Overview
This document will demontrate how to install and configure RCDevs Identity Provider (IDP) for SAML and OpenID Connect (OIDC) Service Provider (SP) integrations. Authentication on the IDP is done through the OpenOTP authentication server. The RCDevs IDP is a web application installed on all WebADM servers part of the same cluster. The IDP portal can be published through WebADM Publishing Proxy (WAProxy) or your reverse proxy to be publicly accessible.
OpenID/SAML application logs are accessible from the Databases menu of WebADM > WebADM Server Log file or WebADM Shared event log.
Note: To be able to use OpenID/SAML, any LDAP users' accounts must be a activated in WebADM.
You can embed the OpenID & SAML Provider Webapp on your website in an HTML iFrame or Object.
#Example
<object data="https://<webadm_addr>/webapps/openid?inline=1" />
For this setup, you need to have a WebADM and OpenOTP server already installed and configured.
Package installation
Installation with Redhat Repository
On a RPM based systems, you can use RCDevs repository.
Clear the dnf cache and install the OpenID & SAML provider (openid) package:
dnf clean all
dnf install openid -y
RCDevs Identity Provider package is now installed.
Installation with Debian Repository
On a Debian-like system, you can use RCDevs repository.
Clear apt cache and install the OpenID & SAML provider (openid) package:
apt update
apt install openid
RCDevs Identity Provider package is now installed.
Installation with the Self-Installer
Download the RCDevs Identity Provider self-installer package from the RCDevs website and copy the downloaded archive to your server(s). To install the OpenID & SAML provider, log in to your WebADM server through SSH and run the following commands to uncompress and install it:
gunzip openid-1.6.x.sh.gz
bash openid-1.6.x.sh
Once the openid package is installed, you can login on WebADM Administrator Portal as super_admins to configure it.
OpenID & SAML Identity Provider configuration
Log in to the WebADM Administrator Portal, click on the Applications tab, and navigate to the Single Sign-On category. The OpenID & SAML Provider should appear there with a status of Not Registered.
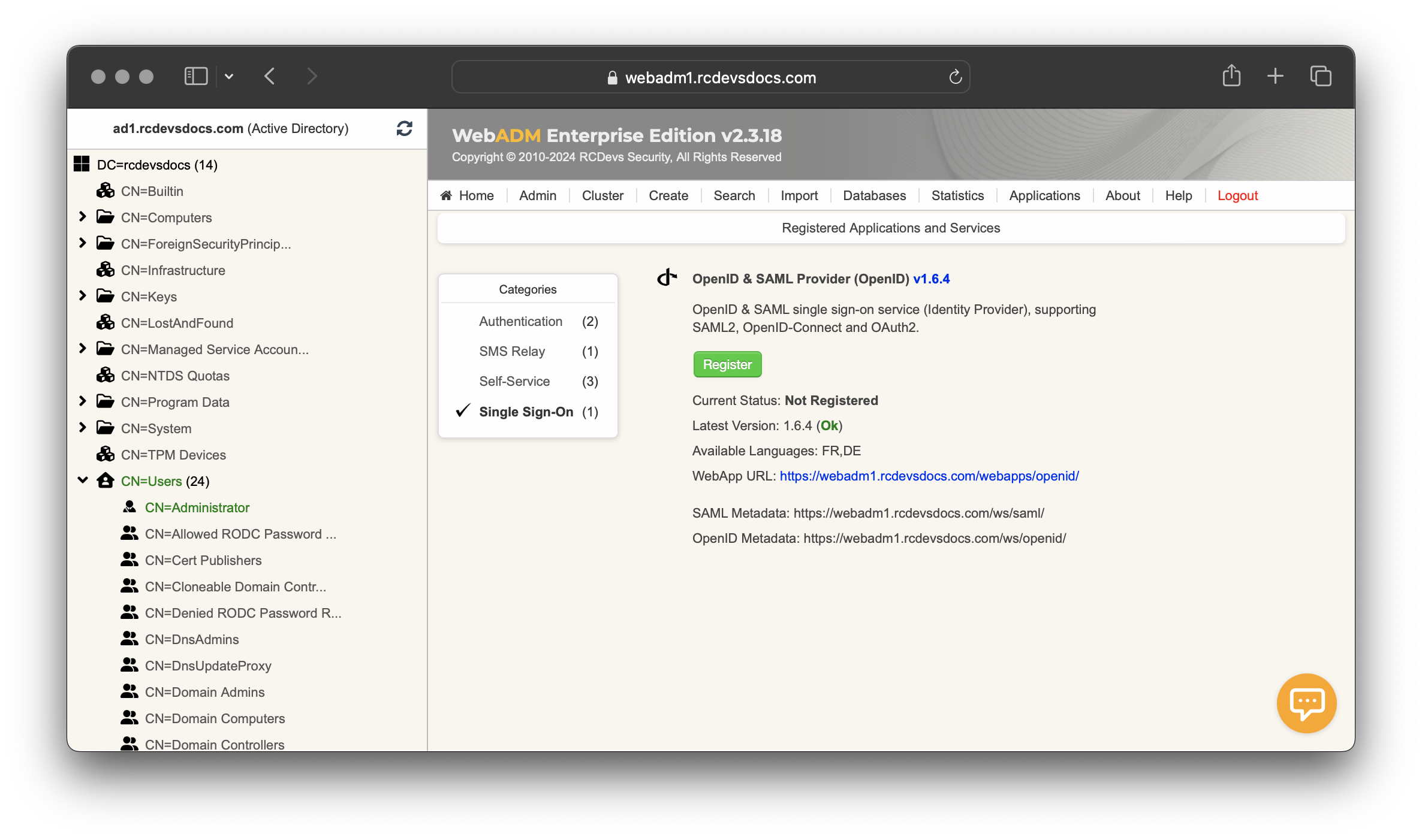
Click on the REGISTER button to create the corresponding LDAP object which will contain the web application configuration.
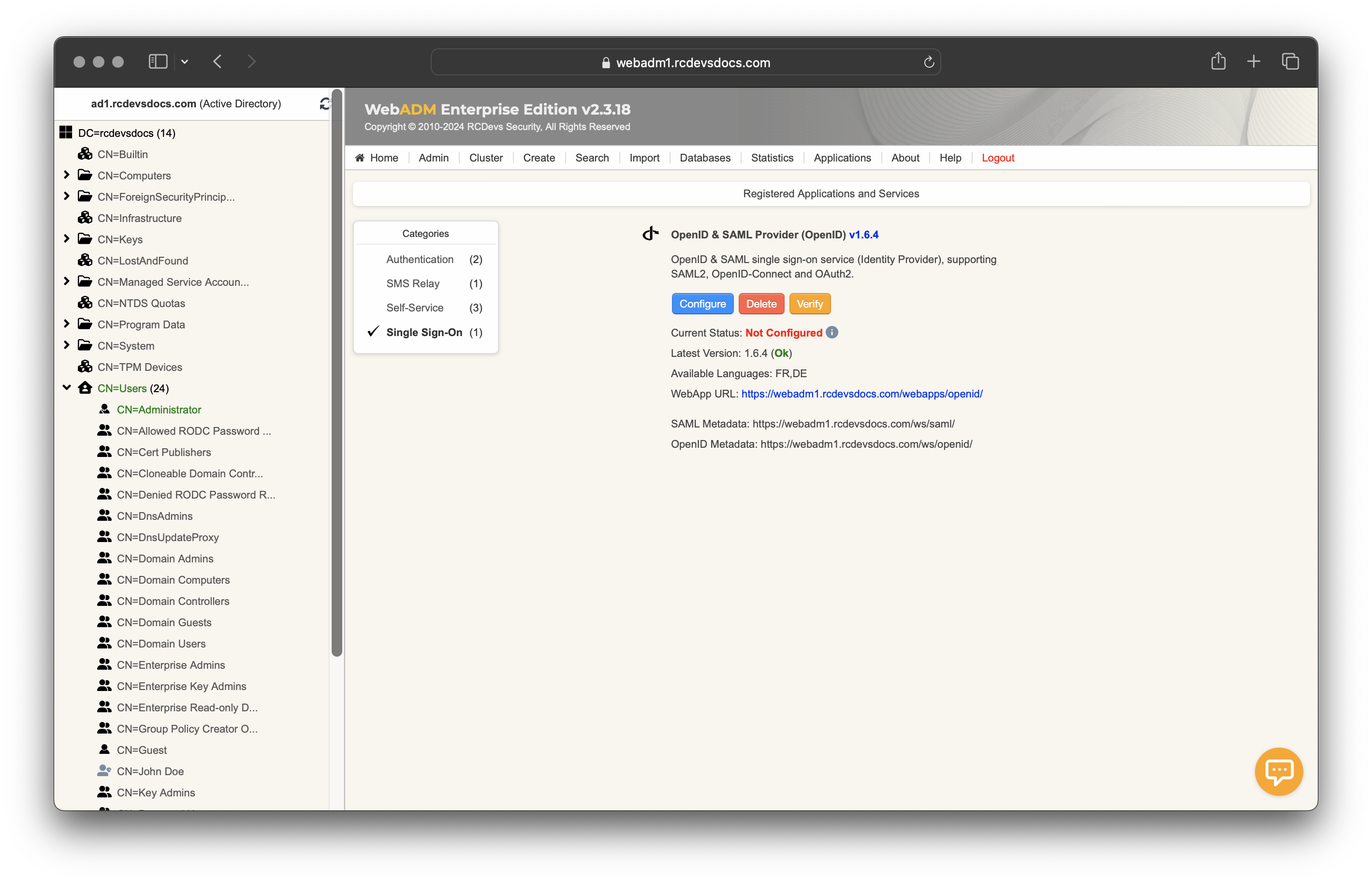
Next, navigate back to the WebADM Administrator Portal, click the Applications tab, and select Single Sign-On from the Categories.
