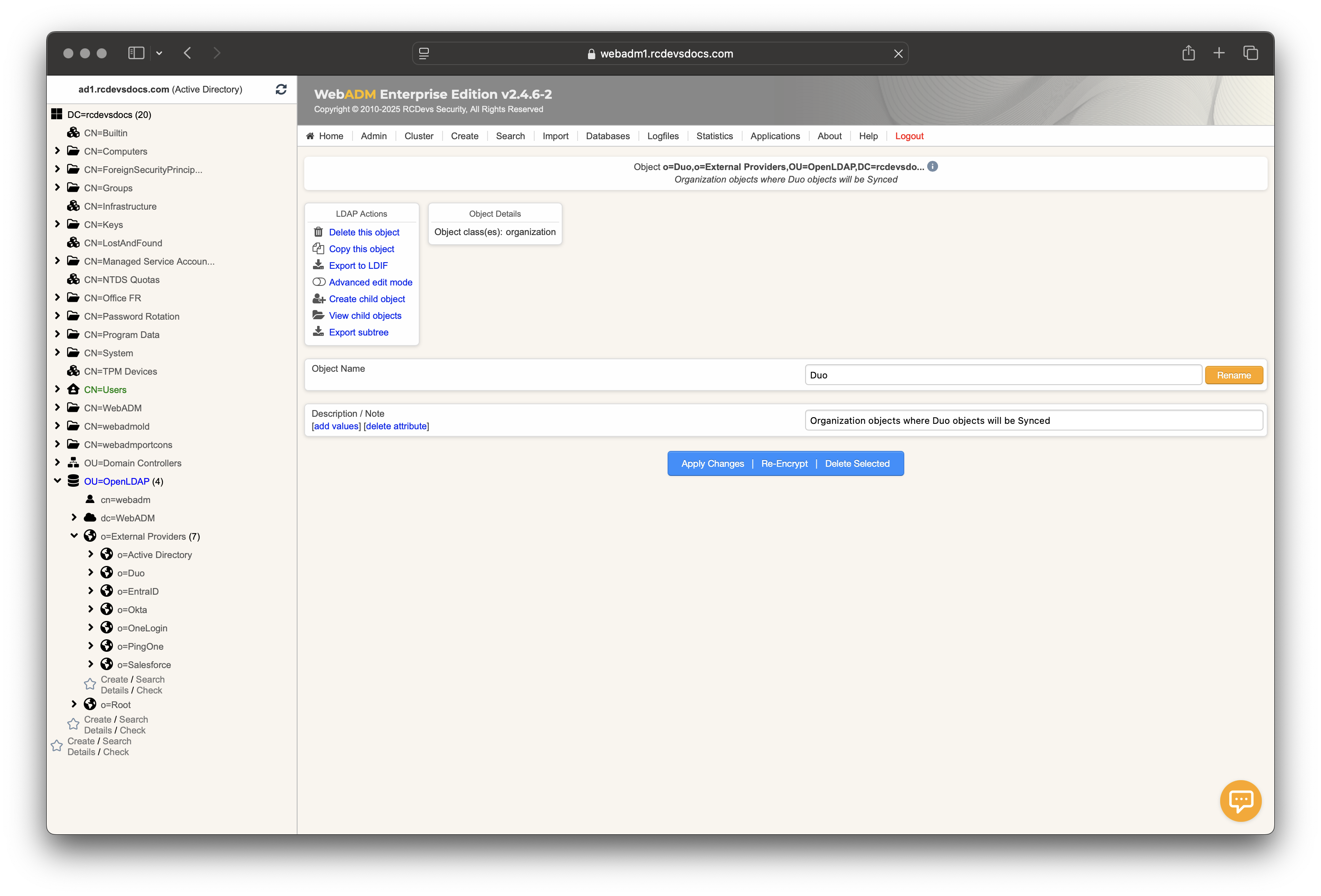
You can optionally create Users and Groups containers/OU to separate users and groups during the synchronization process.
Domain Creation and Configurations
This section provides a clearer understanding of the UPN mode available in WebADM Domains. The example mentions Entra ID, but the principle is exactly the same for all cloud directories.
Username/UPN Concepts
The WebADM User Domain creation involves configuring the following key settings:
- The
User Search Base - The
UPN Modeand optionally theUPN Suffixwhen the UPN Mode is set toExplicit. - The
Directory Synchronizationsettings
When configuring the UPN Mode, you are determining how the login name value will be synced in the login attribute.
Example for Clarification
Consider the UPN (User Principal Name) of an DUO account: testaccount@duo.com.
testaccountis the UPN prefix.duo.comis the UPN suffix.
UPN Mode: Implicit vs Explicit
The UPN Mode can be set to either Implicit or Explicit. Here's how each mode works:
-
Implicit Mode:
In this mode, thetestaccountvalue (the UPN prefix) will be stored in the login attribute. With this mode, users can authenticate using two different methods:- By providing
username=testaccountanddomain=WebADM_Domain_Name_or_UPN_Suffixto the OpenOTP APIs. - By constructing a UPN with the
UPN Suffixconfigured in the WebADM domain object they belong to and logging in asusername@upn_suffix.
- By providing
This mode is the most flexible.
The UPN suffix can also be configured to work with the full UPN, even if it's not synced into the uid attribute.
- Explicit Mode:
In this mode, the full UPN (testaccount@domain.com) will be stored as the login attribute (Active Direcotory usecase). In this case, users can use the full UPN as their username to log in. Thetestaccountvalue (UPN prefix) can also be used for authentication. This mode is not supported with DUO. ChooseImplicitmode if you want to use contructed UPNs for login name values.
Now that you fully have the concepts, we can continue by creating the WebADM User Domain object and configuring the information for Duo.
Go to the Admin tab, select User Domains box, and click Add Domain. Provide a common name to identify the cloud provider, such as Duo, and optionally add a description. Then, click Proceed followed by Create Object.
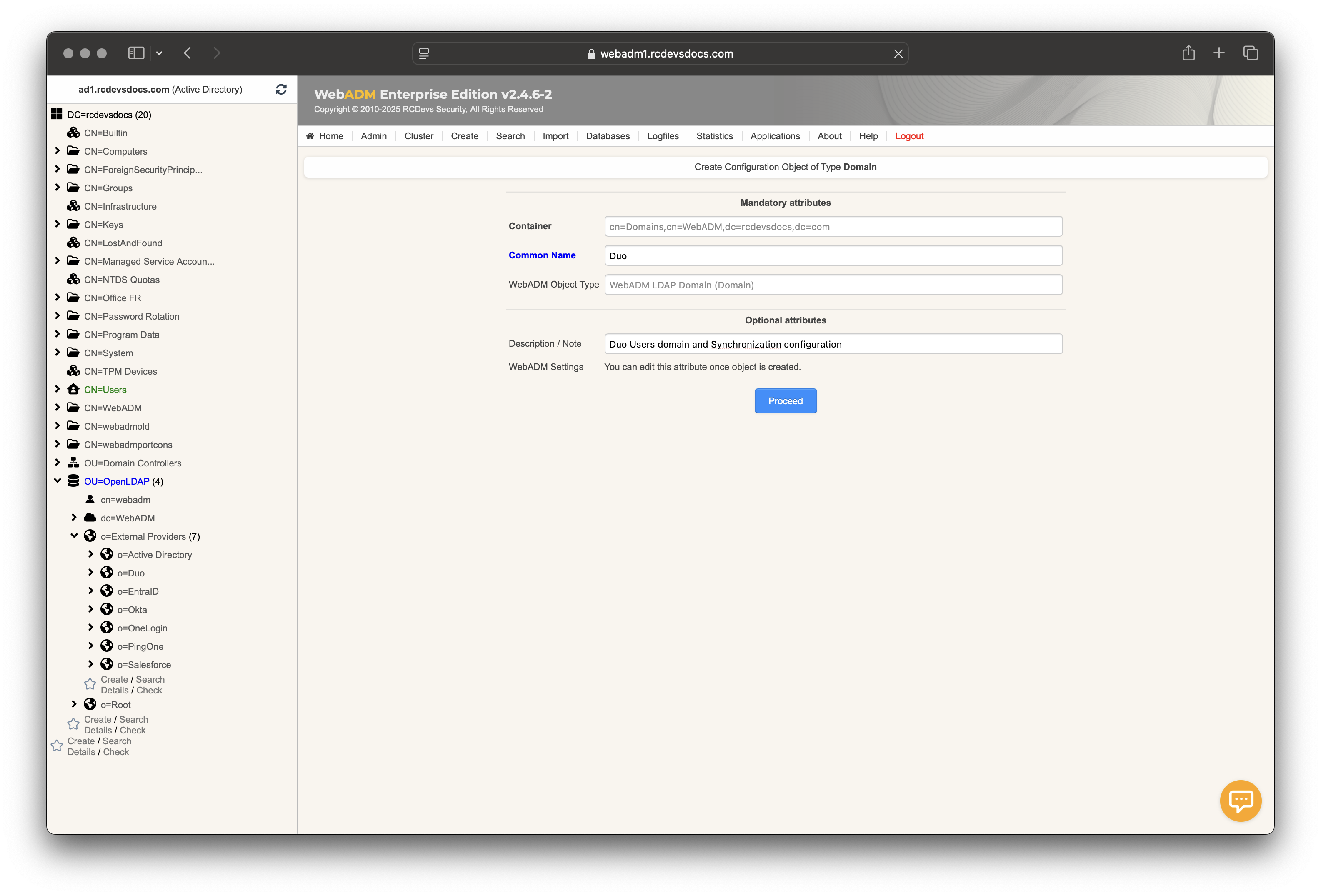
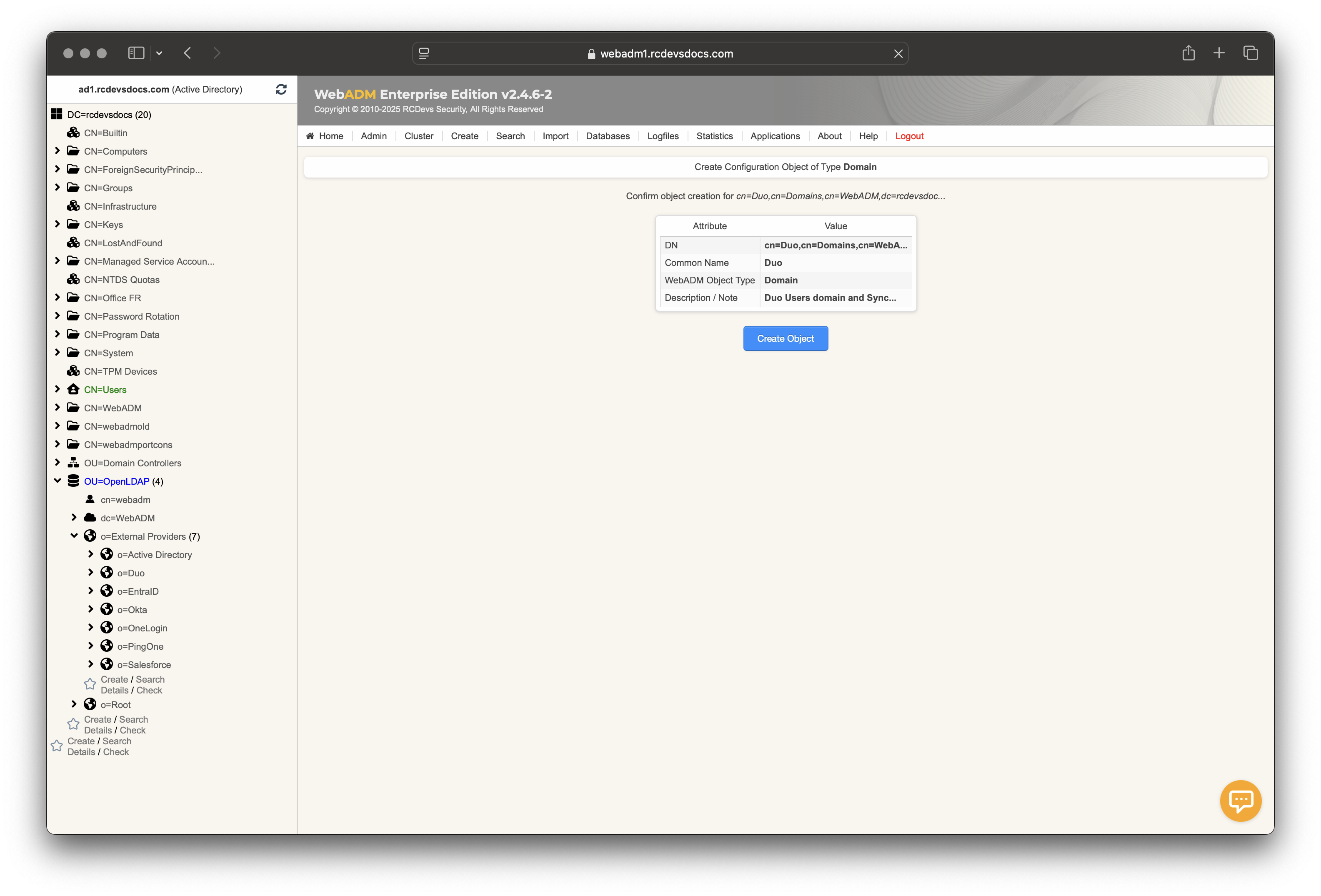
The domain object is created, and you will enter the User Domain configurator. In the first section, configure the User and Group Search Bases to point to the Organizational Unit (OU) you previously created.
Configure the UPN Suffix (e.g. duo.com) and set the UPN Mode to Implicit, or leave both settings blank.