Click the CONFIGURE button next to OpenID & SAML Provider to configure the web application and its services.
Web Application Settings and Common Features
You are now in the global configuration of your OpenID & SAML Provider.

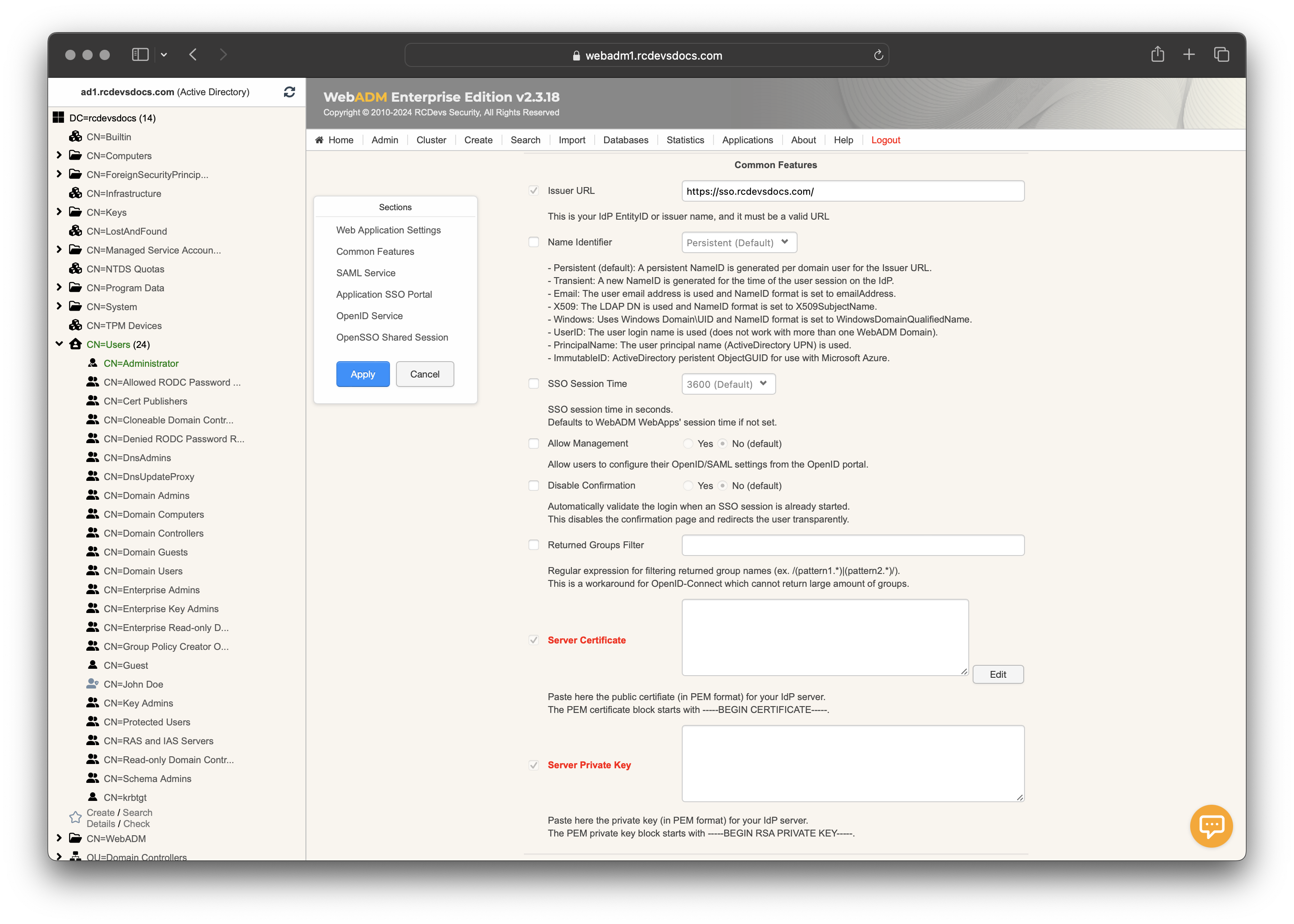
The first section of settings is common across all web applications. Configure the settings you would like to apply.
Scroll down, and you are now entering in the Common Features section. The Common Features section includes common settings for OpenID and SAML Providers.
-
The
Issuer URLorEntityIDis a unique identifier that is used to identify a specific entity in the SAML authentication and authorization protocol. A SAML entity ID is typically a URL or URI that is assigned to the entity, and it is used to identify the entity in SAML messages and metadata. That setting will refer toIssuervalue for OpenID. In that documentation, I configured myIssuer URLwith the public DNS name targeting my WebADM infrastructure. In most of the case, the IDP URL will be a public URL which can be easily proxied with WebADM Publishing Proxy or with another reverse proxy solution. Be careful that the latter must allow the big URI query strings that are sometimes necessary in SAML, so e.g. users of AWS WAF should change SizeRestrictions_QUERYSTRING to Allow or Count. -
The
Name Identifiersetting is the unique identifier of the user. It should be non-volatile and opaque. It should not contain personal information or information that is changeable over time, such as the user's name or email address. The acceptedName Identifiermay vary according to the Service Provider you are integrating and for that reason it can make more sens to configure it per Service Provider throughClient Policies. -
The
SSO Session Timedefine the time for a user session remains valid on the IDP. -
The
Allow Managementsetting provides the possibility to your end-users to enable/disable the SAML/OpenID usage for their account and configure their SSO Session timeout. It is recommanded to disabled that setting by default. -
The
Returned Groups Filteris a regular expression which can be configured in order to filter groups returned in the SAML or OpenID responses based on the RegEx match. -
The
Server CertificateandServer Private Keysettings are mandatory and will be used for request signing purposes. ClickEditandGeneratebuttons, then a certificate with Rsignd internal PKI is issued.

Now that we have the IdP certificate, click on Apply, and the Server Certificate and Private Key will be auto-filled in the configuration.
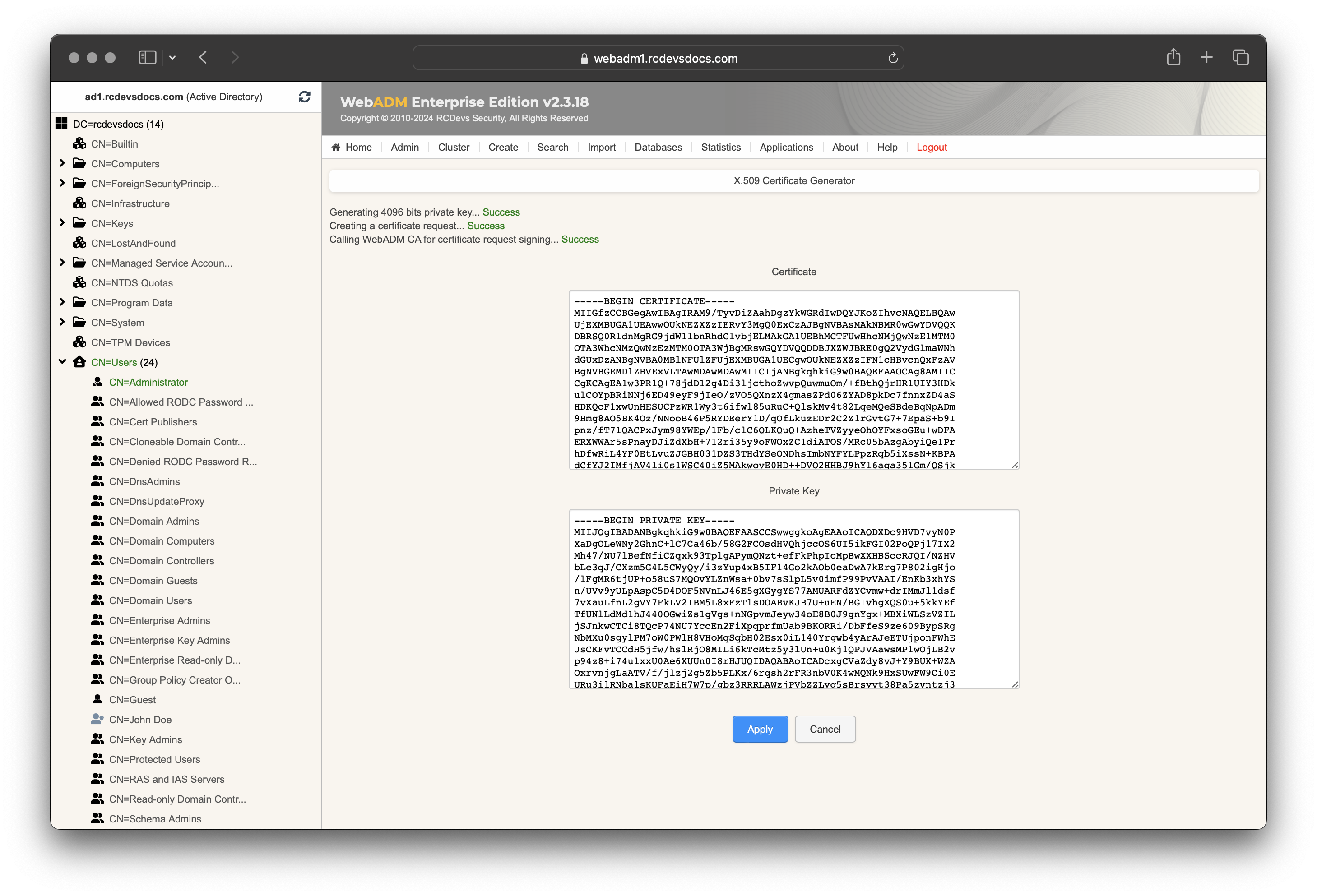
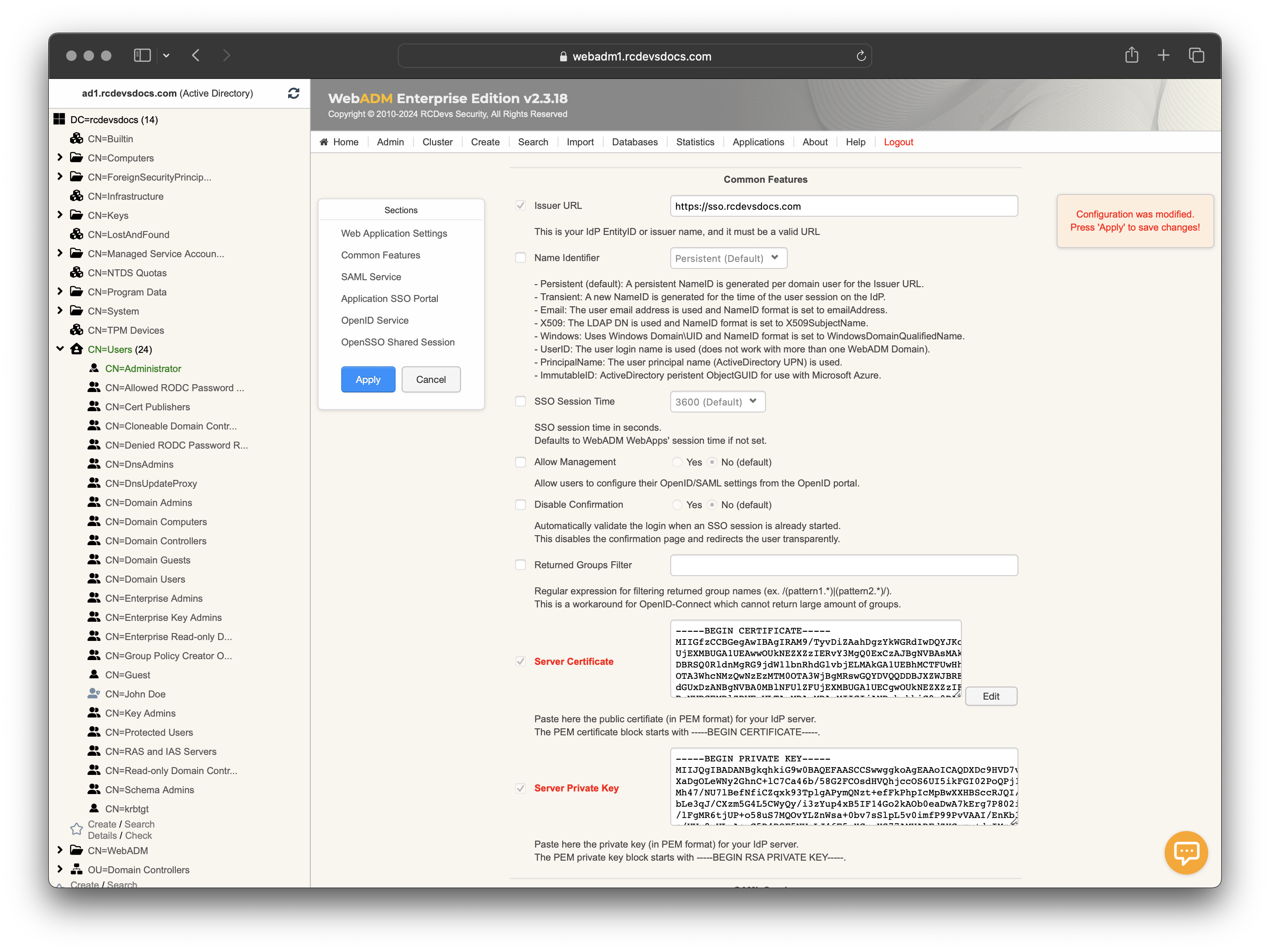
You can also issue a certificate with another Enterprise CA if desired. Note that when the IdP certificate expires, you may need to update the configuration with the newly issued IdP certificate on the integrated service providers.