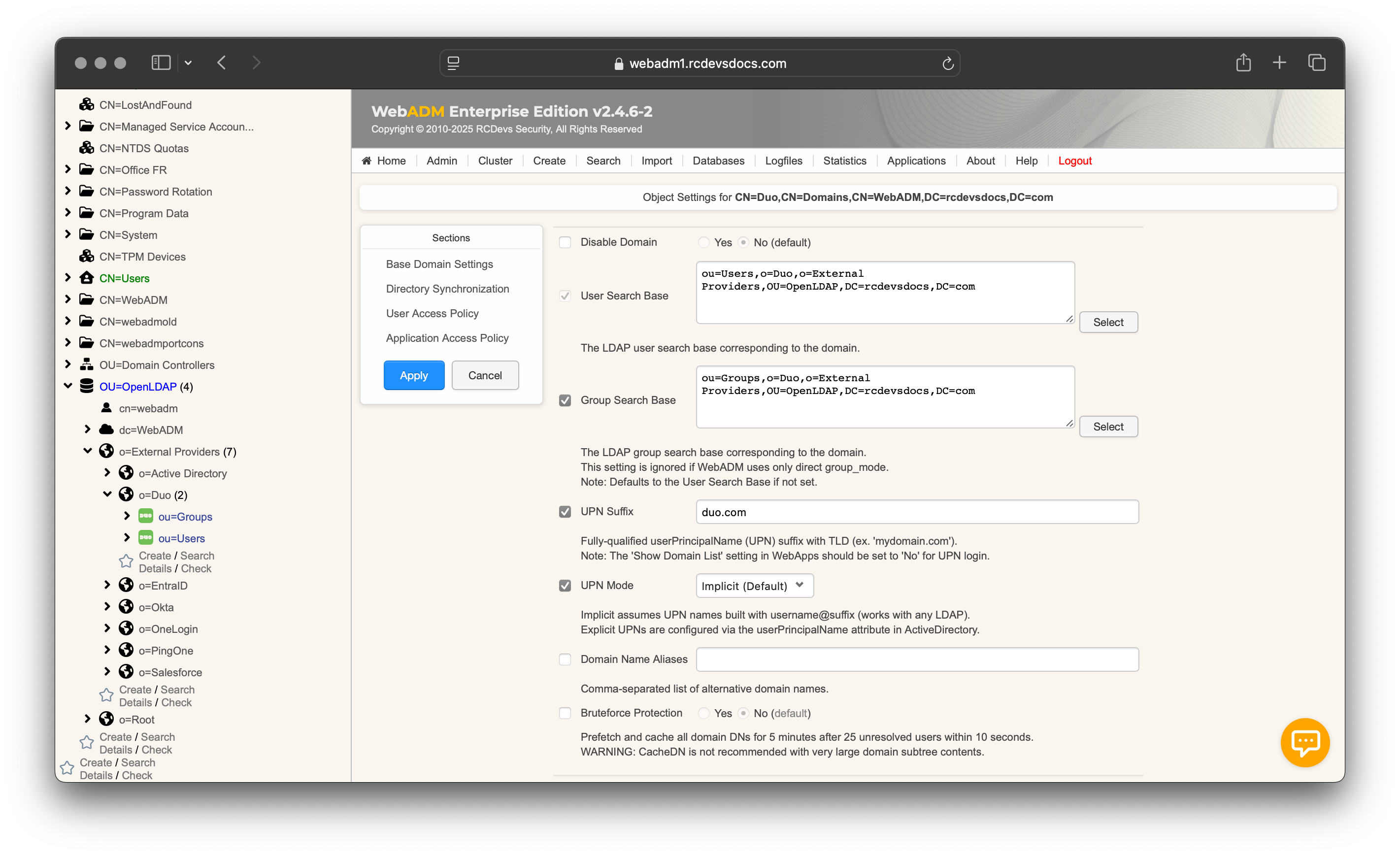
Scroll down to the Directory Synchronization section to fill in the following information:
- In the
Providersetting, selectDUO. - In the
Tenant IDsetting, enter your tenant identifier, which can be retrieved from your Duo tenant or from your tenant URL. - The
Client IDsetting must contain the integration key from the DUO Admin API. - In the
Secret Keysetting, enter the secret key from the DUO Admin API. - The
User Password Modecan be configured toLocalto manage account passwords locally for synced accounts.Remoteis not possible with DUO, as DUO does not store any passwords. - Choose the
Sync Optionsthat best suit your preferences. The most important setting to enable is TwoWay, as this allows you to manage users and groups from WebADM and have these changes reflected in your DUO tenant. - Finish by setting the
Sync Period. By default, synchronization occurs every hour.
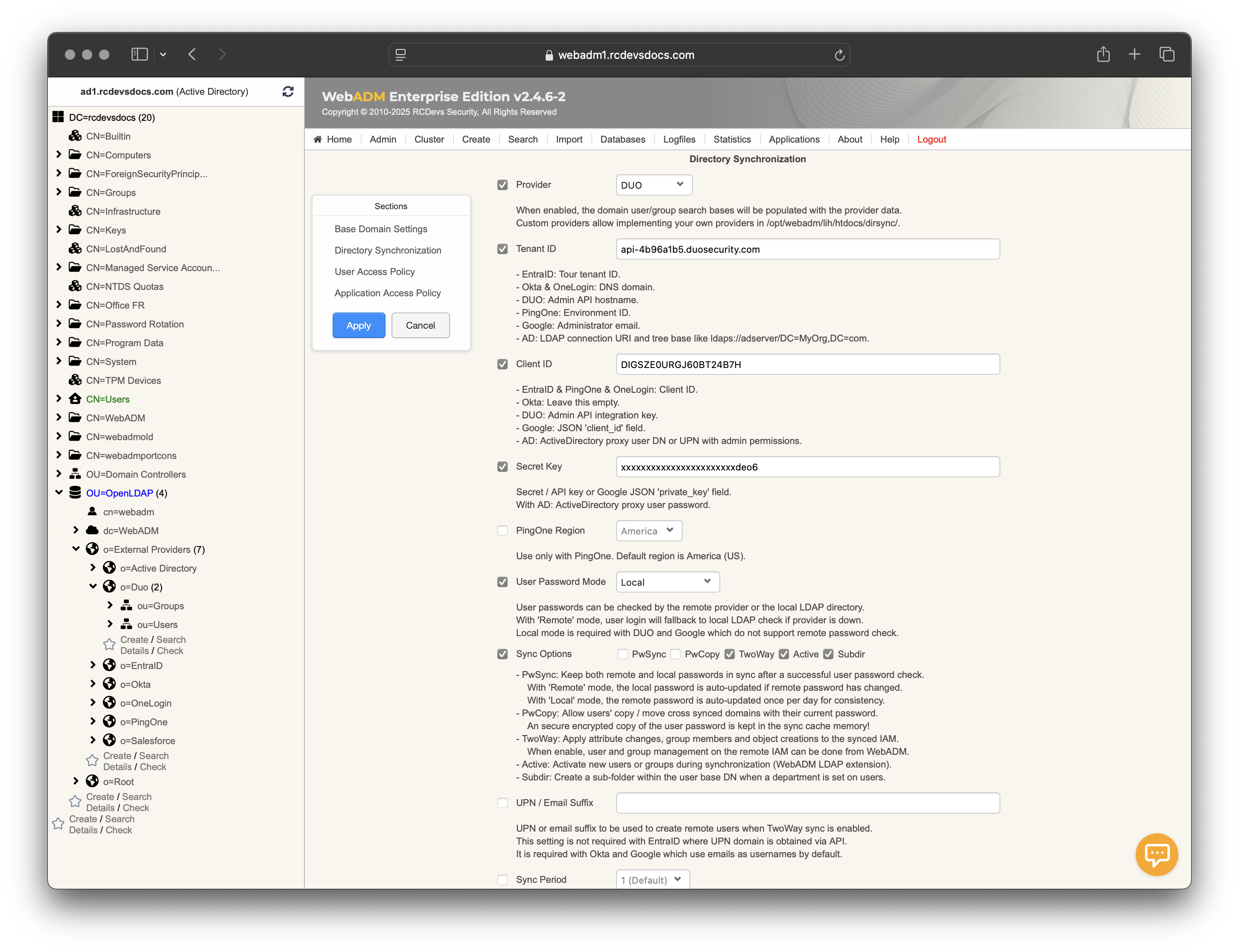
The required information can be retrieved from Duo:

When the configuration is complete, click Apply to save your settings. You will be redirected to the Registered LDAP Domains menu, where your Duo domain should appear with a Sync Now button.