The Common Features section is now configured. Save your configuration by clicking Apply.
SAML Service Configuration
We are now entering in the SAML dedicated configuration.
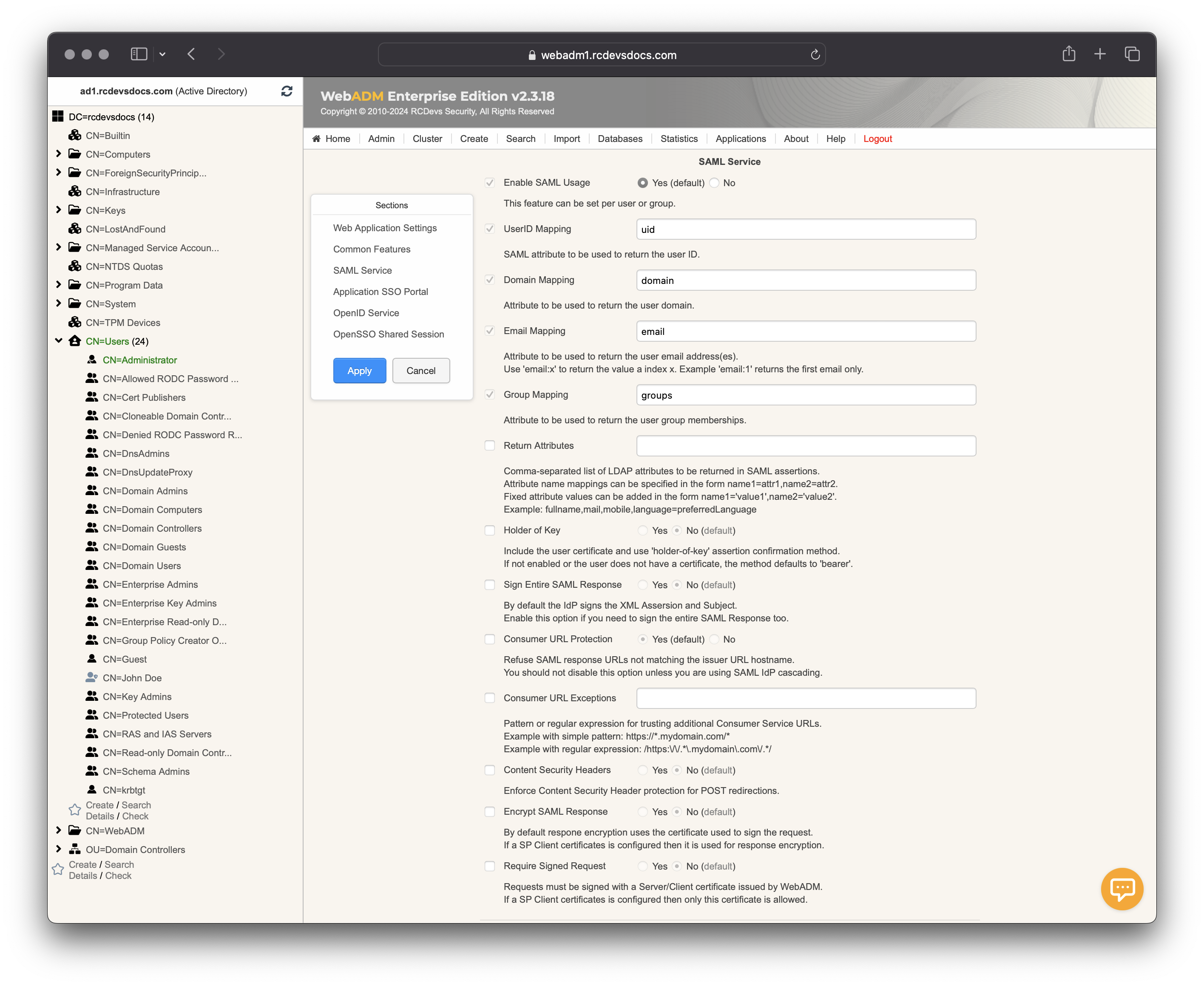
-
The
Enable SAML Usagesetting enable the SAML configuration in order to implement SP through SAML. -
The
UserID Mappingsetting is the attribut value used in the SAML response to return the user ID. -
The
Domain Mappingsetting is the attribut value used in the SAML response to return the domain value. By default, the WebADM domain name is returned based on the domain used to authenticate the user. -
The
Email Mappingsetting is the attribut value used in the SAML response to return the users' email value(s). -
The
Group Mappingsetting is the attribut value used in the SAML response to return the user group memberships. -
The
Return attributessetting is the attribut value used in the SAML response to return a list of desired attributs. You can also manipulate values returned. For example here, I returned in SAML response mobile, displayname sn attributs retrieved from the LDAP account and in userprincipalname I put the user email value. -
The
Holder of Keysetting is used to include the user certificate and use 'holder-of-key' assertion confirmation method. If not enabled or the user does not have a certificate, the method defaults to 'bearer'. -
The
Sign Entire SAML Responsesetting is used to intirely sign the SAML response. This can be an option on some service provider. By default, the IdP signs the XML assersion and the subject. -
The
Consumer URL Protectionis a security setting used to refuse SAML requests containing AssertionConsumerServiceURL which do not match theIssuer URLhostname present in the same request. -
The
Consumer URL Exceptionsetting can be used when the AssertionConsumerServiceURL present in the SAML request do not match the SP issuer URL.
Example:
<?xml version="1.0" encoding="UTF-8"?>
<saml2p:AuthnRequest AssertionConsumerServiceURL="https://system.netsuite.com/saml2/acs"
Destination="https://sso.rcdevsdocs.com/openid/index.php"
ForceAuthn="false"
ID="_184481c4dc4698ff64574278aa43d60"
IsPassive="false"
IssueInstant="2023-11-09T14:26:25.059Z"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Version="2.0"
xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol">
<saml2:Issuer xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">http://www.netsuite.com/sp</saml2:Issuer>
<saml2p:NameIDPolicy AllowCreate="true"
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
SPNameQualifier="http://www.netsuite.com/sp" />
</saml2p:AuthnRequest>
In that example, the AssertionConsumerServiceURL (system.netsuite.com) do not match the Issuer (netsuite.com).
I can then configure a Consumer URL Exceptions like this:
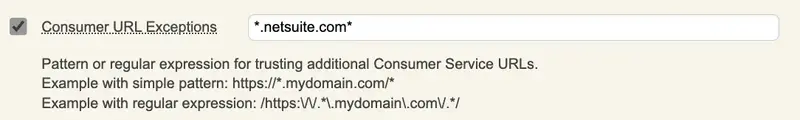
By default, the AssertionConsumerServiceURL is taken from the SAML request and is used by the IDP after the user authentication to redirect the user to the service provider. The AssertionConsumerServiceURL can be rewrite by client policy if needed. If multiple AssertionConsumerServiceURL are available on your service provider, then you can also use the Consumer URL Exception and configure a regex that will match all URLs.
Another usecase when the Issuer value is not an URL, you can define an exception based on the whole AssertionConsumerServiceURL available in the SAML request or define a regex matching mutliple AssertionConsumerServiceURL.
Example:
<?xml version="1.0" encoding="UTF-8"?>
<saml2p:AuthnRequest AssertionConsumerServiceURL="https://cognito.amazon.com/saml2/idpresponse"
Destination="https://sso.rcdevsdocs.com/openid/index.php"
ID="_5696fc7f-392d-4eee-b870-4ab41dd6aa17"
IssueInstant="2024-04-17T13:54:09.966Z"
Version="2.0"
xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol">
<saml2:Issuer Format="urn:oasis:names:tc:SAML:2.0:nameid-format:entity"
xmlns:saml2="urn:oasis:names:tc:SAML:2.0:assertion">urn:amazon:cognito:sp:eu-west-3_OMrbaByvF</saml2:Issuer>
</saml2p:AuthnRequest>
I can define as https://cognito.amazon.com/saml2/idpresponse in the Consumer URL Exception setting or a RegEx like /.*amazon.*/.
- The
Content Security Headerssetting can be used to enforce content security header protection for POST redirections.
You can now save your SAML configuration.
The SAML metadata URLs are accessible through WebADM servers and through WAProxy servers if the Web Application is published through WAPRoxy:
- SAML Metadata URL from the WebADM server: https://webadm1.rcdevsdocs.com/webapps/openid/metadata/
<EntityDescriptor xmlns="urn:oasis:names:tc:SAML:2.0:metadata" entityID="https://sso.rcdevsdocs.com">
<IDPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<KeyDescriptor use="signing">
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<X509Data>
<X509Certificate>MIIGfzCCBGegAwIBAgIRAM9/TyvDiZAahDgzYkWGRdIwDQYJKoZIhvcNAQELBQAwUjEXMBUGA1UEAwwOUkNEZXZzIERvY3MgQ0ExCzAJBgNVBAsMAkNBMR0wGwYDVQQKDBRSQ0RldnMgRG9jdW1lbnRhdGlvbjELMAkGA1UEBhMCTFUwHhcNMjQwNzE1MTM0OTA3WhcNMzQwNzEzMTM0OTA3WjBgMRswGQYDVQQDDBJXZWJBRE0gQ2VydGlmaWNhdGUxDzANBgNVBA0MBlNFUlZFUjEXMBUGA1UECgwOUkNEZXZzIFN1cHBvcnQxFzAVBgNVBGEMDlZBVExVLTAwMDAwMDAwMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1w3PR1Q+78jdD12g4Di3ljcthoZwvpQuwmuOm/+fBthQjrHR1UIY3HDkulCOYpBRiNNj6ED49eyF9jIeO/zVO5QXnzX4gmasZPd06ZYAD8pkDc7fnnxZD4aSHDKQcF1xwUnHESUCPzWR1Wy3t6ifwl85uRuC+QlskMv4t82LqeMQeSBdeBqNpADm9Hmg8AO5BK4Oz/NNooB46P5RYDEerY1D/qOfLkuzEDr2C2Z1rGvtG7+7EpaS+b9Ipnz/fT71QACPxJym98YWEp/1Fb/clC6QLKQuQ+AzheTVZyyeOhOYFxsoGEu+wDFAERXWWAr5sPnayDJiZdXbH+712ri35y9oFWOxZC1diATOS/MRc05bAzgAbyiQe1PrhDfwRiL4YF0EtLvuZJGBH031DZS3THdYSeONDhsImbNYFYLPpzRqb5iXssN+KBPAdCfYJ2IMfjAV4li0s1WSC40iZ5MAkwovE0HD++DVO2HHBJ9hYl6aqa35lGm/QSjkUYvw2xX3kvc3utPQcqUkYDWzF7tLIMpTzO6FtD1pR/FR6DKkqmx9NhLMdIi9eNGK4MG+MgKwCXhE1I6aJxVoRCbAihb0wgnR+Y38P4bJUYzvDCC4upE3DLc+ct5VJ/rtCo9UDyVQGsLDD9cDoywdr6feM/Pou+LpccVNAHul1FJ9CPKxyVECAwEAAaOCAUAwggE8MAsGA1UdDwQEAwIF4DATBgNVHSUEDDAKBggrBgEFBQcDATCBygYIKwYBBQUHAQEEgb0wgbowJgYIKwYBBQUHMAGGGmh0dHA6Ly8xOTIuMTY4LjQuMTYwL29jc3AvMCYGCCsGAQUFBzABhhpodHRwOi8vMTkyLjE2OC40LjE2MS9vY3NwLzAzBggrBgEFBQcwAoYnaHR0cDovLzE5Mi4xNjguNC4xNjAvY2FjZXJ0Lz9mb3JtYXQ9ZGVyMDMGCCsGAQUFBzAChidodHRwOi8vMTkyLjE2OC40LjE2MS9jYWNlcnQvP2Zvcm1hdD1kZXIwSwYDVR0fBEQwQjAfoB2gG4YZaHR0cDovLzE5Mi4xNjguNC4xNjAvY3JsLzAfoB2gG4YZaHR0cDovLzE5Mi4xNjguNC4xNjEvY3JsLzANBgkqhkiG9w0BAQsFAAOCAgEACy/zl7IPSaOn2wEZ66xQNxm9FW408jMrQS2Y6hFvfzRMNhbOh+ZwNFSgCijUJ4ASZVQeZIiYN8f/quH80Y7AJE3kcTpXvJE2LozDbUMsXe0GpkNuzDojbp3K2ZcgUitL0q/rDHPBXXExl1AEhPgpwN1I7ZyHPfZpU92XxcsoSrUi8AMmzoVwlna30RMkkCDDBsf+an1uxdrdwMQLeQddOFddAUI80NWvh0drnv1epkT34K+RpvEAU514a3suErDMIqp+h7BqTdPrdiRkIhTutgSsPquhGIDzv+WvGBzFGWPAfudQHE5jMn3lPgN3r75HrdNfMkVEv0jclpp3VhiUnwQzNQn2UzVe7LQh8ixjEg1kwtIQ8UuwX6LOZ7a51WuKkRfS1iw1yDCM1UmGNuoMGqI6bxwFbBZ1C3brgJKjXBciEpXrSpcJ+ulhDYYUrCmGnpg6xyJ6veWfT2tVExLcffv4edT0KCJuKsyTztLFtT9A9ihyV/lPBsVUtIipe2CaCXupP84812s0cgo6XkcAr99pvtPNLZg9aBLuVt7GmyJSQeLJ6z+QWlkKnsEh7HlSrV2RC/wsTYlTeTRZFmiNa1RGx4UsNyTf9Igp+EG4Nh/UBhGO1Jkn1dIRZyb/qgcF/DWCSdbwFIKxuaKA12KFJMFS4aMV1e0QLDhLfpZ1/10=</X509Certificate>
<!-- Cert Fingerprint (SHA1): 32774463a2e892150f46852b3fdcac7f5be924dc -->
<!-- Cert Fingerprint (SHA256): e0bd10584f5c3a554e279b9241619e8fdf9c3bfbe95c90da939f0342546e52ac -->
<!-- Cert Fingerprint (MD5): 639ed5b4241047c8382f897fc459a714 -->
</X509Data>
</KeyInfo>
</KeyDescriptor>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://webadm1.rcdevsdocs.com/webapps/openid/index.php"/>
<SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://webadm1.rcdevsdocs.com/webapps/openid/index.php"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://webadm1.rcdevsdocs.com/webapps/openid/index.php"/>
<SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://webadm1.rcdevsdocs.com/webapps/openid/index.php"/>
</IDPSSODescriptor>
</EntityDescriptor>
The SAML clients (Service Providers) need to know about the SAML IdP endpoints. Most clients will accept the autoconfiguration with an XML-based metadata URL. You can provide the previous URLs according to your scenario.
Many SAML SP will require your IDP endpoint to be run with a trusted SSL certificate.
OpenID Configuration
The configuration of the OpenID service is very simple. Version 1.2.x includes support for OpenID-Connect and OAuth2.
To use your identity provider in OpenID-Connect mode, the client configuration must include the scope openid in the IdP requests. The supported OpenID-Connect scopes are: basic, email, phone, profile, and groups.
To use your identity provider in OAuth2 mode, the client must include the scope profile in the IdP requests.
If your client application needs the user’s email address, you can additionally request the openid email scope.
The allowed scopes must be enabled in the global configuration or per client policy in order to be returned to the service providers that request them.