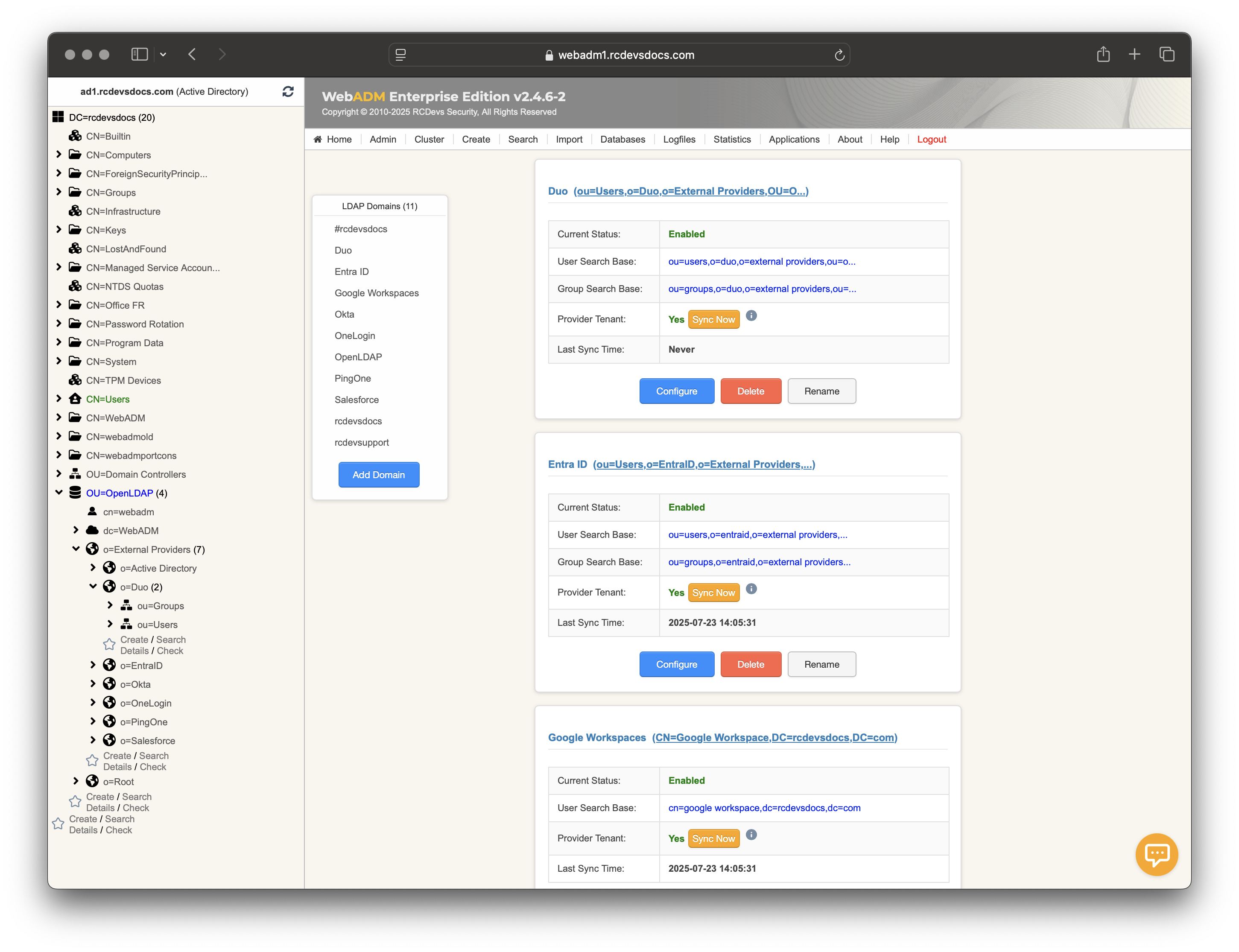
Click on Sync Now button and the synchronization starts.