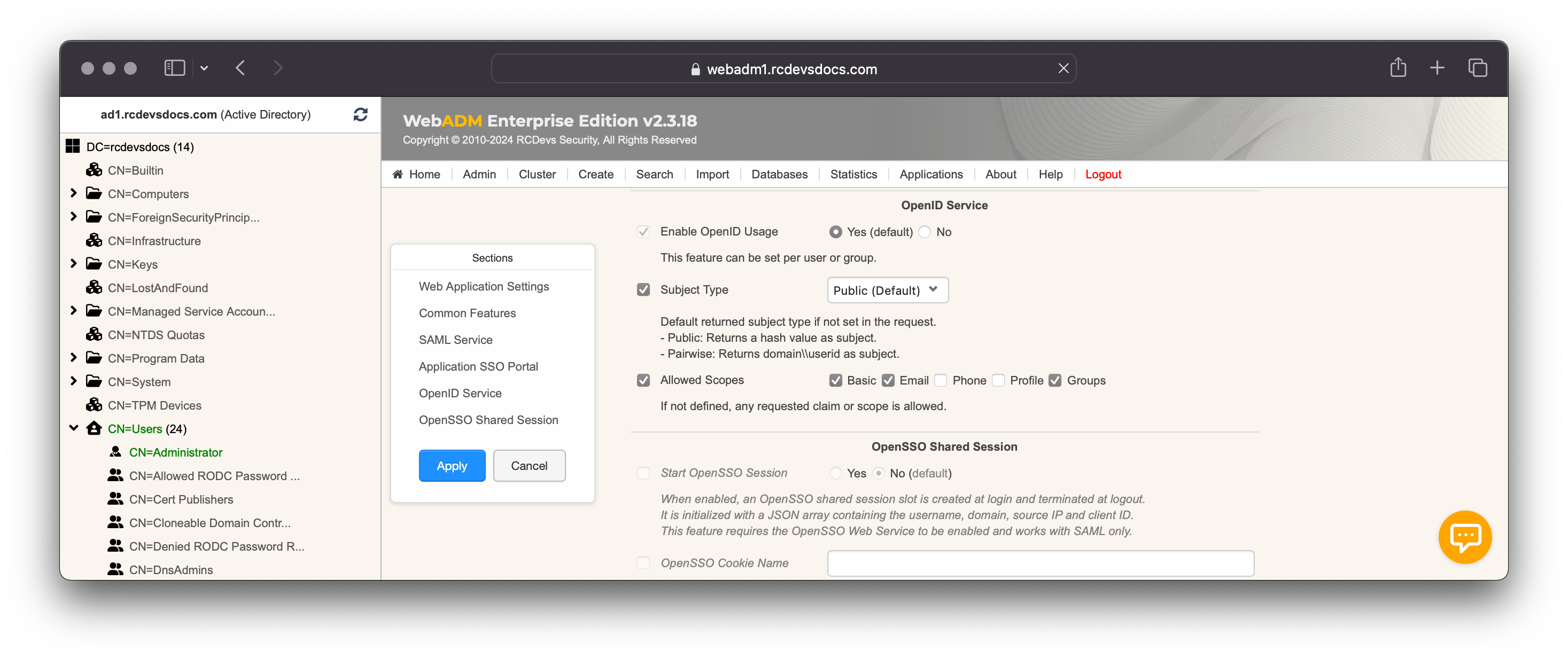
The OpenID metadata URL is accessible through WebADM servers and through WAProxy servers if the Web Application is published through WAPRoxy:
-
Metadata URL from the WebADM server: https://webadm1.rcdevsdocs.com/webapps/openid/.well-known/openid-configuration
-
Metadata URL from the WAProxy/Reverse Proxy: https://sso.rcdevsdocs.com/ws/openid/
Which is returning the following in my scenario:
{
"issuer": "https://sso.rcdevsdocs.com",
"authorization_endpoint": "https://sso.rcdevsdocs.com/openid/index.php",
"token_endpoint": "https://sso.rcdevsdocs.com/openid/index.php",
"userinfo_endpoint": "https://sso.rcdevsdocs.com/openid/index.php",
"jwks_uri": "https://sso.rcdevsdocs.com/openid/certs.php",
"subject_types_supported": [
"public",
"pairwise"
],
"response_types_supported": [
"code",
"token",
"id_token"
],
"response_modes_supported": [
"query",
"fragment",
"form_post"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"claim_types_supported": [
"normal"
],
"scopes_supported": [
"basic",
"openid",
"email",
"phone",
"profile",
"groups"
],
"claims_supported": [
"sub",
"email",
"email_verified",
"phone_number",
"phone_number_verified",
"preferred_username",
"preferred_language",
"given_name",
"family_name",
"name",
"groups",
"mfa-policy",
"amr",
"acr",
"RCDevsMfa"
]
}
The global configuration of your Identity Provider is complete. Browse the next documentation in the Single Sign-On section to explore examples of Service Provider integrations.
Service Provider–specific configuration
Integrating a SAML or OpenID Connect service provider with the RCDevs IdP consists of creating a Client Policy for each integrated SP.
Client policies allow you to define application-specific settings. Within each policy, you can configure multiple constraints, such as:
- Allowed groups or domains
- Authentication policies
- SAML/OpenID-specific settings (for example, the NameID format returned as UPN, ImmutableID, or Transient)
- Attribute mappings, including fixed values or dynamic values retrieved from LDAP attributes
Most customization is handled through client policies.
Refer to the following documentation to create and configure your Client Policy.
Once you enter the Client Policy Configuration Viewer, edit the Default Application Settings.
In the Applications section, select the application you want to configure (OpenOTP or SAML/OpenID).
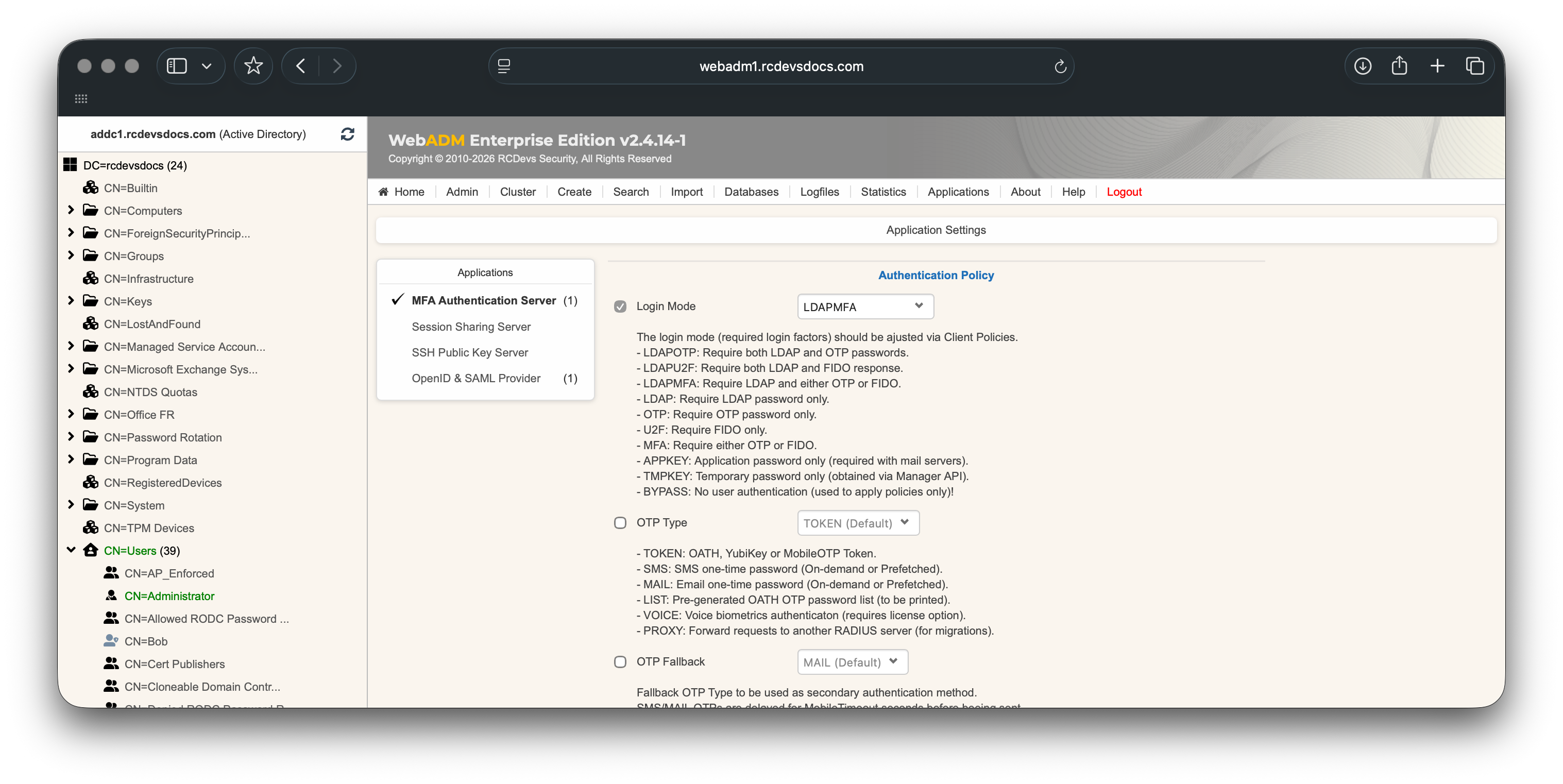
e.g : Configure OpenOTP Authentication to LDAPMFA:
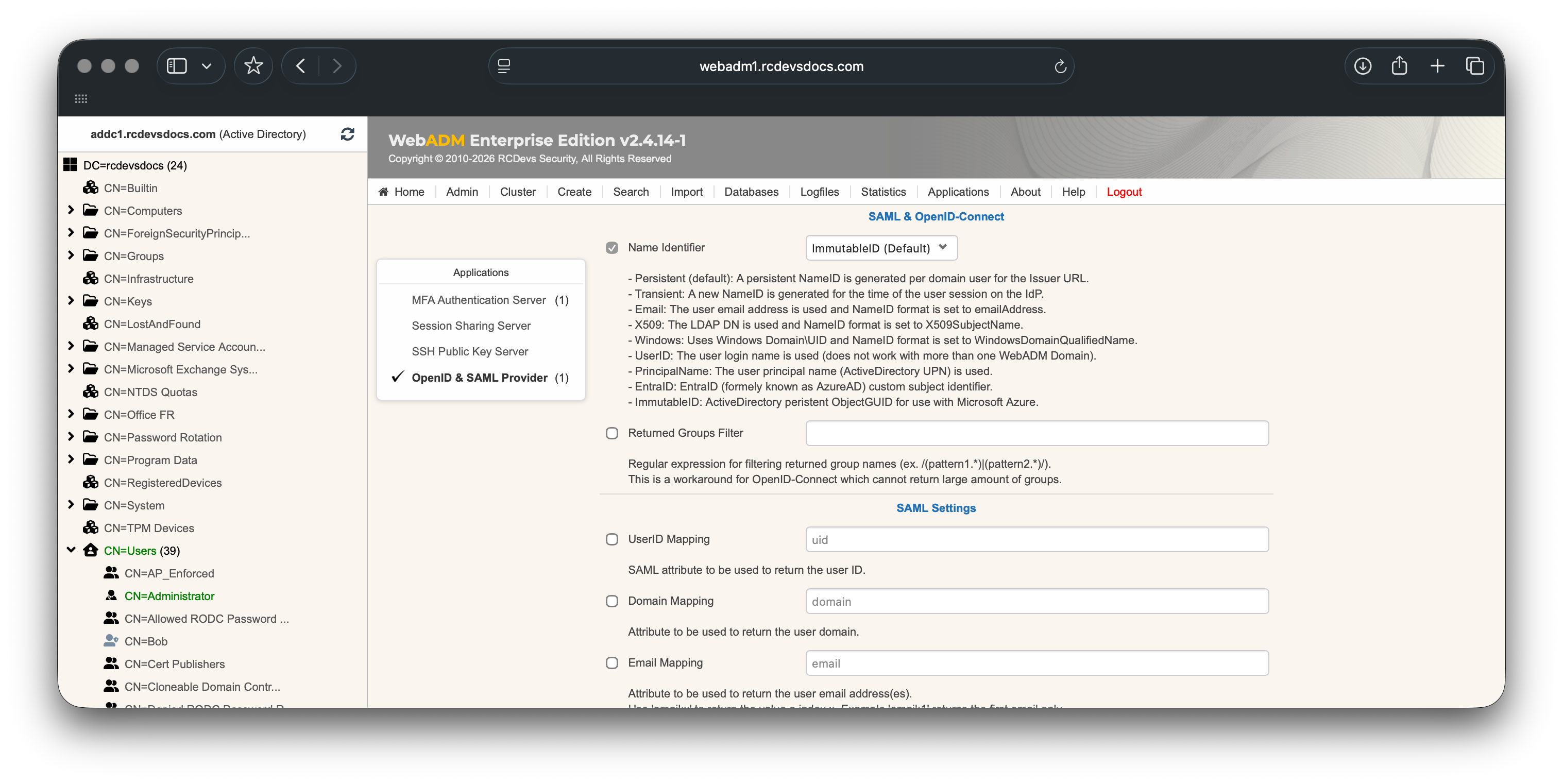
e.g : Configure the Name Identifier to ImmutableId:
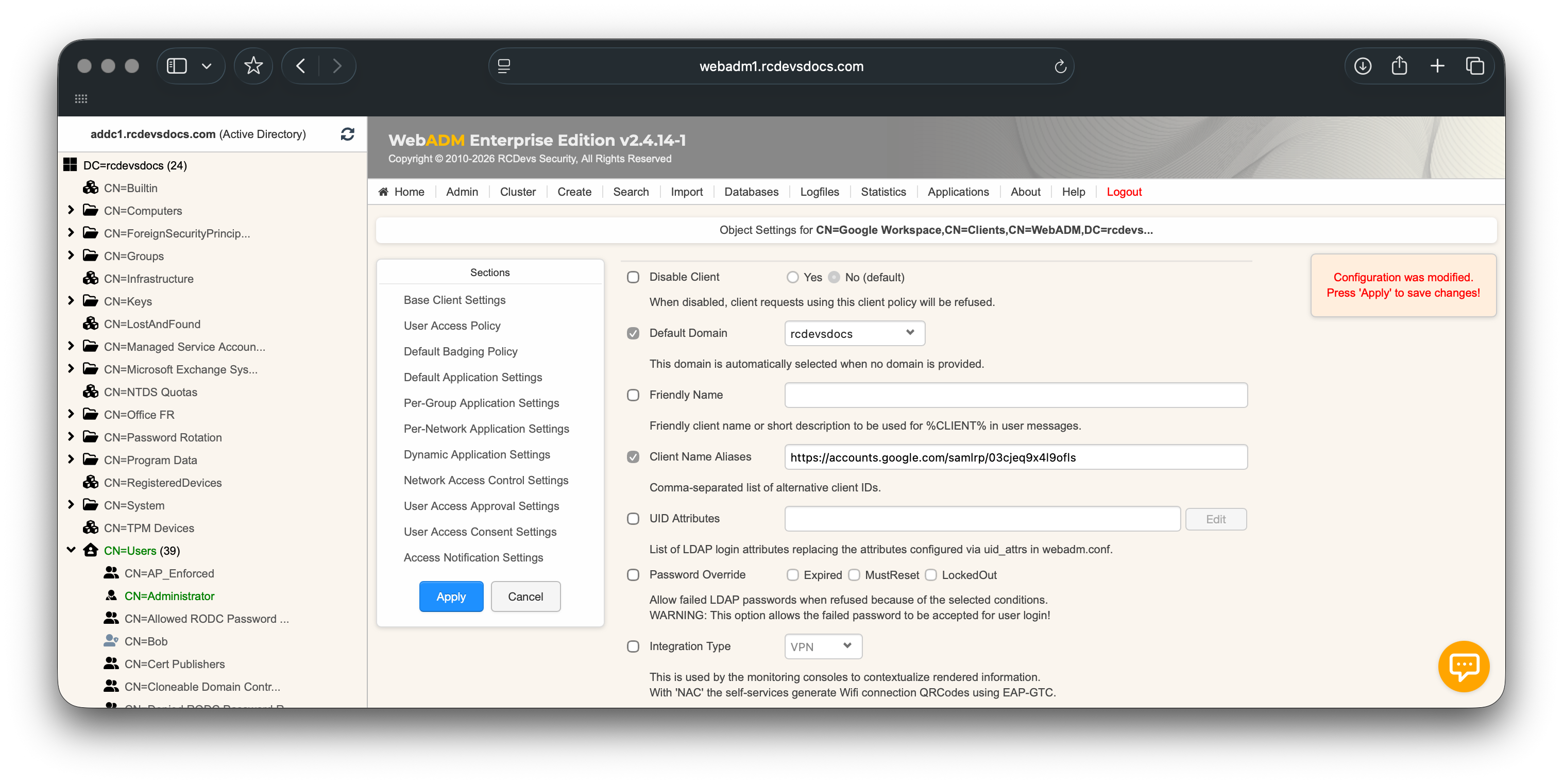
The Client Name Alias must be set to the Issuer value sent by the integrated Service Provider.
This setting is required to ensure correct policy matching when SAML/OpenID requests reach the Identity Provider.
e.g : Configure the Issuer value sent by the service provider :
Supported Integrations with RCDevs Identity Provider
RCDevs Identity Provider supports integrations with any Service Provider (SP) that supports standard authentication protocols like OpenID, SAML, or OAuth. This includes a wide range of applications and services, providing Single Sign-On and federated authentication. Whether you are using cloud services, enterprise applications, or custom-built solutions, RCDevs can integrate effortlessly with your existing environment.