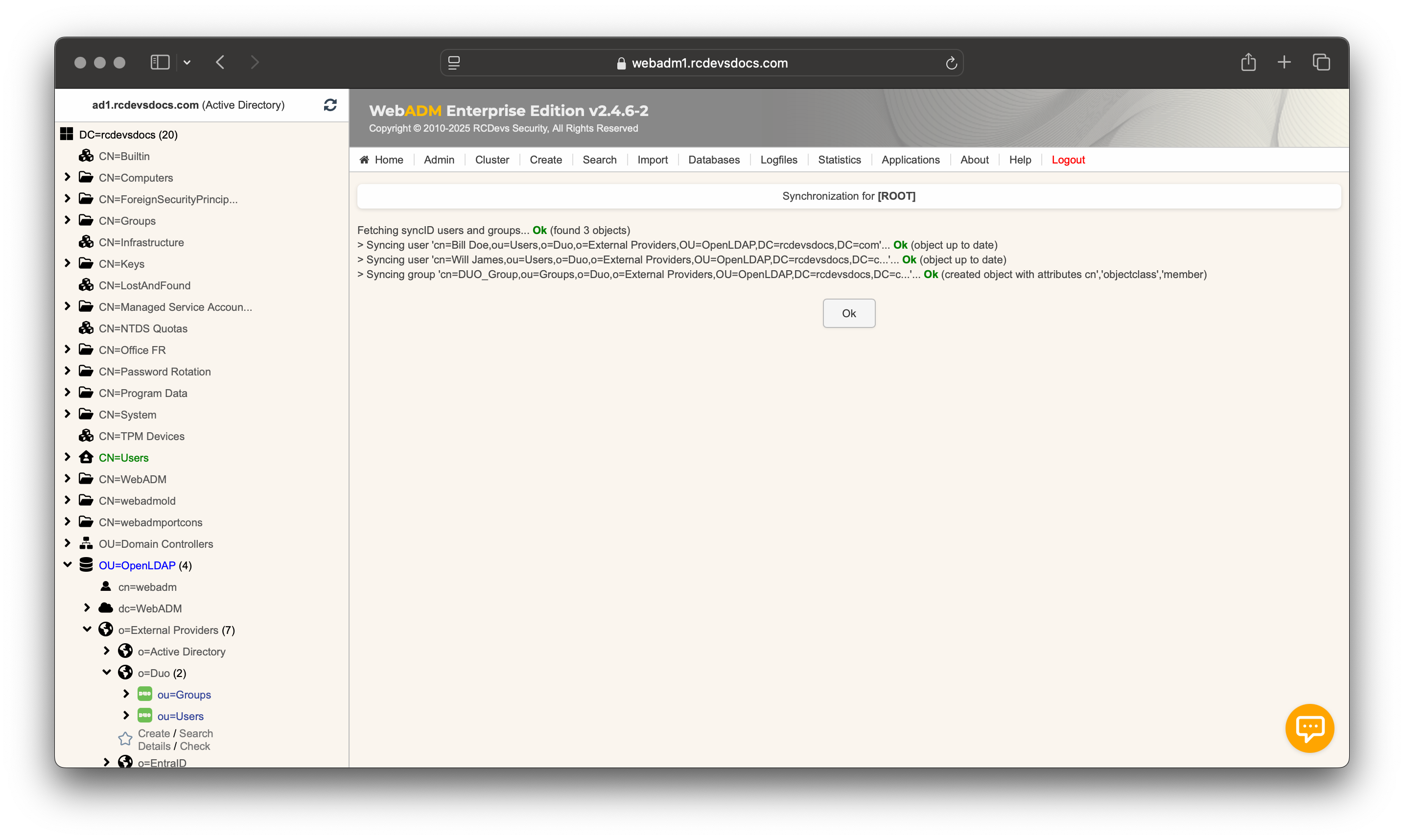
If any objects cannot be synced for any reason, an error message will appear in the synchronization output. For more details, consult the WebADM Server logs. Objects that have been successfully synced will appear in the left LDAP tree
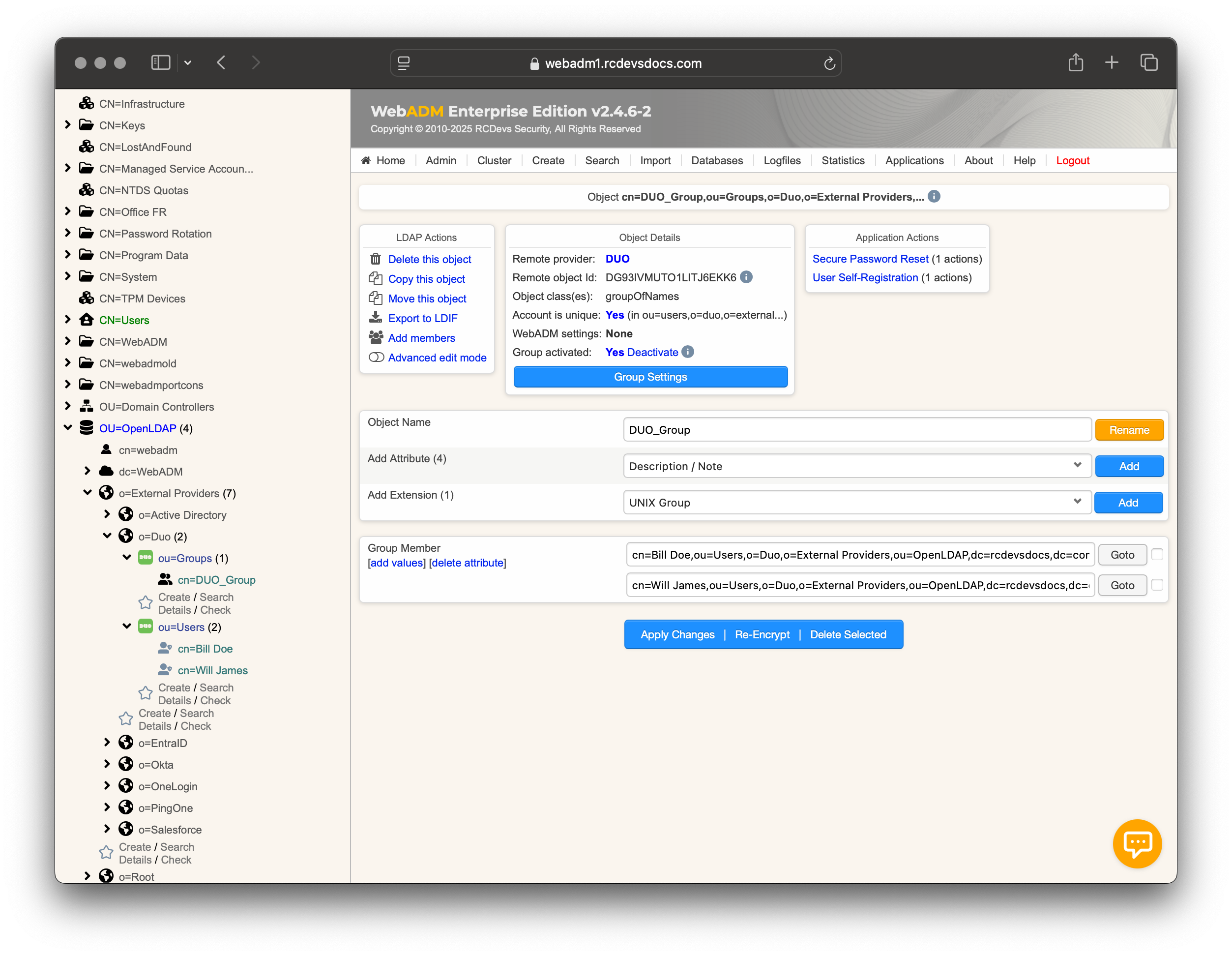
That's it. The synced identities and groups can now be used with WebADM, along with its dependencies and integrations.
Sync‑Option Cheat‑Sheet
| Option | What it does | Remarks & Caveats |
|---|---|---|
| TwoWay | Pushes attribute / membership edits made in WebADM back to DUO. | The permission given to the Admin Application API must have the necessary write ACLs. |
| Active | Activates newly imported users or groups at the end of the sync. | Activating a user consumes an OpenOTP licence; activating a group enables WebADM group‑policy evaluation. |
| Subdir | Builds department‑based sub‑folders under the User Search Base. | Perfect for large tenants: HR updates department in AD → user is moved to the matching OU automatically. |
Attribute Mapping
All attributes below are bi‑directional when TwoWay is enabled.
| RCDevs attribute(s) | Duo field / object | Notes & Caveats |
|---|---|---|
| sn | lastname (user) |
Direct one‑to‑one mapping. |
givenName ( givenname ) |
firstname (user) |
Case‑insensitive attribute name. |
Every attribute listed in ['mail_attrs'] in webadm.conf(e.g. mail, email, rfc822Mailbox, …) |
email (user) |
First non‑empty value wins; extra values are ignored. |
| uid or sAMAccountName | username (user) |
Handled outside the static map; local suffix is replaced by Duo tenant suffix. |