Here are some examples of Service Providers that can be integrated with RCDevs Identity Provider. Please note, this is not an exhaustive list, and many other applications supporting these standards can also be integrated:
| Name | Protocols | Notes | Config URL |
|---|---|---|---|
| 1Password | SAML2, OpenID | 1Password Business/Teams supports SSO. Docs show OIDC and SAML-based configurations (Unlock with SSO). | Link |
| Algolia | SAML2 | Algolia Dashboard SSO is provided via SAML; enablement currently through Algolia support/engineering for your account. | Link |
| Amplitude | SAML2 | Amplitude Org SSO is SAML 2.0 compatible. Provider integration guides exist (MS Entra/OneLogin examples). | Link |
| Anaplan | SAML2 | Anaplan uses SAML (self-service SAML available in Admin console). | Link |
| Aruba Central | SAML2 | Aruba Central supports SAML 2.0 for SSO (Service Provider). | Link |
| Aruba ClearPass | SAML2 | ClearPass Policy Manager supports SAML 2.0 as SP for web logins. | Link |
| Asana | SAML2, OAuth2, OpenID | Asana Enterprise uses SAML for SSO; API access uses OAuth 2.0 / OIDC. | Link |
| AWS Organizations | SAML2, OpenID, OAuth2 | AWS supports SAML 2.0 federation, OIDC for identity providers, and OAuth2 for API delegation. | Link |
| Betterworks | SAML2 | Betterworks Enterprise supports SAML 2.0 SSO via IdP integrations. | Link |
| BILL Accounts Payable & Receivable | SAML2 | BILL (formerly Bill.com) supports SAML 2.0 for SSO on enterprise accounts. | Link |
| Bitbucket | SAML2, OAuth2 | Bitbucket Cloud supports SAML SSO via Atlassian Access; OAuth2 for API integration. | Link |
| Blueboard | SAML2 | Blueboard SSO supports SAML 2.0 integrations. | Link |
| Bonusly | SAML2 | Bonusly supports SAML 2.0 for SSO configuration with major IdPs. | Link |
| Box | SAML2, OAuth2, OpenID | Box supports SAML 2.0 for enterprise SSO and OAuth2/OIDC for API and app integrations. | Link |
| Branch | SAML2 | Branch (branch.io) supports SAML 2.0 for SSO on Enterprise accounts. | Link |
| Brex | SAML2 | Brex dashboard supports SAML 2.0 and OpenID-Connect SSO for enterprise users. | Link |
| Buffer | OAuth2 | Buffer authentication for integrations uses OAuth2. No SAML SSO available. | Link |
| Calendly | SAML2, OAuth2 | Calendly supports SAML 2.0 for SSO; OAuth2 used for integrations. | Link |
| Canva | SAML2 | Canva for Teams/Enterprise supports SAML 2.0 SSO via major IdPs. | Link |
| Carta | SAML2 | Carta Enterprise supports SAML 2.0 SSO setup. | Link |
| Checkr | SAML2 | Checkr supports SAML 2.0-based SSO for enterprise users. | Link |
| Cisco Adaptive Security Appliance (ASA) Software | SAML2 | ASA supports SAML 2.0 for VPN authentication as SP. | Link |
| Cisco AnyConnect | SAML2 | AnyConnect uses ASA’s SAML 2.0 integration for VPN SSO. | Link |
| Cisco Jabber | SAML2, OAuth2, OpenID | Jabber supports SAML 2.0 and OAuth2/OIDC via Cisco Unified Communications Manager and IM&P integration. | Link |
| Cisco Meraki | SAML2 | Meraki Dashboard supports SAML 2.0 SSO with role mapping. | Link |
| Cisco Secure Firewall | SAML2 | Cisco Secure Firewall supports SAML 2.0 SSO via Entra ID and others. | Link |
| Cisco Umbrella | SAML2 | Umbrella dashboard supports SAML 2.0 for login SSO. | Link |
| Citrix Workspace | SAML2 | Citrix Workspace/Cloud supports SAML 2.0 for identity federation. | Link |
| ClearSlide | SAML2 | ClearSlide supports SAML 2.0 SSO for Enterprise. | |
| ClickTime | SAML2 | ClickTime supports SAML 2.0-based SSO via SAML IdPs. | Link |
| ClickUp | SAML2, OAuth2 | ClickUp Enterprise supports SAML 2.0 SSO; OAuth2 used for app integrations. | Link |
| Datadog | SAML2, OAuth2 | Datadog supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| Degreed | SAML2 | Degreed Enterprise supports SAML 2.0 SSO for user authentication. | Link |
| Deputy | SAML2 | Deputy supports SAML 2.0 SSO for enterprise accounts. | Link |
| Dialpad | SAML2, OAuth2 | Dialpad supports SAML 2.0 SSO and OAuth2 for API access. | Link |
| DigitalOcean | SAML2, OAuth2 | DigitalOcean supports SAML 2.0 SSO for Teams and OAuth2 for API access. | Link |
| Docker | SAML2, OAuth2 | Docker Hub supports SAML 2.0 for enterprise SSO and OAuth2 for API integrations. | Link |
| Docusign | SAML2, OAuth2, OpenID | DocuSign supports SAML 2.0 SSO and OAuth2/OIDC for API authentication. | Link |
| Domo | SAML2, OAuth2 | Domo supports SAML 2.0 SSO for enterprise users and OIDC for integrations. | Link |
| Doppler | SAML2, OAuth2 | Doppler supports SAML 2.0 for enterprise SSO and OAuth2 for API use. | Link |
| Drata | SAML2, OAuth2 | Drata supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| Dropbox Business | SAML2, OAuth2, OpenID | Dropbox Business supports SAML 2.0 for SSO and OAuth2/OIDC for API integrations. | Link |
| Dropbox Sign | SAML2, OAuth2 | Dropbox Sign (formerly HelloSign) supports SAML 2.0 for enterprise SSO and OAuth2 for API access. | Link |
| Egnyte | SAML2, OAuth2 | Egnyte supports SAML 2.0 SSO for enterprise accounts and OAuth2 for API. | Link |
| Envoy | SAML2 | Envoy supports SAML 2.0 for enterprise SSO. | Link |
| Eventbrite | SAML2 | Eventbrite supports OAuth SSO for enterprise customers. | Link |
| Expensify | SAML2 | Expensify supports SAML 2.0 SSO for business accounts. | Link |
| F5 BIG-IP Access Policy Manager | SAML2, OAuth2 | F5 APM supports SAML 2.0 and OAuth2/OIDC for identity federation. | Link |
| Figma | SAML2, OAuth2, OpenID | Figma supports SAML 2.0 for enterprise SSO and OAuth2/OpenID Connect for API access. | Link |
| FortiGate Next-Generation Firewall | SAML2, OAuth2 | FortiGate supports SAML 2.0 SSO for user authentication and OAuth2 for API integrations. | Link |
| Frame.io | SAML2 | Frame.io Enterprise supports SAML 2.0 for SSO. | Link |
| Freshdesk | SAML2 | Freshdesk supports SAML 2.0 SSO for enterprise plans. | Link |
| Front | SAML2, OAuth2 | Front supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| Geckoboard | SAML2 | Geckoboard supports SAML 2.0 SSO for enterprise customers. | Link |
| GitHub | SAML2, OAuth2, OpenID | GitHub Enterprise supports SAML SSO; OAuth2 and OIDC for API/app integrations. | Link |
| GitLab | SAML2, OAuth2, OpenID | GitLab supports SAML 2.0 for SSO and OAuth2/OpenID Connect for integrations. | Link |
| Gmail | SAML2, OAuth2, OpenID | Gmail via Google Workspace supports SAML 2.0 SSO, OAuth2, and OpenID Connect. | Link |
| Gong.io | SAML2 | Gong Enterprise supports SAML 2.0 SSO for users. | Link |
| Google Analytics 360 | SAML2, OAuth2, OpenID | GA 360 supports SAML 2.0 via Google Workspace SSO; OAuth2/OIDC for API access. | Link |
| Google Calendar | SAML2, OAuth2, OpenID | Google Calendar supports SAML SSO via Workspace; OAuth2/OpenID for API access. | Link |
| Google Contacts | SAML2, OAuth2, OpenID | SAML SSO via Google Workspace; OAuth2/OpenID for API integration. | Link |
| Google Docs | SAML2, OAuth2, OpenID | SAML SSO via Workspace; OAuth2/OpenID for API. | Link |
| Google Drive | SAML2, OAuth2, OpenID | SAML via Workspace; OAuth2/OpenID for API access. | Link |
| Google Workspace | SAML2, OAuth2, OpenID | Full SSO support with SAML 2.0; OAuth2/OpenID for integrations. | Link |
| GoTo Meeting | SAML2 | GoTo Meeting Enterprise supports SAML 2.0 SSO. | Link |
| Harvest | SAML2 | Harvest supports SAML 2.0 SSO for enterprise accounts. | Link |
| Heap | SAML2 | Heap Enterprise supports SAML 2.0 for SSO. | Link |
| Help Scout | SAML2 | Help Scout supports SAML 2.0 SSO for enterprise plans. | Link |
| Heroku | SAML2, OAuth2, OpenID | Heroku Enterprise supports SAML 2.0 SSO; OAuth2/OpenID for API authentication. | Link |
| HiringThing | SAML2 | HiringThing supports SAML 2.0 SSO for enterprise customers. | Link |
| Hootsuite | SAML2 | Hootsuite Enterprise supports SAML 2.0 SSO. | Link |
| Hotjar | SAML2 | Hotjar Enterprise supports SAML 2.0 SSO. | Link |
| Indeed for Employers | No public documentation confirming SAML or OIDC support. | Link | |
| Intercom | SAML2, OAuth2 | Intercom Enterprise supports SAML 2.0 SSO; OAuth2 for API integrations. | Link |
| JazzHR | SAML2 | JazzHR supports SAML 2.0 for Enterprise SSO. | Link |
| Jira | SAML2, OAuth2, OpenID | Jira Cloud supports SAML 2.0 SSO via Atlassian Access; OAuth2/OpenID for API integration. | Link |
| Jira OAuth | OAuth2, OpenID | Jira OAuth used for app integration; SAML handled at Jira Cloud level. | Link |
| Kantata | SAML2 | Kantata (formerly Mavenlink) supports SAML 2.0 SSO for enterprise accounts. | Link |
| LastPass | SAML2, OAuth2, OpenID | LastPass supports SAML 2.0 SSO for enterprise accounts; OAuth2/OpenID for API apps. | Link |
| Lattice | SAML2 | Lattice supports SAML 2.0 for Enterprise SSO. | Link |
| Leapsome | SAML2 | Leapsome supports SAML 2.0 for enterprise SSO. | Link |
| Lever | SAML2 | Lever Enterprise supports SAML 2.0 for SSO. | Link |
| LinkedIn for Business | No public documentation confirming SAML or OIDC support for LinkedIn login. | Link | |
| Lucidchart | SAML2 | Lucidchart Enterprise supports SAML 2.0 SSO. | Link |
| Mailgun | OAuth2 | Mailgun uses SAML SSO for login. | Link |
| Marketo Engage | SAML2 | Marketo supports SAML 2.0 SSO for enterprise accounts. | Link |
| Meltwater | SAML2 | Meltwater supports SAML 2.0 SSO for enterprise customers. | Link |
| Meta for Business | SAML2 | Meta Business Suite supports SAML 2.0 SSO for enterprise access. | Link |
| Microsoft 365 | SAML2, OAuth2, OpenID | Microsoft 365 supports SAML 2.0 for SSO, OAuth2, and OpenID Connect for integrations. | Link |
| Microsoft Azure | SAML2, OAuth2, OpenID | Azure AD supports SAML 2.0, OAuth2, and OpenID Connect for apps and enterprise login. | Link |
| Microsoft Entra ID | SAML2, OAuth2, OpenID | Entra ID (formerly Azure AD) supports SAML, OAuth2, and OpenID Connect. | Link1 Link2 |
| Mixpanel | SAML2, OAuth2 | Mixpanel supports SAML 2.0 for enterprise SSO; OAuth2 for API integrations. | Link |
| monday.com | SAML2, OAuth2 | monday.com Enterprise supports SAML 2.0 SSO and OAuth2 for API integrations. | Link |
| NetSuite | SAML2, OAuth2 | NetSuite supports SAML 2.0 for SSO and OAuth2 for integrations. | Link |
| New Relic | SAML2, OAuth2 | New Relic supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| Nextcloud | SAML2, OAuth2, OpenID | Nextcloud supports SAML 2.0 SSO, OAuth2, and OpenID Connect. | Link |
| Nextiva | SAML2 | Nextiva supports SAML 2.0 SSO for enterprise accounts. | Link |
| Northpass | SAML2 | Northpass supports SAML 2.0 for enterprise SSO. | Link |
| Notion | SAML2 | Notion Enterprise supports SAML 2.0 SSO. | Link |
| ONLYOFFICE Workspace | SAML2, OAuth2, OpenID | ONLYOFFICE Workspace supports SAML 2.0 for SSO and OAuth2/OpenID for app integrations. | Link |
| Oracle E-Business Suite | SAML2, OAuth2 | Oracle EBS supports SAML 2.0 for SSO and OAuth2 for integrations. | Link |
| Oracle Fusion Cloud ERP | SAML2, OAuth2, OpenID | Oracle Fusion Cloud ERP supports SAML 2.0, OAuth2, and OpenID Connect for identity federation. | Link |
| Oracle Fusion Cloud HCM | SAML2, OAuth2, OpenID | Oracle Fusion Cloud HCM supports SAML 2.0, OAuth2, and OpenID Connect for identity management. | Link |
| Oracle PeopleSoft | SAML2, OAuth2 | PeopleSoft supports SAML 2.0 for SSO and OAuth2 for API access. | Link |
| Outreach | SAML2, OAuth2 | Outreach supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| ownCloud | SAML2, OAuth2, OpenID | ownCloud supports SAML 2.0, OAuth2, and OpenID Connect for identity federation. | Link |
| PagerDuty | SAML2, OAuth2, OpenID | PagerDuty supports SAML 2.0 SSO, OAuth2, and OpenID Connect for API access. | Link |
| Palo Alto | SAML2 | Palo Alto support SAML 2.0 SSO. | Link |
| PandaDoc | SAML2, OAuth2 | PandaDoc supports SAML 2.0 SSO and OAuth2 for integrations. | Link |
| Papertrail | SAML2, OAuth2 | Papertrail supports SAML 2.0 for SSO and OAuth2 for API access. | Link |
| Passbolt | SAML2, OAuth2, OpenID | Passbolt supports SAML 2.0 SSO, OAuth2, and OpenID Connect for authentication. | Link |
| PayPal | SAML2, OAuth2 | PayPal supports SAML 2.0 for enterprise login (Braintree/PayPal Business) and OAuth2 for API integrations. | Link |
| Pendo | SAML2, OAuth2 | Pendo supports SAML 2.0 SSO for enterprise accounts and OAuth2 for API access. | Link |
| Pipedrive | SAML2, OAuth2 | Pipedrive supports SAML 2.0 SSO for enterprise plans and OAuth2 for API integrations. | Link |
| Pivotal Tracker | SAML2, OAuth2 | Pivotal Tracker supports SAML 2.0 for SSO and OAuth2 for integrations. | Link |
| prismic.io | SAML2, OAuth2 | Prismic supports SAML 2.0 for SSO and OAuth2 for API integration. | Link |
| Procore | SAML2, OAuth2 | Procore supports SAML 2.0 SSO and OAuth2 for API integrations. | Link |
| Proto.io | SAML2, OAuth2 | Proto.io supports SAML 2.0 SSO for enterprise accounts and OAuth2 for integrations. | Link |
| QuickBooks Online | OAuth2 | QuickBooks Online OAuth 2.0 for enterprise SSO and OAuth2 for API access. | Link |
| Quip | SAML2, OAuth2, OpenID | Quip supports SAML 2.0 SSO and OAuth2/OpenID Connect for API integrations. | Link |
| Recurly | SAML2, OAuth2 | Recurly supports SAML 2.0 SSO authentication. | Link |
| Rollbar | SAML2, OAuth2 | Rollbar supports SAML 2.0 SSO and OAuth2 for integrations. | Link |
| Salesforce Marketing Cloud Account Engagement | SAML2, OAuth2, OpenID | Salesforce Marketing Cloud supports SAML 2.0 for SSO, OAuth2 and OpenID for integrations. | Link |
| Salesforce Platform | SAML2 | Salesforce supports SAML 2.0 SSO for integrations. | Link |
| Salesforce Sales Cloud | SAML2 | Sales Cloud supports SAML 2.0 SSO for integrations. | Link |
| SAP Concur | SAML2 | SAP Concur supports SAML 2.0 for enterprise SSO. | Link |
| SAP SuccessFactors Work Zone | SAML2, OAuth2, OpenID | SAP SuccessFactors supports SAML 2.0, OAuth2, and OpenID Connect for authentication and SSO. | Link |
| ScreenSteps | SAML2 | ScreenSteps supports SAML 2.0 SSO for enterprise accounts. | Link |
| Secureframe | SAML2, OAuth2 | Secureframe supports SAML 2.0 and OIDC for SSO. | Link |
| SendGrid | SAML2 | SendGrid supports SAML 2.0 SSO for enterprise accounts. | Link |
| SentinelOne | SAML2 | SentinelOne supports SAML 2.0 for enterprise SSO. | Link |
| Sentry | SAML2, OAuth2 | Sentry supports SAML 2.0 SSO and OAuth2 for integrations. | Link |
| ServiceNow | SAML2, OAuth2, OpenID | ServiceNow supports SAML 2.0, OAuth2, and OpenID Connect for authentication. | Link |
| Shopify | SAML2, OAuth2 | Shopify Plus supports SAML 2.0 SSO and OAuth2 for API integrations. | Link |
| Sisense | SAML2, OAuth2, OpenID | Sisense supports SAML 2.0 SSO, OAuth2, and OpenID Connect. | Link |
| Slack | SAML2, OAuth2, OpenID | Slack supports SAML 2.0 for SSO and OAuth2/OpenID for apps and integrations. | Link |
| Small Improvements | SAML2 | Small Improvements supports SAML 2.0 SSO for enterprise accounts. | Link |
| Smartsheet | SAML2, OAuth2, OpenID | Smartsheet supports SAML 2.0 for SSO and OAuth2/OpenID for integrations. | Link |
| Splunk Enterprise | SAML2, OAuth2, OpenID | Splunk Enterprise supports SAML 2.0 for SSO and OAuth2/OpenID Connect for integrations. | Link |
| Sprout Social | OIDC | Sprout Social supports OpenID-Connect for integrations. | Link |
| Statuspage | SAML2, OAuth2 | Statuspage supports SAML 2.0 for SSO and OAuth2 for API integrations. | Link |
| Stripe | SAML2 | Stripe supports SAML 2.0 for enterprise SSO. | Link |
| SugarCRM | SAML2, OAuth2, OpenID | SugarCRM supports SAML 2.0 SSO and OAuth2/OpenID for API and app integration. | Link |
| Sumo Logic | SAML2, OAuth2, OpenID | Sumo Logic supports SAML 2.0 SSO, OAuth2, and OpenID Connect for integrations. | Link |
| SurveyMonkey | SAML2 | SurveyMonkey Enterprise supports SAML 2.0 SSO. | Link |
| Talkdesk | SAML2 | Talkdesk supports SAML 2.0 for SSO for integrations. | Link |
| Time Doctor | SAML2 | Time Doctor supports SAML 2.0 SSO for enterprise accounts. | Link |
| TINYpulse | SAML2 | TINYpulse supports SAML 2.0 SSO for enterprise customers. | Link |
| Toggl Track | SAML2 | Toggl Track Enterprise supports SAML 2.0 for SSO. | Link |
| Trello | SAML2, OAuth2, OpenID | Trello Enterprise supports SAML 2.0 for SSO, OAuth2/OpenID for integrations. | Link |
| Twitter/X | OAuth2, OpenID | Twitter supports OAuth2/OpenID Connect for apps. | Link |
| UserVoice | SAML2 | UserVoice supports SAML 2.0 SSO for enterprise accounts. | Link |
| Vanta | SAML2, OAuth2 | Vanta supports SAML 2.0 SSO and OAuth2 for integrations. | Link |
| VMware Cloud Director | SAML2 | VMware Cloud Director supports SAML 2.0 for integration | Link |
| When I Work | SAML2 | When I Work supports SAML 2.0 SSO. | Link |
| Wistia | SAML2, OIDC | Wistia supports SAML 2.0 SSO and OpenID-Connect for enterprise accounts. | Link |
| WordPress | SAML2, OpenID | WordPress supports SAML 2.0 SSO via plugins and OpenID for integrations. | Link |
| Workable | SAML2, OAuth2 | Workable supports SAML 2.0 SSO for enterprise accounts and OAuth2 for API access. | Link |
| Workday Adaptive Planning | SAML2 | Workday Adaptive Planning supports SAML 2.0 SSO, OAuth2, and OpenID Connect. | |
| Workleap Pingboard | SAML2 | Pingboard supports SAML 2.0 SSO. | Link |
| Wrike | SAML2 | Wrike supports SAML 2.0 SSO. | Link |
| Xero | OIDC | Xero supports OpenID-Connect for SSO. | Link |
| Zabbix | SAML2, OAuth2 | Zabbix supports SAML 2.0 for SSO and OAuth2 for API integration. | Link |
If your application (service provider) supports OpenID, SAML, or OAuth, it is highly likely that it can be integrated with RCDevs Identity Provider to streamline user authentication and improve security across your applications.
You can find several integration examples in the OpenID Connect & SAML2 IdP section of the RCDevs documentation site.