Attributes in ['mobile_attrs'] in webadm.conf(e.g. mobile, telephoneNumber, …) |
phone number (separate Phone object) | Existing phone links are wiped, then the number is re‑attached; only one number per user is kept. |
| description (on a group) | desc (group) |
Only attribute explicitly mapped for groups. |
| cn / supplied group name | name (group) |
Set when the group is created; not part of the static mapping array. |
Group Synchronisation
One‑Way Sync (Default)
- Group structures and memberships are imported from DUO into WebADM.
- Synced groups in WebADM are read-only; any manual changes are automatically overwritten during the next synchronization.
- Only direct group memberships are synchronized (member attribute).
- Nested groups are supported via the member attribute.
- The memberOf attribute is calculated with DUO and is not writable; RCDevs Directory/OpenLDAP uses the same mechanism.
- If you require custom group configurations, you can create local groups within WebADM and manually assign imported users.
Two‑Way Sync
- Groups can be created, renamed, or deleted directly in WebADM, and these changes are pushed back to DUO.
- When creating a new group, WebADM prompts: “Local object only?”
- Select Yes to keep the group local (not synced to DUO).
- Select No to enable synchronization, making the group editable in both WebADM and DUO.
Visual Indicators in WebADM
- Green objects → synced with an external IAM (AD via LDAP Connector).
- Red objects → local only.
With Two‑Way mode enabled, you can set an auto‑deletion date (under LDAP Actions) for any user. On that date the account is removed from both WebADM and DUO.
